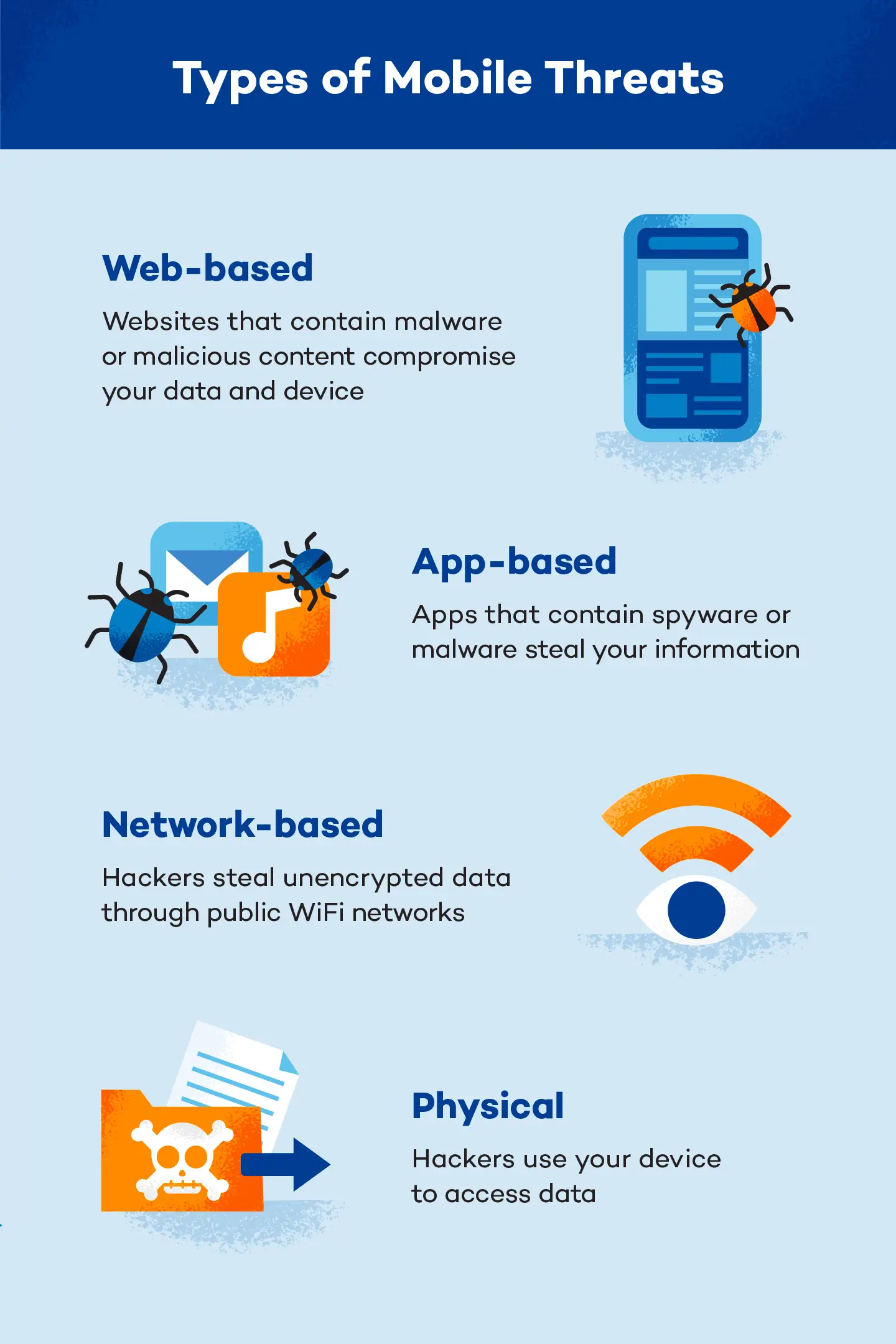
Nearly all the technology we depend on is susceptible to viruses and cyberattacks, and our phones, tablets and laptops are no exception. Since these threats continue evolving faster than we can devise solutions for them, maintaining secure mobile devices is an ongoing responsibility.
