Encryption is the process of converting readable information into a secret code to protect it from unauthorized access. Only individuals with the correct key can decrypt the data and restore it to its original form.
Cybercriminals are constantly searching for their next victim, and unfortunately, that could be you. In fact, the number of Americans affected by data breaches surged in the first half of 2024, rising 490% year over year. An astonishing 1,078,989,742 people were impacted, up from 182,645,409.
With data breaches happening all the time, protecting your personal information is essential. This is where encryption is essential. So what is encryption? It acts as a secret code to safeguard your sensitive data, ensuring it remains unreadable to anyone lacking the right key.
From your online banking to your social media accounts, encryption is like digital armor. But what exactly is encryption, and what does being encrypted mean? We discuss all the ins and outs of encryption, explaining why it’s crucial for your online safety and how you can benefit from using it.
What Is Encryption?
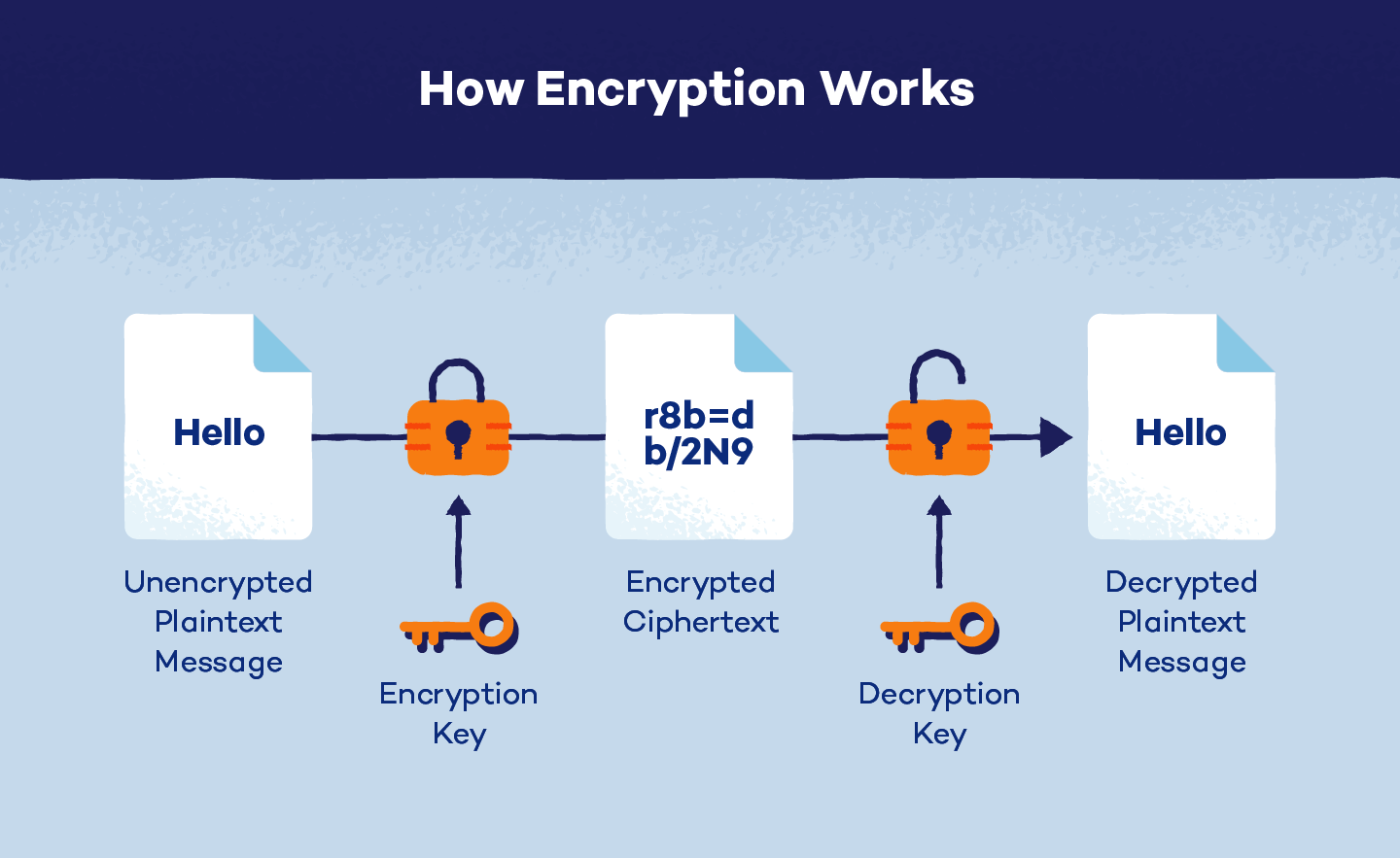
Encryption is the process of converting readable information (plaintext) into unreadable code (ciphertext). This is done using complex mathematical algorithms and a secret key. Only individuals with the correct key can decrypt the data and restore it to its original form.
