The Distribution tool lets you install the protection centrally, avoiding manual intervention from users throughout the process.
Preliminary information
For the tool to work properly in Internet Explorer, you will need to disable the use of SSL in the Advanced Security Settings and enable the use of TSL.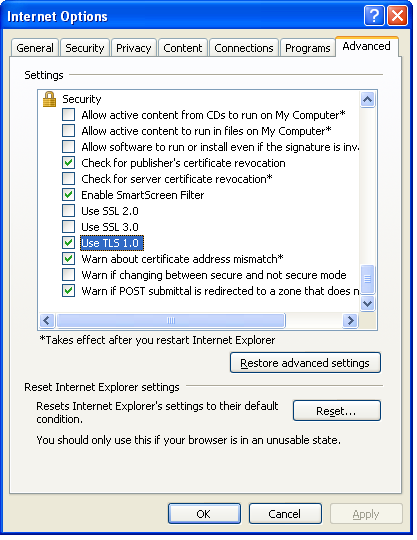
Downloading the distribution tool
- Go to the administration console.
- Select the Installation tab.
- In Use distribution tool section, click the Download distribution tool link.

- This opens the group selection screen. Select the one you want and click Download.

- Click Save in the Distributiontool.msi file download window.

- When the download has finished, run the DistributionTool.msi file from the directory you have saved it in. A wizard will guide you through the installation process.
Installing the protection
- Go to Start>> Programs>> Panda Security>> Distribution tool or to the shortcut on your Desktop.
- Select Install protection in the console. The Protection Installation screen will open, which will allow you to distribute the protection in two ways:
- Distribution by Domain
- Enter the group in which you want to include the computers to be installed. The settings policy to be applied on the computers will depend on the group selected
- Select the domains or computers in the network tree on which you want to install it
- Use the user name and password with administrator permissions to carry out the installation. The user name must be entered in domain\user name format
- Once the data is entered, click Install to generate the installation jobs.
- Distribution by IP address or computer name
- Enter the group in which you want to include the computers to be installed. The settings policy to be applied on the computers will depend on the group selected.
- Add the name or IP address of the computers to be installed, separated by commas. You can also select IP ranges using the ?-? symbol (e.g. 172.18.15.10 ? 172.18.15.50).
- Use the user name and password with administrator permissions to carry out the installation. The user name must be entered in domain\user name format.
- Click Install to generate the installation jobs.
- Check the installation job has completed successfully from the console.
- The protection installation will begin, completely transparently.
- Restart the computer if prompted.
Note: Short network connection interruptions may occur during the protection and firewall installation processes.