All users look for and count on a safe, secure online experience. Whether they’re buying a new pair of shoes or transferring money to a new bank account, security is top of mind. But how can you tell if a website is safe, and what’s the difference between sites with “http://” and “https://” in their URL?
Even if you try to stay anonymous online or vary your passwords, browsing unprotected websites can be dangerous. Knowing what HTTPS is and how it works can increase the security of any browsing experience.
If you’ve ever wondered “What is HTTPS?” and “What keeps you safe while browsing the internet?” this guide is for you.
What Is HTTPS?
HTTPS, or Hypertext Transfer Protocol Secure, is the secure protocol that helps data move between web browsers and websites. While HTTP transfers unencrypted data, HTTPS encrypts information to increase security for sensitive data, like passwords and bank account information.
To encrypt this data, HTTPS uses Transport Layer Security (TLS) — formerly known as Secure Sockets Layer (SSL). It begins by using two types of keys to encrypt information, known as an asymmetric public key infrastructure.
- Public key: This key allows anyone to encrypt messages. This encryption can only be unlocked by a secondary, private key.
- Private key: This key is privately controlled by the website’s owner. Because this key can unlock public key information, it is kept on the webserver to help public decryption.
The information transferred using HTTP is susceptible to attacks, including man-in-the-middle attacks. After the initial TSL/SSL handshake, HTTPS begins using symmetric encryption to safely transmit and protect data from these types of attacks. By encrypting transmitted communication, HTTPS helps create safer links for a more secure browsing experience.
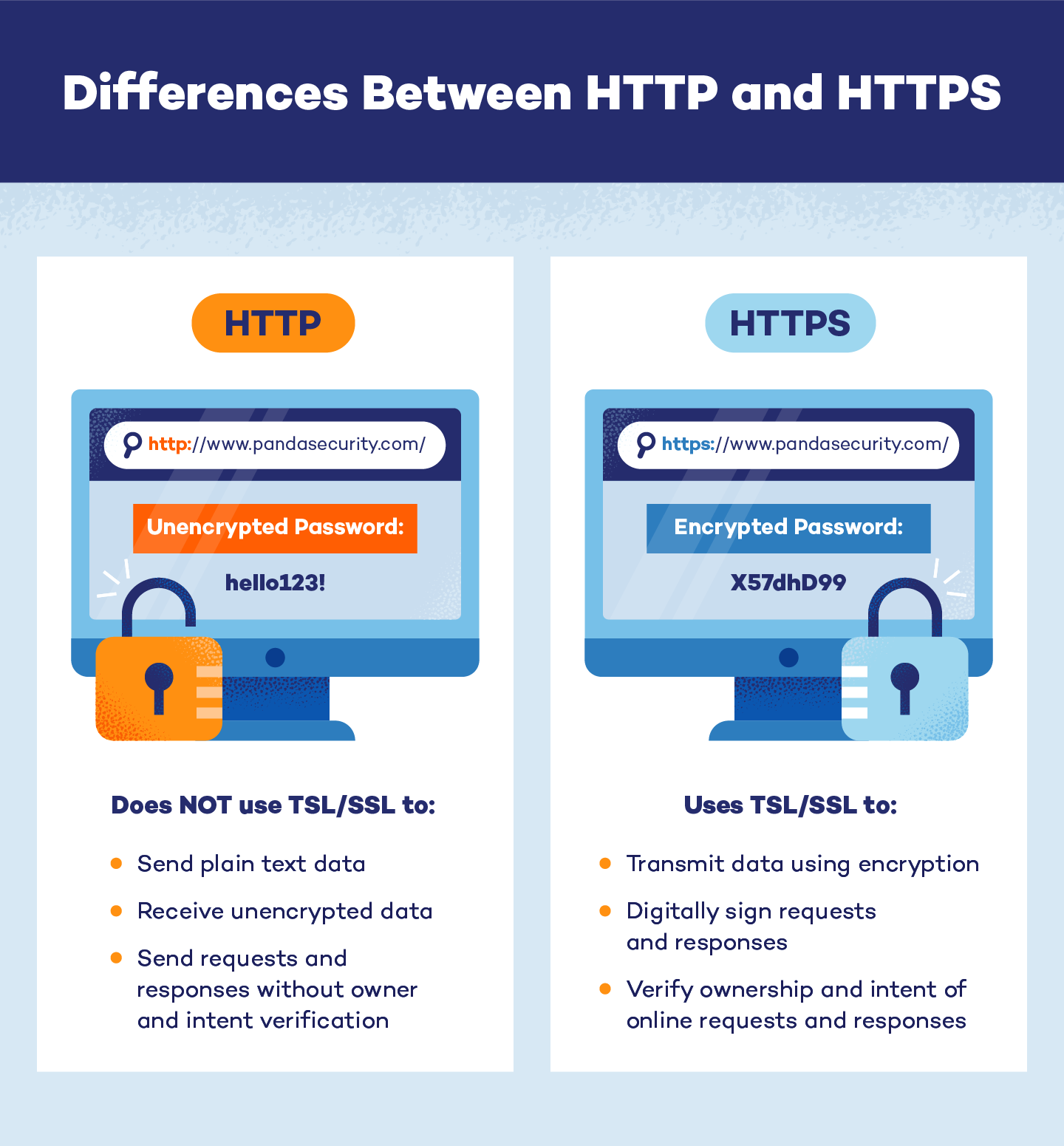
HTTP vs. HTTPS
