A distributed denial-of-service (DDoS) attack is like a digital traffic jam aimed at a website. Attackers flood the site with junk internet traffic, overwhelming it and making it slow or inaccessible to real users.
In today’s interconnected digital world, distributed denial-of-service (DDoS) attacks pose a serious threat to online services and businesses, disrupting operations and causing significant financial losses.
By understanding DDoS attacks and learning about effective mitigation strategies, you can better protect your online assets and ensure the uninterrupted availability of your services.
In this post, we’ll explore the insidious nature of DDoS attacks, how they work and learn some prevention tips to stay safe.
What Is a DDoS Attack?
A DDoS attack is a malicious attempt to shut down a website or online service. The attacker does this by flooding the target with a massive amount of internet requests, like fake website visits or data downloads.
These requests come from a network of hacked devices controlled by the attacker, making them appear like legitimate traffic and difficult to distinguish from real users. This overwhelming flood of requests jams the target’s system, preventing real users from accessing the website or service.
Think of it like a mall on a busy shopping day. Normally, the mall can handle the crowd of shoppers coming in and out of the stores. But if a group of people decide to target one specific store at the same time and overwhelm the entrance with shopping carts, deliveries and fake purchase orders, that store would be unable to function properly and serve its real customers.
How Does a DDoS Attack Work?
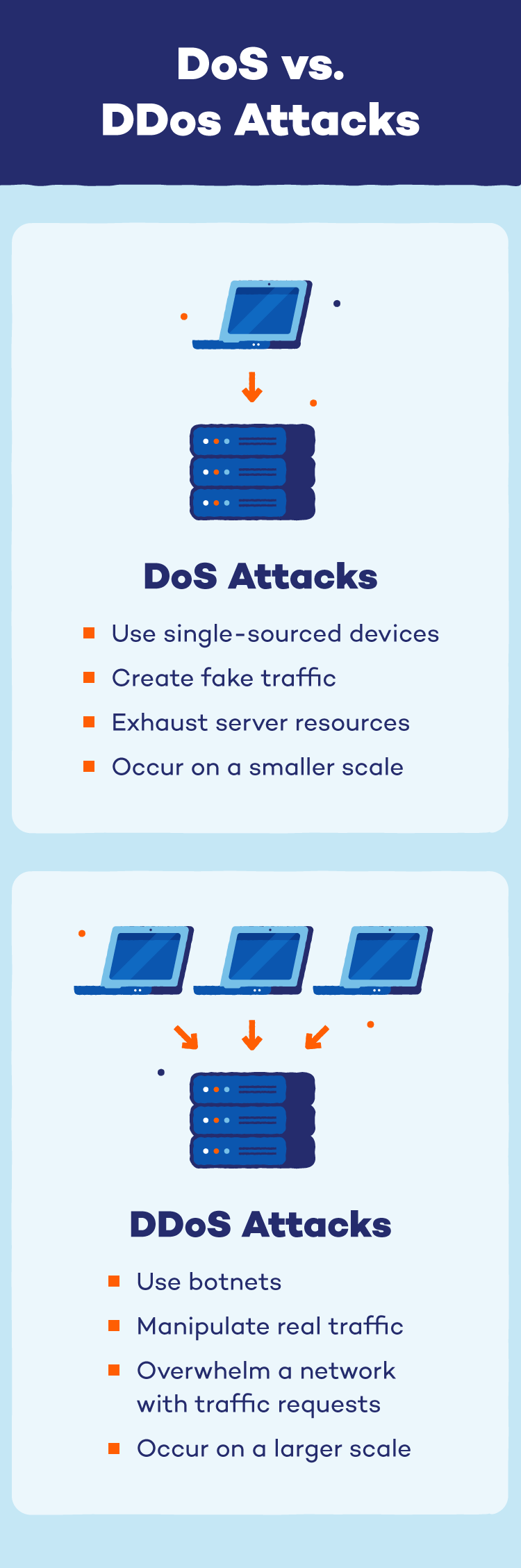
DDoS attacks cripple websites and services by leveraging a massive army of compromised devices. Unlike a denial-of-service (DoS) attack that floods a target with traffic from a single source, a DDoS attack utilizes a botnet — a network of hacked devices secretly controlled by the attacker.
