Hackers are going to hack, and scammers are going to scam — no matter how much technology changes. While cryptocurrency is a new and exciting investment opportunity, it is vulnerable to cryptocurrency scams.
Similar to cash, crypto is accessible at any time from your very own digital wallet, but it isn’t protected by banks or a central protection organization. Without these additional protections, scammers know how to slip in and out undetected — leaving you coinless in their wake.
You can better protect your cryptocurrency with general knowledge and protection services. Our guide discusses what cryptocurrency scams are and dives deep into how you can identify and avoid them.
Table of Contents:
- What Are Crypto Scams?
- Types of Cryptocurrency Scams
- Identifying Cryptocurrency Scams
- Common Scam Tactics
- How to Avoid Cryptocurrency Scams
- How to Report Cryptocurrency Scams
What Are Crypto Scams?
Crypto scams are similar to other types of financial scams, but scammers target crypto assets instead of cash, credit or other cash equivalents. Cryptocurrencies — like Bitcoin or Ether — are stored in physical or digital crypto wallets, which can also become the target of a bad actor’s scam.
Cryptocurrency is especially prone to scams because it is:
- Decentralized: Without a central organization dedicated to monitoring and flagging suspicious activity, cryptocurrency scams frequently go undetected and unreported.
- Irreversible: Blockchain technology does not allow crypto transactions to be reversed, locking in funds and making them irretrievable.
- Anonymous: Wallet addresses and usernames allow users to buy, sell and trade — or scam — currency while staying relatively anonymous.
Because cryptocurrency is still a relatively new and often misunderstood form of technology, the number of crypto scams has skyrocketed in recent years.
Types of Cryptocurrency Scams
There are various types of cryptocurrency scams, and each is designed to gain access to a user’s cryptocurrency in some way. From targeting a user’s humanistic tendencies to simply breaking into their digital wallet, these scams run far and wide.
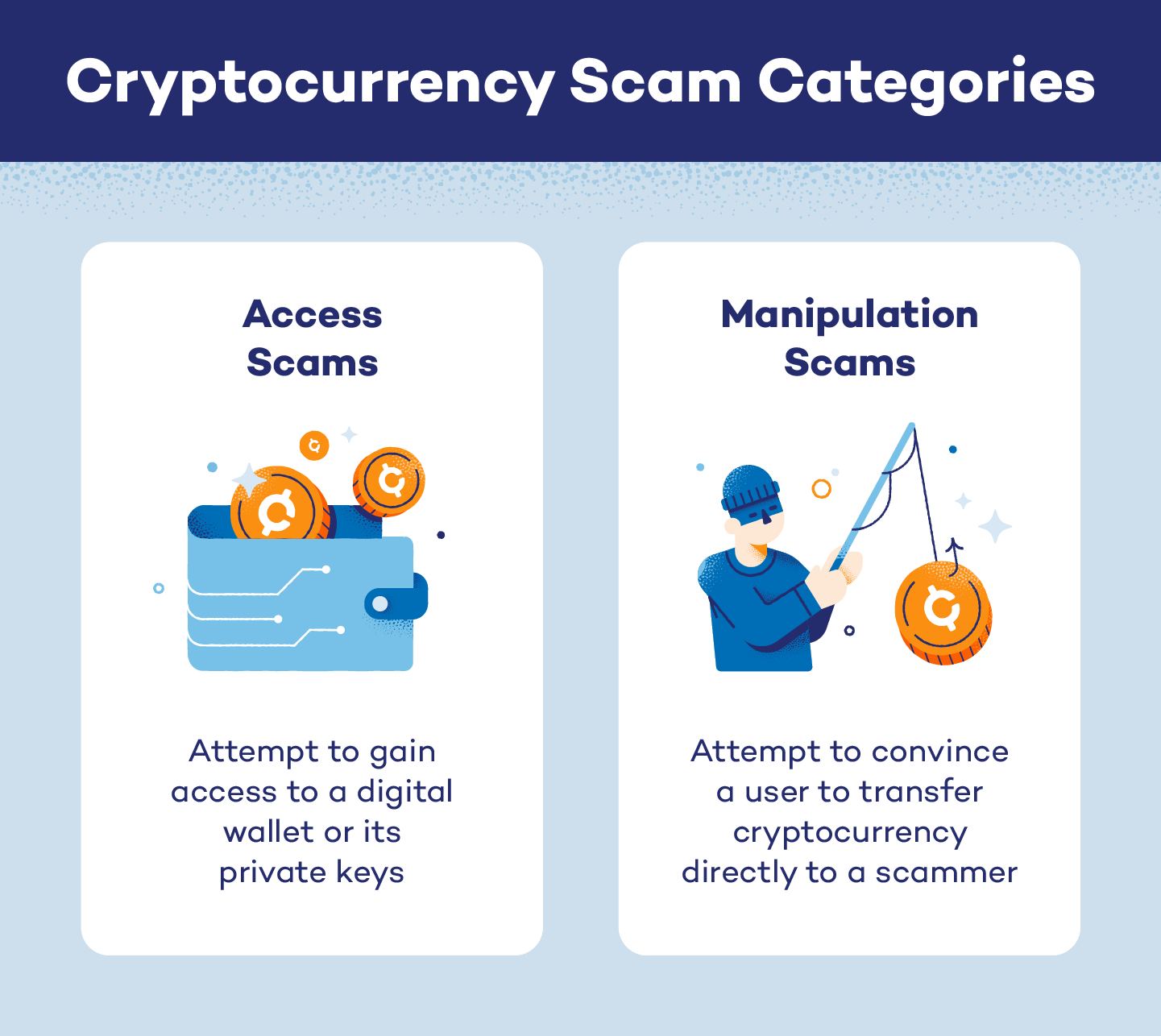
Despite there being so many different types of cryptocurrency scams, each can usually be classified into one of two main categories:
- Access scams: attempt to gain access to a digital wallet or its private keys
- Manipulation scams: attempt to convince a user to transfer cryptocurrency directly to a scammer
Many scams can be classified into both of these categories, and scammers may try to obtain both crypto funds and access codes.
