
There is an ever increasing amount of personal data circulating on the Internet, yet the security in place to safeguard this data is not evolving at the same rate. Many applications and Web services jeopardize user information by not employing any encryption system to protect it.
Given this situation, IT engineer Tony Webster has set up a website to draw attention to those who are reckless in their approach to safeguarding data. At HTTP Shaming you can find the names of the ‘guilty’ websites and how they are violating users’ privacy. If they abuse the trust of their users, it’s only fair that the users should know.
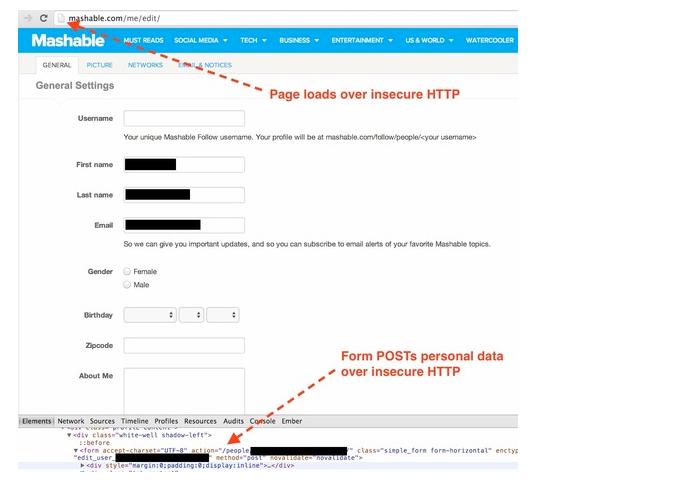
One of the names that appears on the website is Mashable. According to Webster, this news website enables users to connect using their social networks accounts and interact through them. The problem however is that all this activity is happening on an HTTP address, instead of the secure HTTPS internet protocol, which encrypts the information transmitted with the SSL (‘Secure Sockets Layer’) system.
An SSL certificate, which guarantees the security of Internet communications, works by assigning keys to files exchanged between a client computer and the server of the company providing the service, so that only the company can access the file content.
If however you use the service offered by Mashable while connected to an open WiFi network, as with many public sites, your email address, alias and passwords could be stolen by cyber-criminals (those you use for Mashable as well as the social networks you use to access the page).
The TripIt travel planning site, where you can manage bookings, check timetables and flight schedules, and share all of this with other users, is another similar case.
In both the Tripit versions for smartphones and for websites, users are first asked to enter an email address and password. Webster highlighted this site as it does not encrypt the information displayed to others through the calendar feature. As is the case with Mashable, a criminal could discover your full name, phone number, email address and the last four digits of your credit card.
Those responsible for the website have reported this summer that the problem is now fixed and that security measures are now applied to all communications.
Such poor security practices also occur on other e-commerce sites where companies and customers exchange more sensitive information. Research by the IT security consultants High-Tech Bridge showed that 73% of the top 100 online stores don’t use the HTTPS protocol for data they consider less sensitive, and only two of them apply it in all cases.
The same applies to apps running on mobile devices. In a recent study by HP, a group of IT experts analyzed the security measures in place on 2,107 apps and found that 75% of them do not encrypt stored data. Some 18% didn’t even encrypt data exchanged across the Internet.
Webster’s list of shame now has 19 names, many of these put forward by others who wanted to take part in the project. These names include Creative Cloud, VLC and Adobe Flash Player. Even the Tumblr microblogging site, where the HTTP Shaming page is hosted, doesn’t have a secure protocol. In the worst cases, the IT engineer has directly contacted companies to let them know the error of their ways.
Webster fails to understand why some companies are subjecting customers to unnecessary risks, as there is no reason not to use HTTPS, which is available to anyone offering services on the Internet.


2 comments
tried to buy global internet security for 44.95 for 3 devices but said that my credit card was not supported
Hello Mark. Please send an email to customer.service@pandasecurity.com Thanks!