IMPORTANT INFORMATION YOU MUST READ BEFORE YOU START! ATTENTION! If you only see a single device in the web UI, you must repeat the process, rebuild the gold image and deploy it again to the affected endpoints as soon as possible. For any questions, contact Technical Support. |
Introduction
In large networks with many similar computers, you can automate the process to install the operating system and other software with a gold image. This is sometimes referred to as a master image, base image, or clone image. You then deploy the gold image to all computers on the network, which eliminates most of the manual work required to set up a new computer.
To generate a gold image, install an up-to-date operating system with all the software that users might need, such as security tools, on a computer on your network. Once the computer is ready, you need to use virtualization software to "seal" the installation and distribute it to the computers on the network. For information specific to your virtualization solution, consult your vendor's documentation.
The installation procedure requires the preparation of a template (for persistent environments) or a gold image (for non-persistent environments) that will be later deployed to the virtual computers on the network.
In persistent environments, information stored on the computer's hard disk persists between reboots. Therefore, you must install an updated version of the operating system with all the programs that users need and then create the template with your product protection updates configured.
In non-persistent environments, two security configuration profiles will be created; one to update the gold image when it is prepared and for maintenance purposes, and one to disable updates when the gold image is running, as it is not appropriate to update the client software when the computer's storage system reverts to its original state with each reboot.
This article offers a step-by-step walkthrough of how to install Panda Security solutions for Windows on Aether platform in persistent and non-persistent Virtual Desktop Infrastructure (VDI) environments. Due to their characteristics, virtual computers or instances require you to follow a specific procedure to ensure that the images or templates to be used in virtual environments are up to date, and don't have a previously assigned machine ID so that, when a virtual computer is started, it is uniquely registered in the Web UI.
It is very important to follow this procedure closely to:
- Ensure engine and knowledge updates.
- Optimize resource and bandwidth consumption in non-persistent environments.
- Ensure virtual instances are uniquely identified.
Prerequisites
- In persistent environments, computers must have fixed MAC addresses.
The computer used to generate the template or gold image must have an Internet connection. - Endpoint Agent Tool for Windows must be run as administrator and has a graphic interface but can also be run from the command line.
If you run the tool from a .bat or .cmd file, you must use this command: start /wait "".
For example, if the instruction is: EndpointAgentTool.exe /sg, this is the command you must type:
start /wait "" "C:\Path\EndpointAgentTool.exe" /sg
Compatibilities
Generally, the procedure described in this document works with the following types of virtual machines:
- VMware Workstation
- VMware Server
- VMware ESX
- VMware ESXi
- Citrix XenDesktop
- XenApp
- XenServer
- MS Virtual Desktop
- MS Virtual Servers
Click on the + sign to see the instructions of each phase.
- Install or update the operating system with the user's applications.
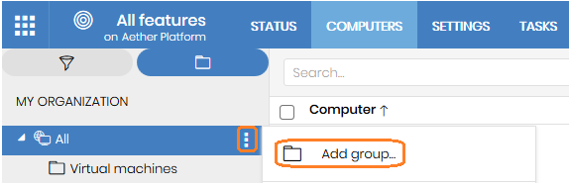
- From the Aether platform, create a group called Virtual machines to host the template and the virtual machines. To do so, follow these steps:
- Click on the Computers tab.
- Select My organization from the left pane.
- Select Add group.
