Aether shows the technique of exploitation that has been detected within the activity of exploits, along with the program that has been compromised.
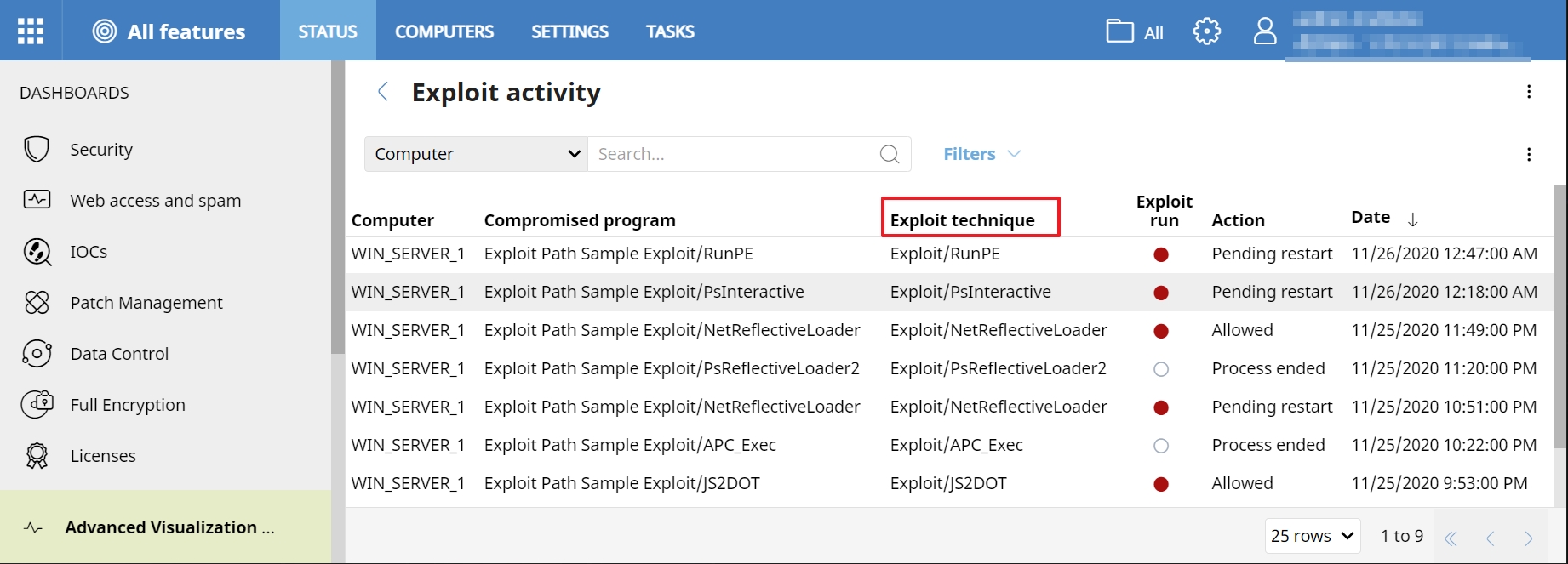
Below you can find the different techniques monitored, as well as a brief description of these:
Exploit/Metasploit
The Metasploit Framework is a testing platform that enables its users to create, test, and execute exploit code. If Panda products detect a metasploit shellcode signature, it appears as an Exploit/Metasploit exploit technique.
Exploit/ReflectiveLoader
Reflective DLL injection uses reflective programming to load a library from memory into a host process without detection. If Panda products detect a reflective executable loading (for example, metasploit or cobalt strike), it appears as an Exploit/ReflectiveLoader exploit technique.
Exploit/RemoteAPCInjection
The asynchronous procedure call (APC) is a legitimate way to run code in a process thread that waits for data without consuming resources. To evade process-based defenses and possibly elevate privileges, attackers can use the APC queue to inject malicious code into a process. APC injection executes arbitrary code in the address space of a separate live process. If Panda products detect remote code injection by an APC, it appears as an Exploit/RemoteAPCInjection exploit technique.
