Shortcuts aren’t just for keyboards. Digital browsers use various online shortcuts regularly — like web extensions — which can help them surf the web quickly.
Unfortunately, not all shortcuts are safe and secure. Our list of malicious Chrome extensions reveals the dangers lurking behind unlisted, poorly scanned and third-party downloads freely available across the web.
Premium protective services from Panda Security can help keep your browsers and devices safe — even from malicious extensions. Pairing these protections with knowledge about dangerous add-ons, how to detect them and ways to remove them can help online users navigate the web without compromising privacy and security.
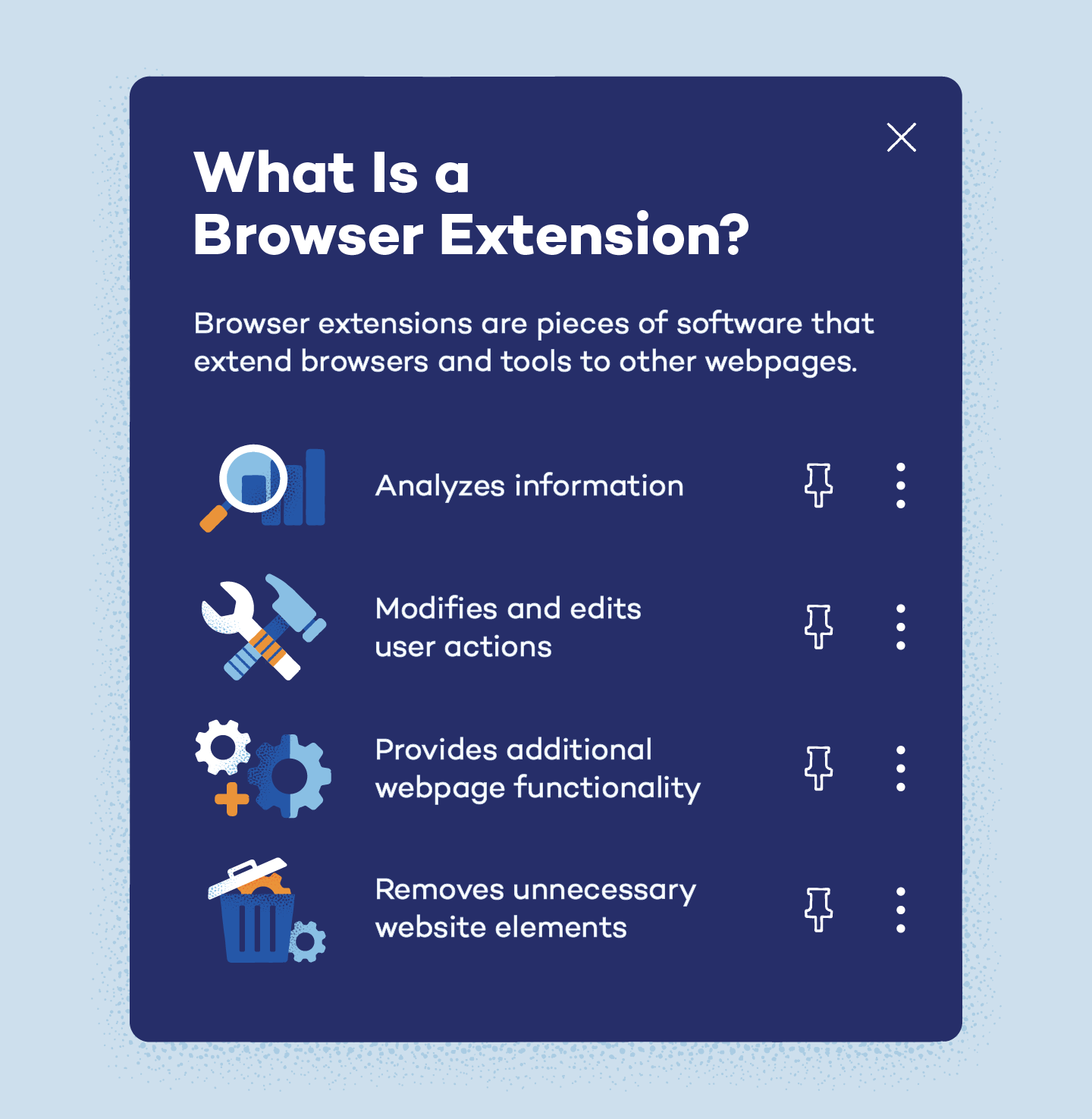
What Is a Browser Extension?
