OAuth (Open Authorization) is a standard for authorization that allows a third-party application to obtain limited access to your account on an HTTP service, such as a social media platform, without sharing your password.
OAuth, or open-standard authentication, is a framework or protocol that allows client-operated applications secure access to other servers and services. With OAuth, you can safely control this third-party access to protect passwords and login credentials.
As you interact with websites or web-based applications, like your social media accounts, third parties may ask for permission to access your protected information. If you grant them permission, OAuth can protect your private information in case the third party experiences a breach or other emergency situation.
Have you ever seen a pop-up asking for permission to post on your social media feed, access your smart devices or share files across different platforms? If yes, you’ve most likely used OAuth already. But what exactly is OAuth, and how does it work? Is it safe to use this framework? Let’s find out — and more!
What Is OAuth?
OAuth (vaguely termed OAuth authentication) is a secure way to give apps access to your information on other websites. The best part? You don’t have to share your password. Imagine you want a fitness app to access your workout data on a separate health app. With OAuth, you can grant the fitness app permission to access that specific data without giving it your login credentials for the health app.
That said, people often wonder: Is OAuth authentication or authorization? Despite the name, OAuth is about authorization, not authentication. Authentication apps like Google Authenticator verify who you are (like checking your ID at a store). Authorization determines what you can do once you’re verified (like granting access to specific sections of the store). OAuth focuses on the latter, letting you control what parts of your data apps can access on other platforms.
How Does OAuth Work?
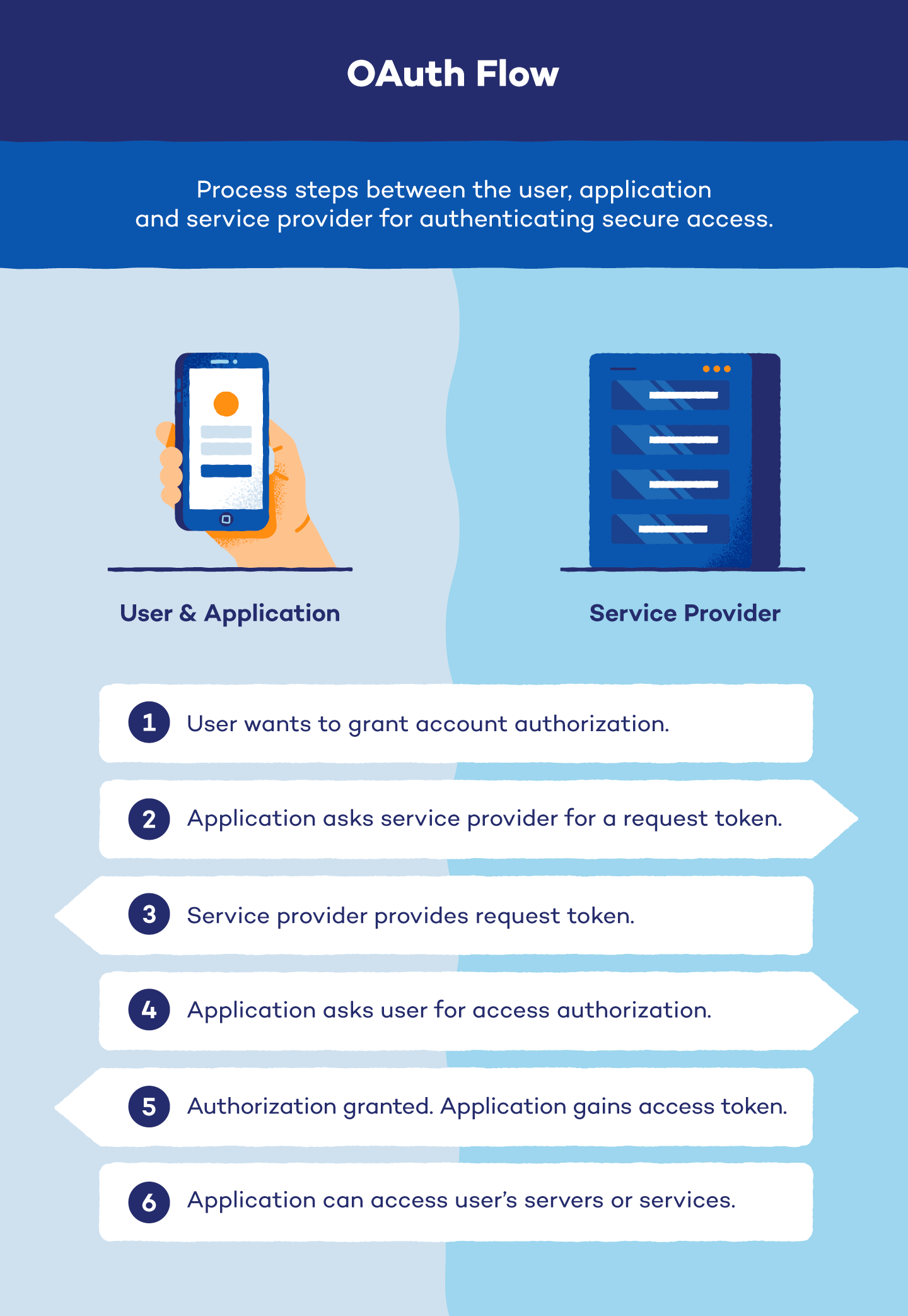
After you have given a third party access to your account, a six-step OAuth process begins automatically. There are three groups involved in this process, known as OAuth flow: the user, the third party referred to as the application and the service provider.
In most cases, the user is the original owner of the profile in question, the application is who wants access to the profile and the service provider is where the profile in question resides.
Steps in OAuth flow:
- Reveal intent: The user reveals that they want to give permission to an application to access protected servers or services. This intent is most often revealed during interactions with social media apps or file sharing across systems.