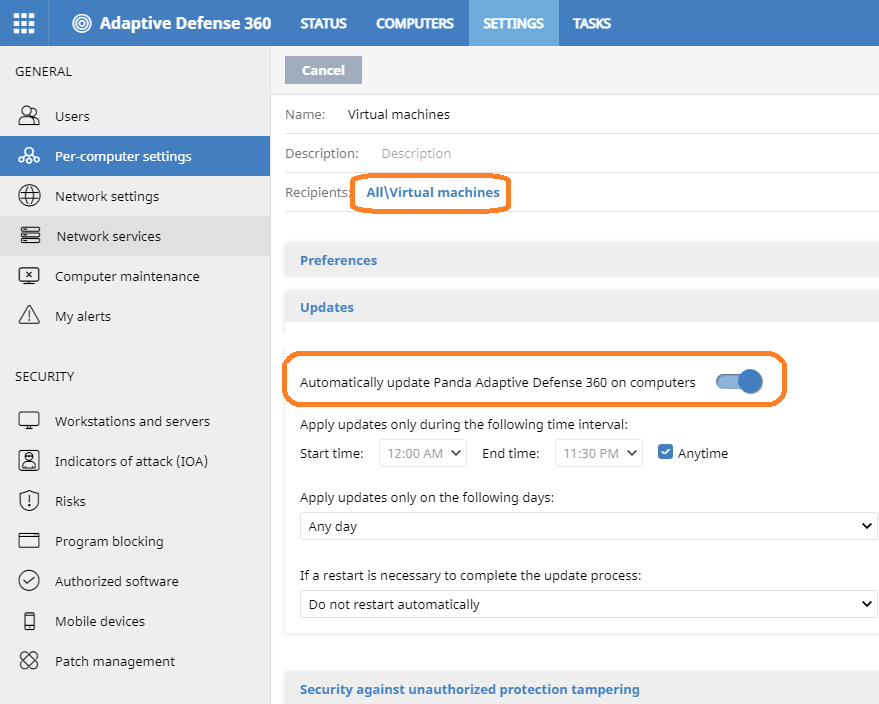
- Create a settings profile with automatic Agent and Adaptive Defense 360 updates. To do so, follow these steps:
- Click on the Settings tab.
- Select Per-computer settings from the left pane.
- Click Add and to create a settings profile that will ensure the image is updated.
- Make sure the Automatically update Panda Adaptive Defense 360 on computers toggle is enabled.
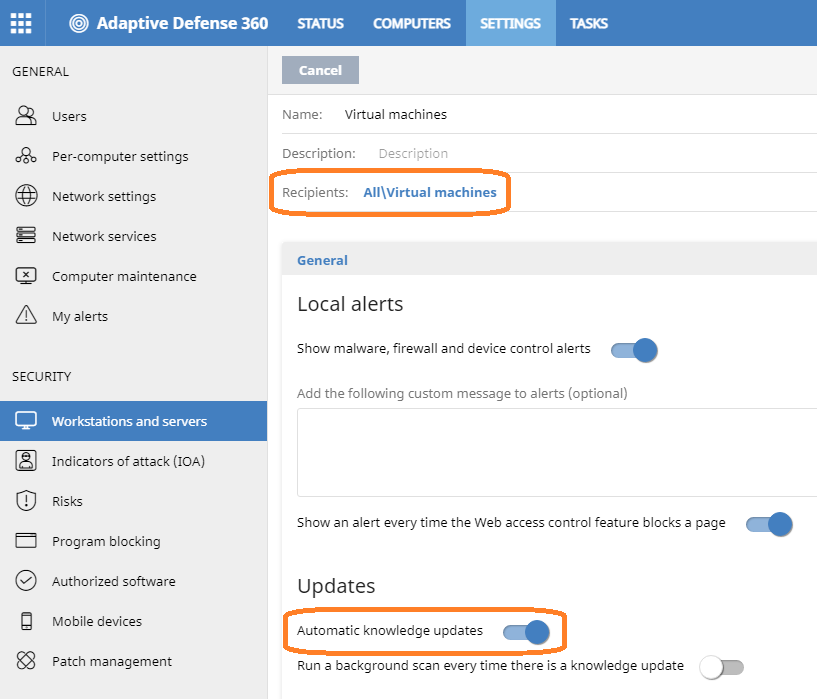
- Assign these settings to the Virtual machines group you created earlier for the template.
- Select the Settings tab and select Workstations and servers on the Security left pane.
- Click Add to create a new profile with automatic Knowledge updates enabled and type a name and description if required.
- Select General and enable the Automatic Knowledge Updates toggle.
- Assign these settings to the Virtual machines group.
- Install the agent and the protection on the Virtual machines group:
- From the top navigation bar, select Computers, select the Virtual machines template group and click on Add computers to download the installer.