Simply speaking, HTTPS is the HTTP protocol with a TSL/SSL certificate. So, if they don’t use different protocol systems, what is the difference between HTTP and HTTPS? On the surface, they don’t seem so different, but HTTPS is significantly safer for data transfers.
To the original HTTP protocol, HTTPS adds:
- Encryption: Instead of sending plain text data across a port, HTTPS uses encryption to conceal private information from outside parties. This occurs when browsers, web servers or websites share a secret key.
- Authentication: Each TSL/SSL certificate includes a public key. The web browser can use this key to prove that the data being transmitted is owned by someone with the corresponding private key.
Integrity: Each document that is sent to a corresponding server via HTTPS is digitally signed. Browsers can use this signature to determine if a document was corrupted during transit. If the document’s integrity is intact, it can be opened, viewed or transported again.
How Does It Work?
HTTPS automatically uses port 443 for any type of data transfer. Although the default port for HTTP is port 80, port 443 can support HTTP connections as well. However, the steps of every secure HTTPS transfer must use port 443.
- Step 1: The client’s browser and server exchange introductory messages, known as a TSL/SSL handshake.
- Step 2: Using an asymmetric public key infrastructure, standards for encryption are communicated.
- Step 3: The server certificate is shared with the browser.
- Step 4: The client checks the certificate and verifies it is valid.
- Step 5: A public key is used to create a secret key.
- Step 6: The public key encrypts the newly created secret key. This encrypted data is shared with the server.
- Step 7: Both the client and the server create a symmetric key based on the secret key.
- Step 8: This symmetric key is used to encrypt and decrypt incoming and outgoing data between the client and server.
In this model, the TSL/SSL handshake and server certificate help ensure the security of data transfers across the HTTPS port.