A browser extension is software that does exactly as the name suggests: it extends your browser — or specific browser tools — to other webpages. These extensions can analyze information, modify or edit user actions and provide additional functionality across various browsing sites.
Some of the most common browser extensions are Grammarly, AdBlock, LastPass, Google Calendar and Scribe. While most browser extensions are harmless and can be incredibly useful, users are still able to unknowingly download malicious software that can access personal information or cause damage to devices.
Popular Malicious Chrome Extensions
Google’s Chrome is the most popular web browser across the globe, supporting more than 130,000 unique browser extensions. Most of these unique extensions are safe and supported by Chrome itself, but a few popular extensions have been identified as malicious.
These malicious Chrome extensions can contain malware, insert affiliate links into webpages and internally damage systems. This list includes some of the most notorious extensions Chrome users should be aware of.
Netflix Party
Designed to allow synchronized media viewing, the Netflix Party extension was actually used for affiliate links. This add-on would track a user’s digital footprint and inject affiliate links into appropriate pages. The owners of this extension can then make a profit based on the user’s browsing history.
Netflix Party 2
Netflix Party 2 was similar to its predecessor Netflix Party, which also attempted to inject affiliate links into a user’s browsing. Add-ons of this variety — including Netflix Party 1 and 2 — may even conceal their malicious intentions by waiting multiple days before injecting links.
Full Page Screenshot Capture — Screenshotting
More than 200,000 users downloaded the Full Page Screenshot Capture — Screenshotting Chrome extension before its malicious behavior was uncovered. Designed to screenshot webpages in one click, this extension also tracked user data and changed the location of certain cookies on e-commerce sites to disguise a user’s origin URL as a referral site.
friGate Light
Chrome extensions have various uses, and friGate Light was designed to access locked sites and encrypt user traffic data. However, this extension also housed malware, which was used to access user data. Additionally, users downloading this extension were asked to provide friGate Light with permission to access sensitive data.
friGate CDN
Similar to friGate Light, friGate CDN was designed to provide users access to blocked websites. This extension also housed malware, which could access sensitive user data. This extension also redirected users to secondary sites via its proxy, which could have been used to collect data and further infect devices.
SaveFrom.Net
Have you ever wanted to download media from your favorite sites — YouTube, TikTok, Facebook and more — with one click? If so, you’re not alone, and that’s why SaveFrom.Net became popular. This extension allows users to download videos and music, but it also collects user data like IP addresses and browsing behavior, which has been and can be leaked when using the site.
SHARPEXT
SHARPEXT is well-known in the world of email spyware. This extension was created and deployed by SharpTongue, also known as Kimsuky. SharpTongue is an infamous bad actor known for stealing and revealing private information — including usernames and passwords. SHARPEXT was designed to infiltrate email accounts, extract sensitive data and continuously spy on user behaviors.
Hola VPN – The Website Unblocker
It’s frustrating when you need to access a website or want to watch a movie, but your country is blocked from doing so. Hola VPN is a free, unlimited website unblocker created to remove these roadblocks from a user’s online experience. However, this malicious Chrome extension has experienced various security breaches and weaknesses while secretly tracking behavior and leaving web traffic unencrypted.
Dormant Colors Campaign
The extension campaign, Dormant Colors, isn’t a single malicious Chrome extension — in fact, it’s 30 unique, dangerous add-ons that millions of users have downloaded. These extensions were injected with malicious code after their initial introduction to the web store and corrupted into information-stealing extensions. Unfortunately, this campaign is still operational even though many affected extensions have been deactivated.