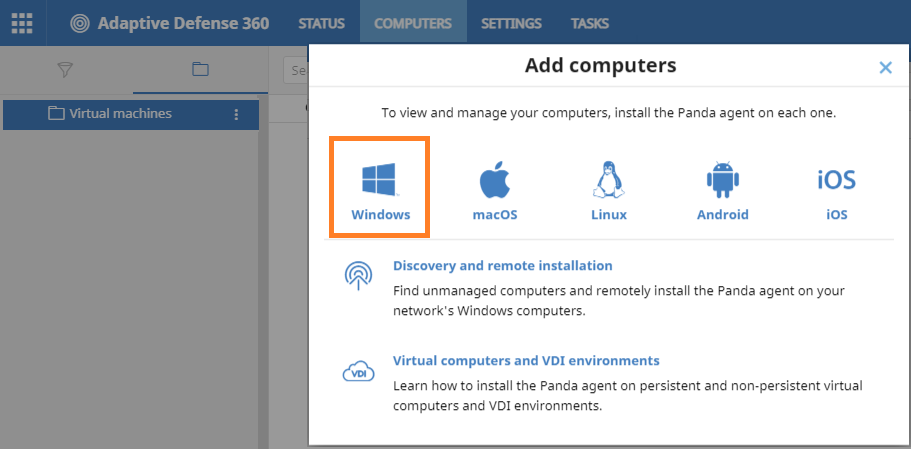
- Install the agent on the template and wait for the progress window to finish.
During that time, the protection will be automatically installed, configured and updated. After the installation is completed, the computer will appear on the list of protected computers in the Web UI, with a green icon. The computer's protection and knowledge will be updated.
- From the top navigation bar, select Computers, select the Virtual machines template group and click on Add computers to download the installer.
- Download the Endpoint Agent Tool for Windows, unzip it and run it on the computer with the template.
- In the Non exclusive events section, select Detections, Counters and Check commands and click Send, or else, right-click on the protection icon and select Synchronize.
If you do it from the command line, type in: EndpointAgentTool.exe /d /c /cmd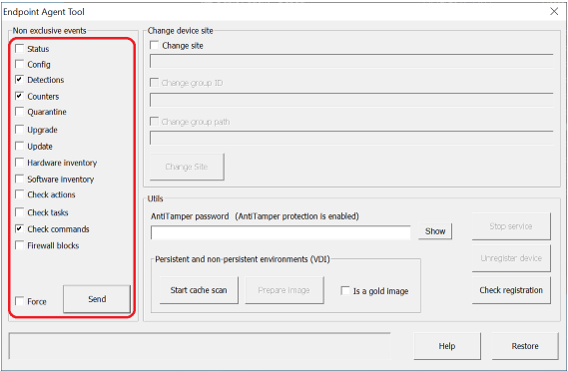
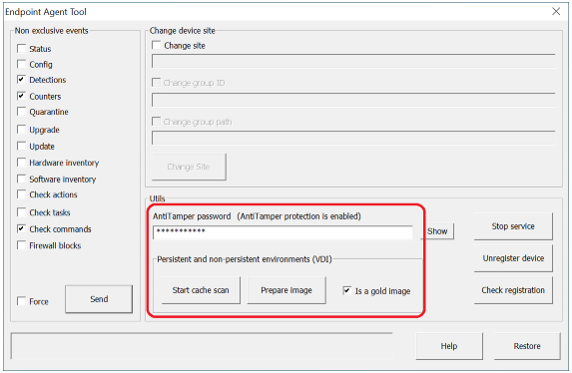
- Remove the computer's ID. To do so, leave the Is a gold image checkbox unchecked.
- If the computer is protected with Anti-Tamper, enter the password in the AntiTamper password field.
If you use the command line, type in:
EndpointAgentTool.exe /pei /atp:antitamperpassword
If there is no password, do not add the atp parameter. - Click on the Prepare image button.
