In today’s increasingly interconnected digital world, even the most secure organizations face ever-growing cybersecurity risks. Sophisticated cyberattacks, data breaches, natural disasters and other unforeseen events can disrupt business operations, or worse — they can compromise sensitive information and damage an organization’s reputation. Businesses must have a well-defined incident response plan to protect consumers and enable a swift recovery.
Our guide can help you outline the steps you need to prepare for a cybersecurity incident — because it’s better to be safe than sorry.
Table of contents:
- What Is an Incident Response Plan?
- Why It Matters
- How to Build a Cybersecurity Incident Response Plan
- Benefits of an Incident Response Plan
What Is an Incident Response Plan?
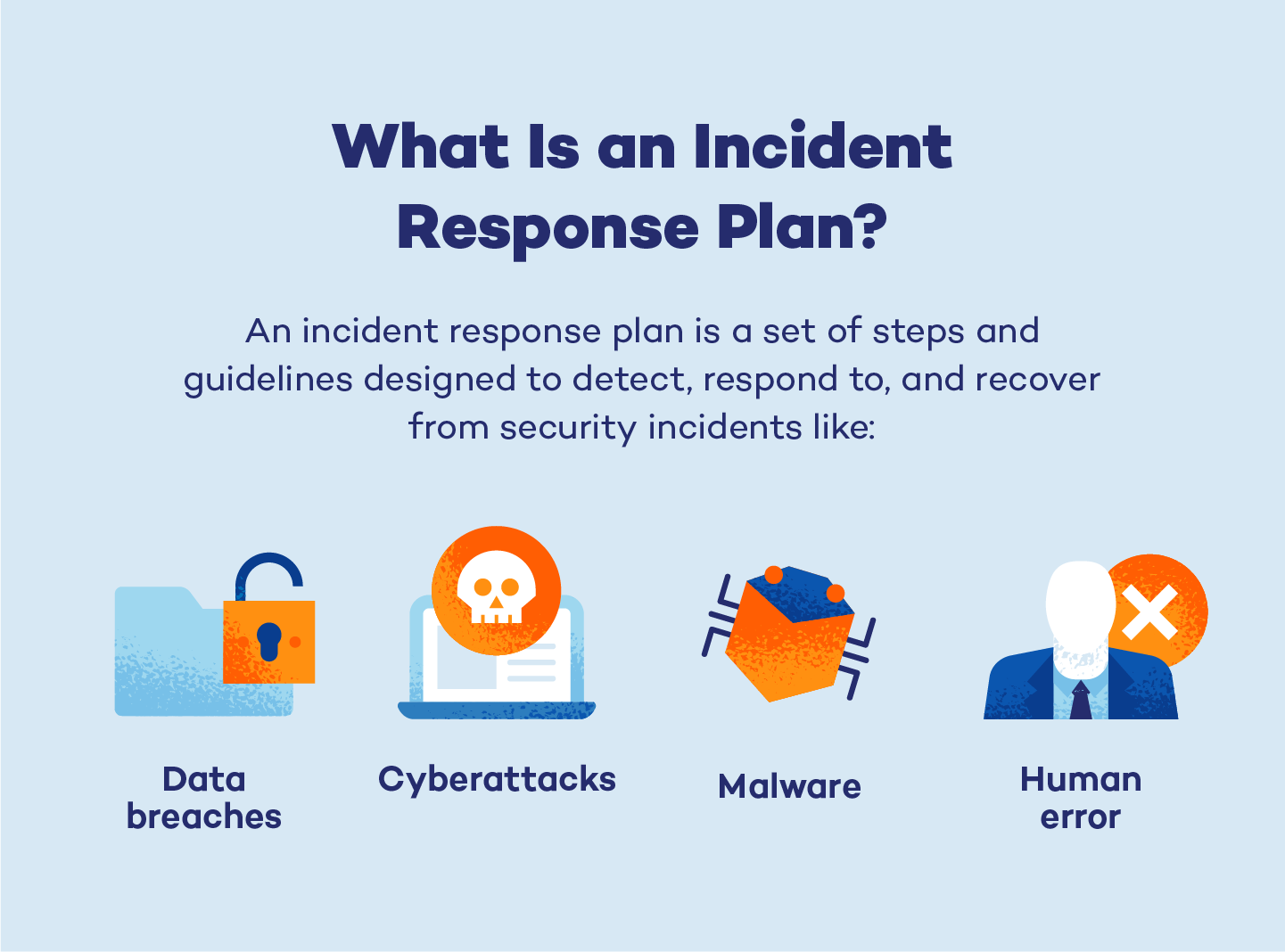
An incident response plan — sometimes referred to as a security incident response plan, or SIRP — is a comprehensive set of procedures and guidelines designed to detect, contain, eradicate and recover from security incidents swiftly and effectively.
Incident response plans help minimize the frequency and severity of cybersecurity incidents, like:
- Data breaches: security incidents where unauthorized individuals gain access to sensitive or confidential data, potentially exposing it to theft, manipulation or unauthorized use
- Cyberattacks: deliberate malicious activities launched against computer systems, networks or digital infrastructure with the intent to disrupt, steal or damage data, or gain unauthorized access
- Distributed denial-of-service (DDoS) attacks: a type of cyberattack where multiple compromised devices are used to overwhelm a target server or network with a flood of internet traffic, significantly slowing down operations and preventing legitimate users from accessing it
- Natural disasters: any incident where physical damage to infrastructure, power outages or disrupted communication networks increase an organization’s vulnerability to cyberattacks
- Corporate account takeovers (CATO): cyberattacks that occur when unauthorized individuals gain control of a company’s financial accounts, typically through phishing, malware or social engineering techniques
- Human error: vulnerabilities created by authorized users through actions such as falling for phishing scams, weak password practices, improper handling of sensitive information or unintentionally installing malicious software
Why does your business need an incident response plan?