Think of it as locking a box with a unique key; without the key, the contents remain inaccessible. In today’s digital world, where people constantly share sensitive information online, data encryption is crucial for protecting your data from unauthorized access.
How Does Encryption Work?
Encryption takes your readable data and scrambles it into something that looks like gibberish called ciphertext. Algorithms are the secret formulas used for encryption. Encryption algorithms are like the instructions for scrambling and unscrambling the data.
Many different algorithms are out there, such as Data Encryption Standard (DES) and Advanced Encryption Standard (AES), each with its own level of security and purpose.
So, there are two processes involved here:
- Encryption: Transforming plaintext into ciphertext using a key and an algorithm
Decryption: Converting ciphertext back into readable plaintext To decrypt data, you need a special key — unique codes that unlock the encrypted data. They can be short or long, and the length of the key determines how strong the encryption is. Longer keys are usually more challenging to crack.
Think of it like a physical key that opens a locked door. You need the correct one to unscramble the ciphertext back into readable plaintext.
So, the next time you send a secure email or make an online purchase, remember that encryption is working behind the scenes to protect your information.
Types of Encryption
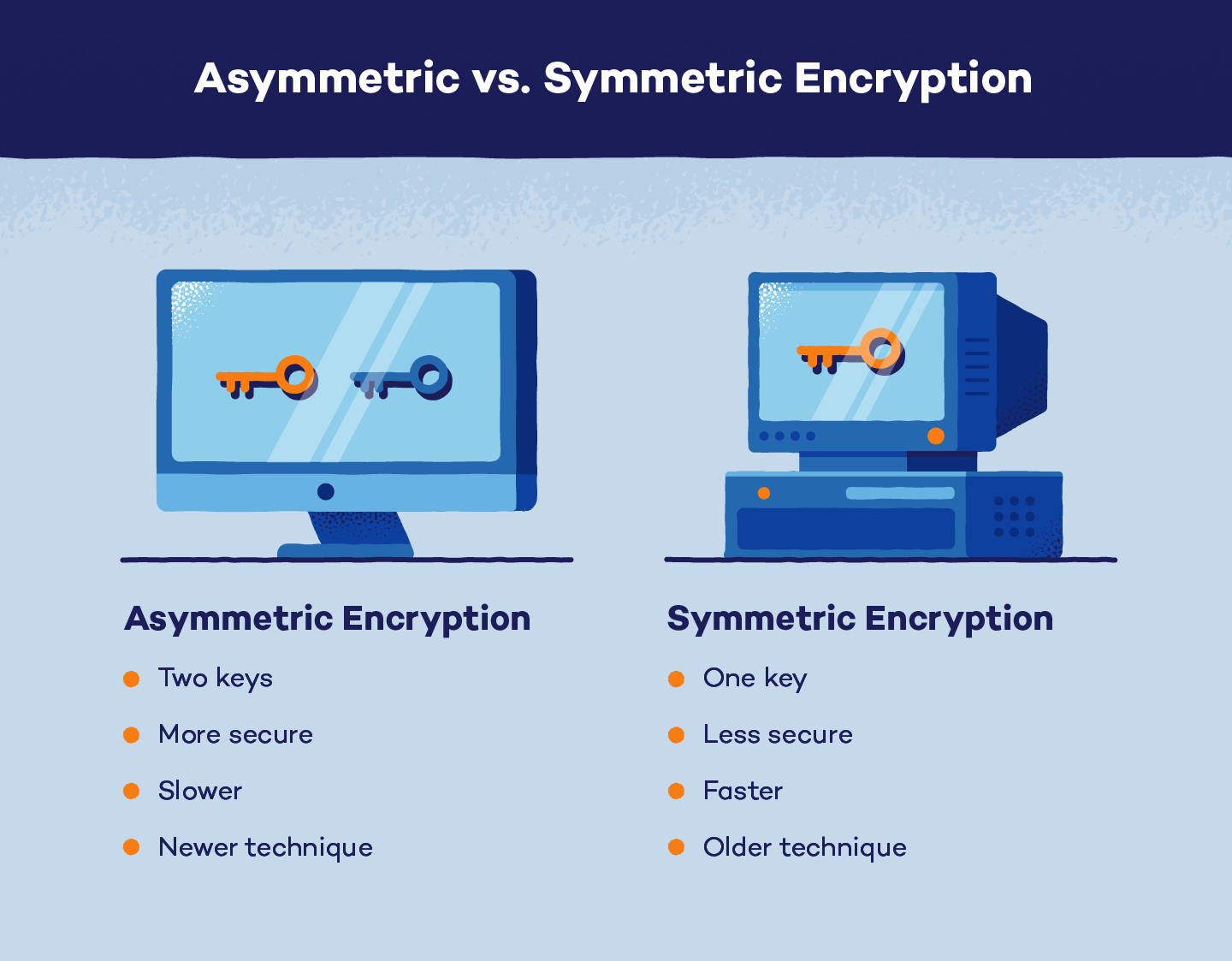
The two main methods of encryption are asymmetric and symmetric. While both encryption methods work in similar ways, the difference in the number of keys sets them apart.
Asymmetric Encryption
Asymmetric encryption, otherwise known as public key encryption or cryptography, relies on two different keys for encoding and decoding data. The public key encrypts the plaintext, turning the message into ciphertext. The private key decrypts ciphertext, returning it to plaintext.