- Ask for service provider’s permission: The application requests permission from the service provider for authorization. If it is granted, the service provider gives the application a request token and shares a randomly generated password known as a secret with the user. The user will sign each authentication request with the secret so the service provider can verify they are truly making the request.
- Be redirected: The application gives the user the request token. They are then redirected to the service provider to provide application authorization.
- Ask for user permission: The user authorizes the request token. When authorized, the application returns to the service provider without pharming for passwords or usernames. The service provider will ask the user what permissions to grant and approve the request token.
- Gain access token: The application exchanges its request token for an access token and secret from the service provider.
- Access user profile: Every time the application accesses the user’s servers or services, it must present its access token and secret to the service provider.
Instead of divulging password information to third-party users, OAuth uses tokens to authorize a user’s identity, their connection to an account and their service providers. An OAuth token is safer than sharing password information and is also protected by a secret known only by the user, application and service provider.
SAML vs. OAuth
Security Assertion Markup Language (SAML) is often compared to OAuth. The former can be referred to as OAuth’s “older sibling” because of the similarities between the two programs. Because SAML uses XML and cookies to give users access to web maps while both authenticating and authorizing credentials, it eventually became too outdated for high-tech mobile, web and gaming applications.
While these two protocols share some similarities, there are a variety of important differences between them.
Differences Between OAuth and SAML
| OAuth | SAML | |
|---|---|---|
| Definition | Open-standard authentication framework for users and applications | Open standard that passes authorization credentials to service providers |
| Format | JSON | XML |
| User Experience | Uses API calls to provide a simple mobile experience | Uses session cookies for enterprise security |
| Best Used For | Mobile apps, modern web apps, game consoles and Internet of Things (IoT) devices | Single sign-on applications |
OAuth 1.0 vs. OAuth 2.0
While OAuth is a standard authentication framework, there have been different versions of its protocols. OAuth 1.0 is the original open-standard authentication framework, while OAuth 2.0 is the newer, more mainstream version. Because OAuth 2.0 was expected to replace older versions of the framework, 1.0 and 2.0 are incompatible. However, websites can support both versions of OAuth, even though there are major differences between the two.