These devices, ranging from computers to smartphones, become the attacker’s “soldiers” and bombard the target with requests simultaneously. This distributed assault overwhelms the target system’s capacity, preventing real users from accessing the website or service.
How to Identify a DDoS Attack
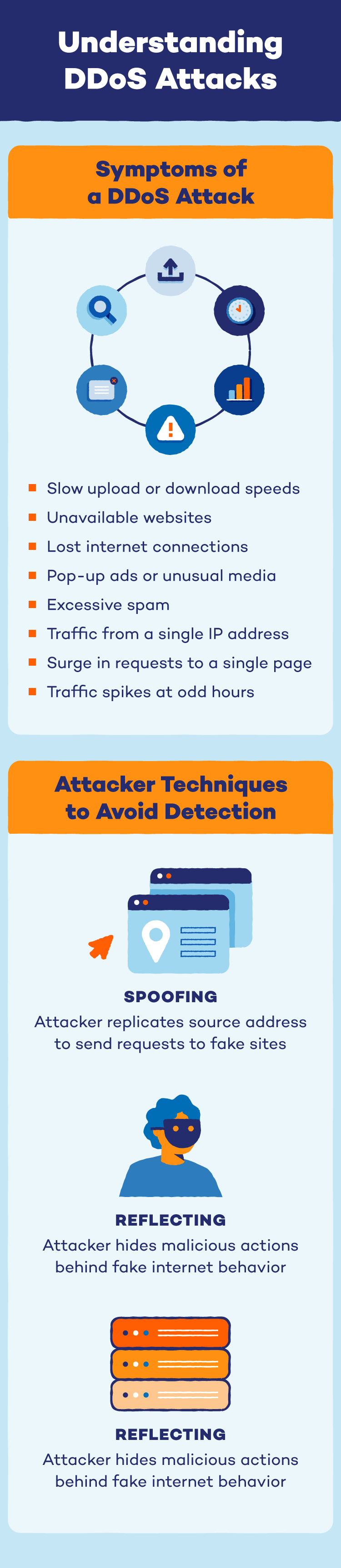
If your website is slow, unresponsive or even crashes entirely, it might be under a DDoS attack! Here are some red flags to watch out for:
- Slow upload or download speeds
- Unavailable websites
- Lost internet connections
- Pop-up ads or unusual media
- Excessive spam
- Traffic originating from a single IP address
- A surge in requests to a single page
- Spikes of traffic at odd hours of the day
Each type of attack has more specific signs, but these common DDoS attack symptoms could alert you to an attack before it’s in full force.
Many of these distributed denial-of-service attacks are also difficult to prevent, identify and mitigate. DDoS attackers avoid detection in a number of ways, particularly by:
- Spoofing: Spoofing — including DNS spoofing — is when an attacker replicates source addresses and sends legitimate traffic to illegitimate sites or destinations.
- Reflecting: Reflecting refers to when an attacker changes the normal behavior of internet services to hide their malicious actions.
- Amplifying: Amplifying is when an attacker uses a source modifier to create large amounts of traffic that can then overwhelm a network or server.
Types of DDoS Attacks
According to the open systems interconnection (OSI) model, a network has seven different connection layers that help networks communicate with each other. Because these layers individually determine the behaviors, tools and techniques needed to invade it, each type of DDoS attack is classified based on the layers it targets and the behaviors it needs to replicate.
