Hacktivism refers to cyber-activism, or the act of breaking into a computer system to wage an information war for political, social, religious, or anarchistic reasons. From protests and sit-ins to doxing and distributed denial-of-service attacks, hacktivism gained new authority with the rise of optical networking in 1996.
Proven to be powerful agents for change, virtual vigilantes known as hacktivists build and deploy hacking tools for an agenda’s greater good. More about disruption than disobedience, there have been countless instances of political and social change as a result of hacktivist campaigns. Here we explore what motivates hacktivists, how to prevent hacktivism and some of the most infamous hacktivist campaigns.
Jump to the full timeline of campaigns.
Hacktivism Explained
Hacktivism is a form of non-violent digital activism where the motive is not, primarily, personal financial gain. Instead, hacktivist campaigns aim to achieve political, social, or religious justice in line with the group’s cause. Hackers use tactics such as doxing, defacement, and denial-of-service to break into government or private organization systems.
Results are often scrutinized, and these agendas are carried out in the name of transparency claimed for the public good. Unlike typical hackers, these computer connoisseurs will often work in groups instead of alone. In the name of anonymity, these groups are typically fashioned as a decentralized network of individuals around the world.
Hacktivism Goals
Generally, hacktivists are referred to as “ethical hackers” or “white hat hackers” and are motivated by justice and the common good. Hacktivists will often attempt to accomplish one of these nine goals:
- Stop the financing of terrorism, including terrorist acts and groups
- Evade censorship laws
- Vocalize disagreements about ongoing and potential war
- Lift up those whose rights are threatened or violated, usually through the use of social media
- Move local and political upheavals forward by hacking websites or speaking against government systems
- Support freedoms, including the freedom of speech
- Promote access it online information by breaking down government firewalls
- Discredit the authority of large organizations like the government
- Help immigrants cross borders to safety
What Does Hacktivism Target?