How to Detect Malicious Chrome Extensions
The above list of malicious Chrome extensions only contains the most popular and dangerous add-ons. It is possible — and probable — that other extensions also contain dangerous malware or other malicious programs. These tips can help you identify malicious Chrome extensions on your devices:
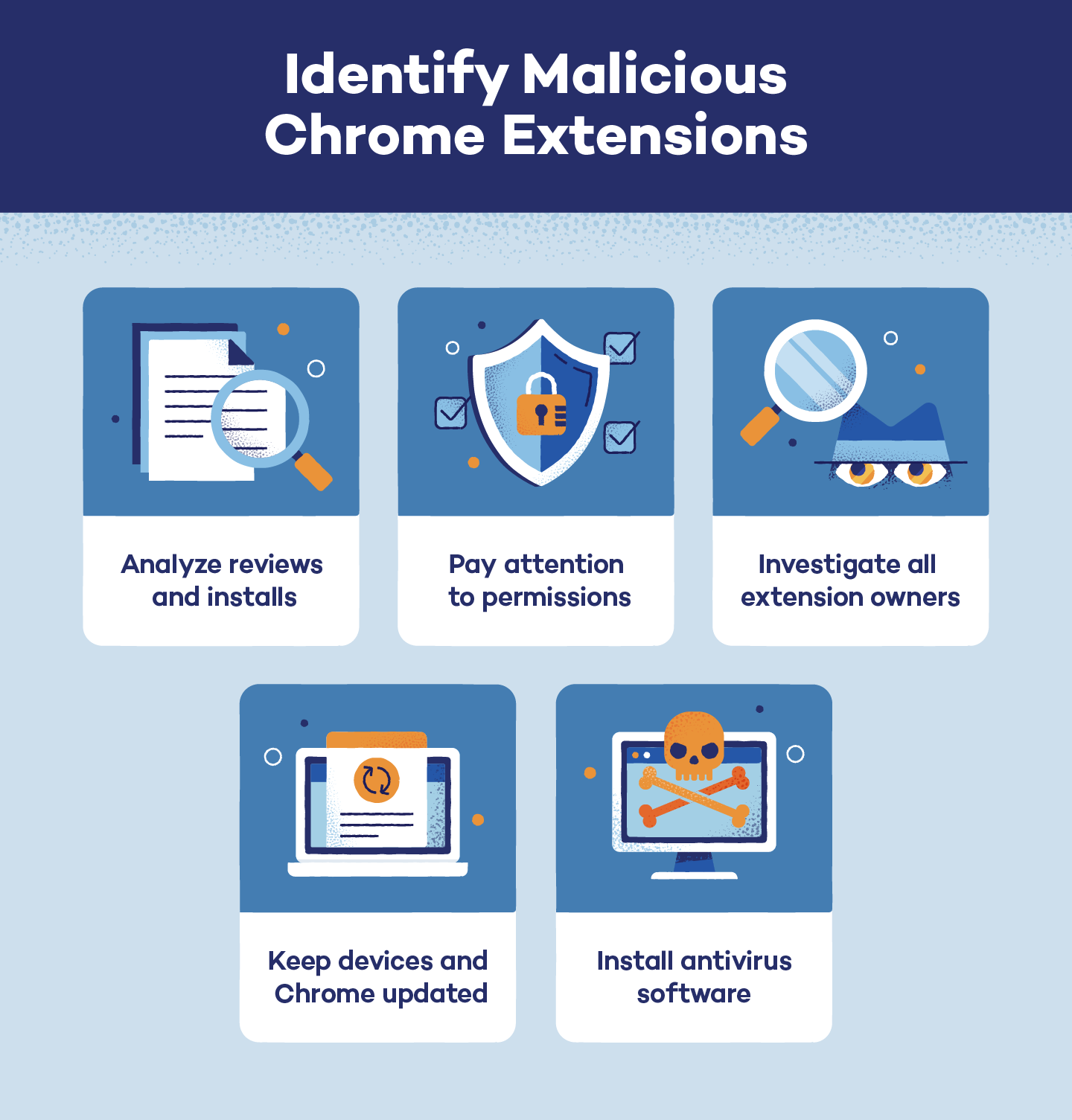
- Analyze an extension’s reviews and installs. Users who have fallen victim to a malicious Chrome extension may reveal this in a review. Additionally, extensions with fewer downloads could also be dangerous.
- Pay attention to permissions. Extensions with malicious intent may request permission to access unnecessary programs or personal information.
- Investigate extension owners. Where possible, only download extensions created and distributed by popular and well-known companies to limit potential malware downloads.
- Keep devices and Chrome updated. Updates to operating systems often include new protections against and warnings about identified malware and dangerous extensions.
- Install antivirus software. This software will automatically notify you of any malicious activity on your device.
How to Remove an Extension From Chrome
Similar to removing a virus, malicious extensions should be removed from Chrome as soon as they are detected. Once Chrome is downloaded on your device, you can remove these add-ons in 7 simple steps.
Step 1: Launch Chrome.
