This article features access to the guide aimed at network administrators who need to protect their organization's IT assets, find out the extent of the security problems detected, and define response and remediation plans against targeted attacks and advanced persistent threats (APTs). Panda Adaptive Defense 360 on Aether and Panda Adaptive Defense on Aether are managed services that deliver guaranteed security without the need for network administrators to intervene, and offer highly detailed information thanks to the new Aether platform developed by Panda Security.
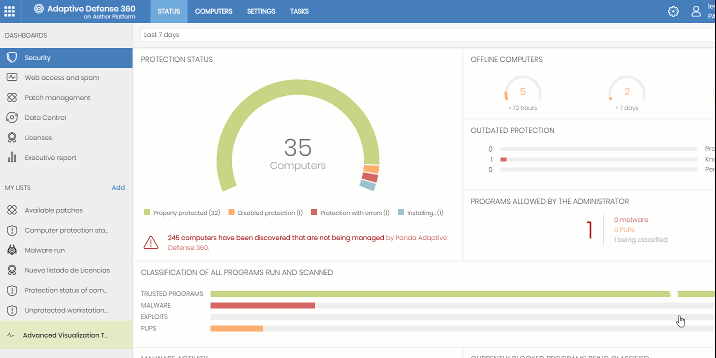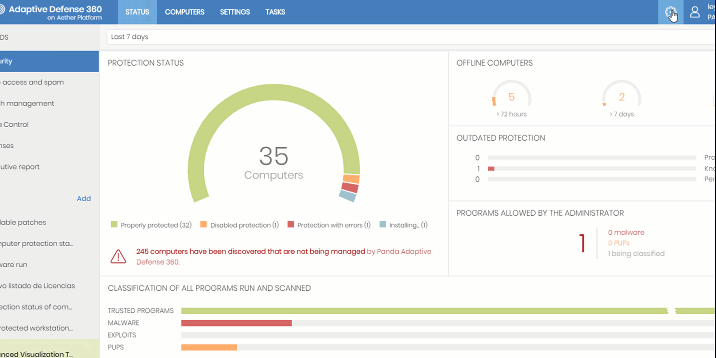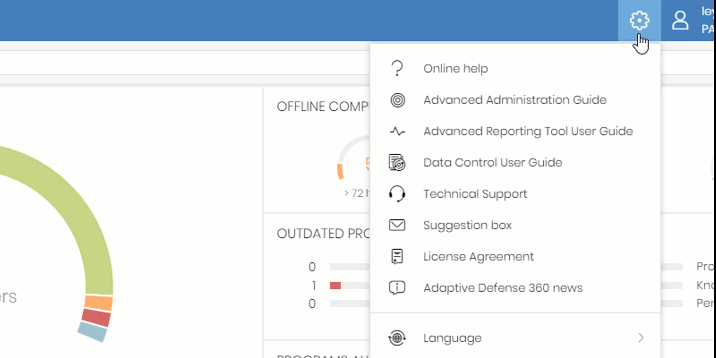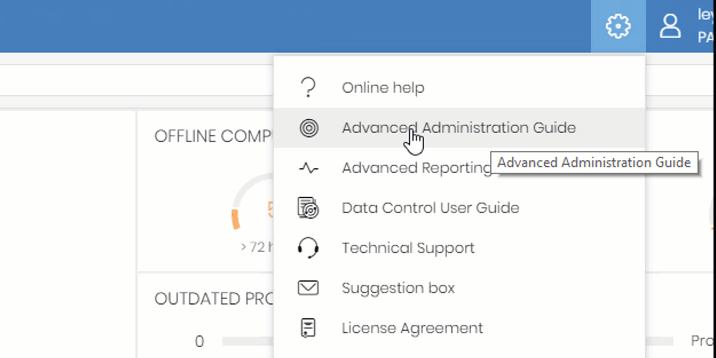
Aether is a scalable and efficient platform for the centralized management of Panda Security solutions, addressing the needs of key accounts and MSPs. Aether facilitates the real-time presentation of information generated by Adaptive Defense products about processes, the programs run by users and the devices installed, in a coordinated and highly detailed manner.
To get the most out of Adaptive Defense products on Aether, certain technical knowledge of the Windows environment is required with respect to processes, the file system and registry, as well as understanding the most commonly-used network protocols. This way, network administrators can accurately interpret the information in the management console and draw conclusions that help to bolster corporate security.
The Administration Guide is available from your product's administration console, more specifically, here:
 |
To access the Documentation download area, click here.