Hacktivists carry out data breaches for more than monetary gain. Instead, their distinct agendas wage informational wars in political, social, religious, or anarchist ways.
- Political: Hacktivism as a form of political mobilization aims to lean or sway the population to the hacker’s agenda.
- Social: Social justice in hacktivism aims to bring about societal change.
- Religious: Hacktivism for a religious agenda aims to recruit or disavow a religious entity.
- Anarchist: Hackers can have an anarchist agenda to access or control civil infrastructure, military equipment, or the general population.
7 Types of Hacktivism
Hacktivists use a variety of hacking techniques in order to reach their goals, and anonymity is important in every type.
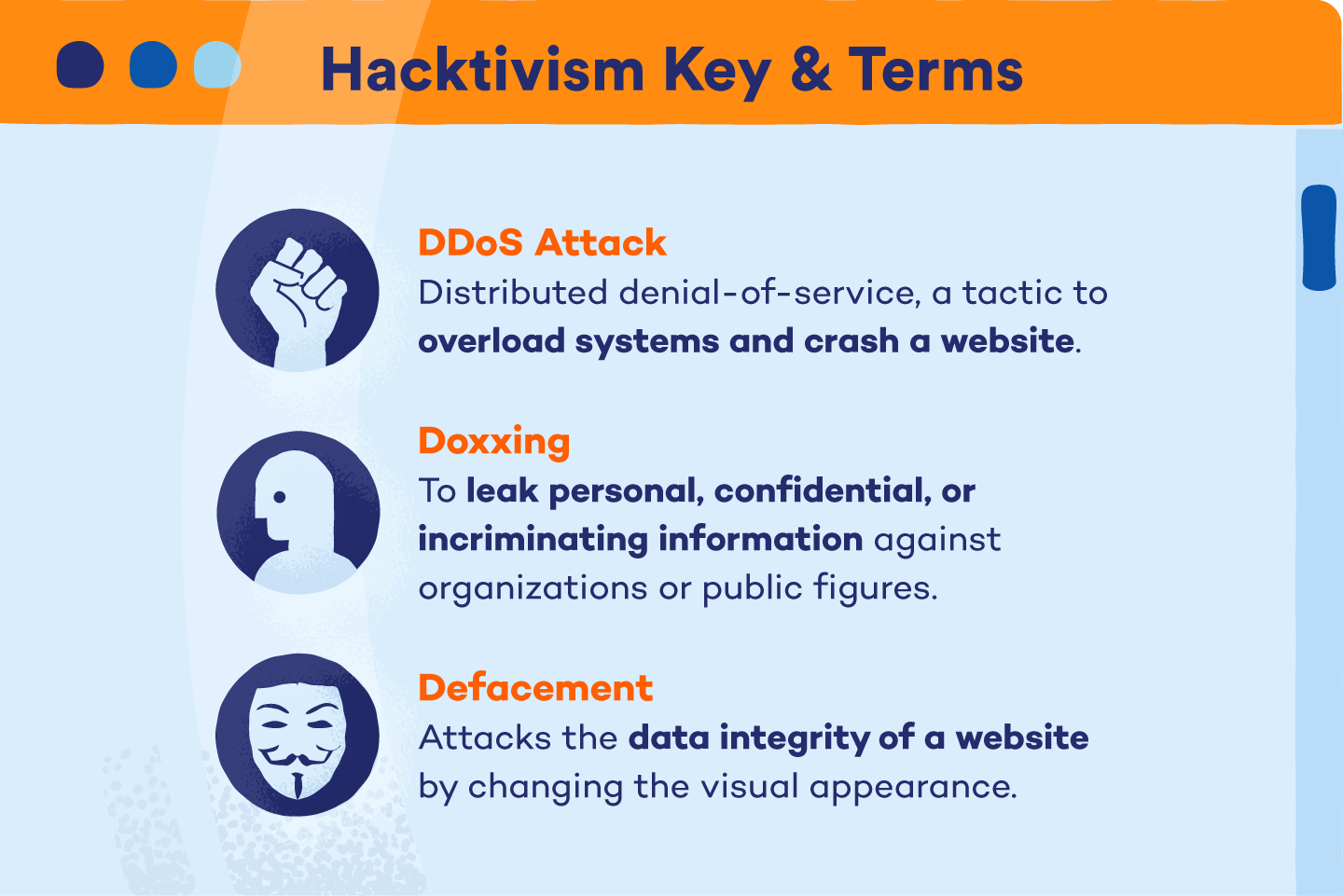
- Doxing: Doxing exposes personal and identifiable information about a specific person or group to the public.
- Anonymous blogging: Used frequently by whistleblowers and journalists, this type of hacktivism publicly exposes certain issues or information while protecting the source.
- DoS and DDoS attacks: Denial-of-service attacks, like smurf attacks, flood networks in order to prevent and disrupt system access.
- Informational leaks: Informational leaks use insider sources to make incriminating information public.
- Geo-bombing: In social and political videos, geo-bombing makes the hidden location of an image known.
- Website mirroring: Website mirroring replicates a real website with a slightly different URL in order to evade censorship laws.
- Code Changing: By changing the code of a website, hacktivists can personalize website content and deface the site’s appearance to fit the message of their own agendas.
5 Tips to Prevent Hacktivism
Being aware of what hacktivism is, what it targets, and the goals of hacktivists is the first step to preventing a data breach. After these initial steps are taken, these five tips can help you prepare even more effectively.
- Train users on cybersecurity practices: Infrastructure users should understand cybersecurity practices, where sensitive information is stored in their systems and how to safely protect or dispose of it.
- Perform regular vulnerability assessments: Vulnerability assessments review infrastructures for potential weaknesses and provide steps for analysis, prioritization, and remediation.
- Use multifactor authentication systems: Multifactor authentication systems can help protect against faulty or weak log-in credentials.
