Have you ever stopped and wondered what the benefits of a VPN are besides granting you access to Japan’s Netflix shows? If not, now is the time.
Whether you’re browsing the web at a public coffee shop or creating a project proposal on your organization’s network, a VPN is your first line of defense against online hackers, cybercriminals and other nefarious actors. And while VPNs protect your online data, they do so much more.
If you’re thinking about installing a VPN or you’re already familiar with their services, our guide can help you understand exactly why a virtual private network is vital to online security — both personally and professionally.
1. Network Security
Unprotected networks are gold mines for organizations and cybercriminals who want to track, store and analyze personal information. With your data, these actors can do more harm than simply targeting you with ads — they can track your online whereabouts, steal passwords and usernames and more. VPNs can stop these actors from retrieving sensitive data across private and public networks.
2. Anonymity and Information Protection
VPNs hide locations and IP addresses, which can help you maintain anonymity online. Instead of seeing your personal information, hackers can only see your VPN’s server data. Additionally, VPNs use encryption to protect your identity and other sensitive information, including names, addresses, passwords and credit card numbers.

3. Data Throttling Evasion
Some internet service providers (ISPs) only allow users to consume a specific amount of data before limiting their use — known as data throttling. ISPs can choose to slow down a user’s service once they meet their data limit, but a VPN can help users avoid this limit. VPNs disguise usage, allowing users to exceed their data cap without experiencing slower service or paying for additional services.
4. Bandwidth Throttling Evasion
Similar to data throttling, ISPs can slow down a user’s internet speed. This can happen if users access certain sites or engage in suspicious online activity. Users can use VPNs to encrypt traffic and online activity, which can prevent your ISP from throttling your bandwidth.
5. Blocked Content Access
There are plenty of streaming services that lack access to a variety of shows, movies and other types of content. With a VPN, it’s possible to unlock blocked content and avoid content restrictions so you can access your favorite movies, shows and other types of media.
6. Geographic Censorship Avoidance
Online browsers and actors are only able to view your fake, secondary IP address when you use a VPN, which shows masks your geographical location. In countries where content is censored due to laws and regulations, VPNs can help bypass location tracking so users can access data of all kinds. Additionally, a VPN can change how you receive location-based quotes, access to specific services and more by helping you avoid geographic censorship.
7. Network Growth
Network expansion can be costly, especially for small businesses experiencing substantial growth. With a VPN, it’s possible to grow your network without paying too many fees — even if you’re granting access to remote users or using the cloud to store and access data and applications. Instead of paying for network access on each new device, VPNs allow users to access a single device with network or application access, which expands its reach and lowers the cost of its use.
8. Cost Reduction
With a VPN, the days of security costs are behind you — well, kind of. Instead of relying on an internal team to monitor the effectiveness of your network and protect your systems against malware attacks, you can rely on the IT support of your service provider. A VPN transfers this burden from your team to another, saving money, time, energy and data across your network.
9. Gaming Defenses
Depending on your level of gameplay, VPNs can help protect you from DDoS attacks while gaming and they can help protect your personal information from other players and game creators. Additionally, bypassing an area’s geographic censorship may even improve your network speeds and grant you access to blocked gaming content.
10. Remote Access
In the world of distributed work, remote access and security are vital. With a VPN, it’s possible for organizations to grant remote workers access to their network from anywhere in the world. This type of access can mirror the connection a user would experience within the organization itself, allowing distributed networks to be nearly identical to their counterparts.
11. Access Control
With a VPN, organizations can verify the identity of anyone attempting to enter a network before granting them access. This security protocol requires multifactor authentication, keeping networks secure from unauthorized individuals and protecting network users from outside attacks.
12. Tracking Prevention
It’s common for an ISP to track your digital footprint. Frequently, these services will share your online information with other organizations so they can create targeted ads or continue tracking your information. VPNs block ISP tracking, which can help maintain confidentiality and personal security.