Exploit/DynamicExec
Code injections occur when applications allow the dynamic execution of code instructions from untrusted data. An attacker can influence the behavior of the targeted application and modify it to get access to sensitive data. If Panda products detect the execution of code in pages without execution permissions (32-bits only), it appears as an Exploit/DynamicExec exploit technique.
Exploit/HookBypass
Hooking refers to the interception of function calls, system events, or messages. The code snippets that perform these interceptions are called hooks. WatchGuard Endpoint Security products use hooks to monitor events in the operating system. If Panda products detect a hook bypass in a running function, it appears as an Exploit/HookBypass exploit technique.
Exploit/ShellcodeBehavior
Shellcode is a small piece of machine code used as the payload in the exploitation of a software vulnerability. Exploits commonly inject a shellcode into the target process before or at the same time as they exploit a vulnerability. If Panda products detect the execution of code on MEM_PRIVATE pages that does not correspond to a Portable Executable (PE), it appears as a ShellcodeBehavior exploit technique.
Exploit/ROP1
Return-oriented programming (ROP) is an exploit technique that enables attackers to control the call stack and program control flow. The attacker then executes machine instruction sequences that are already present in the machine memory. These instructions usually end in a return instruction and are located in a subroutine within an existing program or shared library code. If Panda products detect the execution of memory management APIs when the stack is out of the thread limits, it appears as an Exploit/ROP1 exploit technique.
Exploit/IE_GodMode
Windows God Mode enables you to quickly access administrative tools, backup and restore options, and other important management settings from a single window. This includes Internet options. If Panda products detect God Mode in Internet Explorer, it appears as an Exploit/IE_GodMode exploit technique.
Exploit/RunPE
RunPE is a type of malware that hides code inside a legitimate process. It is sometimes referred to as a hollowing technique. If Panda products detect process hollowing techniques or RunPE, it appears as an Exploit/RunPE exploit technique.
Exploit/PsReflectiveLoader1
Hackers commonly use reflective loaders to extract sensitive information, such as passwords and credentials, from system memory. If Panda products detect a PowerShell reflective loader in the computer, such as mimikatz, it appears as an Exploit/PsReflectiveLoader1.
Exploit/PsReflectiveLoader2
Hackers commonly use reflective loaders to extract sensitive information, such as passwords and credentials, from system memory. If Panda products detect a PowerShell reflective loader in a remote computer (not the local computer), such as mimikatz, it appears as an Exploit/PsReflectiveLoader2.
Exploit/NetReflectiveLoader
Hackers commonly use reflective loaders to extract sensitive information, such as passwords and credentials, from system memory. If Panda products detect a NET reflective loader, such as Assembly.Load, it appears as an Exploit/NetReflectiveLoader exploit technique.
Exploit/JS2DOT
js2-mode is a JavaScript editing mode for GNU Emacs (a free, customizable text editor). If Panda products detect a JS2DOT technique, it appears as an exploit technique.
Exploit/Covenant
Covenant is a .NET collaborative command and control platform for cybersecurity professionals. If Panda products detect the Covenant framework, it appears as an exploit technique.
Exploit/DumpLsass
Adversaries can attempt to access credential material stored in the process memory of the Local Security Authority Subsystem Service (LSASS). If Panda products detect an Lsass process memory dump, it appears as an exploit technique.
Exploit/APC_Exec
To evade process-based defenses or elevate privileges, attackers can try to inject malicious code into processes in the asynchronous procedure call (APC) queue. APC injection is a method that executes arbitrary code in a separate live process. If Panda products detect local code execution through APC, it appears as an Exploit/APC_Exec exploit technique.
