Until recently, financial companies and governments were the main targets of cyberattacks. Nowadays, companies of every size and sector depend on the Internet to carry out their business, and as a consequence, the threat of cyberattacks has become universal.
While the threat of cyberattacks is not new, hackers use increasingly sophisticated and difficult tactics to carry them out. To respond to this, companies are moving from cybersecurity to cyber resilience. But what do we mean when we talk about how important cyber resilience is for a company?
What is Cyber Resilience?
Cyber resilience is an organization’s ability to prevent, detect, contain, and recover from cybersecurity threats. A cyber resilient company can minimize exposure time and the impact of countless serious threats against data, applications and IT infrastructure. The latest Panda Security report, presented at #PASS2018, defines cyber resilience as “the key to business security.”
Why is Cyber Resilience Important?
As the dangers of cybersecurity increase, current approaches to maintaining cyber resilience are no longer sufficient. Cybersecurity management needs an update to more sophisticated security models, because being cyber resilient is not an option anymore — it is a requirement.
The first Panda Security Summit (#PASS2018), which brought the CIOs and CISOs of European companies to Madrid, served to underscore the concept of cyber resilience as a key trend in the current cybersecurity environment.
Common Types of Cyber Resilience Threats
It’s important to understand the difference between resilience and recovery. Cyber resilience is a form of business continuity management that mitigates security breaches and keeps the company running successfully during a cyber attack. Here are the common security-related cyber resilience threats companies may experience:
- Cybercrime: Cybercrime is a digital criminal activity where the end goal is to make money, access personal information or disable a device.
- Cyber espionage: Cyber espionage involves gaining access to sensitive materials, such as government or military information, using proxy servers.
- Hacktivism: Hacktivism is a type of cybercrime involving a war on information or data that is conducted for political, social, religious or anarchistic reasons.
How to Adopt a Cyber Resilient Stance in Your Company
Companies must adopt a comprehensive, strategic, and persistent stance, with a new approach to their security program that can provide protection without imposing undue restrictions on their business. This new stance must be based on strengthening preventative defenses, acknowledging that these defenses can be overcome by the attackers, and accepting that the attackers may already be present within the organization.
Cybersecurity must be treated as a corporate risk management problem, not as a purely IT-based problem. To do this, companies need to proactively implement ways to protect themselves pre-incident, such as:
- Finding out the most relevant threats and adversaries
- Investing in cybersecurity initiatives to close the readiness gap
- Building a robust ecosystem of threat detection initiatives
- Increasing cybersecurity visibility initiatives within the company