This removes the agent ID from the template, so that all virtual machines obtain their ID when they connect to Aether for the first time.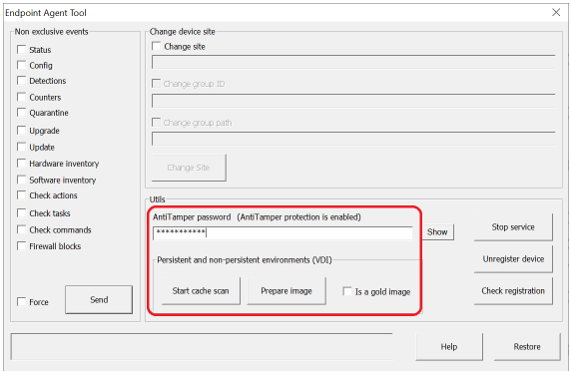
- In the Non exclusive events section, select Detections, Counters and Check commands and click Send, or else, right-click on the protection icon and select Synchronize.
- ATTENTION! Disable the Panda Endpoint Agent service so the service does not start automatically before the template is created for your virtual instances.
This step is critical to ensure that each virtual machine is uniquely identified in the Web UI. - Access the virtual environment management tool and generate the template. If you have questions about this step, contact your vendor.
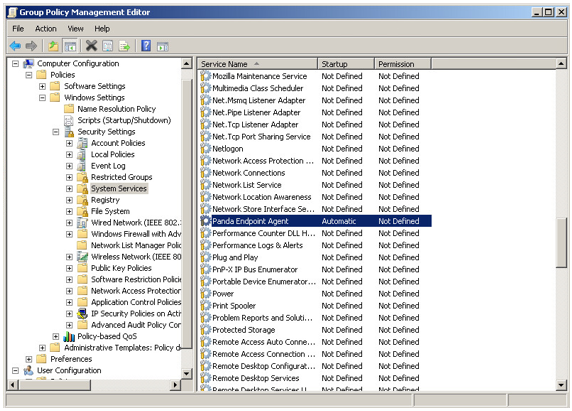
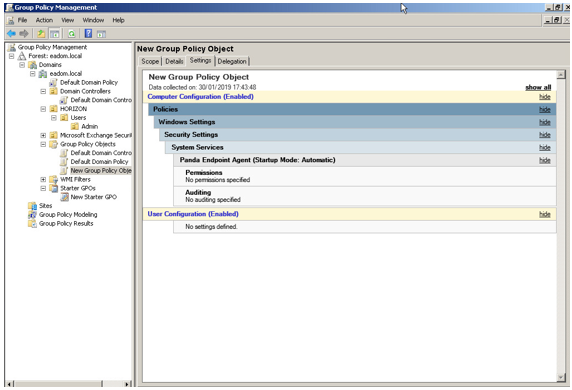
Once the custom template is ready, you can enable the Panda Endpoint Agent service, either with GPO policies for devices within a domain, or through other types of script applications such as Horizon, Windows Logon Scripts, etc. In this example, we explain how to change the Panda Endpoint Agent service's startup type, using GPO. First, you must create a GPO.
In the GPO settings, go to the following path: Computer Configuration, Policies, Windows Settings, Security Settings, System Services, Panda Endpoint Agent. The service will be disabled. Change the status to Automatic. The service will start automatically on the next reboot and will be integrated in the console.
Click on the + sign to see the information of each phase.
Before you create the gold image, prepare the computer where you are going to create it:
- Install/update the operating system with the user's applications.
- From the product's console, create a group where you will host the gold image (Gold group or template image) and the virtual computers (Virtual machines group).
- Gold or Template image Group
- Go to the Settings tab, click Per-computer settings and create a settings profile for future image updates.
- Make sure the Automatically update Panda All features on computers toggle is enabled.
- Select the Automatically Restart both workstations and servers option to make sure the computer will be updated.
