Pharming definition: Pharming is a cyberattack that redirects users from legitimate websites to fake ones, often without their knowledge.
Picture this: You enter your bank’s URL, but instead of the real site, you’re unknowingly directed to a counterfeit one. This is pharming — an alarming cyberattack that tricks users into handing over sensitive information like passwords or financial details. For home users, the dangers of pharming are real, and it can happen without you even knowing.
Pharming is especially harmful because it doesn’t rely on user actions like clicking suspicious links. Instead, cybercriminals use malicious code to redirect you to fake websites automatically. Learn more about this attack and how you can prevent it.
What Is Pharming?
In pharming scams, hackers manipulate website traffic, redirecting users to fake websites without their knowledge. Unlike traditional phishing attacks, which rely on tricking users into clicking suspicious links, pharming operates in the background. Hackers install malicious code on a victim’s computer or server, altering the system’s IP address settings. As a result, even if you type in the correct URL, you’re redirected to a fake website designed to steal sensitive information.
What makes pharming particularly dangerous is its ability to target multiple users at once. Since hackers can plant malicious code on a large scale — through compromised servers or infected devices — they can execute these attacks without directly interacting with you.
Once you land on these fake websites, you may unknowingly enter personal data, such as passwords or credit card details, which cybercriminals use for identity theft or financial fraud.
How Does Pharming Work?
Pharming attacks can occur in two main ways: through DNS-based pharming or host-based pharming. Both methods rely on manipulating the way your device connects to websites, redirecting you to fraudulent sites.
Here’s how DNS attacks work:
- DNS cache poisoning: Hackers corrupt the DNS cache with false information, rerouting you to malicious websites without altering the original URL.
- Rogue DNS servers: Cybercriminals set up rogue DNS servers that automatically redirect web traffic to fake sites, making it difficult to detect the scam.
- DNS server compromise: Hackers infiltrate legitimate DNS servers, altering their records to mislead large numbers of users into visiting counterfeit websites.
- DNS hijacking: Attackers take over DNS settings on a victim’s device or router, redirecting traffic to phishing sites without the user’s knowledge.
- Credential pharming: This tactic aims to capture login credentials by directing users to fake login pages, often bypassing security measures like CAPTCHA verification.
Host-based pharming can happen through:
- Host file modifications: Malicious software modifies a device’s local host file, forcing it to redirect to fraudulent websites even when the user enters legitimate URLs.
- Malware infection: Malware infects a device, allowing hackers to manipulate DNS settings or browser configurations to redirect users to phishing sites.
- Router DNS configuration manipulation: Attackers exploit vulnerabilities in a user’s router, altering DNS configurations to reroute all connected devices to phishing websites.
