Situation
Dieser Artikel bietet Ihnen Richtlinien und Empfehlungen für die Aktualisierung des Schutzes von Panda Adaptive Defense/Panda EndPoint Protection-Produkten in Ihrer Netzwerkumgebung.Panda Security-Produkte werden in unserer QA-Abteilung und in der Vorabversionsphase umfassend getestet. Es kann jedoch vorkommen, dass es benutzerdefinierte Anwendungen und bestimmte Umgebungen gibt, die nicht vollständig abgedeckt werden. Daher besteht das Hauptziel dieses Leitfadens darin, das Risiko potenzieller Probleme zu verringern und ein reibungsloses Upgrade Ihrer Netzwerkumgebung zu gewährleisten.
Erwägungen
Wenn Sie diese Zeilen lesen, liegt es daran, dass Sie ein Upgrade Ihrer Umgebung planen, in der Regel aus Sie möchten eine neue Produktfunktion testen oder eine neue Version installieren, die eine Korrektur für ein bestehendes Problem enthält. Diese spezifischen Upgrade-Anforderungen werden in der Regel direkt mit einem Panda Account Manager oder Support-Mitarbeiter verwaltet.
Beachten Sie generell, dass ein Versions-Upgrade in einigen Fällen zu folgendem führen kann:
- Konsolen-Versions-Upgrade (transparent, auf der Seite des Panda-Servers).
- Versions-Upgrade des Agenten (transparent, erfordert keinen Neustart, auf der Seite des Endpunkts).
- Upgrade der Schutzversion.
Wie bei jeder anderen Sicherheitssoftware läuft das Panda Security-Schutzmodul im Hintergrund des Betriebssystems. Daher kann es erforderlich sein, Treiber zu deinstallieren/installieren, was wiederum einen Neustart des Computers erforderlich machen kann.
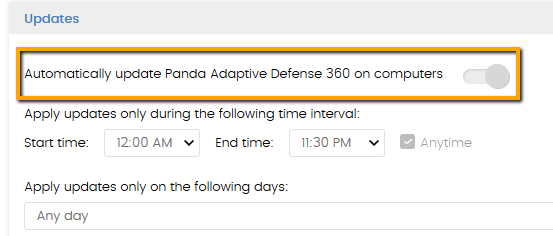
Dieser Artikel bezieht sich auf die Aktualisierung der Schutzversion, die das sensibelste Modul unserer Sicherheitsprodukte ist. Denken Sie daran, dass das Schutz-Upgrade über die Verwaltungskonsole konfiguriert wird:
|
Implementierung eines kontrollierten Schutz-Upgrade-Prozesses
Für den oben genannten Zweck werden wir einen kontrollierten Schutz-Upgrade-Prozess durchführen. Auf diese Weise beschränken wir den Aktualisierungsprozess auf einige wenige Endpunkte und Profile, die Sie als Netzwerkadministrator nach Ihren Kriterien festlegen. Sobald Sie die korrekte Funktionsweise nach der Schutz-Aktualisierung überprüft haben, empfehlen wir Ihnen, den Prozess schrittweise für den Rest Ihres Netzwerks zu planen und durchzuführen. Befolgen Sie die folgenden Schritte:
- Deaktivieren Sie die Upgrade-Option in allen Ihren Profilen.
- Erstellen Sie ein Profil und eine Gruppe und fügen Sie eine Reihe von Feldern ein, die Sie als Netzwerkadministrator als repräsentativ für Ihre Umgebung betrachten:
- Endpoints: Standardendpunkt, Endpunkt mit wichtigen Geschäftsanwendungen, Endpunkte mit den für das Managementteam spezifischen Einstellungen usw.
- Server mit den wichtigsten benutzerdefinierten Anwendungen usw.
- Aktivieren Sie das Upgrade für dieses Profil.
- Überwachen Sie das Upgrade über einen angemessenen Zeitraum, z.B. 1-2 Wochen, um sicherzustellen, dass das Upgrade in diesen Boxen durchgeführt wurde und alle Anwendungen wie erwartet funktionieren. Denken Sie daran, dass das Upgrade in den meisten Fällen einen vollständigen Neustart erfordert. Wenn Sie ein Problem feststellen, klicken Sie bitte hier wenden Sie sich bitte an Ihren Panda-Supportvertreter.
- Teilen Sie die Bereitstellung des Schutz-Upgrades für Ihr Netzwerk schrittweise auf. Der Prozess kann in 2-3 Phasen erfolgen, abhängig von Ihrer Netzwerkkonfiguration (Anzahl der Endpunkte, Server usw.).
Berücksichtigen Sie, dass, um den besten Schutz Ihrer Umgebung zu gewährleisten, ALLE Endpunkte Ihres Netzwerks, einschließlich Ihrer Server, auf den neuesten Schutz migriert werden müssen, um die neueste verfügbare Technologie zu erhalten. Daher wäre es ratsam, das Upgrade des Panda-Schutzes in Ihr nächstes geplantes Wartungsfenster aufzunehmen, das Sie planen.
Von diesem Zeitpunkt an muss jede weitere Installation in Ihrem Netzwerk mit dem neuesten Installationsprogramm erfolgen, das in der Panda-Verwaltungskonsole verfügbar ist. Alte Installationsprogramme mögen zwar funktionieren, aber sie führen zu unnötigem Bandbreitenverbrauch und Upgrades.
Außerdem ist es ratsam, wenn Sie Gold-Images oder ein anderes Imaging-System verwenden, z. B. virtuelle Boxenaufnahmen, so bald wie möglich ein Upgrade des Adaptive Defense/Endpoint Protection-Agenten auf die neue Version zu planen.