- Implement security software: Antivirus software provides an additional level of protection to information systems.
- Create and support protection procedures: After weaknesses are identified, security software is in place, and multifactor systems are in use, it’s important to create and support procedures to follow in the event of a data breach.
Even if you or your organization has little to fear from hacktivists, these are important safety precautions to consider.
Prominent Hacktivist Groups
There are a variety of hacktivist groups around the world that target corporations, governments, and religious organizations, but there are a few major, well-known hacktivist groups that set the stage for what hacktivism is today.
- Anonymous: Anonymous, or Anon, is arguably the most notable hacktivist group in the world. They formed in 2008 and rose to prominence following their attacks on the Church of Scientology.
- LulzSec: Members of Anonymous joined together and formed LulzSec in 2011. This organization specializes in information dumps.
- WikiLeaks: Founded in 2006, Wikileaks is a whistleblower site that is well-known for leaking classified and sensitive information.
- Legion of Doom (LOD): From the 1980s to the 2000s, LOD was legendary on computer networks for confidential information sharing.
- Masters of Deception (MOD): MOD was established to mock LOD, but soon became a notable name in the cyberwar sphere in the 1990s.
- Chaos Computer Club: Originating in 1989, Chaos Computer Club is one of the earliest known hacktivist groups. This group focuses mainly on Germany’s information systems and has since its inception.
6 Most Infamous Campaigns by Influential Hacktivist Groups
Unlike traditional activism, hacktivism is often anonymous. However, even with an anonymity component, hacktivism has influenced a variety of political, social, and religious situations. Although not an exhaustive list, these are six of the most infamous campaigns that have shaped hacktivism in the past century. More influential campaigns are covered in the timeline below.
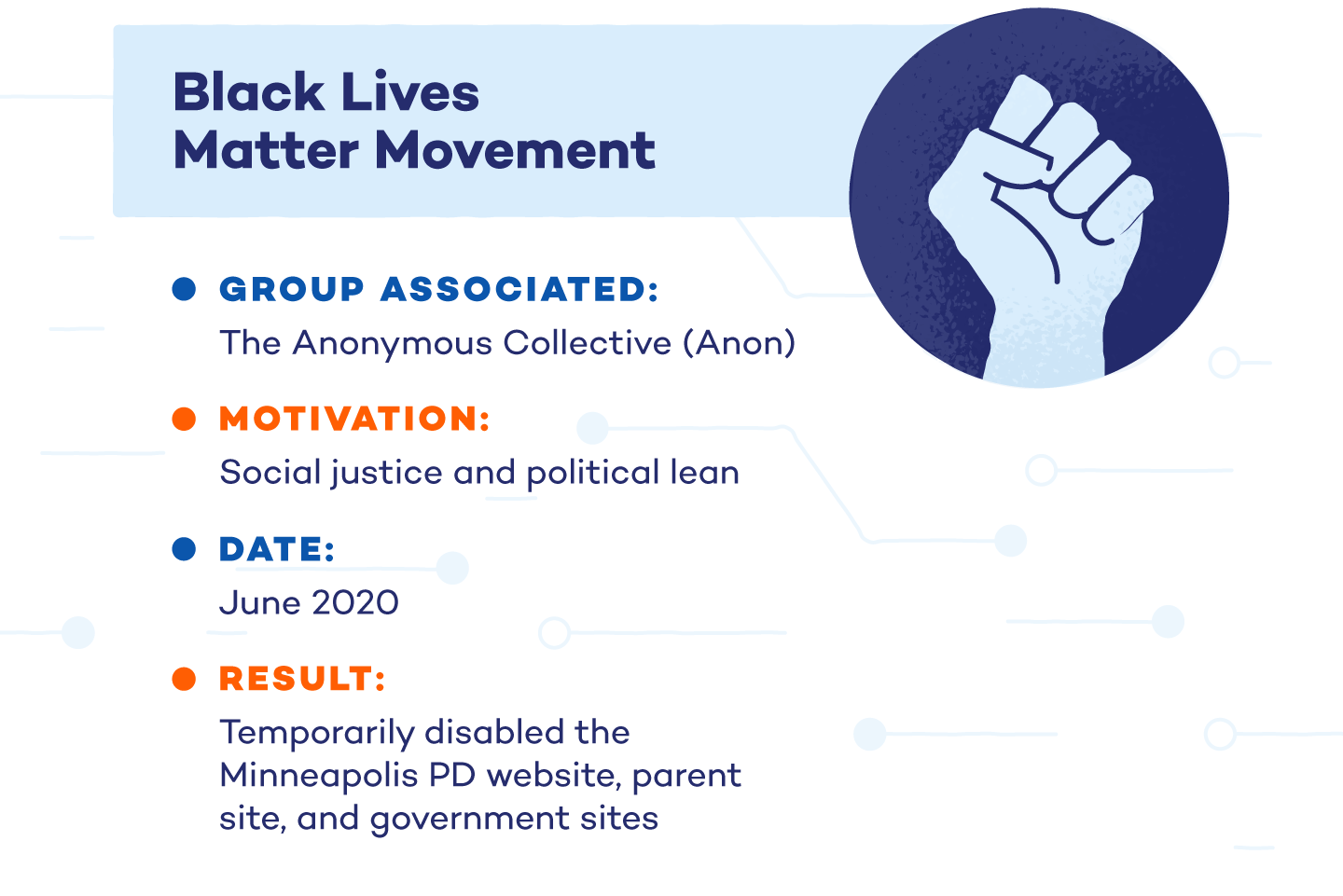
1. Black Lives Matter Movement
Anonymous was silent for years following the relaunch of Operation Darknet in 2017. That is—until the group spoke out against police corruption following the death of George Floyd. The group has raised similar condemnations of police brutality in the past, following the deaths of Michael Brown and Tamir Rice.
The Purpose
In support of the major social and political movement Black Lives Matter, the group released a video on Twitter specifically criticizing the Minneapolis police department. This attack was enacted to support freedoms, move a political upheaval forward, and lift up those whose rights were threatened.
The Result
Anon’s Twitter account exploded in popularity, with an influx of 3.5 million new followers in the days following the video. At the time, the campaign consisted of a series of DDoS attacks that briefly shut down the Minneapolis police department website, its parent website, and the Buffalo, New York, government site over the course of a weekend.
2. Collection of Clinton Emails Leaked
WikiLeaks, founded and directed by Julian Assange, released a series of emails from the Democratic National Committee (DNC) acquired by a group of Russian hackers in GRU in 2016. Previously, they had released everything from documented corrupted investigations to the manual of operations at Guantanamo Bay.

The Purpose
In order to protect the freedom of speech and media publishing, WikiLeaks leaked a collection of emails between Hillary Clinton and her campaign manager. Said to have originated from Russian hackers, these emails were released to promote societal transparency, decrease disruption, and further the campaign in Donald Trump’s favor.
The Result
Hackers sent spear-phishing emails to employees of the Clinton campaign to steal the credentials of DNC members. The leaked emails significantly affected the Clinton campaign, and many have attributed them to her resulting loss. Following the leak, the Department of Justice indicted 12 Russian hackers for the incident.
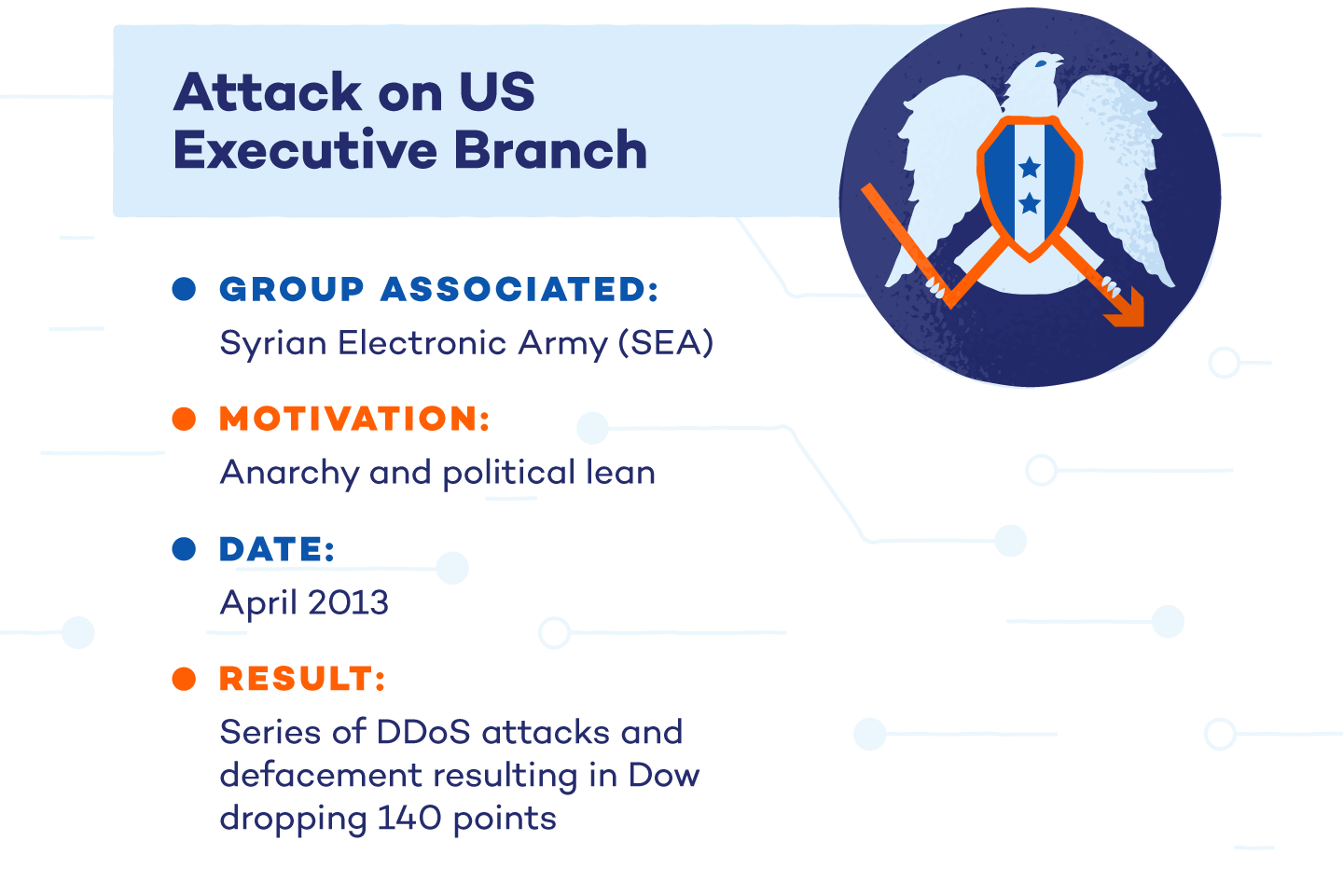
3. Attack on US Executive Branch
Allegedly associated with Syrian President Bashar al-Assad, the Syrian Electronic Army (SEA) has carried out operations using spear-phishing and DDoS attack tactics to compromise government, media, and privately-held organizational websites. In 2016, the FBI charged two individuals affiliated with the SEA with criminal conspiracy.
The Purpose
The goal of SEA, and this particular political anarchy attack, is to deny rumors of support concerning the Syrian uprisings and compromise computer systems and organizations deemed as a direct threat to the Syrian government. SEA also aims to collect information on Syrian enemy countries.