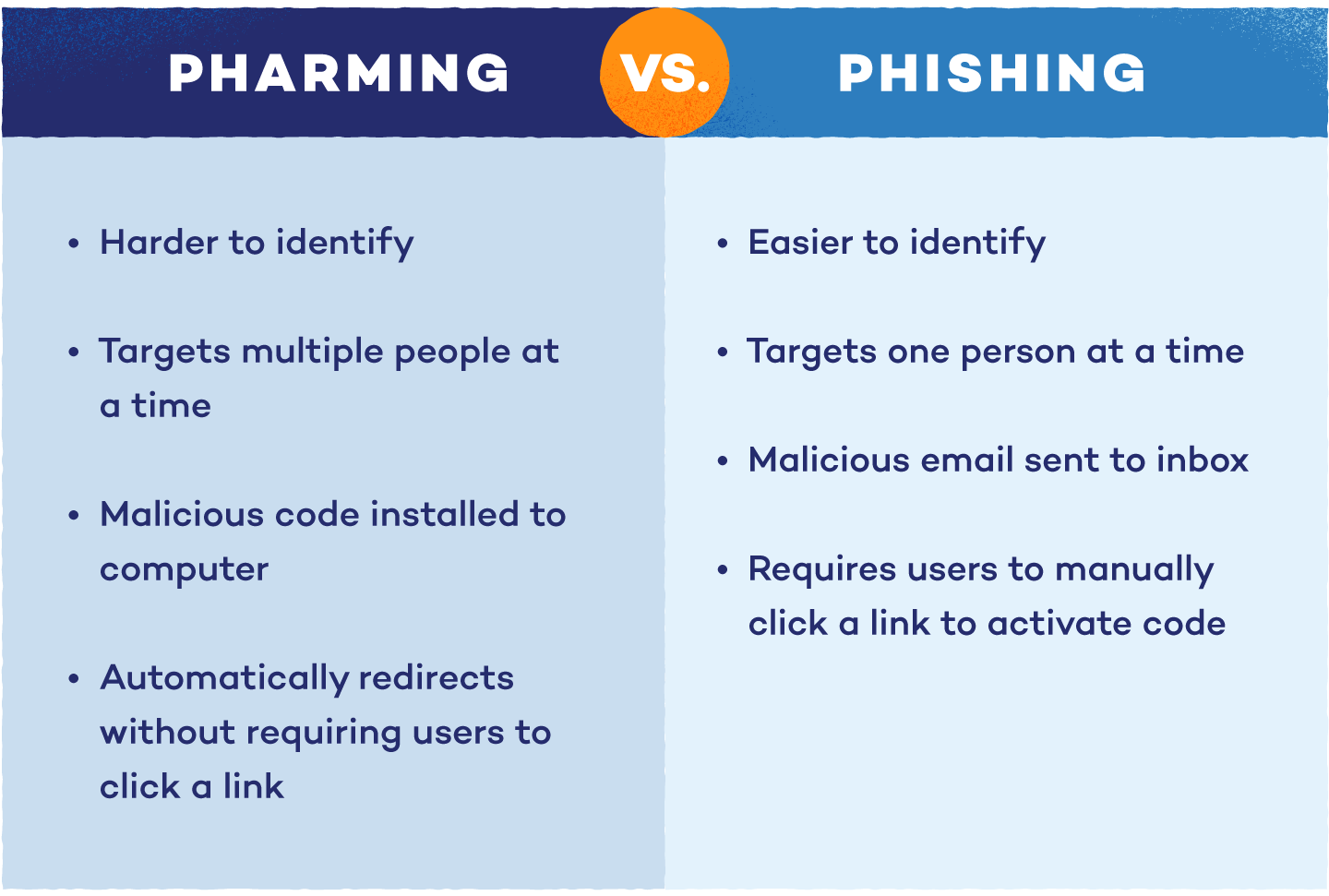
Pharming vs. Phishing
With so many “ph-” words in cybersecurity, it can be tricky to distinguish between pharming, phishing and other attacks. While both aim to steal personal information, the methods are different.
Phishing attacks trick users into sharing sensitive information by sending fake emails that appear legitimate. These emails often include links that lead to fraudulent websites or attachments that install malware. Phishing isn’t limited to email — it can also happen through text messages (smishing) or voice messages (vishing). To prevent phishing attacks, you need to be cautious of unsolicited messages and verify the sender’s legitimacy.
Pharming, on the other hand, is more covert. It redirects you to counterfeit websites without any action required, often through malware or DNS manipulation. Unlike phishing, where a user must click on a malicious link, pharming works in the background, making it harder to detect.
Pharming Examples
Pharming attacks may not always make headlines, but they can have devastating effects on individuals and organizations alike. These attacks often target financial institutions and other sensitive services, silently redirecting users to fraudulent websites. Here are a couple of examples that illustrate the dangers of pharming:
- Brazilian bank attack (2017): Cybercriminals successfully redirected all traffic from a major Brazilian bank’s website to a fake version hosted on malicious servers. Over several hours, attackers captured login credentials from countless customers, leading to significant financial losses.
- DNSChanger malware (2007): The DNSChanger malware infected millions of computers globally. It altered DNS settings and redirected users to fraudulent websites and advertisements, helping them generate millions in ad revenue.
Signs of Pharming
Pharming can be tricky to detect, but staying alert to certain red flags can help you spot potential attacks. Here are some common signs to watch for:
- Subtle changes to a link or website: If the URL looks slightly different or the website layout seems off, you may have been redirected to a fake site.
- Unsafe connection: A missing padlock icon or “not secure” warning in the browser may indicate you’re on a fraudulent site. Always check for a secure connection before entering any personal information.
- Unusual account or banking activity: Unexplained transactions or login attempts can result from a pharming attack. Monitoring your accounts closely can help catch these early.
- Unauthorized password changes: If you’re locked out of your accounts or notice a password change you didn’t initiate, it could be a sign that hackers have gained access.
- Unfamiliar apps or downloads: Unexpected software or downloads on your device may indicate a malware infection linked to pharming. Regular malware removal checks can prevent further damage.
- Pop-ups asking for personal information: Legitimate sites rarely request personal details via pop-ups, so treat these with caution.
- Emails and texts containing suspicious links: Even if the message looks official, links could lead to fake websites designed to steal your information. Always verify before clicking.