To help you keep your phone or tablet as safe as possible, we’ve put together 10 of our top tips for promoting mobile device security so you can stay protected, whether you’re at home or on the go.
1. Keep Your Home Screen Locked
If your device gets lost or stolen, it could give a stranger complete access to your personal information. While it won’t help you keep possession of your phone, locking your home screen can go a long way in blocking a thief from stealing the data inside it. Here are a few popular screen lock mechanisms to consider:
- Passcode: A sequence of letters or numbers that has to be entered to unlock the device; this is a simple but effective option.
- Pattern: Similar to a passcode, this is something you have to draw to unlock the device. It’s quick and difficult for another user to guess correctly.
- Fingerprint: A form of biometrics, this keeps your device locked unless someone with a pre-registered fingerprint attempts to open it.
- Face recognition: Similar to fingerprints, this biometric option means your device will only unlock after scanning an authorized user’s face.
When enabling a lock screen, you can choose how long the phone can be idle before locking. Be sure to choose the shortest amount of time. This will protect you by automatically enacting the lock screen even if you forget to lock it yourself. It will also save your battery by darkening your screen more quickly when you’re not using it.
2. Keep Bluetooth Turned Off
From earbuds to wireless speakers to gaming accessories, many of us use Bluetooth so regularly that we hardly even think about it. But hackers can target devices using Bluetooth, too.
To do this, hackers replicate networks your device has connected to before and consider to be trusted. They can then prompt your device to connect to their own network and devices via Bluetooth, which opens the gates for a huge array of attacks.
To stay protected, follow two general rules: Only connect via Bluetooth to devices you know and trust, and turn Bluetooth connectivity off when you’re not using it. Doing both of these things will help you keep would-be Bluetooth attackers at bay.
3. Keep Your Device’s OS Up-to-Date
Mobile phone operating system updates are intended to improve your experience. This could entail anything from performance to security. Although they happen frequently and users tend to repeatedly ask the device to remind them in the future, it’s important to stay up-to-date with them. These updates can protect both iOS and Android devices from newly discovered threats.
