Cerber is a relatively new family of ransomware that has hit hard in the last few months. In this article, we want to take a look at some of the techniques it uses to infect its victims.
Chapter 2: Cerber
In my first article of this series I talked about the (ab)use of the Windows tool known as PowerShell to infect computers with ransomware. This can be done in a number of different ways, after all, PowerShell was named for a good reason: it is really powerful. One of the simplest ways to use it is by downloading a (malware) file and running it. Of course before getting there, PowerShell has to be executed, which can happen through some script, macros inside Office documents, or as a payload of some exploit. In the case of Cerber, most cases come from exploit kits.
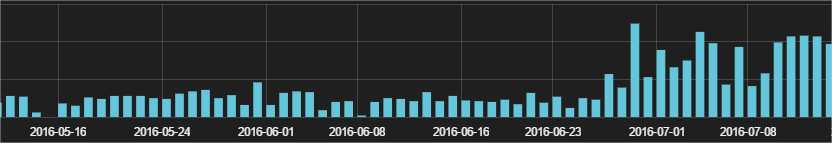
Due to all the information we have I can easily filter this kind of information. In the last 3 months we have blocked +3,000 infection attempts that were using PowerShell to download and run malware (ransomware):
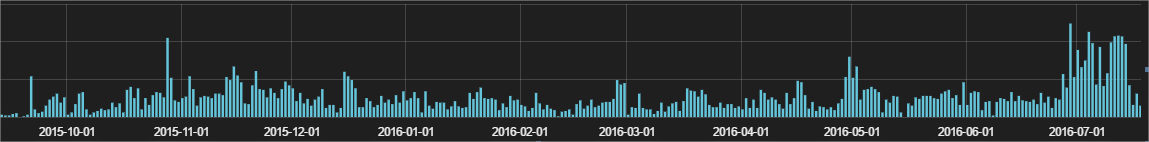
Taking a quick look they are Cerber, although there could be different ransomware families there (as long as we are blocking all infections we do not need to examine each of the binaries except for research purposes). Most of these attacks have taken place in the first weeks of July. If we move back to October of last year, we can see how this is indeed the biggest wave of infections using this particular technique in the last 10 months:
I have randomly selected a few hashes with the thousands we have blocked in case you want to play with them in your labs and protect your customers:
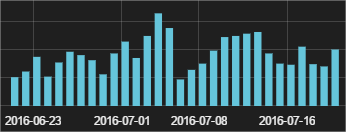
Another way to execute the malware to infect victims with Cerber rather relevant nowadays is through WMIC, the command line version of Windows Management Instrumentation (WMI). So far all the cases we are seeing are coming through exploits in computers running Internet Explorer. A malware sample is downloaded in the computer and instead of executing it right away, they use WMIC to execute it (trying to look like a legit behavior as WMIC is goodware that belongs to Windows operating system). So far we have blocked another +3000 infection attempts using this trick in the last 4 weeks:
This is a selection of some of the hashes of ransomware we have stopped during 3 days using this WMIC trick: