A Smurf attack is a cyberattack where a hacker tricks devices into sending unwanted traffic to a target, overwhelming it.
Ever experienced your internet being overloaded with useless traffic, making everything slow or crashing altogether? That’s what a Smurf attack feels like for a computer network.
A Smurf attack is a distributed denial-of-service (DDoS) attack in which an attacker floods a victim’s server with spoofed Internet Protocol (IP) and Internet Control Message Protocol (ICMP) packets. As a result, the target’s system is rendered inoperable. This type of attack gets its name from a DDoS.Smurf malware tool that was widely used in the 1990s. The small ICMP packet generated by the malware tool can cause significant damage to a victim’s system, hence the name Smurf.
While Smurf attacks aren’t as common today, understanding how they work can help protect you from similar online threats. We will break down Smurf attacks, explaining what they are, their types, how they work and how to stay safe.
Smurf Attack Example
Think of a trickster (the DDoS.Smurf malware) calling an office (the IP broadcast network) while masquerading as the company’s CEO.
In our example, the trickster asks a manager to tell every employee to return his call (the ICMP echo requests) on his private number to give a project status update — but the private number (the spoofed IP address) actually belongs to the trickster’s targeted victim. As a result, the victim receives an onslaught of unwanted phone calls (the ICMP echo replies) from each employee in the office.
How Does a Smurf Attack Work?
Smurf attacks are similar to a form of denial-of-service (DoS) attacks called ping floods, since they’re accomplished by flooding a victim’s computer with ICMP echo requests. Here’s how a Smurf attack works:
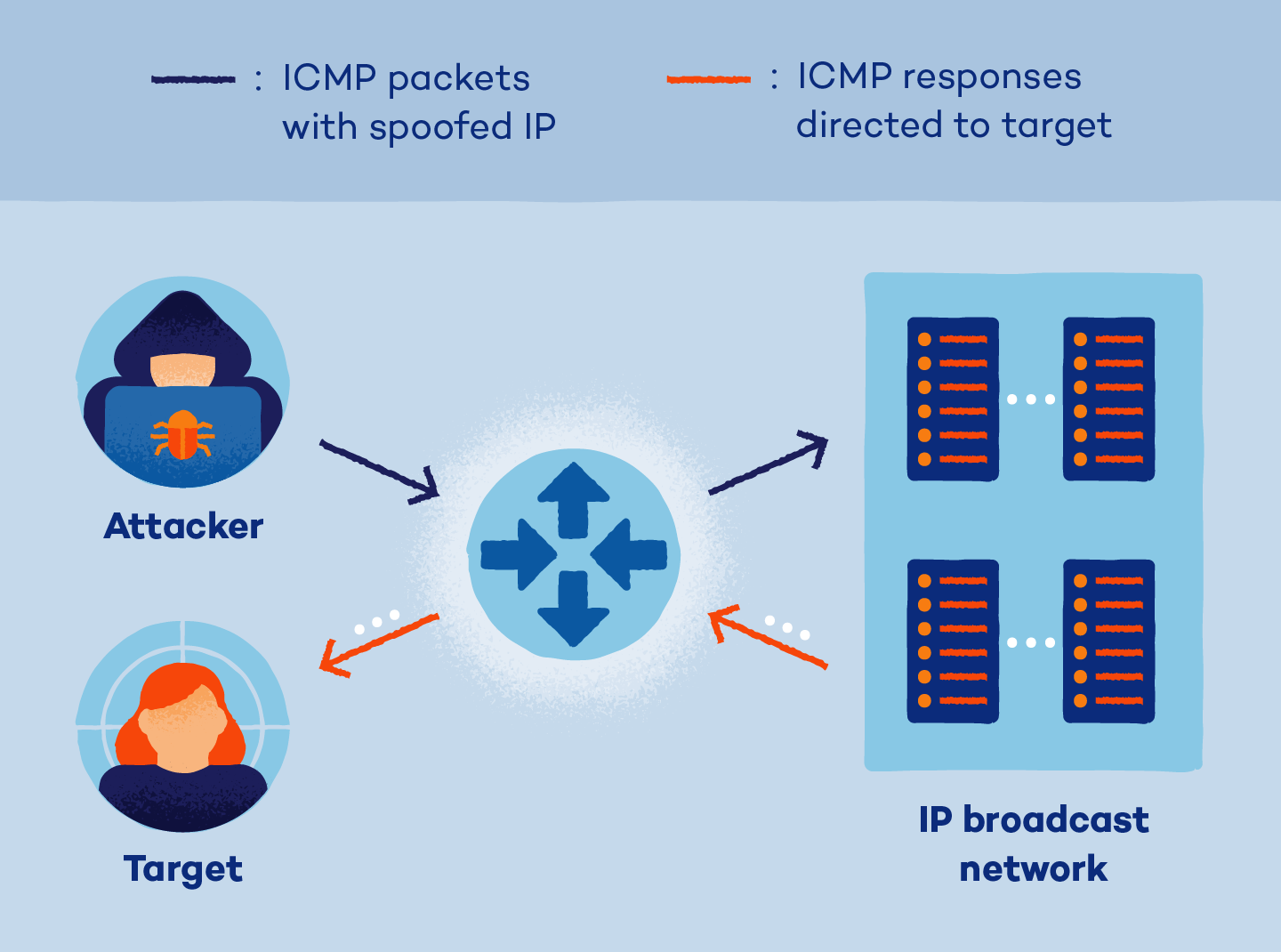
- Attacker locates the target’s IP address: An attacker identifies the target victim’s IP address.