Application Layer Attacks
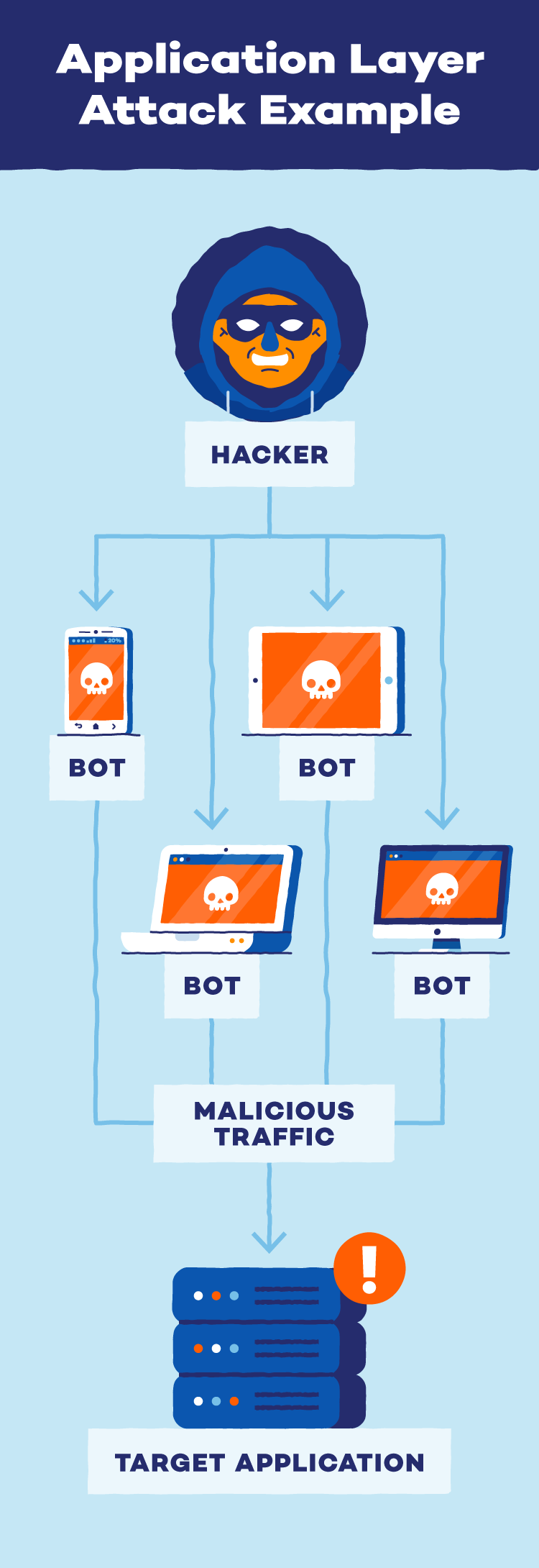
Application layer attacks target vulnerabilities within the software applications running on a system, bypassing network security measures. Unlike network attacks that disrupt overall traffic flow, these attacks exploit weaknesses in the code itself. This can involve manipulating databases (SQL injection) or injecting malicious scripts (XSS) to steal data, disrupt functionality or compromise user devices.
Protocol or Network Layer Attacks
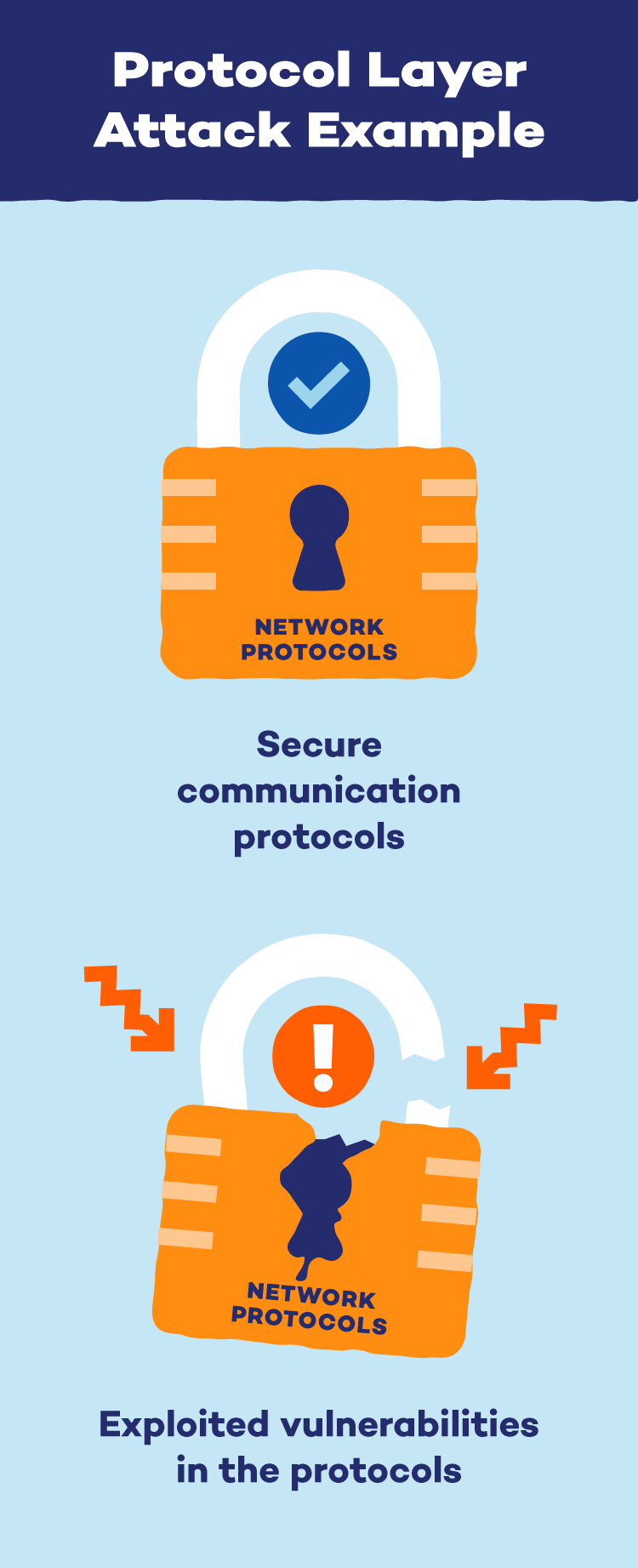
Protocol attacks, also called network layer attacks, usually target levels three and four of a network’s communication system. Networks have communication protocols, like a highway with lanes and traffic lights. Hackers exploit weaknesses in these protocols to disrupt communication.
These attacks overwhelm the capacity of the resources in these layers, like firewalls, which causes a state of exhaustion to overtake the system. SYN floods and smurf attacks are examples of protocol attacks that target the third or fourth OSI layers.
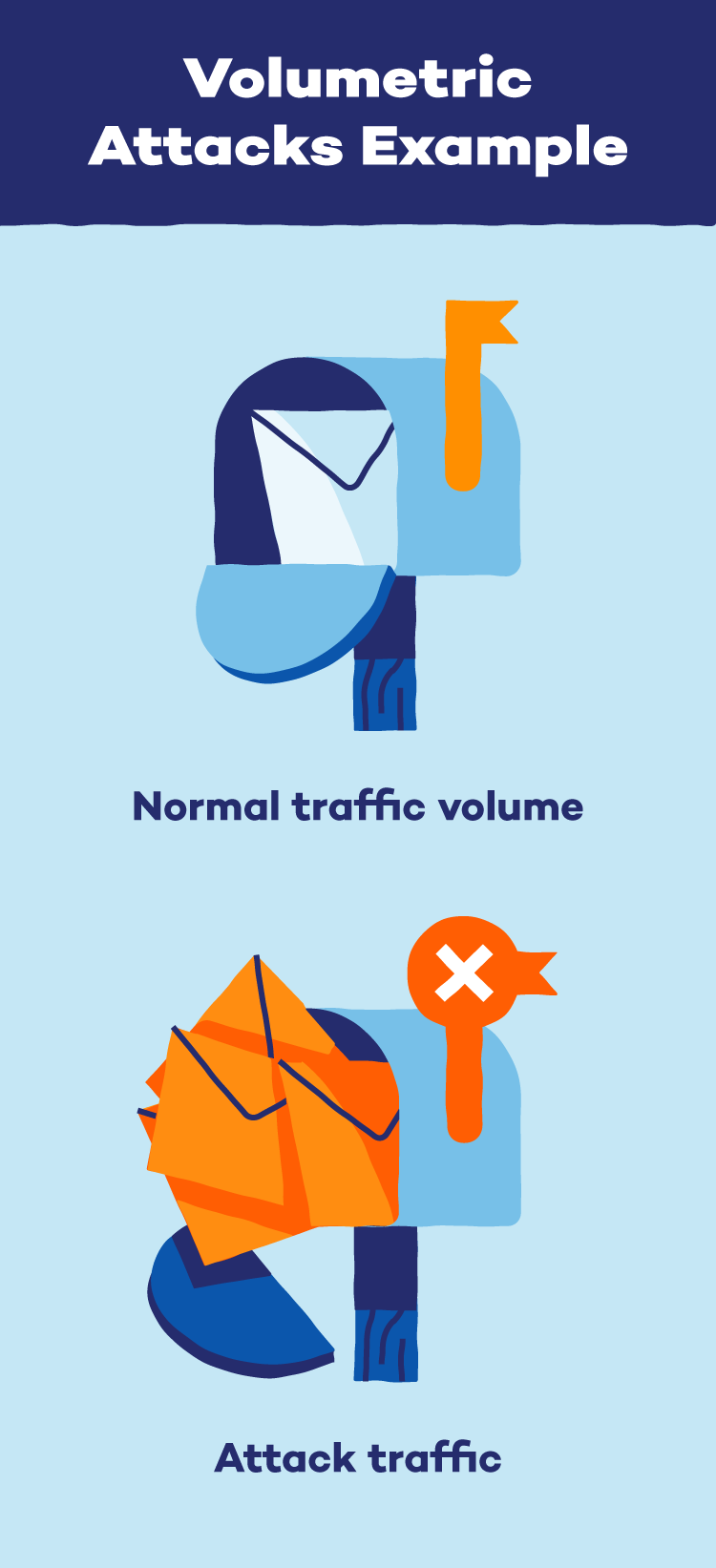
Volumetric Attacks
Volumetric attacks attempt to overwhelm a network and its connection to the internet. Attackers will amplify data and other communication requests to the extent that a system is unable to operate successfully. DNS attacks, including DNS amplification attacks, are commonly used to increase the volume of traffic for volumetric attacks.