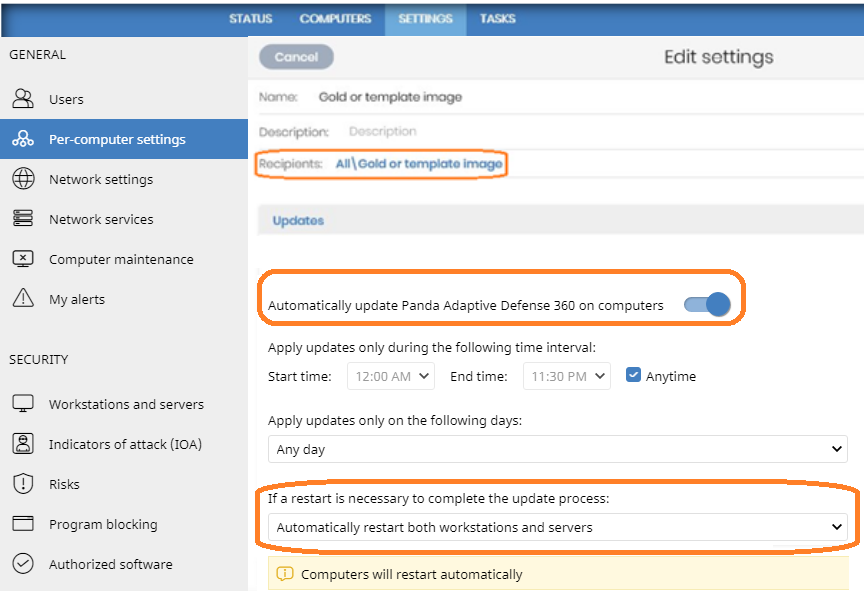
- Assign these settings to the Gold or template image group.
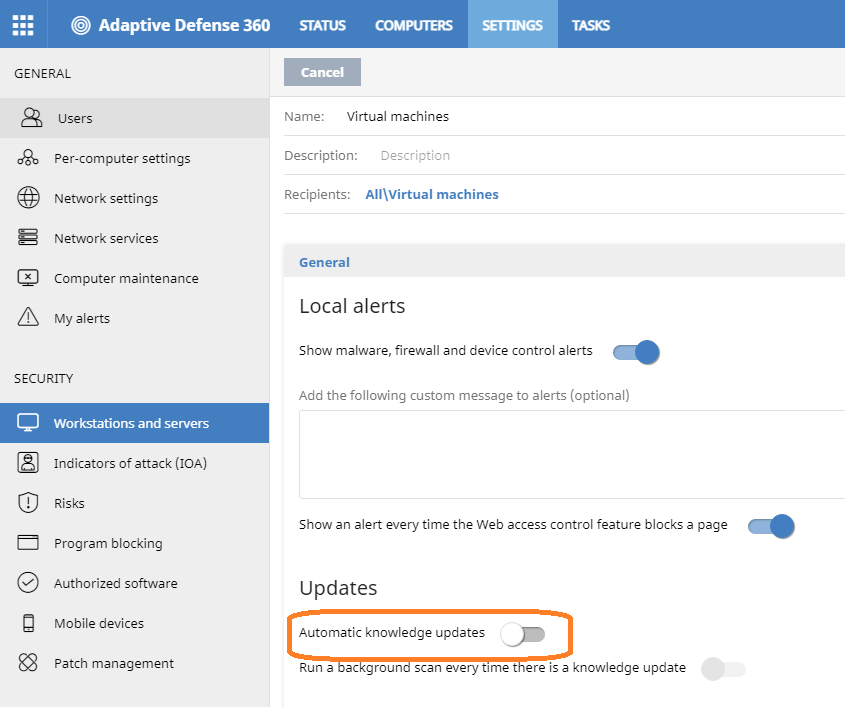
- Next, click the Settings tab, and select Workstations and servers from the Security section to create a settings profile for future image updates.
- Expand General and in the Updates section, make sure the Automatic knowledge updates toggle is enabled.
- Assign these settings to the Gold or template image group.