| OAuth 1.0 | OAuth 2.0 |
|---|---|
| More secure than OAuth 2.0 | Supported by more sites and devices |
| No OAuth token expiration | Less secure than OAuth 1.0 |
| Less complex than OAuth 2.0 | Request tokens are short-lived while refresh tokens last longer |
| Uses cryptographic requirements for the transmission of tokens and secrets | Does not support encryption, signatures or channel binding |
| Only supports three flows that don’t cover non-browser or mobile device applications | User needs a secondary protection protocol like Transport Layer Security (TLS) |
| Secret signatures are simpler |
OAuth 2.0 is the more widely accepted version of the framework. Many high-level websites and experts encourage users to make this their standard authentication protocol since it offers a more secure, flexible and user-friendly authorization experience compared to OAuth 1.0.
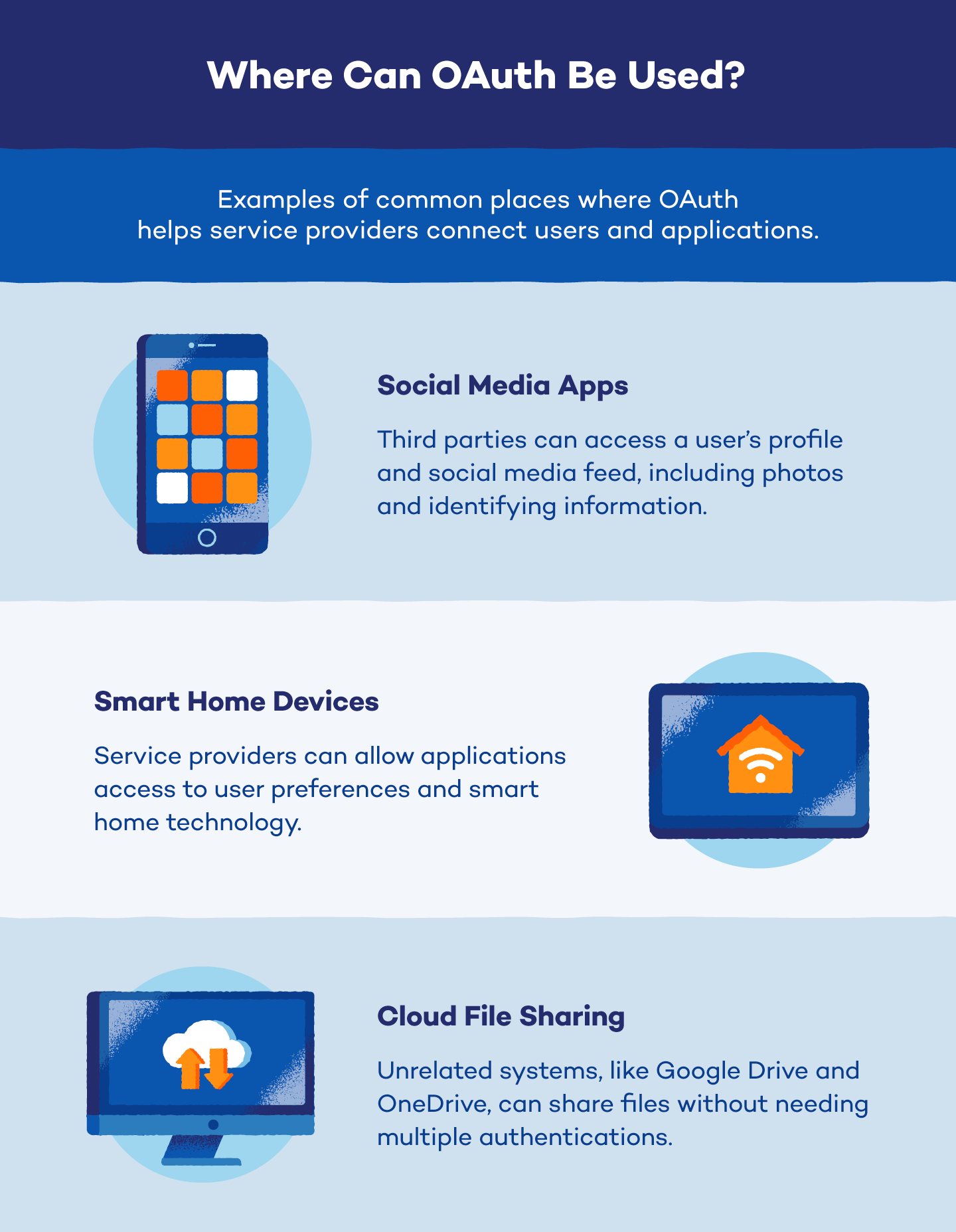
OAuth Examples
Third-party applications have started using OAuth to access user profiles, post to accounts and log in to websites and mobile applications more frequently. Here are a few examples of how you can use OAuth with social media apps, smart home devices and the cloud to share files. While these represent some of the most common uses of OAuth, the protocol finds application in various other areas as well.
Social Media Apps
Social media platforms like Facebook store user profiles and control access to that data. To access this information, external apps need an OAuth token (and secret) granted by the platform. This ensures users control what data is shared and prevents apps from accessing unauthorized information.
For example, if you want an app like ESPN to post updates on your Facebook, it needs Facebook’s permission. Facebook grants access tokens after you authorize the request, keeping your login credentials secure.
Smart Home Devices
Smart home devices, like Nest Learning Thermostat, control user data and require OAuth for secure access. This ensures third-party apps get authorized user permission before accessing information like temperature settings or controlling your home, such as turning lights on or off based on security alerts.
Cloud File Sharing
Sharing cloud files across platforms can be tricky without OAuth. Let’s say you want to share your Google Drive wedding album with parents using Microsoft OneDrive. OAuth lets you securely grant access without them needing extra accounts.