The Result
The group infiltrated U.S. government media and private-sector organizations to steal credentials and perform DDoS and defacement attacks. The group successfully released a false tweet about an explosion in the White House that claimed to injure the President. The Dow briefly dropped 140 points after the tweet went live.
4. Project Chanology
Anonymous performed a DDoS attack on the Church of Scientology after the church attempted to remove a video of Tom Cruise voicing his affiliation with the organization. In-person protests followed with attendees wearing the infamous Guy Fawkes masks around the country.

The Purpose
Project Chanology attempts to combat web censorship. This campaign was a protest against the Church of Scientology and its members.
The Result
The campaign ran DDoS attacks to prevent access to the church’s websites. A series of prank calls and black faxes followed. Anon further exercised doxing by distributing private documents stolen from Scientology computers over the Internet.
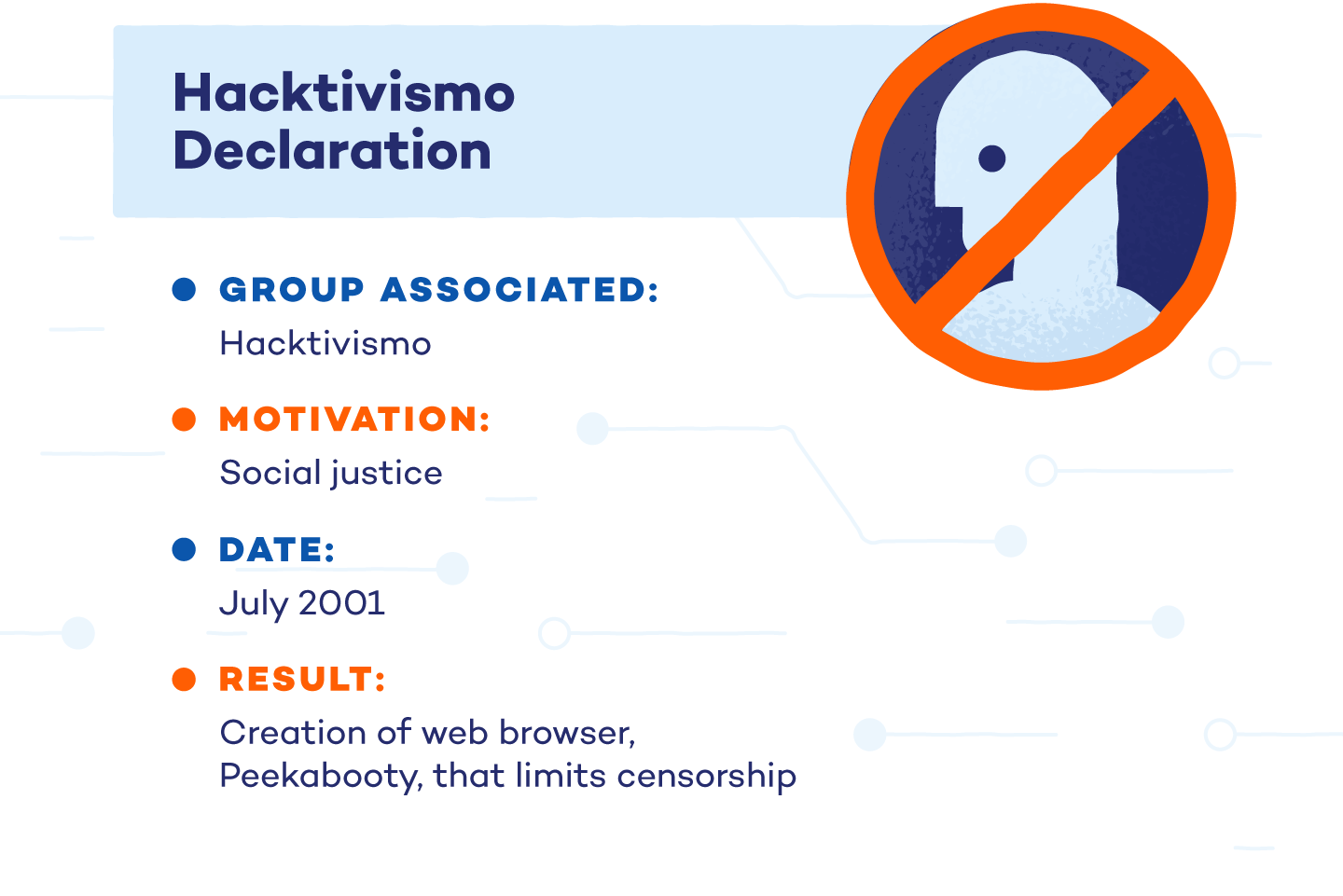
5. Hacktivismo Declaration
In its first public act of hacktivism, Hacktivismo released a declaration that elevated freedom of speech. The group — connected with another hacker group, Cult of the Dead Cow (cDc) — attempted to not only engage in civil disobedience but explain the reasons behind its attacks.