- Virtual machines group
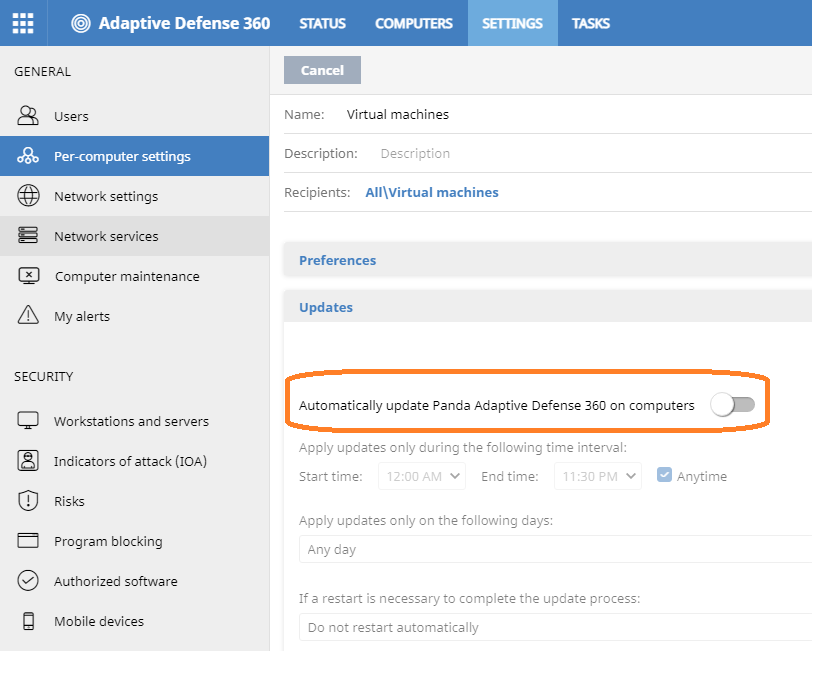
Virtual instances are based on the updated gold image. To optimize the VDI server's resources and reduce bandwidth usage, disable updates by following these steps:- Create a Per-computer settings profile that has the Automatically update Panda Adaptive Defense 360 on computers toggle disabled, and assign it to the Virtual Machines group.
- Go to Workstations and servers in the Security section of the Settings tab, expand General, go to the Updates section, disable the Automatic knowledge updates toggle, and assign those settings to the Virtual Machines group.
- Create a Per-computer settings profile that has the Automatically update Panda Adaptive Defense 360 on computers toggle disabled, and assign it to the Virtual Machines group.
- Gold or Template image Group
- Install the agent and the protection on the Virtual Machines group in order to generate the gold image:
- Go to the Computers tab, select the Virtual Machines group, and click Add computers. This will download the installer.
- Install the agent on the machine used to create the gold image and wait for the progress window to finish. During that time, the protection will be automatically installed and configured. After the installation is completed, the computer will appear on the list of protected computers in the console.
- Move the machine with the gold image to its Gold or template image group so that it receives the settings with the option to update. We recommend that, from the computer, you right-click the protection icon in the notifications area of the taskbar, and force a synchronization. This will push the settings to the computer so that it will start updating.
- Download the Endpoint Agent Tool for Windows, unzip it and run it on the computer with the gold image.
- Although it is not mandatory, in non-persistent environments with persistence levels of less than a week, we recommend that you scan the computer.
- For Adaptive Defense 360, you can use the scan option available either from the right-click menu or from Adaptive Defense 360 interface.
- For Adaptive Defense, use the Start cache scan button from the Endpoint Agent Tool for Windows interface.
This will fill the goodware cache and prepare the protection for virtual images. The process can take some time, depending on the contents of the hard disk. Wait until the operation finishes.
Equivalent command line: EndpointAgentTool.exe /sg
Remember that if you use a .bat or .cmd file, you must run this command:
start /wait "" "C:\ToolPath\EndpointAgentTool.exe" /sg
- In the Non Exclusive Events section, select the Detections, Counters and Check commands options and click Send or else, right-click on the protection icon and select Synchronize.
Equivalent command line:
EndpointAgentTool.exe /d /c /cmd
- Remove the ID of the computer, by selecting the checkbox Is a gold image.
- If the computer is protected by AntiTamper, type in the password in the AntiTamper password field.
Equivalent command line:
EndpointAgentTool.exe /pei /gi /atp:antitamperpassword
If there is no password, leave the atp value blank. - Click the Prepare image button. This removes the agent ID from the gold image, so all virtual machines obtain their ID when they are run and connect to Aether for the first time.
This step is critical to ensure that each virtual instance is uniquely identified in the Web UI.
- Although it is not mandatory, in non-persistent environments with persistence levels of less than a week, we recommend that you scan the computer.
- ATTENTION! Disable the Panda Endpoint Agent service to prevent it from starting automatically before the gold image is created for your virtual instances.
This step is critical to generate a specific ID for each virtual machine. - Access the VDI management tools and generate the gold image. If you have questions about this step, contact your vendor.