According to a recent study, 77% of companies still lack a formal incident response plan, despite a 7% increase in cyberattacks in the first few months of 2023. Not having a SIRP in place can lead to uncoordinated and chaotic responses during cybersecurity crises, resulting in:
- Prolonged downtime
- Increased financial loss
- Compromised data security
An incident response plan allows you to identify and address an incident as soon as possible, making sure damage is minimized and solutions are applied almost immediately.
How to Build a Cybersecurity Incident Response Plan
 An incident response plan consists of a series of proactive processes that can be divided into five key phases:
An incident response plan consists of a series of proactive processes that can be divided into five key phases:
- Preparation
- Detection and analysis
- Containment and eradication
- Recovery
- Continuous improvement
1. Preparation
The first phase in constructing a cybersecurity incident response plan is to thoroughly assess potential risks and vulnerabilities within your systems, networks and processes. This means analyzing areas prone to cyberattacks, including:
- IT infrastructure
- Data storage
- Access controls
- Existing security measures
By identifying these risks and vulnerabilities upfront, you can develop appropriate strategies and countermeasures to address them effectively, enhancing the resilience and preparedness of your incident response plan.
2. Detection and Analysis
Once you’re aware of your system’s vulnerabilities, implement detection methods and tools to identify and alert you of potential security incidents. This involves deploying security technologies that can continuously monitor your networks, systems and user activities for any signs of suspicious or malicious behavior, like:
- Intrusion detection systems (IDS): Monitor network traffic and identify potential unauthorized or malicious activities, such as intrusion attempts, malware infections or suspicious network behavior.
- Intrusion prevention systems (IPS): Goes a step further than IDS by actively blocking and preventing identified malicious activities, providing real-time protection against network-based threats.
- Log monitoring tools: Detect and analyze log files generated by various systems, applications and network devices to identify unusual or suspicious activities.
- Security information and event management (SIEM): Aggregate and correlate log data from various sources, allowing for centralized monitoring, real-time alerting and advanced analytics to detect security incidents and anomalies.
- Endpoint detection and response (EDR): Focus on monitoring and protecting individual endpoints, such as desktops, laptops and servers.
- Behavior analytics: Employ machine learning algorithms and user behavior modeling to detect unusual activities and deviations from normal patterns, helping identify potential insider threats or compromised accounts.
These tools allow you to quickly respond to and mitigate potential threats by proactively detecting security incidents.
Don’t settle for a cybersecurity solution that’s only effective against select viruses and malware. Panda Security’s 100% threat detection rate has been guaranteed by the leading IT security institute AV- Comparatives, so you’ll know you’re getting the best protection available.
3. Containment and Eradication
When responding to a cyberattack, outline immediate actions to isolate and contain the security breach, preventing it from spreading further and causing additional damage. This may include:
- Identifying affected systems
- Quarantining compromised devices
- Disconnecting infected network segments
- Employing network segmentation to safeguard critical systems and sensitive data
- Temporarily revoking or restricting user access
- Utilizing external cybersecurity experts or incident response services to help contain and remediate the incident
After containment, the focus shifts to eradicating the root cause of the incident, which involves removing malware, closing vulnerabilities and implementing necessary security patches or updates.
4. Recovery
Once the incident has been contained and eradicated, you can start restoring affected systems, services and operations to their normal state. Your incident response plan should have a thorough recovery process in place that includes:
- Applying data backups to recover lost or corrupted information
- Reconfiguring systems and networks to ensure their security
- Conducting post-incident testing to verify the integrity of restored components
- Ensuring all recovery actions align with legal and regulatory requirements, particularly regarding data breach notification and incident reporting
- Installing security patches and updates to close known vulnerabilities that may have been exploited in the incident, reducing the risk of further attacks
The recovery phase aims to minimize downtime, enabling operations to resume as swiftly as possible while preventing similar future incidents.
5. Continuous Improvement
An incident response plan should be treated as a living document — as threats evolve, so should your mitigation strategy. After successfully responding to and recovering from an incident, focus on enhancing your incident response capabilities based on lessons learned through a comprehensive post-incident analysis. These analyses typically include:
- A detailed incident timeline
- A description of the attack, including attack vectors, affected systems and data exposed or compromised
- A list of response actions and their effects
- A root cause analysis
Schedule regular reviews, updates and testing of the incident response plan to ensure it remains effective against evolving threats. By consistently refining your incident response procedures, you can strengthen your ability to detect, contain and mitigate future incidents, reinforcing your overall cybersecurity resilience.
Benefits of an Incident Response Plan
Having an organized response plan in place before an incident occurs has many benefits, including:
- Insight into existing security gaps: outlines the steps taken to detect, respond to and mitigate incidents, revealing areas where vulnerabilities and weaknesses may have been exploited
- Reduced downtime and recovery time: provides predefined procedures and resources for effectively restoring systems, services and operations, enabling a quicker return to normalcy
- Protection of sensitive data: implements measures such as encryption, access controls and secure data handling protocols, reducing the risk of data compromise during and after an incident
- Ensured compliance: defines procedures for incident reporting, data breach notification and adherence to relevant regulatory requirements, helping organizations mitigate potential legal and reputational consequences
It’s imperative for organizations of all sizes to have an incident response plan in place — even better if you never have to use it. Panda Security’s premium protection services continuously scan your devices for vulnerabilities and automatically apply security patches to minimize the risk of cyberattacks. If all else fails, you’ll always have a dedicated technician ready to get you up and running again in record time.