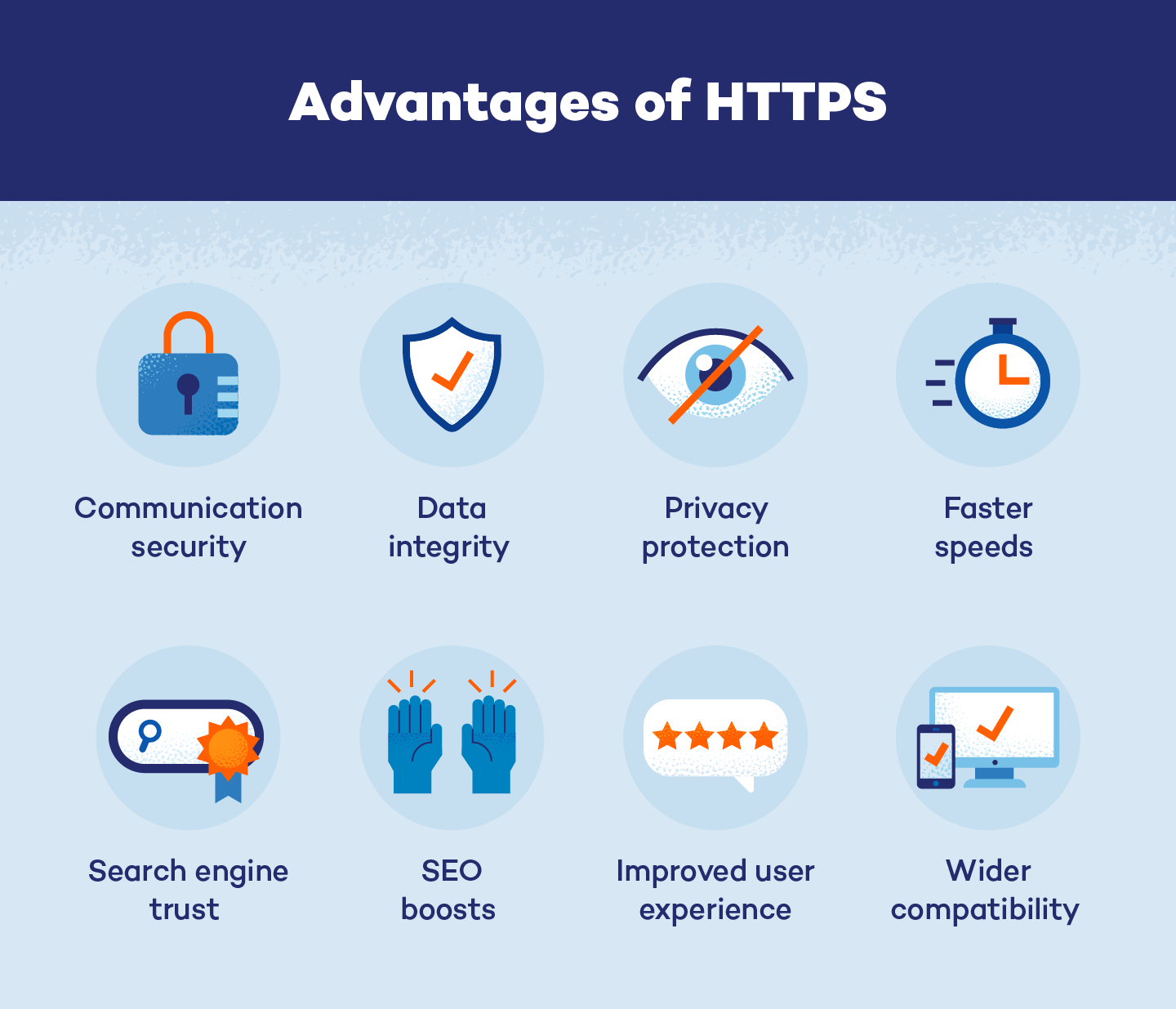
Why use HTTPS?
It may seem like a waste of time and resources to switch browsers, servers and websites to HTTPS when it uses the same protocol as HTTP. However, HTTPS offers clients and servers a variety of advantages and benefits that HTTP does not.
Advantages and Benefits of HTTPS:
- Information passed between a browser and a server is encrypted which increases communication security.
- Data can maintain its integrity even if it is trapped by hackers.
- HTTPS makes eavesdropping on online conversations more difficult and protects the privacy of clients and website users.
- Data size is reduced, so HTTPS is faster than HTTP.
- Sites that use HTTPS are trusted by search engines.
- HTTPS websites often rank higher on search engine results pages which can help boost SEO.
