Surely this has happened to you before: you’re browsing online and you come across a blog or website that has a plugin for Chrome that you think looks interesting or useful. You check out the developer’s website, have a look at the benefits and decide to download it. You click on the corresponding button and you see something like this:
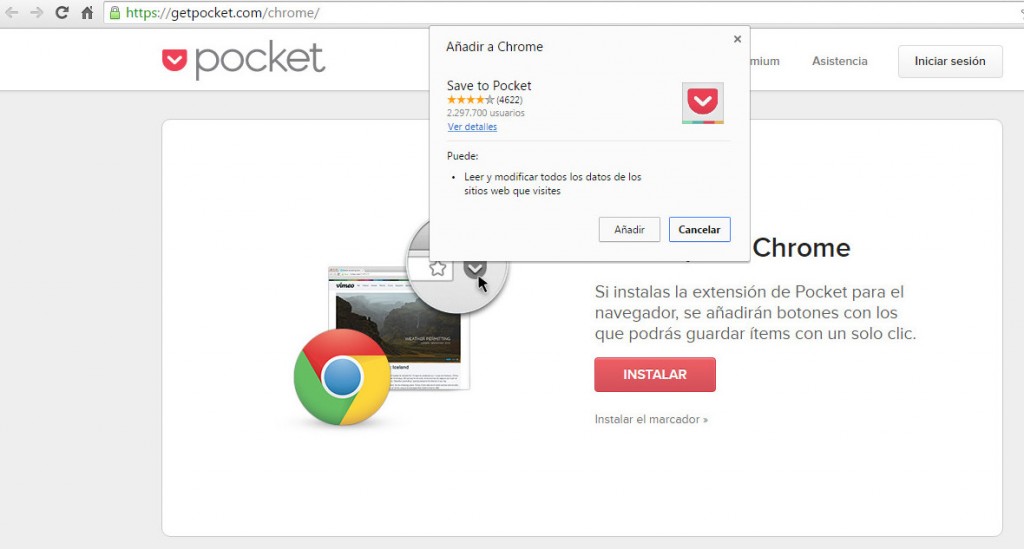
All you need to do is click add to get the extension. So, since Google implemented inline installation in 2001 it’s been as easy as that. Before then, the plugins needed to be installed via the Chrome Web Store. They are now staying there in the internet giant’s servers, but can also be downloaded from other pages. If you want the extension of Pocket, you can get it on the Pocket website.
Even though it’s logical, this process is proving to be quite the headache for Google. Some schemers are abusing this method so that you accidentally install dangerous extensions which could compromise your security. How are they doing this? Well, they trick you, by making you believe that they are necessary updates in order to view a video, for example:
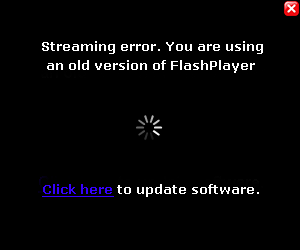
If you fall for this trick and click on the link, a box will appear that allows for the installation of the extension – like the one we showed you earlier in the article. In other words, you’ll be left with a plugin that you didn’t want and one which you have given a whole host of permissions to, which means it can do a lot of things to your browser such as filling it with ads like this:
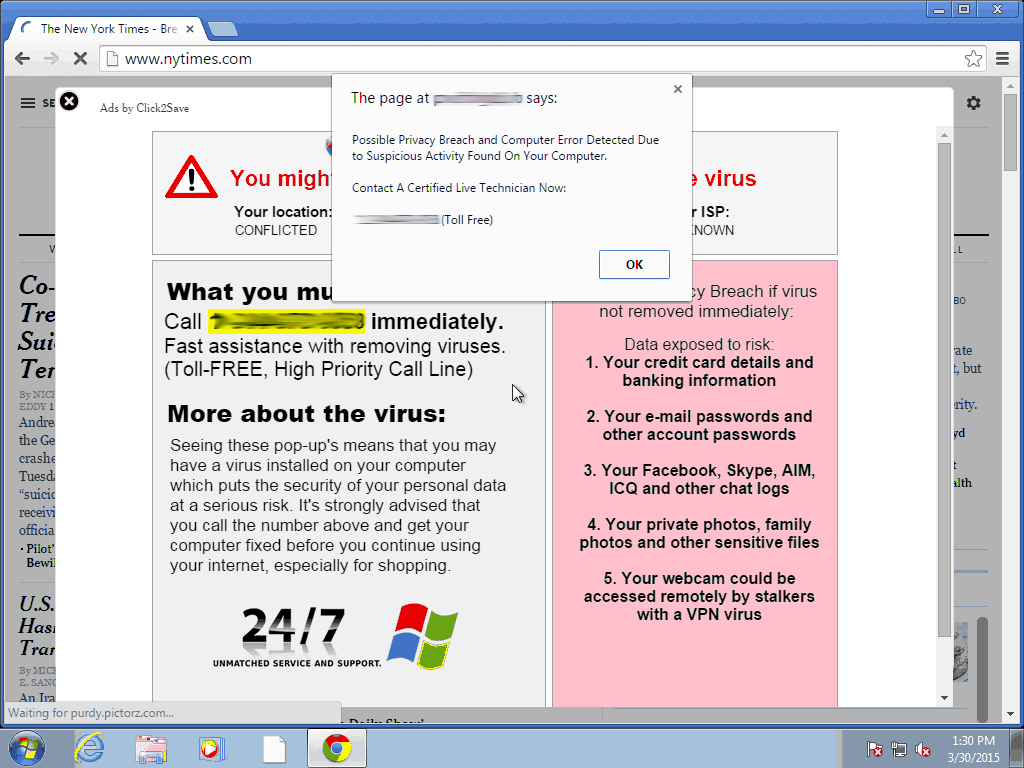
Pretty annoying, no? To avoid this, Google will prohibit the installation of plugins from webpages that abuse inline installation. Each time it spots one with bad intentions, it will blacklist it. From then on, every use user who tries to download the extension will be directed to the Chrome Web Store so that they check if it is installed. This way they’ll realize that it wasn’t an update for Flash Player.