- Improving the hiring pipeline of cybersecurity professionals
Additionally, being cyber resilient means that this adaptation needs to be carried out as quickly as possible. Companies can adapt their strategy to mitigate new threats in real-time by doing the following:
- Prioritizing the most valuable assets in the organization
- Adopting an ongoing crisis stance
- Continually implementing risk-mitigation initiatives
- Continually improving processes, technologies, tools, and security systems
- Creating a full register of assets and monitoring actions carried out with them
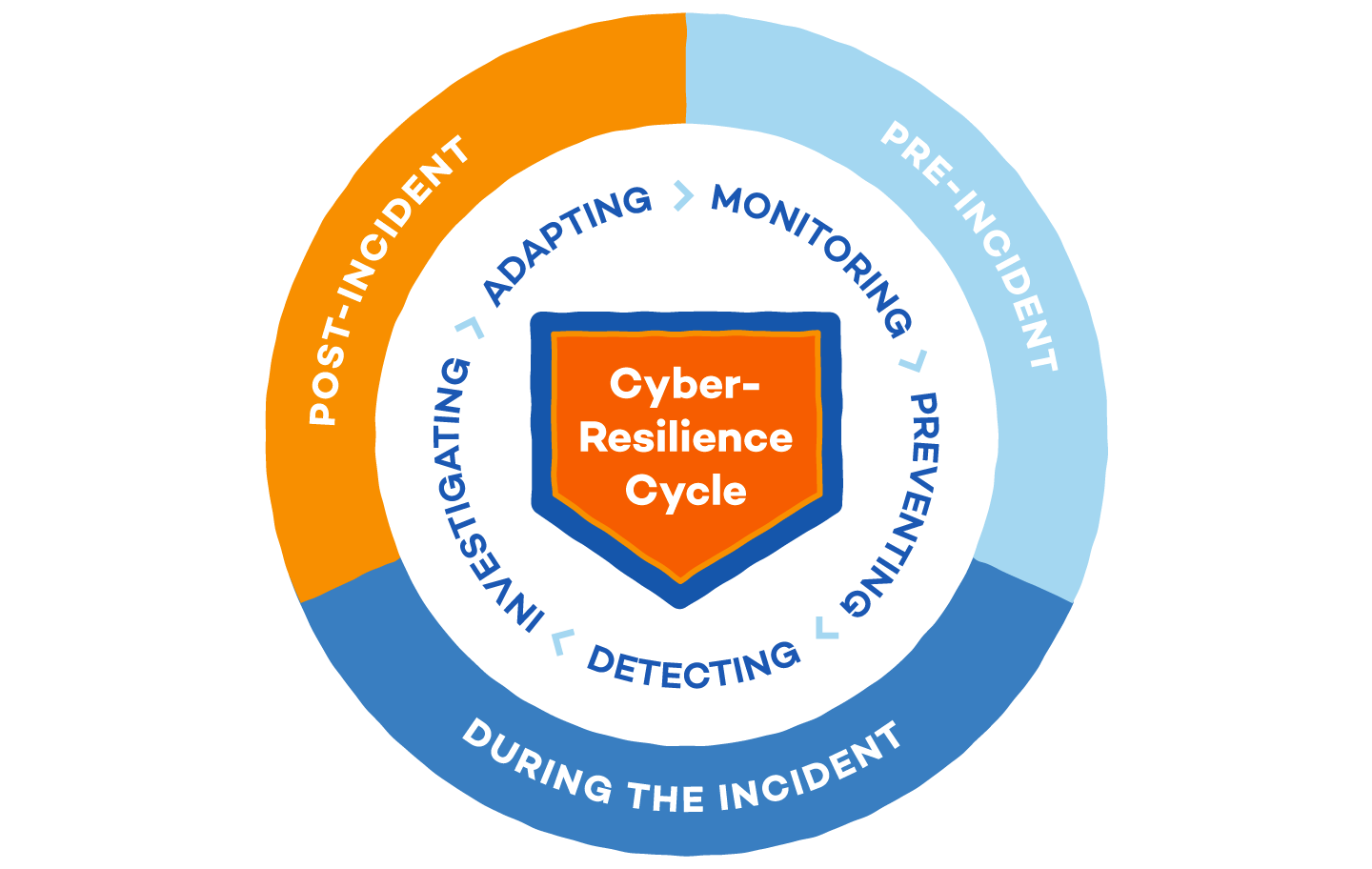
Cyber-resilient companies also have to assume that, sooner or later, they will be compromised by a cyberattack. To correctly manage their cybersecurity, organizations need to understand and adopt the recovery ‘cycle of resilience’ whose key phases are:
- Pre-incident: The ability to better prevent and resist threats, making use of advanced cybersecurity technologies that can detect known and unknown, or zero-day, malware.
- Incident: The resilient attitude is implemented by quickly reacting to sudden threats with detection, containment and response. For this, it’s necessary to make the most of the new paradigms that are arising as a result of the monitoring and visibility capabilities that Endpoint Detection and Response (EDR) solutions provide.
- Post-incident: Absorb impacts while strategic security objectives are still met and the operative environment is reconstructed in a way that future sources of threats are eliminated.
When it comes to minimizing impact on the business, the time that passes between a breach and its discovery is the decisive factor in the overall cost of the incident. Monitoring, visibility of what happens on endpoints, and technologies that automate the detection and investigation, such as Panda Adaptive Defense, drastically reduce this time.
What Cyber-Resilient Companies Do Right
The report also reflects the fact that the increase in the volume and severity of cybersecurity incidents detected by a majority of companies — 64% and 65% respectively — has meant an increase in detection and response times in 57% of cases.
The report identifies robust features highly cyber-resilient companies in common:
- Cyberattack prevention systems (72%)
- Detection systems (68%)
- Containment systems (61%)
- Response systems (67%)
Another distinctive feature of these high-performing cyber-resilient companies is that they have in place a Computer Security Incident Response Plan (CSIRP), with professionals specialized in application (91%). These are led by managers who understand that high cyber resilience is directly related to economic growth (63%) and the company’s reputation (69%).
The growing number of threats, and the more sophisticated nature of attacks pose a challenge for companies’ cybersecurity, compelling them to review their cybersecurity program to make their organization cyber resilient.
At Panda Security, we have at our disposal the latest technology as well as the most highly skilled team of experts to help your company to achieve this goal, with a new security model that has all the answers.