The public key is available for anyone, but each private key is specific for that recipient. Since two different keys are required, asymmetric tends to be a more secure method of encryption. This is because the encoded message can only be decrypted with the private key. However, it is a slower process.
RSA is a common asymmetric encryption algorithm widely used in real-world applications. A common use case of this algorithm is securing information sent over the internet and collected by websites in SSL certificates, which create an HTTPS connection.
Symmetric Encryption
Symmetric encryption uses just one private key to encrypt the plaintext and decrypt ciphertext data.
Compared to asymmetric encryption, symmetric encryption is less secure, with only one key, and is quicker to run. Another disadvantage is that since there is only one secret key, all parties who need access to the plaintext message must exchange the key before decryption.
Some symmetric encryption algorithms, like DES, were outdated and replaced with AES and Triple DES. This form of encryption is often used in online payment applications and random number generation.
Why Encryption Matters
We hope (by now) you understand that encryption is more than just technical jargon; it’s a vital shield protecting your digital life. Here’s why it matters:
- Protects sensitive data from unauthorized access: Encryption acts as a digital lock, preventing hackers and cybercriminals from stealing your personal information, financial data and other sensitive details.
- Ensures privacy in digital communications: Whether you’re sending emails, messaging friends or making online purchases, encryption keeps your conversations and transactions confidential.
- Prevents data breaches and cyber attacks: Encryption significantly reduces the risk of data breaches and cyberattacks by making data unreadable to unauthorized individuals.
- Builds trust with customers and users: When businesses and individuals demonstrate a commitment to data security through encryption, it fosters trust and confidence.