Social Engineering Scams
Category: Manipulation and access scam
Scams that employ social engineering concepts are designed to gain control of personal and sensitive information. These scams target a user’s humanity and trusting instincts to manipulate them into releasing private information to what they assume is a legitimate organization or person.
Similar to whaling, social engineering scammers may impersonate or pretend to be powerful members of an organization. These scams can take days, weeks, months or even years, and will demand payment through cryptocurrency.
Romance Scams
Category: Manipulation scam
Dating apps and websites can be prime grounds for crypto scammers to hide. Many scammers will convince users they are part of a long-term relationship, gain their trust and then demand cryptocurrency payments and transfers.
Of the 70,000 romance scams reported in 2022, almost a quarter convinced targets to send payment because they claimed someone close to them was sick or in trouble. Similar to social engineering scams, these scams target a person’s instinct to trust, plus they are usually carried out completely online.
Imposter Scams
Category: Manipulation and access scam
If you are cold contacted by a celebrity, business, influencer or government employee, verify their identity before interacting with them. Imposter scammers will pose as high-level, important individuals to convince you to send them money or participate in a fake giveaway.
Do not give out access numbers or crypto credentials to anyone — even if you think the imposter could be real. Anyone who demands payment via cryptocurrency should be considered suspicious.
Phishing Scams
Category: Access scam
Phishing scams specifically target digital wallets and access to a user’s cryptocurrency. Like a standard phishing scam, bad actors will use malicious links to steal a user’s private key. These links can be sent through email, text, social media channels or other platforms, and they will take a user to a dangerous landing page. Once clicked, a user will be prompted to enter their information, which can be used to access crypto wallets.
Blackmail Scams
Category: Manipulation and access scam
Some scammers will claim to have sensitive information, photos or other types of blackmail on a target when attempting to scam them. Scammers often suggest a trade — incriminating information for private keys to access their digital wallet. These types of scams are classified as extortion attempts and should be reported immediately.
Investment Scams
Category: Manipulation scam
Choosing to invest money — even in the form of cryptocurrency — into items, NFTs, markets or other investment opportunities is a chance at luck. There are no guarantees in the investment world, but scammers may try to convince you there are.
If you are promised a large return on your investment, reevaluate what you are investing in. These types of schemes are typically irreversible, and you will lose your entire investment without gaining anything in return.
Cloud Mining Scams
Category: Manipulation scam
Cloud mining on its own is not necessarily a scam, but scammers have been known to use the tactic to secure crypto funds. Bad actors and mining platforms can convince retailers and investors to invest capital into a project — at an unmanageable or untrue hash rate — which never delivers its promised returns.
Rug Pull Scams
Category: Manipulation scam
Having the rug pulled out from under you is never an enjoyable experience, but it can be especially frustrating and hurtful when it takes your capital or crypto funds with it. In a rug pull scam, scammers convince investors to place stock into a project fund for a new item, coin or another opportunity before the scammer removes the liquidity and disappears.
Any coins or items an investor received are likely fake or unsellable. Investors lose the funds and capital they invested, are unable to gain from the items they received and the project is abandoned — if it was ever real in the first place.
Employment Scams
Category: Manipulation and access scam
It’s common for crypto scammers to pose as employers or job recruiters to scam job hunters out of cryptocurrency. Fake job postings on online bulletin boards may lead to malicious landing pages, or imposter employers and recruiters may request crypto in exchange for job training.