Most devices make these updates fairly obvious, but it’s never a bad idea to make sure you’ve got the latest version of your OS installed. You can usually do this in the device’s settings. From the Settings menu,, look for an option like “About Phone,” “About This Device,” or “General” if you don’t see an “Update” or “Version” section. From there, look for “System Updates” or “Software Update.” When in doubt, most devices also have search features, where you should be able to find it if you enter the word “update.”
4. Only Connect to Secure Wi-Fi
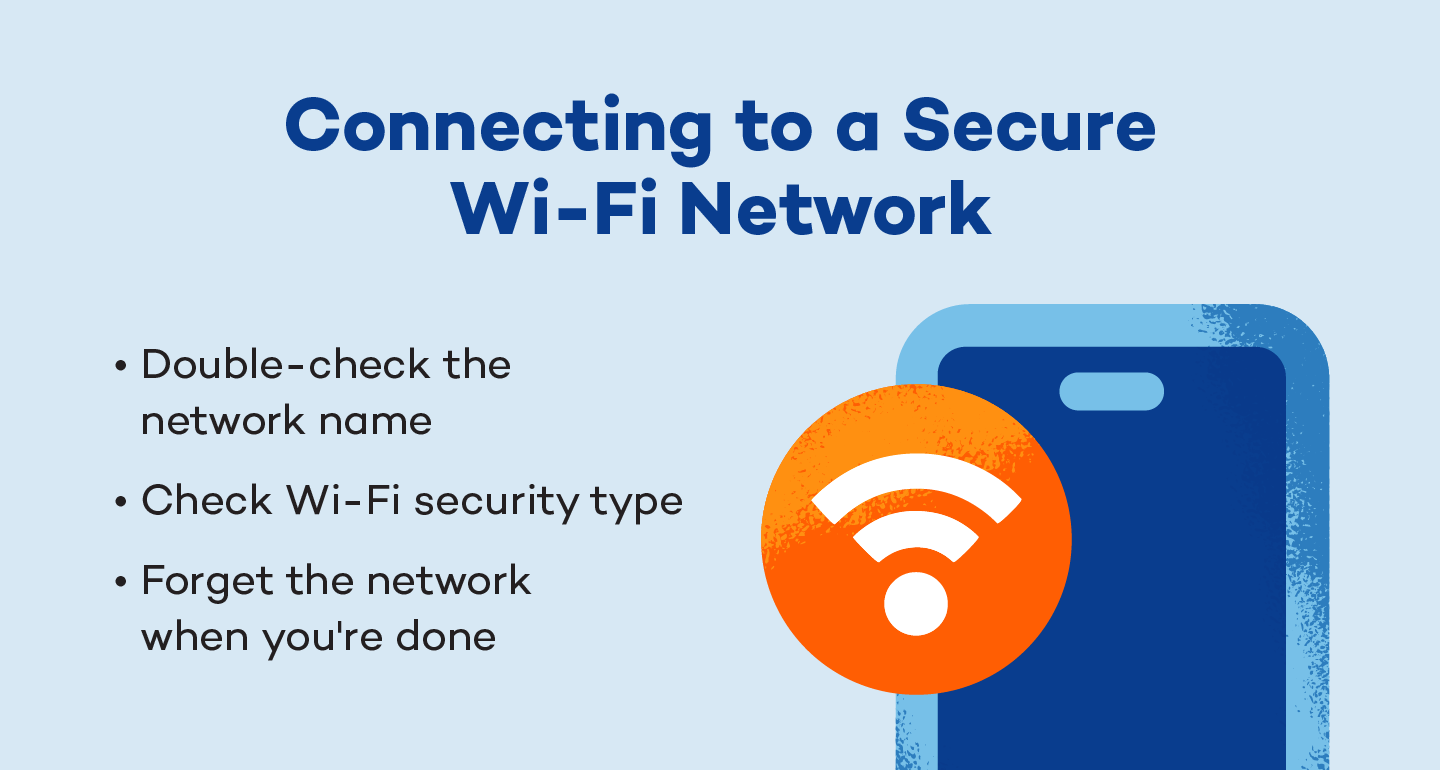
The beauty of mobile devices is that we can access the internet anywhere and everywhere we go. While free Wi-Fi can save data or help us access the internet in places where our phone service is limited, it’s important to be wary of unsecured networks.
Bad actors can do a lot of damage if they take advantage of unsecured networks or even trick you into connecting to their networks. Here are a few ways to combat their tactics.
Double-check the Network Name
Sometimes, staying safe can be as simple as looking at the names of the networks. If you can, verify the legitimate network name in a public place by asking an employee or looking for a sign. If you can’t do that, read the names of the networks and avoid any that look like knockoffs of a legitimate-sounding option. If you see “Cafe Guest” and “Cafe Geust” for example, the misspelled option is an obvious culprit.
Check Wi-Fi Security Type
To be safe, only connect to secure public networks. When you select a network, explore its details to see its security type. A wired equivalent proxy, or WEP, is the least secure. Wi-Fi Protected Access, or WPA, is more secure, whether it’s WPA, WPA2, or, more recently, WPA3. Whenever possible, prioritize public networks with the most recent WPA possible.
Forget the Network When You’re Done
When you leave the network behind, be sure to manually forget the network so your device doesn’t stay connected when it’s in range. When you connect to a new network, your device will typically prompt you to connect to that network automatically. It’s safer to reject this option. If the network gets compromised when you’re not connected, you don’t want it to automatically reconnect to it when you come back, even if you’re not planning to use it.
5. Use a VPN
To stay safe while using public Wi-Fi, be sure to connect to a virtual private network, or VPN. These services encrypt your data, which can be extremely useful since many public Wi-Fi networks are not encrypted. Essentially, this can help stop phone hackers from seeing the data you share and access on your device.