Each of these types of DDoS attacks can be broken down further based on the duration of the attack:
- Long-term attacks: A long-term DDoS attack is any attack that lasts hours, days, weeks, months or longer.
- Burst attacks: A burst DDoS attack will usually only last a few seconds to a few minutes.
No matter how long an attack lasts, the damage can be crippling to each targeted connection layer.
Preventing a DDoS Attack
While there is no one-stop shop for DDoS protection, there are a few ways you can prepare your systems for a potential attack. Being aware of the possibility of a DDoS attack is the first step, and these five tips are the next best ways to prevent a possible system attack.
1. Vulnerability Assessments
If you run an organization with an information and security infrastructure system, it’s important to perform regular vulnerability assessments. In addition to simply finding system vulnerabilities, a vulnerability assessment can also document these findings and provide guidance for threat solutions. Penetration tests are also recommended, and white hat hackers can be hired to help run these tests and find and alert you to possible weaknesses or entry points.
2. Black Hole Routing
Black hole routing is a more extreme prevention and protection tactic. If you have reason to assume that you may fall victim to a DDoS attack, a black hole route can send all of your traffic on a neutral route away from your systems. This will remove all legitimate traffic — both good and bad — which can lead to business loss.
3. Rate Limiting
Rate limiting is one way to prevent or mitigate a DDoS attack. This lowers the number of requests a server can accept based on a specific timeframe, which can stop a DDoS attack from damaging or overtaking your systems. While this prevention tactic may not work for all attacks, it can reduce the damage one may cause.
4. Network Diffusion
Instead of allowing a DDoS attack to overwhelm and take over a network, network diffusion disperses traffic between a variety of distributed servers so it is absorbed by the network itself. This spreads the distributed denial-of-service attack’s impact so it becomes manageable instead of destructive.
5. Firewalls
In the event of a seven-layer DDoS attack, it’s important to have a web application firewall in effect. This is a tool that separates the server from the internet and offers an additional layer of security protection from dangerous and overwhelming traffic. Additionally, firewalls can implement custom rules during an attack to better disperse or accept traffic.
While those carrying out a DDoS attack can be sneaky, there are ways to protect your business, your home and yourself. By investing in security protocols, including VPNs and protection plans, you can be prepared for a DDoS attack at any time.