These scams can work the opposite way, too. Scammers have also applied for remote work positions and lied about their identity and home country in order to gain access to crypto farms.
Initial Coin Offering Scams
Category: Manipulation scam
New crypto companies will often release an initial coin offering (IOC) to raise money and awareness of their new product. IOC scams promise users a discount on a new type of currency if they agree to exchange real, usable coins — like Bitcoin — with the company. Similar to rug pull scams, IOC scammers will go to great lengths to convince investors their company is real before liquidating the investments and disappearing.

Identifying Cryptocurrency Scams
If you invest in crypto, it’s important to know how to identify scams and legitimate operations.
Only scammers will:
- Demand payment in crypto
- Guarantee profits and payouts
- Mix online dating and investment advice
- Request crypto keys
- Send texts or emails impersonating a person, business or government agency
- Blackmail you with real or fake explicit materials
If you notice any of these tactics — or if you receive unsolicited investment advice or cryptocurrency — you may be the target of a cryptocurrency scam.
In addition to these identifying features of a scam, there are four other major scam identifiers.
1. White Papers
Real, recognized cryptocurrencies create white papers during their development processes. These documents outline and identify the characteristics of a new currency, and they explain the network’s functionality.
Fake cryptocurrencies will not have white papers, or they will have white papers that are incorrect, poorly and quickly written, and lack depth or explanation about the use of funds. Read through the white papers of well-known cryptocurrencies to gauge how thoroughly new organizations have written their own. If they aren’t comparable, be wary about investing in or purchasing a new cryptocurrency.
2. Developers
In addition to functionality, white papers should identify the developers and team members behind an organization. Unless the project is open-source, you should be able to identify the developers here or find mentions of them and their processes on GitHub or GitLab. If none of these are present, you may have stumbled into a cryptocurrency scam.
3. Freebies
Promises of free items — especially promises of free crypto coins — should be taken with caution. Scammers may try to convince you to give them access to your wallet to give you free coins, or they may request payment of some kind after transferring the funds.
4. Marketing
Crypto scammers are in it for the money, but cryptocurrencies are not usually a money-making business. Real cryptocurrency coins should be designed specifically to help the blockchain function, and their marketing should be low-key.
Any crypto companies frequently posting on social media or overhyping their product should be considered suspicious. Marketing focused on funding rather than any new technology in production may also indicate a scam.
Common Scam Tactics
While there are various types of cryptocurrency scams, many scammers depend on the same or similar tactics when scamming users.
Some common scam tactics include:
- Guarantees: promises of large payouts
- Out-of-the-blue contact: random contact from an unknown person through text, email and even social media platforms
- Celebrities: imposters posing as celebrities with fake giveaways or problems
- Love interests: imposters posing as romantic partners online
- Freebies: promises of free funds, coins or items
- Lack of detail: vague explanations about a currency or organization
- Business impersonation: imposters posing as business leaders, partners or other business-centric individuals
- Employment opportunities: fake employers, employees or job listings
These tactics can be dangerous and convincing. To protect yourself and your belongings, you need to know how to avoid crypto scams — even when these tactics are involved.
How to Avoid Cryptocurrency Scams
There are some important actions you can take to avoid cryptocurrency scams. Do not send anyone money or contact them in any way, plus:
- Protect private keys from everyone
- Ignore unsolicited contact from users you don’t know
- Don’t click unusual links
- Separate your crypto and bank accounts
- Research all businesses before agreeing to invest or partner with them
- Identify HTTPS in the URL of a crypto exchange or wallet address
- Look for grammatical errors and misspelled words in communications, white papers and marketing materials
- Invest slowly instead of all at once
- Don’t jailbreak smart devices
- Meet all romantic partners in person before agreeing to send or exchange crypto (and even then, proceed with caution!)
- Contact an agency directly if a message or investment officer claims your funds are frozen
- Investigate jobs and recruiters specializing in cryptocurrency
- Do not accept offers of free items or funds
- Be suspicious of excessive marketing

How to Report Cryptocurrency Scams
It’s important to report any suspicious or malicious activity you encounter, and there are multiple organizations available for you to contact.
To report a cryptocurrency scam:
- Submit a Federal Trade Commission fraud report.
- Send in a complaint or tip to the Commodity Futures Trading Commission.
- Report the scam to the U.S. Securities and Exchange Commission.
- Notify the FBI Internet Crime Complaint Center.
- Report the crime to your local law enforcement office.
You may also want to notify your personal crypto exchange to learn what type of fraud prevention and reporting they have in place.
As crypto continues to gain popularity, cryptocurrency scams will become more common. Protect yourself and your family with Panda Dome, which offers premium protection in more than 180 countries.