While cloud storage encrypts content, OAuth adds another layer of protection when sharing data. However, both platforms need to support the same OAuth version for a smooth connection.
OAuth FAQ
Got OAuth questions? We’ve got answers! Dive into this FAQ section to learn more about how OAuth works and how it keeps your data safe.
Is OAuth Safe?
There is yet to be a perfectly safe solution to keeping passwords and credentials secure when providing third parties with authenticated access. However, using OAuth (specifically OAuth 2.0) can substantially increase security during the authentication and authorization processes. Plus, combining OAuth with Transport Layer Security (TLS) or Secure Sockets Layer (SSL) can further increase the safety of credential authentication.
What Is OAuth Used For?
OAuth is used for secure authorization instead of sharing passwords. It allows apps to access your personal information on other platforms with your permission. This way, you control what data is shared and keep your passwords secure.
What Is the Difference Between OAuth and Standard Authentication?
Let’s say you want to share your epic workout playlist from Spotify with your fitness instructor. With a standard login, you’d have to give them your password! OAuth login lets you grant the instructor access to your Spotify playlist directly without ever revealing your password. They get what they need, and your login stays secure.
What Is OAuth Token?
An OAuth token is a digital key that lets authorized apps access specific parts of your data on other platforms. Imagine you have a house party — OAuth tokens are like guest passes.
After learning “What is OAuth?” you may be wondering how to avoid being hacked or losing your login credentials. Without proper authentication and authorization practices, it’s easier for outside forces to hack your accounts using man-in-the-middle attacks and other credential-stealing attacks.
Being proactive and understanding your security environment is the best way to avoid cyberattacks that steal your credentials. Secure your network and internet access by investing in a VPN with Panda Security, and practice password security by using our password manager.