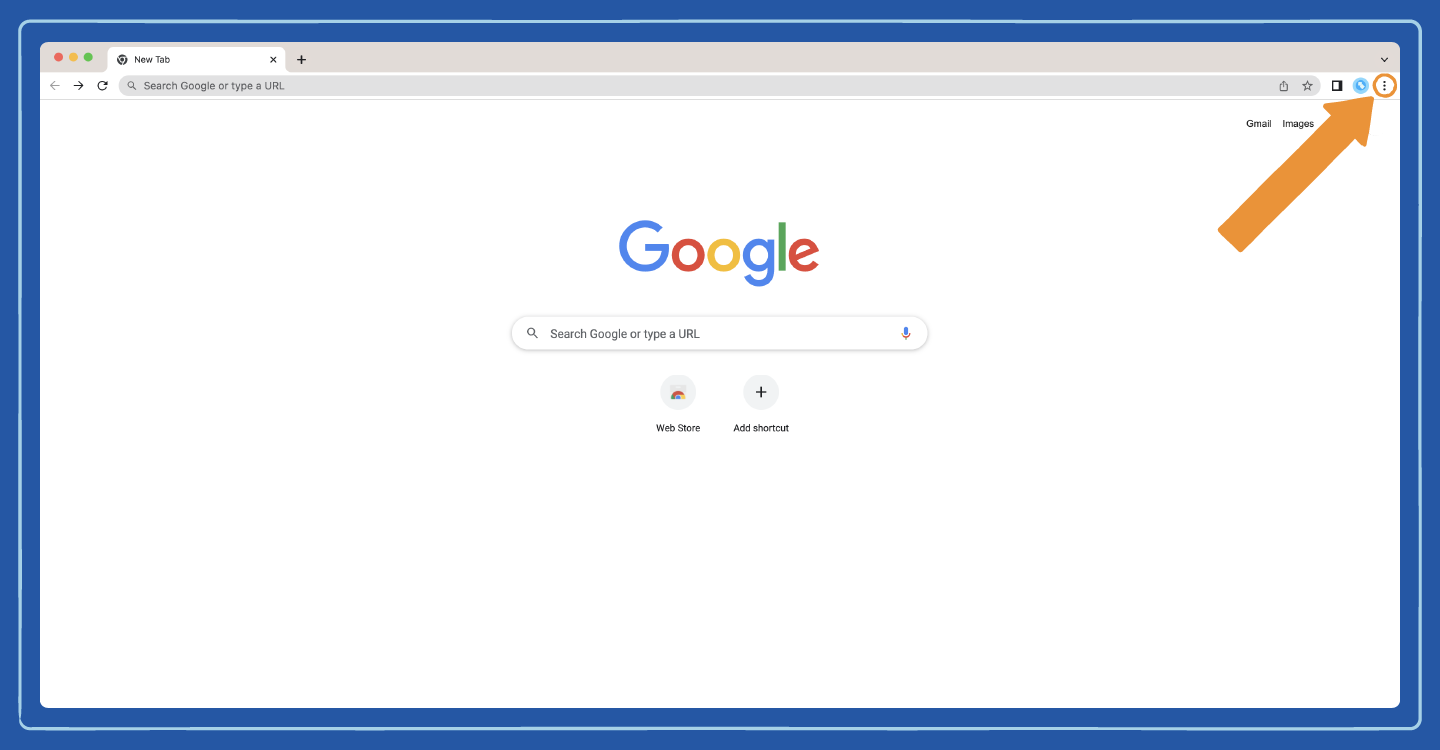
Step 2: Open Chrome settings. This can be accessed via the three vertical dots in the upper right corner.
Step 3: Open the dropdown under More Tools.