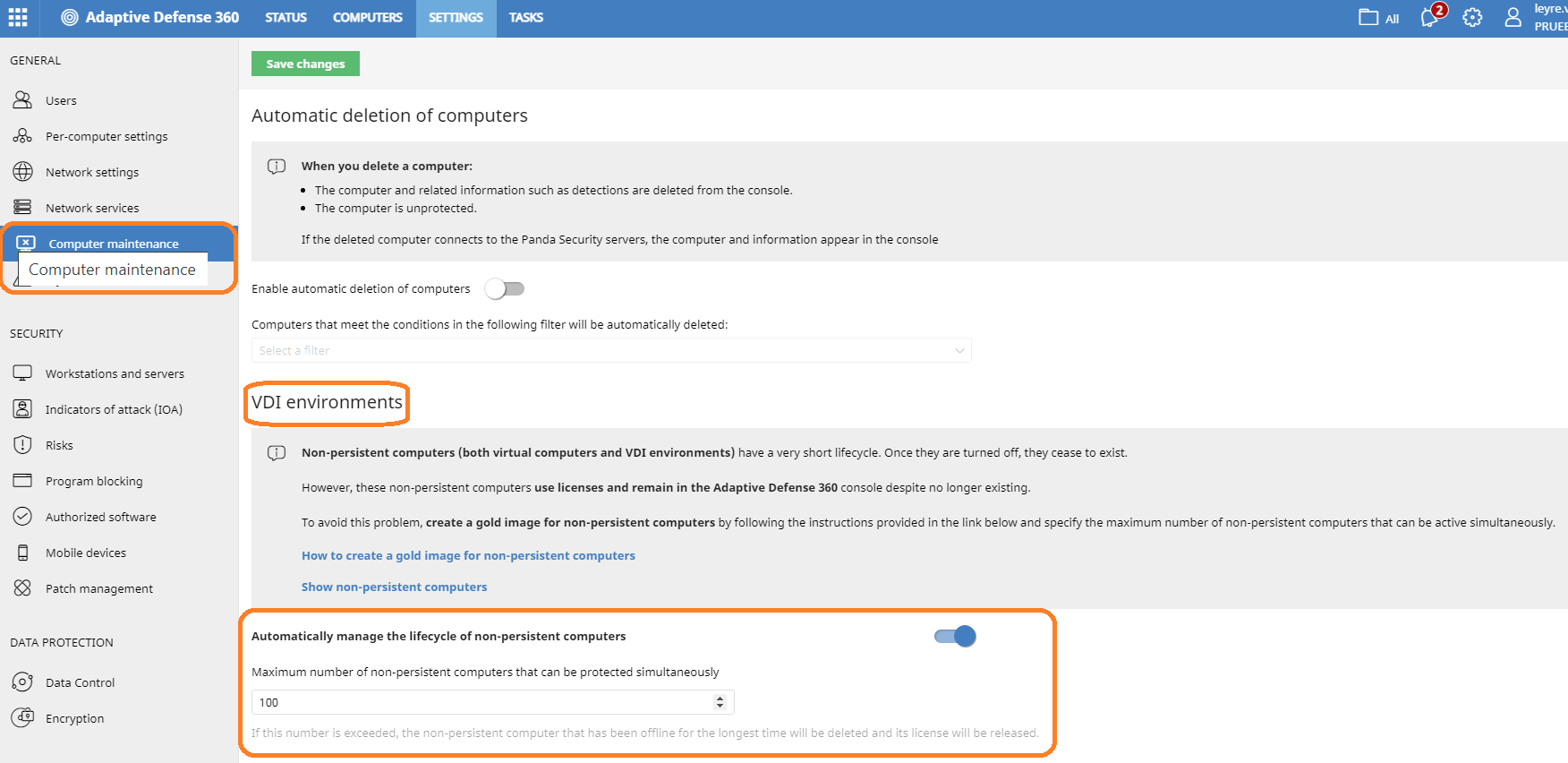
- You can configure the maximum number of non-persistent machines that can be active simultaneously in the VDI environments section of the Web UI. This enables automatic management of the licenses used by those machines, relieving you of the task of deleting them from the Aether platform to recover their licenses.