The Purpose
Hacktivismo wrote and released a declaration that cites the International Covenant on Civil and Political Rights and the Universal Declaration of Human Rights. The group’s purpose was to elevate information to the level of human and political rights.
The Result
The campaign created moral and legal grounds for future hacktivism campaigns. They also released Peekabooty, a web browser that prevents censorship from nation-states that deny web access.
6. Worms Against Nuclear Killers
Believed to have been created by Melbourne-based hackers, “Electron” and “Phoenix”, W.A.N.K was the first glaringly apparent hacktivism attempt. At the time of its campaign, there was a hugely anti-nuclear sentiment in the country which fueled the attack.
The Purpose
The Realm created this attack as an anti-nuclear protest. Days before a NASA launch, the group attempted to shut down the DECnet computer network with a worm that defaced the devices.
The Result
The campaign consisted of two worms, W.A.N.K and OILZ, which contained bugs that prevented access to accounts and files and changed passwords. The worm exploited weak security in the system, identifying accounts that had passwords identical to the username.
A Timeline of Hacktivism
The term “hacktivism” was coined in 1996 by Omega, a member of the early hacktivist organization Cult of the Dead Cow. Although this new name solidified the importance of these events in history, it wasn’t the first instance of cyber-activism. In this timeline, we explore major events during the evolution of hacktivism in the last century.
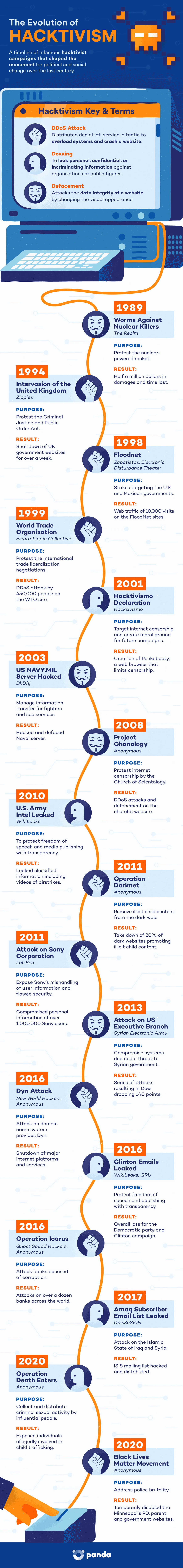
So, what is hacktivism, then? Some may say it’s the selfless acts of heroes and vigilantes. Others may argue it’s simply cybercriminals performing digital attacks behind the mask of online anonymity. In either regard, it’s clear that hacktivism has and will continue to have an enormous effect on the political, social, and religious realms.
Sources: Journal of Human Rights Practice | Science Direct | First Monday | UCLA Law | Google Scholar | AS USA | TEDx | Department of Justice | Research Gate | AI Time Journal | TechShielder