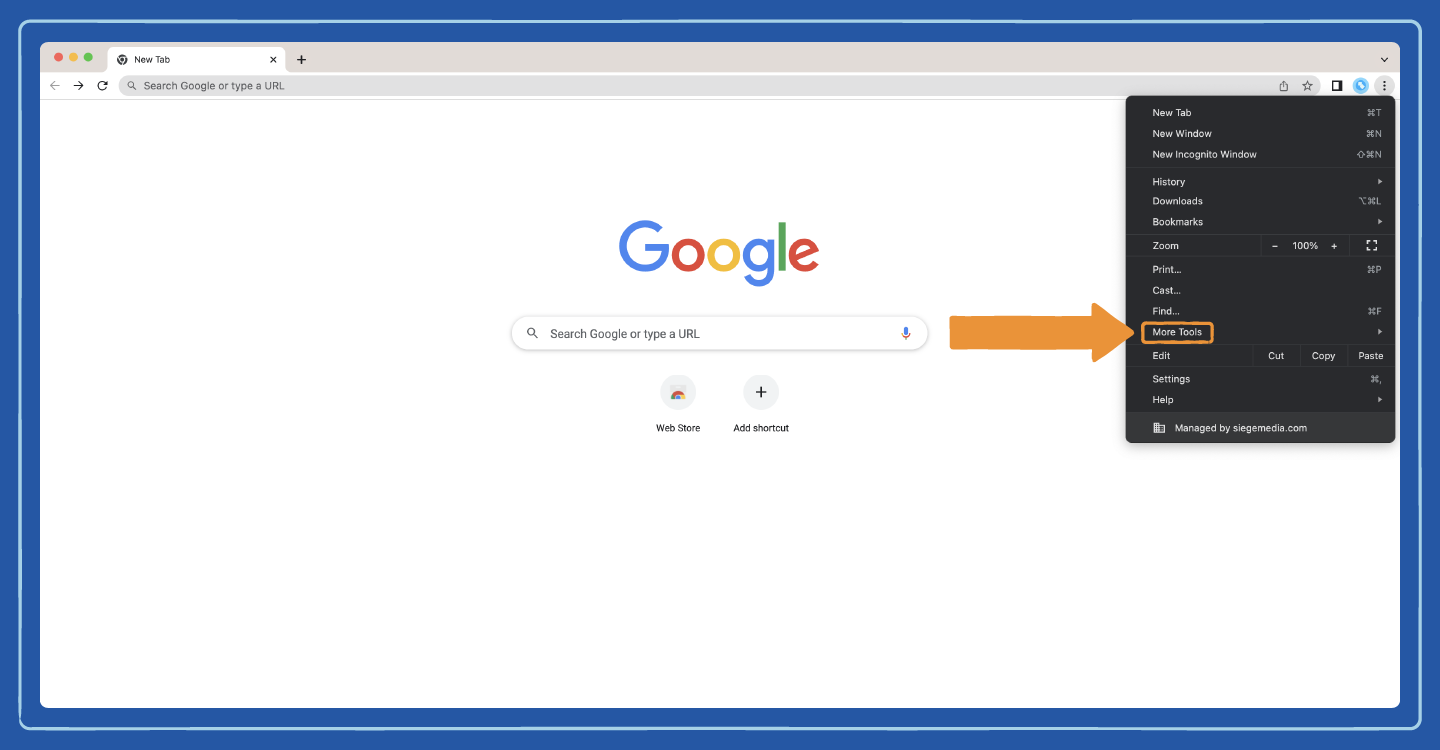
Step 4: Click on Extensions.
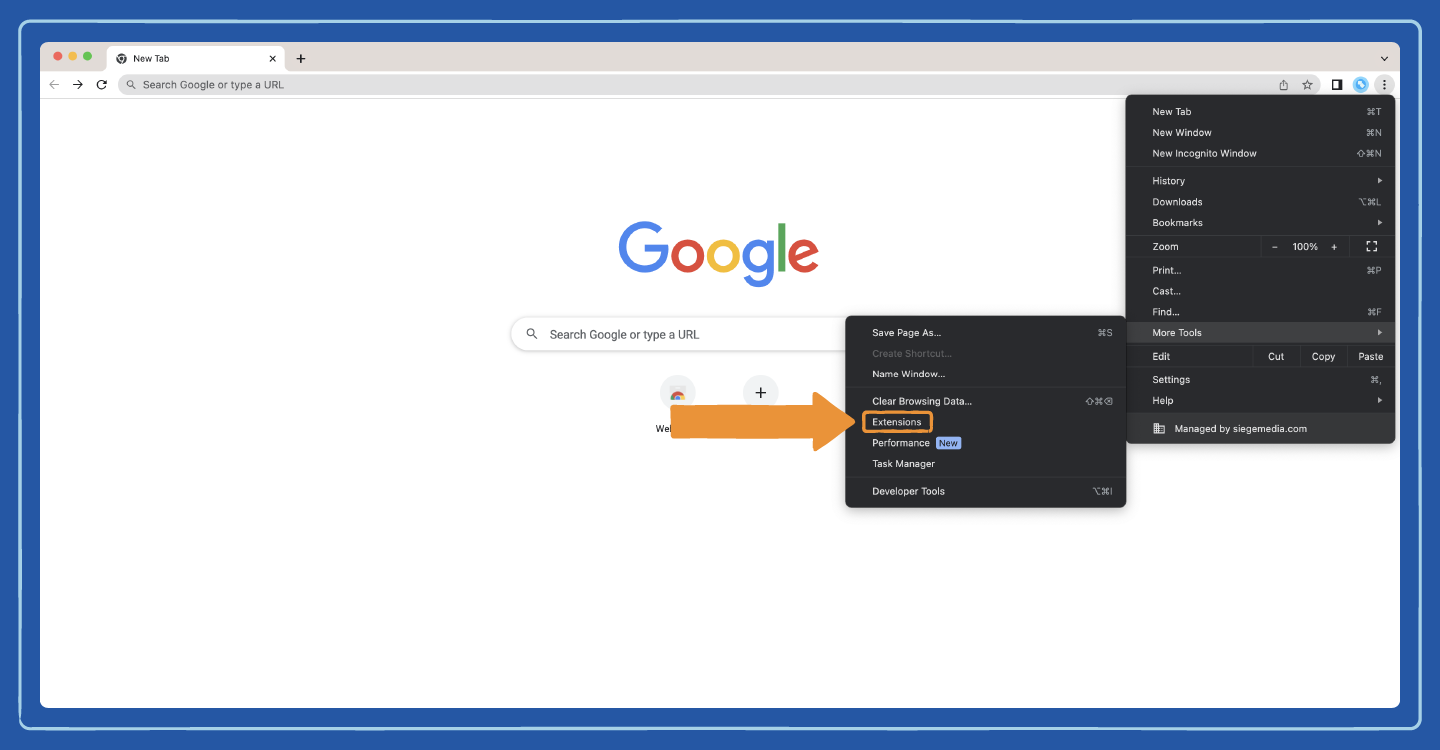
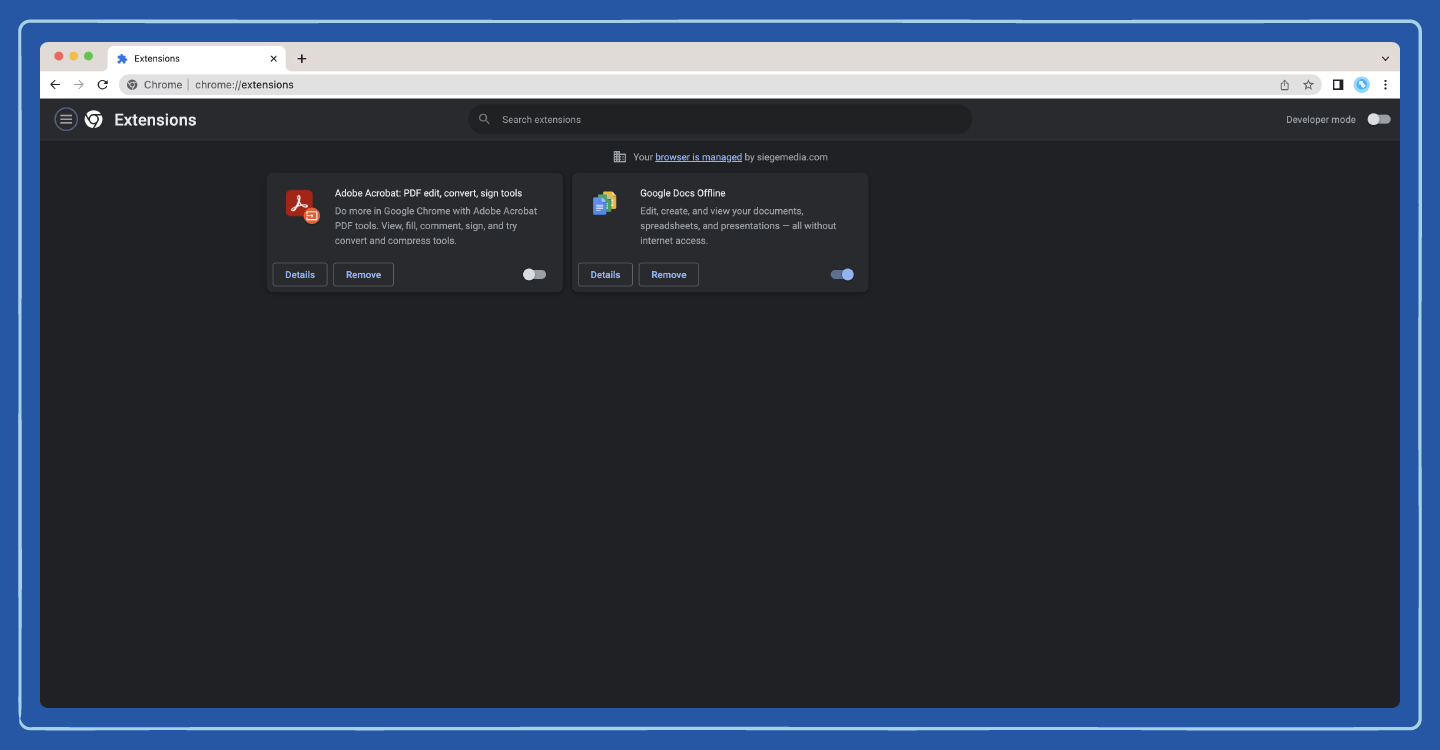
Step 5: Identify the extension you want to remove by scrolling down the page or searching for the add-on’s name.