Benefits of Encryption
Legend has it: Most people think encryption is just for big corporations and don’t bother about it. In truth, it’s a powerful tool for protecting your personal digital life, too. Here are some ways you can benefit from encrypted data:
- Protects personal data: From your online banking to your social media profiles, encryption safeguards your sensitive information from prying eyes.
- Secures online communications: Whether you’re emailing, messaging or video chatting, encryption ensures your conversations remain private. Remember that encryption message from WhatsApp at the beginning of a new chat?
- Prevents identity theft: By protecting your personal information, encryption makes it significantly harder for thieves to steal your identity.
- Enhances device security: If your phone or laptop is lost or stolen, encryption helps protect your data from falling into the wrong hands.
Potential Drawbacks of Encryption
While encryption is a powerful tool for protecting data, it’s not without its challenges:
- Loss of encryption key: In case you lose or forget the encryption key, the data becomes permanently inaccessible, even if you are the rightful owner.
- Increased system complexity: Implementing and managing encryption can be complex and requires specialized knowledge, potentially increasing costs and system overhead.
- Performance impact: Encryption can slow down system performance, especially for resource-intensive tasks.
- Potential for misuse: Bad actors can use encryption to conceal illicit activities, making it difficult for law enforcement to investigate crimes.
- Susceptibility to brute force attacks: While strong encryption algorithms are highly resistant, weak encryption methods can be vulnerable to brute force attacks (bad actors use a hit-and-trial system to guess your password).
- Ransomware risk: Malicious actors can target encrypted data in ransomware attacks, holding it hostage until a ransom is paid.
Common Encryption Algorithms
Several encryption algorithms exist for different circumstances. The most common algorithms are:
- Data Encryption Standard (DES): An original and less secure form of encryption rarely used today for protecting private information.
- Triple DES: The original DES method ran three times over to strengthen the encryption further. It uses three keys, each with 56 bits, and is most widely used in financial services.
- Advanced Encryption Standard (AES): Runs 128, 192 and 256-bit keys and is considered the most secure encryption algorithm currently available. AES is the trusted standard for the U.S. government and other private sectors.
- RSA: A public-key encryption algorithm standardly used for securing data shared via the internet. RSA is strong, reliable and popular.
- TwoFish: A fast and free encryption algorithm commonly used in hardware and software applications.
Each algorithm requires a specific number of keys to determine which type of encryption is in place.
Encryption is your digital bodyguard, protecting your sensitive information from the ever-growing online threats. By understanding the basics of how encryption works, you can make informed decisions about safeguarding your personal data. A little knowledge goes a long way in protecting your digital life.
In addition to your knowledge, tools like a VPN can help enhance your online security. A VPN adds an extra layer of protection by encrypting your internet traffic and masking your IP address. Prevent hackers from intercepting your data and protect your privacy online with Panda Dome VPN.
Encryption FAQ
Still have questions about encryption? We’ve got answers.
What Is an Example of Encryption?
An everyday example of encryption is sending a secure email. The content of your email is scrambled into an unreadable format using encryption. Only the intended recipient, with the correct decryption key, can read the message.
What Is a Key in Cryptography?
A cryptographic key is a piece of information, often a string of numbers and letters, used to encrypt and decrypt data. It’s essential for protecting information, as it acts like a digital lock and key.
Is Encryption Safe?
Modern encryption methods are highly secure when implemented correctly. Strong encryption algorithms like AES are virtually impossible to crack with current computing power. However, the security of encryption depends on factors like key length and user practices.
Can Hackers Access Encrypted Data?
While hackers can theoretically access encrypted data, breaking strong encryption is extremely difficult and often impractical. Use strong, unique passwords and keep your software up-to-date to protect against other types of attacks.
Do You Need to Encrypt Your Computer?
Encrypting your computer is highly recommended, especially if you handle sensitive information. It protects your data from theft or unauthorized access in case your device is lost or stolen.