Once the custom gold image is ready, you can enable the Panda Endpoint Agent service, either with GPO policies for devices within a domain, or through other types of script applications such as Horizon, Windows Logon Scripts, etc.
In this example, we show you how to change the Panda Endpoint Agent service's startup type with GPO. First, you must create a GPO. To do so, in the GPO settings, browse to this path: Computer Configuration, Policies, Windows Settings, Security Settings, System Services, Panda Endpoint Agent. The service will be disabled. Change the setting to Automatic. The service will start automatically on the following reboot and will be integrated in the console.


- Start the machine where the gold image is installed.
- From the console, move the computer with the gold image to the Gold or template image group so that it receives the appropriate settings with automatic updates of the engine and knowledge.
- From the computer, right-click the protection icon in the notifications area of the taskbar to force a synchronization. This will update the computer.
- Updates are performed silently in the background. We recommend that you wait a few minutes to make sure the image is properly updated.
- If a new version of the protection is available, a restart window will be displayed and the computer will restart automatically (as configured in Per-computer settings).
In this case, once the restart is completed, we recommend that you force a new synchronization to make sure the product is fully updated and properly configured.
- Download the Endpoint Agent Tool for Windows, unzip it and run it on the computer with the gold image.
- Scan it by using the Start cache scan button. This will fill the goodware cache and leave the protection in an appropriate state for virtual images.
This process can take some time, depending on the contents of the hard disk. Wait until you are notified that the operation has finished.
Equivalent command line: EndpointAgentTool.exe /sg
Remember that if you use a .bat o .cmd file, this is the command to type:
start /wait "" "C:\ToolPath\EndpointAgentTool.exe" /sg - In the Non exclusive events sections, select options Detections, Counters and Check commands and click Send or else, right-click on the protection icon and choose Synchronize.
Equivalent command line: EndpointAgentTool.exe /d /c /cmd
- Remove the ID of the computer, by selecting the Is a gold image verification checkbox.
- If the computer is protected with AntiTamper, write the password in the AntiTamper password field. Otherwise, leave it blank.
Equivalent command line: EndpointAgentTool.exe /pei /gi /atp:antitamperpassword - Select the Prepare image button, making sure the Is a gold image option is checked.
This will remove the agent ID from the gold image, so that all virtual instances obtain their unique ID when they are run and connect to Aether for the first time.
This step is critical to ensure that each virtual instance is uniquely identified in the Web UI!
- Scan it by using the Start cache scan button. This will fill the goodware cache and leave the protection in an appropriate state for virtual images.
Verify Procedure
It is essential to ensure that you have followed the procedure correctly.
- View non-persistent computers
Panda Adaptive Defense 360 uses the FQDN (Fully Qualified Domain Name) to identify computers whose IDs have been deleted using the Endpoint Agent Tool and are marked as gold image.
To get a list of non-persistent VDI computers,follow these steps:- From the top navigation bar, go to Settings.
- Click Computer Maintenance from the left pane.
- Go to the VDI Environments section.
- Click the Show non-persistent computers link.
- The Computers list is displayed, with the non-persistent computers filter applied.
- View persistent computers
- From the top navigation bar, select Computers.
- Verify that all your cloned devices are correctly displayed in the web UI.
IMPORTANT! If you see a single device, you must remove the device from the Computers list and start the procedure from scratch, that is, rebuild the gold image and deploy it again to the affected endpoints.
Manage Licenses
If you follow the process correctly and delete the agent ID by configuring the Is a gold image option as indicated, every time a new computer is started, the system will calculate its ID and will determine if it is a new computer or an existing one.
In non-persistent environments, if the maximum number of machines that can be active simultaneously for non-persistent images is set, the server will manage licenses automatically, provided there are available licenses and the number of concurrent machines is not exceeded.
In persistent environments, if there are multiple machines that are no longer used, delete them from the database in order to free up licenses just as you would do with physical machines. This can be done from the Aether console, by selecting all machines to delete and clicking the Delete button, or individually via the context menu of each machine to delete.
Related articles
How to create an image for Linux persistent and non-persistent environments (VDI) with products based on Aether