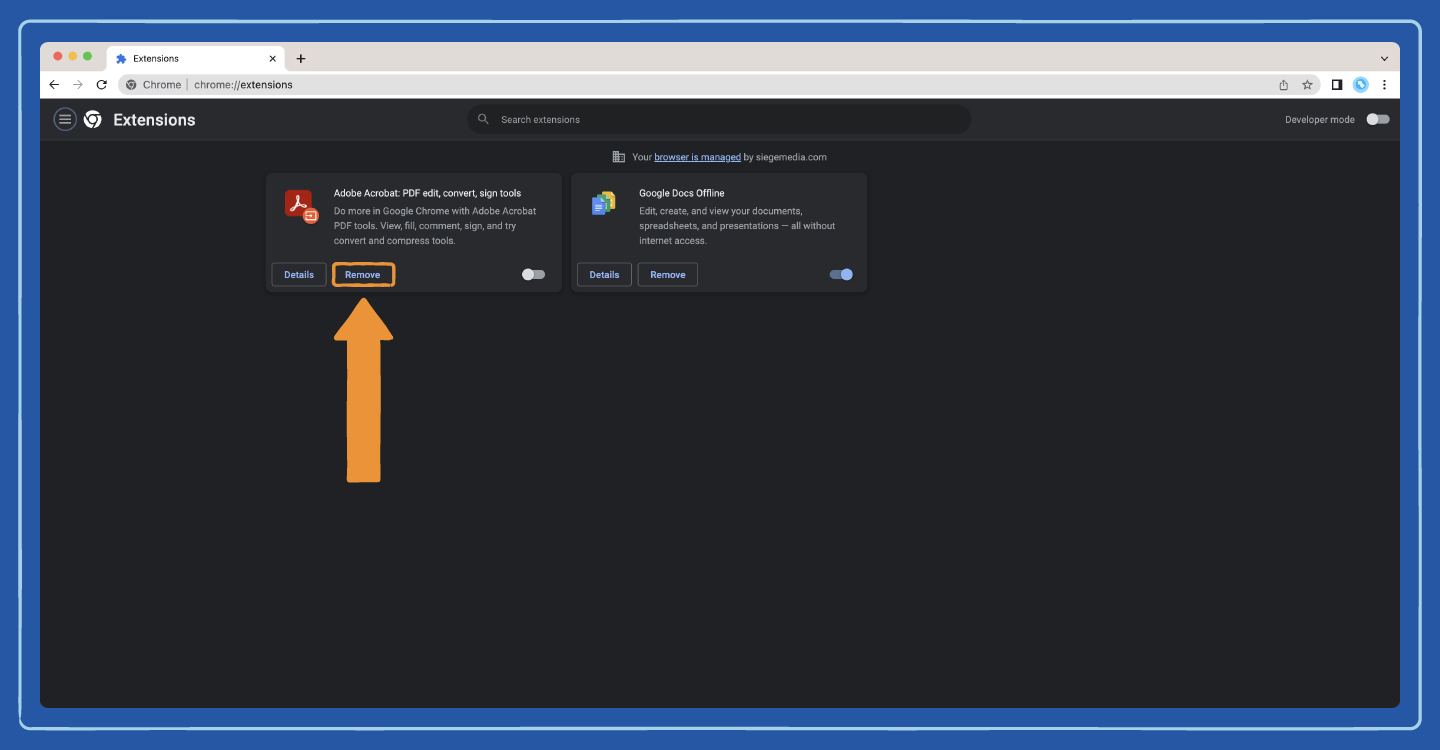
Step 6: Select Remove.