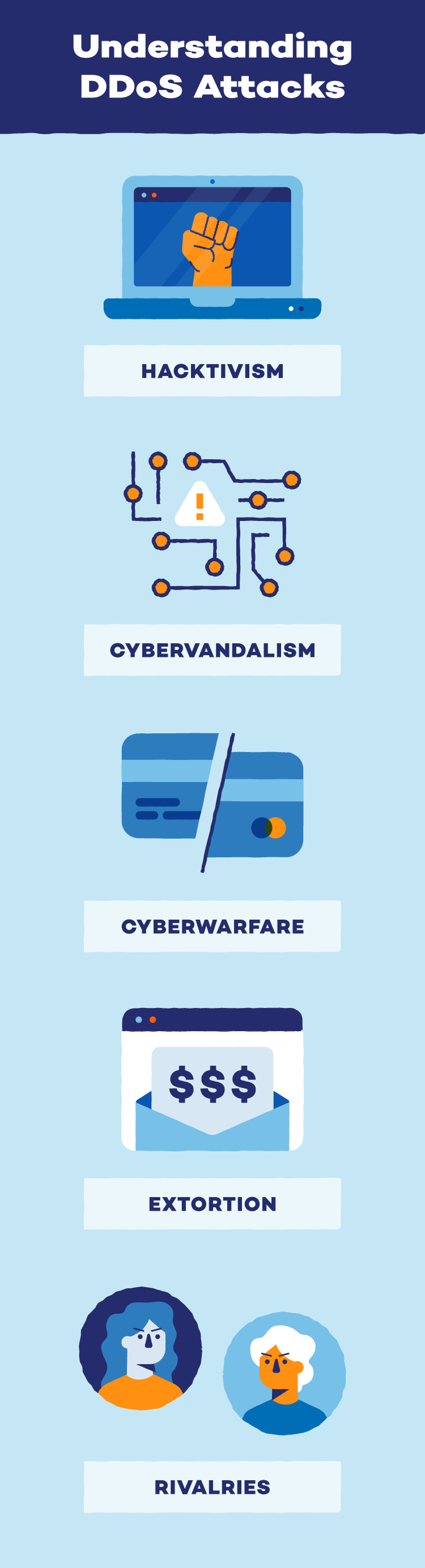
Motives for DDoSing
DDoSing — the term used when someone executes a DDoS attack — can result from a variety of motives. While these motives are different for every hacker, they can range anywhere from political gain to social justice.
- Hacktivism: Hacktivism is a form of digital activism. Hacktivists usually engage in hacktivism to reach social, political or religious justice, and they often fight for the greater good. Some hackers will use DDoS attacks during a hacktivism campaign.
- Cybervandalism: Cybervandalism is a cyberattack that often has no social, political, religious or criminal intentions. Most online vandalism acts are intended to show a hacker’s expertise, and vandals often pay a DDoS-for-hire fee to initiate DDoS booters and IP stressors.
- Cyberwarfare: Unlike cybervandalism, cyberwarfare has political or military intent and is often used to overtake or dismember organizational infrastructures. Many of these types of DDoS attacks are state-sanctioned and can disrupt finances, health care and government security.
- Extortion: A cybercriminal may demand money or other resources while threatening a DDoS attack. If the victim complies, the attacker may not issue the attack. On the other hand, if the victim does not comply, organizations may be forced to go offline until the threat has passed or been mitigated.
- Rivalries: DDoS attacks are sometimes used as competition tools for both personal and professional rivalries. These attacks can dissuade people from going to events, shut down online storefronts, cause reputational damage and more.
DDoS and application layer attacks can pose significant threats to websites and online services. By understanding these different attack methods and implementing the recommended security measures, organizations can significantly bolster their defenses. However, cyberthreats are constantly evolving.
Panda Free Antivirus offers comprehensive real-time protection against various online threats, including malware, phishing attempts and even botnet infections. And for an extra layer of security when using public Wi-Fi, consider using Panda Security VPN. It encrypts your internet traffic, making it unreadable to hackers and eavesdroppers, so you can browse safely on any network.
DDoS Attack FAQ
Let’s discuss some common queries related to DDoS attacks.
What Does DDoS Attack Stand For?
DDoS stands for distributed denial-of-service attack. It’s a malicious attempt to overwhelm a website or online service with a flood of internet traffic, making it unavailable to legitimate users.
What Does a DDoS Attack Look Like?
You might experience a DDoS attack as:
- Slow or unresponsive websites: The website might take a very long time to load or not load at all.
- Error messages: You might see error messages about the server being overloaded.
- Trouble using online services: Online games, streaming platforms, etc. might be difficult to connect to or use.