- Sites using HTTPS are less likely to be flagged as insecure, which improves the user experience.
- HTTPS is compatible with more browsers and servers than HTTP.
HTTPS is quickly becoming the preferred method for online browsing and data sharing. Unsecured connections using HTTP leave both clients and servers at risk of targeted attacks and information tracking, while secure HTTPS connections are designed to protect data and client information.
How Secure Is HTTPS?
While HTTPS cannot guarantee security from hackers or other cybercrime events, it does guarantee greater safety than HTTP. By encrypting transmitted information and supporting the CIA triad, HTTPS increases link safety and website security.
CIA Triad
Principles for an organization's security protocols| Confidentiality | Integrity | Availability |
|---|---|---|
| HTTPS protects confidentiality by hiding cookies and encrypting other data. | HTTPS maintains integrity by protecting data from tampering and modification. | HTTPS ensures website availability by redirecting access away from fake versions. |
However, it is still possible for HTTPS’ security to falter. Be aware that HTTPS is still vulnerable to some weaknesses and attacks, including:
-
- DNS spoofing: Certificate authority can be tampered with, meaning HTTPS websites can fall victim to DNS spoofing.
- Cryptanalysis: Hackers may use cryptanalysis to target the potential weaknesses of HTTPS.
- Client computer attacks: HTTPS connections can be the target of false or dangerous certificate attacks. If the connecting browser or server is compromised, the HTTPS connection is also at risk.
Despite the possible risks and weaknesses of HTTPS, it is substantially more secure than HTTP because it is less vulnerable to other common cyber and malware attacks.
7 Steps for Switching From HTTP to HTTPS
HTTPS is becoming the standard for browser and server security. There are seven steps to switch from HTTP to HTTPS:
Step 1: Back up your website to its hosting platform or an external hard drive.
Step 2: Purchase a TSL/SSL certificate. The types of security certificates are:
-
- Domain validated (DV) certificate: Indicates you own the domain
- Organization validated (OV) certificate: Indicates you own the domain and notes its name and other identifying information
- Extended validated (EV) certificate: Indicates you own the domain, notes identifying information and validates its legal existence
- Single-name certificate: For a single subdomain name
- Wildcard certificate: Allows a domain to have an unlimited number of subdomains
- Multi-domain certificate: Also known as Subject Alternative Domain (SAN) certificates, these support up to 100 domains, subdomains and IP addresses
- Unified communications (UCC) certificate: Designed specifically for Microsoft Exchange and Microsoft Office Communication Servers
Step 3: Change internal and external links to HTTPS. There are online services to help change and migrate links.
Step 4: Update your code library so it continues to program and update pages to HTTPS.
Step 5: Create a 301 redirect to send visitors to your newly secure website.
Step 6: If you use a content delivery network, update the TSL/SSL to match your new certificate.
Step 7: Make sure Google Analytics and Google Search Console are updated to match your HTTPS site.
Even though HTTP and HTTPS use the same protocols, be aware of the following factors that could affect your site transfer:
- Certificate expiration dates: Before purchasing or adopting a TSL/SSL certificate, check the expiration date. If the certificate is expired or expires soon, your site transfer could fall through.
- Supported host names: Choose a TSL/SSL certificate that will support all your hostnames.
- Server Name Indication (SNI): For better results, include an SNI extension with your certificate so your specific hostname is available to servers and browsers.
- Crawling and indexing: Check that your robots.txt file allows search engines to crawl your pages.
- Matching content: The content on your web pages should match for both your HTTP and HTTPS pages.
Browser and server security is an important modern-day problem. Even though 75% of Americans are concerned about their online privacy, most never take personal action to ensure their safety.
More than 30 million users trust Panda Security to prioritize and keep their information protected in a variety of ways. We have a strong understanding of HTTPS and additional security products like VPNs so you can stay safe while surfing the web or sharing sensitive data.




1 comment
Muito bom