How to Prevent Pharming Attacks
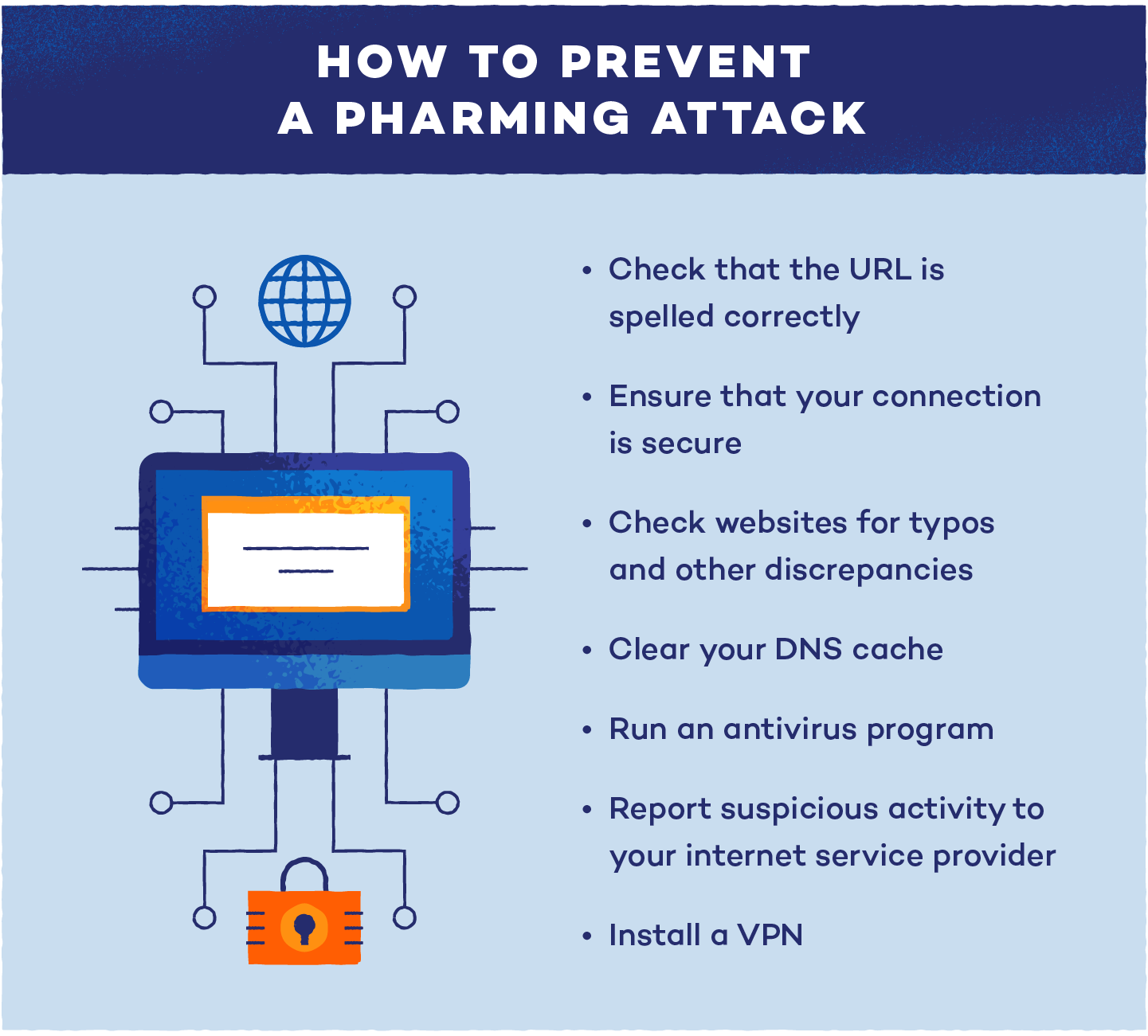
Here are some useful tips to prevent pharming:
- Clear your DNS cache regularly: If you suspect a pharming attack, clearing your DNS cache can remove any corrupted entries that might redirect you to fraudulent sites.
- Run antivirus and malware removal software: Keeping your antivirus program up-to-date is crucial for detecting and removing malicious code. Regular scans help ensure your device stays protected from hidden threats.
- Use a VPN: A virtual private network (VPN) encrypts your internet traffic, making it harder for cybercriminals to intercept your data or redirect you to fake websites.
- Enable multi-factor authentication (MFA): MFA adds an extra layer of security to your accounts, requiring multiple forms of verification. This can help prevent hackers from accessing sensitive information even if they obtain your credentials.
- Update your software and firmware: Regularly updating your device’s operating system, router firmware and browser helps patch vulnerabilities that could be exploited in a pharming attack.
- Monitor your accounts: Keep an eye on your financial and online accounts for any unusual activity, and report anything suspicious immediately.
- Use secure HTTPS websites: Ensure the websites you visit use HTTPS, which encrypts your data. This is indicated by a padlock icon in the browser’s address bar, providing an extra level of security.
- Contact your internet service provider (ISP): If you suspect that your DNS settings or server has been compromised, contact your ISP immediately for assistance resolving the issue.
Start Browsing With Confidence
Pharming attacks can have serious consequences, from stolen personal information to drained bank accounts. With hackers constantly refining their methods, it’s crucial to stay ahead of threats by being aware of the dangers and taking steps to protect your online activity. The good news? You don’t have to navigate these risks alone.
With Panda Security, you get cutting-edge tools to safeguard your browsing. From real-time malware protection to secure VPN access, Panda helps you block threats before they reach you. Whether stopping pharming attempts or preventing phishing attacks, Panda Security has the solutions to keep your data and devices safe.