Step 7: In the pop-up screen, select Remove again.
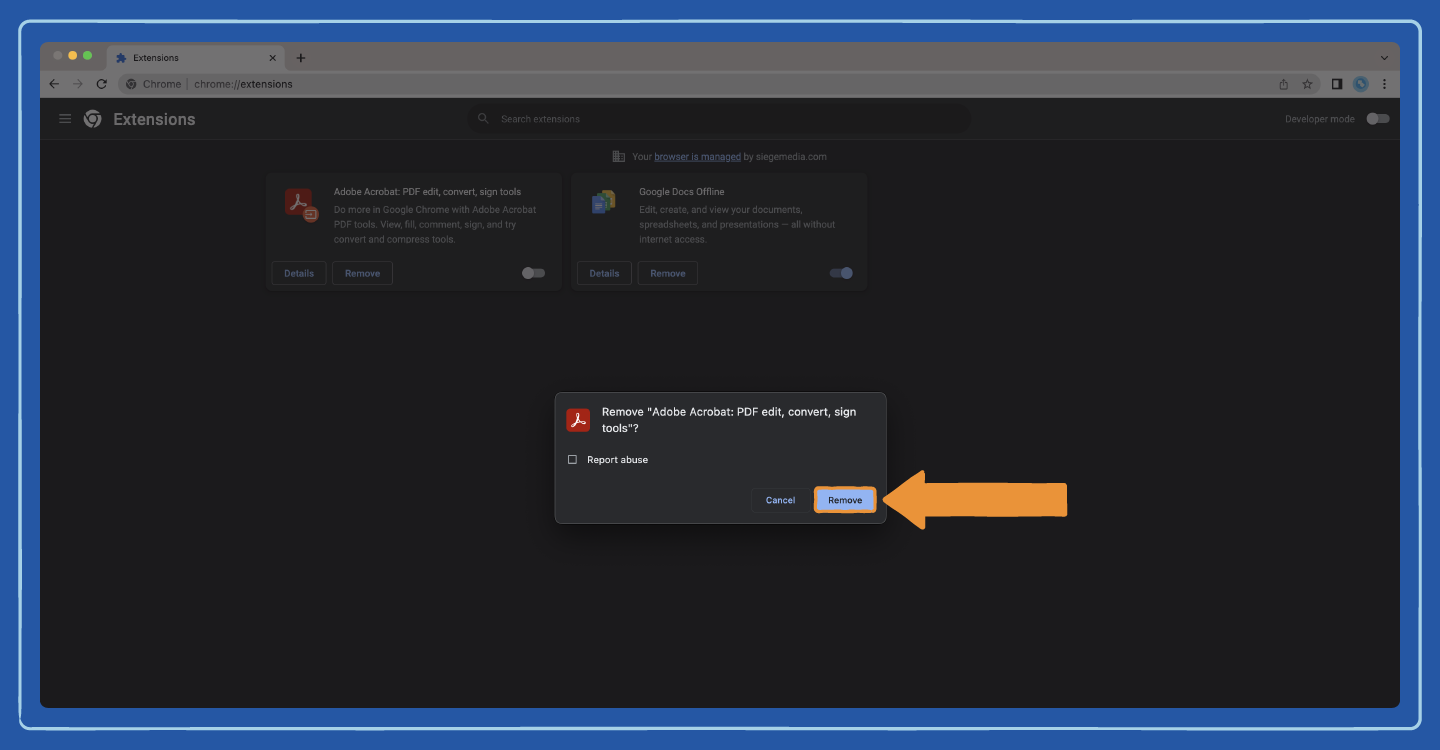
These steps can be repeated as many times as needed to remove any malicious or unwanted extensions from Chrome. Also, consider using a private search engine to help keep your information protected from potentially malicious add-ons.
While the add-ons on this list of malicious Chrome extensions do exist and can cause extensive damage to personal devices, Panda Security can help clean up your PC and optimize its systems. Chrome consistently updates add-ons and removes well-known malware from its extension library — providing additional protection against digital dangers.
Sources: Software Testing Help | Oberlo | Bleeping Computer | Wonderfox | Volexity | Top10VPN