Exclusions
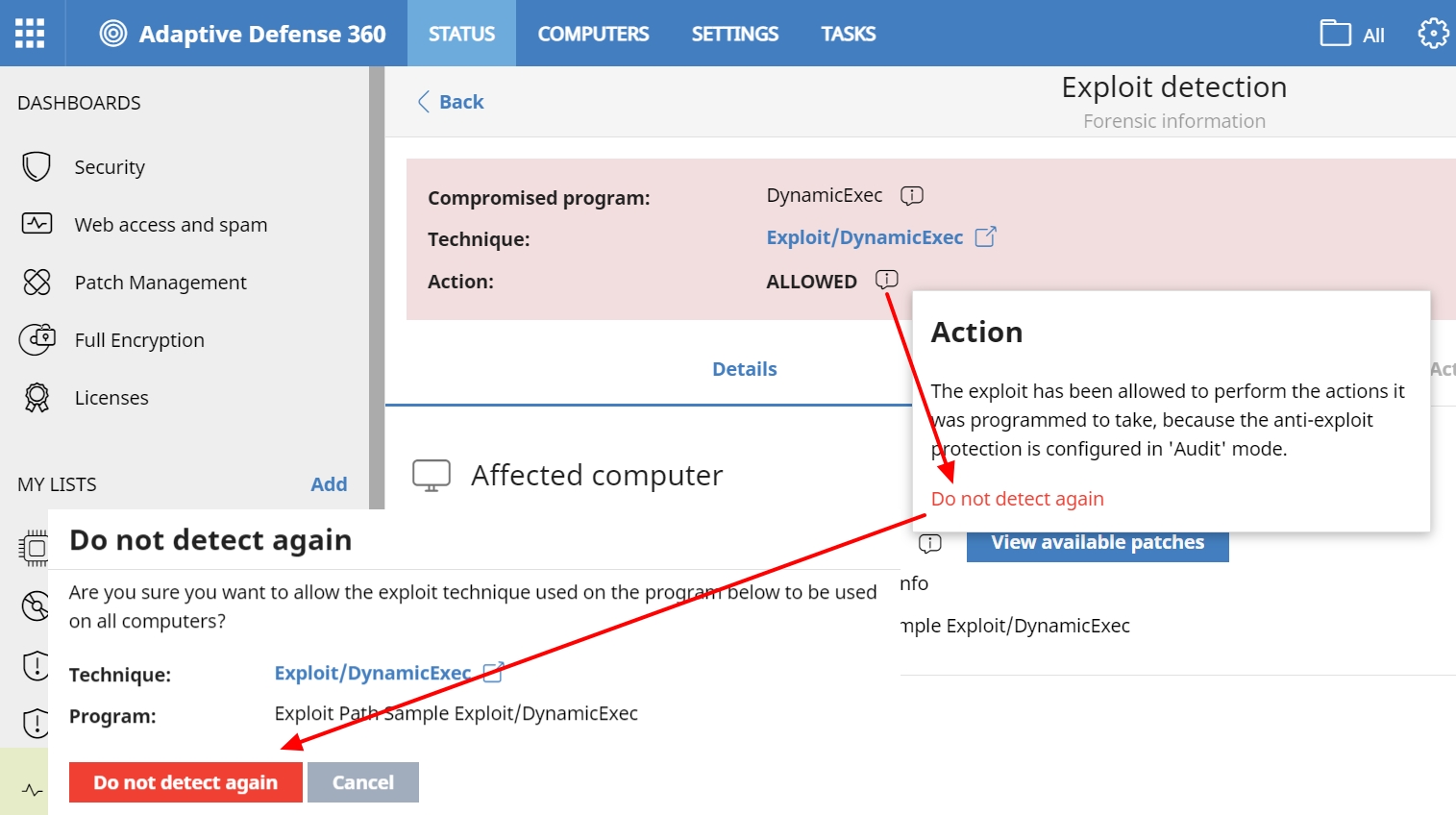
Additionally, the possibility of excluding the detection of a technique for a specific program has been added. In this way, in the event that the client wants to allow, for whatever reason, an exception for a specific process or program, it can be done, and continue to protect the rest of the processes against this attempt at exploitation.
To do this, in the detection of the exploit, within the tooltip accessible from Action, there is the option Do not detect again.