Check out Panda VPN for Android, which allows you to enjoy a secure Wi-Fi connection even on public networks. Changing your virtual network will protect your location and keep your information from prying eyes. On the other end, make sure you keep your Wi-Fi secure to prevent others from accessing your network.
6. Only Download From Trusted Sources
When downloading apps, be sure to download them from the official app stores and check reviews. Cybercriminals create rogue mobile apps that mimic trusted brands to obtain users’ confidential information. To avoid this trap, be sure to look at the number of reviews, last update and contact information of the organization.
For iOS devices, this tends to be much less of an issue because users can only download apps from Apple’s App Store (though iPhones can get viruses). It can be more of a risk for Android devices or jailbroken iPhones, which allow users to download applications from less secure sources.
7. Use Multi-Factor Authentication
Also called two-factor authentication (or 2FA), multi-factor authentication is steadily becoming the norm for web security. Many applications and websites will prompt you to enroll in it, while others require it.
Multi-factor authentication requires users to authenticate their login with a second, trusted account or device. Since remote hackers won’t have access to that other account or device, this is a much stronger security measure than simply entering a password or opening a pre-logged-in app.
This can seem cumbersome in that it requires you to go through an extra step before accessing a website or app, but it’s well worth it. To secure your mobile device as much as possible, enroll in 2FA for any application with the option.
8. Encrypt Your Data
Your smartphone holds a lot of data. If it’s lost or stolen, your emails, contacts, financial information and more can be at risk. To protect your mobile phone data, make sure the data is encrypted. Encrypted data is stored in an unreadable form so it can’t be used by a bad actor. Fortunately, most phones have encryption settings you can enable in the security menu, and these are often enabled by default. Here’s how to check.
For iOS Devices
To check if your iOS device is encrypted, go to the Settings menu and click on “Face ID & Passcode.” It will prompt you to enter your lock screen code. Then scroll to the bottom of the page where it should say “Data protection is enabled.”
For Android Devices
- Plug your device in
- Go to Settings
- Select the “Security” field
- Then, select the “Encryption” field and choose “Encrypt Phone” (or “Encrypt Tablet”).
Just be aware that if you don’t charge your device, unroot it or interrupt the encryption process, you may lose all your data. Encryption can take an hour or more.
9. Restrict Location Tracking
Unfortunately, many of the settings and services that make our devices more convenient also come with added vulnerabilities. Location tracking is no exception. We commonly use location tracking to let our navigation apps know where we are. It also allows apps or websites to personalize advertisements, which you likely recall from automated prompts from your favorite apps.
This isn’t inherently problematic, but it does present a vulnerability. Location data is valuable to hackers, and if they can track your location, they can use it against you. To stay as secure as possible, it’s a good idea to turn location tracking off whenever possible, deny location tracking when prompted by an app or website, or restrict location tracking to only while you’re actively using the app or website.
10. Install Antivirus Software
You’ve probably heard of antivirus programs for laptops or desktop computers, but your handheld computers can benefit from them, too. These programs can protect against viruses and hacking attempts. Some software, like Panda’s free antivirus software for Android, has VPN features included as a bonus.
The Importance of Mobile Device Security

Smartphones and tablets can hold all your important data and personal information, even if you don’t realize it. Remember that every piece of data on your phone is vulnerable to attack to some degree. That includes your location, personal data, login information for all the apps on your phone and more.
While there’s no way to be 100% sure that you’re safe all the time when you use a smartphone or tablet, there’s a lot you can do to reduce your risk of succumbing to a cyberattack. Keeping these tips for establishing secure mobile devices in mind will help you browse safely and protect your device.








6 comments
Superb article, I hardly found a useful post which contains real and useful information.
We’re glad you enjoyed it! We appreciate the feedback and we will continue to bring you useful content in the future.
All the best,
Panda Security
Hi, I was interested in using this article in a university essay on Mobile Security. Could you tell me when it was first published as I’ll need to reference it if I decide to use it.
Thanks
Hi James,
It was published on March 9, 2019.
Thank you for a straight forward article on mobile security that was easy to follow .
Thank you for this, it was easy to follow