The hunt for these schemers, which was announced on the company’s official blogs, will begin on September 3rd. It is expected to affect only 2% of the extensions as, unfortunately, the practice isn’t very extensive yet. That aside, Google states that it is “an important step towards maintaining a healthy ecosystem of extensions.”
This isn’t the first measure they have taken to achieve their objective. In May of this year they rolled out a change in the policies relating to extensions that impedes installation if it is stored outside of its own servers. Even if the download is done from another site using inline installation, the file that runs your browser comes from the Chrome Web Store.
According to a recent study which analyzed 48,000 plugins, they found that 130 were malicious and a further 4,712 were considered as suspicious. Google safeguarded some avenues of attack but left others exposed, such as the ones they will close off in September. Thanks to these measures, Google is making it progressively more difficult for its controls to be breached.


3 comments
Hello and thanks for your quidance with regard to the webpages extension blocking which I.m experiencing on my Nokia 3110c using Google Chrome. I hereby beg to request you to unblock or to remove extension blocking on my browser and I have to appolozise any mistake that occured in this regards as this might be the matter of online cyber criminals. Thanks
Hi Martin,
Thanks for reading us! Are you experiencing this problem with Panda Security? If so, please contact our tech support team on support.pandasecurity.com
Best regards,
Panda Security.
Unquestionably consider that that you said. Your favourite justification seemed to be on the net the easiest thing to keep in mind of.
I say to you, I definitely get irked at the same time as other people consider worries that they plainly don’t realize about.
You controlled to hit the nail upon the top as smartly as defined out the entire
thing with no need side-effects , folks could take a signal.
Will probably be again to get more. Thanks