Disadvantages of Using a VPN
As with all technology, you may face a few issues while using a VPN:
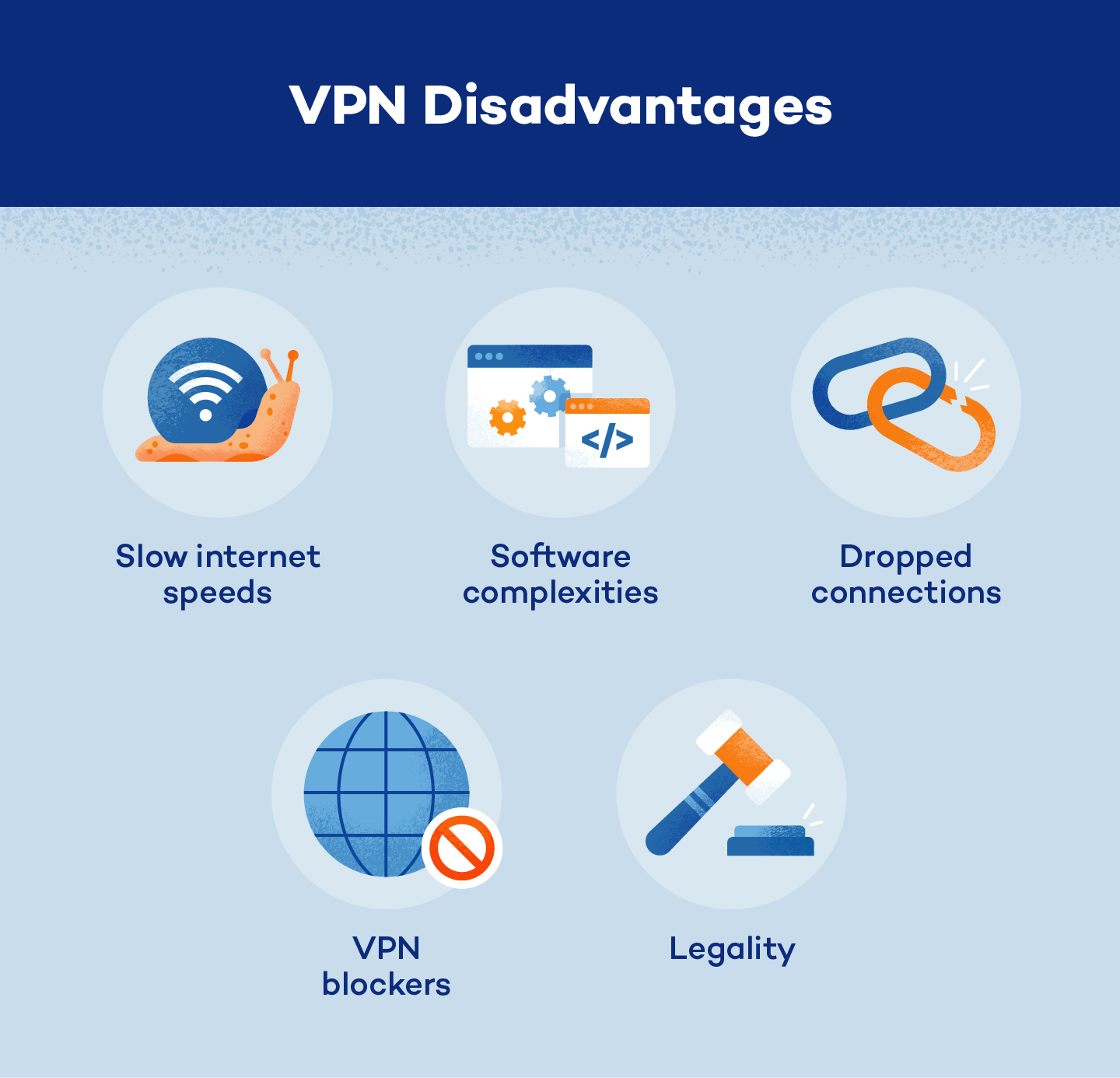
- Slower internet speeds: While VPNs use high-level encryption to protect networks, data security takes time and can slow down internet speeds.
- Software complexity: Not all VPNs are easy to use. Most have various complex parts, and a working vocabulary of network terminology is necessary to get a VPN up and running.
- VPN blockers: VPN-blocking software exists and can be used by individuals and organizations to prevent VPN users from accessing sites or information.
- Dropped connections: VPN connections can be lost. Unlike losing a Wi-Fi signal, dropping a VPN connection strips away your security measures and puts your network information on display.
- Legality: Some countries have laws and regulations against VPNs. Before downloading a VPN, research your area’s security restrictions.
The benefits of a VPN far exceed the disadvantages, especially when it comes to personal and professional security. Many cybersecurity professionals recommend VPNs as one of the best safety measures as well. With Panda Security’s premium protection services, you can access beloved content, protect sensitive information and avoid data and bandwidth throttling — improving your overall security and online experience.