- Attacker creates spoofed data packet: Smurf malware is used to create a spoofed data packet, or ICMP echo request, that has its source address set to the real IP address of the victim.
- Attacker sends ICMP echo requests: The attacker deploys ICMP echo requests to the victim’s network, causing all connected devices within the network to respond to the ping via ICMP echo reply packets.
- Victim is flooded with ICMP replies: The victim then receives a flood of ICMP echo reply packets, resulting in a denial-of-service to legitimate traffic.
- Victim’s server becomes overloaded: With enough ICMP reply packets forwarded, the victim’s server is overloaded and potentially rendered inoperable.
Types of Smurf Attacks
Smurf attacks are generally categorized as basic or advanced. The only difference in the type of attack is the degree of the attack that takes place.
Basic
Imagine a prankster sending thousands of postcards with your return address to a single random address. A basic Smurf attack works similarly. The attacker finds the victim’s IP address and exploits network vulnerabilities to send a massive wave of ICMP “ping” requests (like digital echoes) to the victim’s network’s broadcast address.
These requests appear to come from the victim, tricking every device on the network to respond with a reply. This flood of replies overwhelms the victim’s device, potentially crashing it.
Advanced
An advanced Smurf attack takes this concept further. Now, the prankster is sending postcards with your address and also including additional addresses on the postcards as targets. It starts like a basic attack, but the attacker manipulates the “ping” requests to include multiple victim IP addresses.
When devices on the initial target network respond, the replies are also directed at these additional victims. This creates a domino effect, overwhelming not just the original target but also the unsuspecting additional victims bombarded with unexpected traffic.

Consequences of a Smurf Attack
While the goal of a Smurf attack is to render a victim’s system useless for hours or even days, it can also be the first step toward more harmful attacks like data theft or identity theft. Either way, the consequences of a Smurf attack remain:
- Revenue loss: A company server that’s inoperable for hours or days on end often means a halt in business operations, resulting in lost revenue and frustrated customers.
- Data theft: Attackers can gain unauthorized access to the data on the victim’s host server during an attack.
- Reputational damage: If your clients’ confidential data is leaked after an attack, it can lead to a permanent breach of their trust and loyalty to your organization.
Smurf Attack Prevention: How to Protect Yourself
Mitigating a Smurf attack comes down to securing your network, which begins with your router. To protect yourself, you’ll need to configure how your routers and devices interact with ICMP packets. This involves five important prevention steps:
- Disable IP broadcast address responses: This setting prevents your network devices from replying to messages sent to a general broadcast address. It’s like stopping your mailbox from accepting mail addressed to “Everyone on This Street.”
- Rate limit ICMP traffic: This helps you set a limit on the number of ICMP requests (pings) your network can receive within a specific timeframe. Think of it like having a security guard at your mailbox who only allows a certain amount of mail per hour.
- Employ network firewalls: Firewalls act as security guards for your network traffic. You can configure them to identify and block suspicious ICMP traffic patterns that might indicate a Smurf attack.
- Configure anti-spoofing rules: These rules prevent devices on your network from disguising their IP addresses as someone else’s. It’s like requiring everyone sending mail to use their real address, making it harder for attackers to spoof the victim’s IP.
- Keep network devices updated: Outdated software can have vulnerabilities that attackers exploit. Regularly updating your router and other network devices ensures they have the latest security patches to defend against known attack methods.
If your current router is an older model, we recommend investing in a new one since newer models usually come with the above configurations already in place by default. In addition, consider using antivirus and anti-malware solutions to secure your firewalls and add an extra layer of protection to your network.
As with most cyberattacks, prevention is often the best strategy for protection. While Smurf attacks are nothing new, they remain a common tactic among cybercriminals looking to exploit vulnerable networks. To further protect yourself from all kinds of cyberattacks, consider installing a trusted antivirus software program to keep all your devices secure.
Smurf Attack FAQ
Now that questions like how a Smurf attack operates and why we call it a Smurf attack are clear, let’s answer some more frequently asked questions about the attack to help you protect yourself from them.
What’s the Difference Between a Smurf Attack and a DDoS Attack?
A DDoS attack aims to prevent victims from accessing their network by flooding it with fake information requests. A Smurf attack is a form of a DDoS attack that renders a victim’s network inoperable in a similar way, but the difference is that it does so by exploiting IP and ICMP vulnerabilities. Exploiting these vulnerabilities is what sets a Smurf attack apart, in turn increasing the potential for damage.
What’s the Difference Between a Smurf Attack and a Fraggle Attack?
Both a Fraggle attack and a Smurf attack are forms of a DDoS attack that aim to flood a victim’s system with fake information requests. The difference is that while a Smurf attack uses spoofed ICMP packets, a Fraggle attack uses spoofed User Datagram Protocol (UDP) traffic to achieve the same goal. Everything else about these attacks is the same.
What Is a Smurf Attack Amplifier?
A Smurf attack amplifier is a component of Smurf attacks that increases their damage potential. The amplification factor correlates to the number of hosts on the victim’s IP broadcast network.
For example, an IP broadcast network with 300 hosts will yield 300 responses for every fake ICMP echo request. This enables an attacker with low bandwidth to successfully disable a victim’s system, even if that system has a much higher bandwidth. Smurf amplifiers can be deployed as long as the attacker maintains a connection and the amplifiers are broadcasting the ICMP traffic.





