Spoofing is a deceitful tactic where an individual or entity — such as a scammer — masquerades as someone else, usually with harmful intentions.
Spoofing techniques include forging email addresses, manipulating caller IDs or creating fake websites to trick individuals or systems into believing the spoofed entity is genuine, resulting in unauthorized access, data theft or other adverse consequences.
Imagine you’re enjoying a quiet evening at home, browsing the internet, when you suddenly receive an email claiming to be from your bank, urgently requesting your personal information to verify your account. Alarmed, you hastily comply, only to realize later that you’ve fallen victim to a clever scheme known as spoofing. But what is spoofing exactly, and how does it work?
The consequences of spoofing can extend far beyond mere inconvenience, leading to compromised security, identity theft and financial loss. In this post, we’ll go over what spoofing is, different types and tips to prevent it.
Spoofing Definition
Spoofing is a deceptive practice where cybercriminals impersonate another entity or source, often with malicious intent. It can involve various techniques such as forging email addresses, manipulating caller IDs or creating counterfeit websites to trick individuals or systems into believing the spoofed entity is legitimate. These deceptive tactics lead to unauthorized access and data theft.
For example, say you regularly receive emails from Amazon.com. A spoofer may disguise an email by changing the email address to “Amaz0n.com” to trick you into sharing your login information with that address.
How Does Spoofing Work?
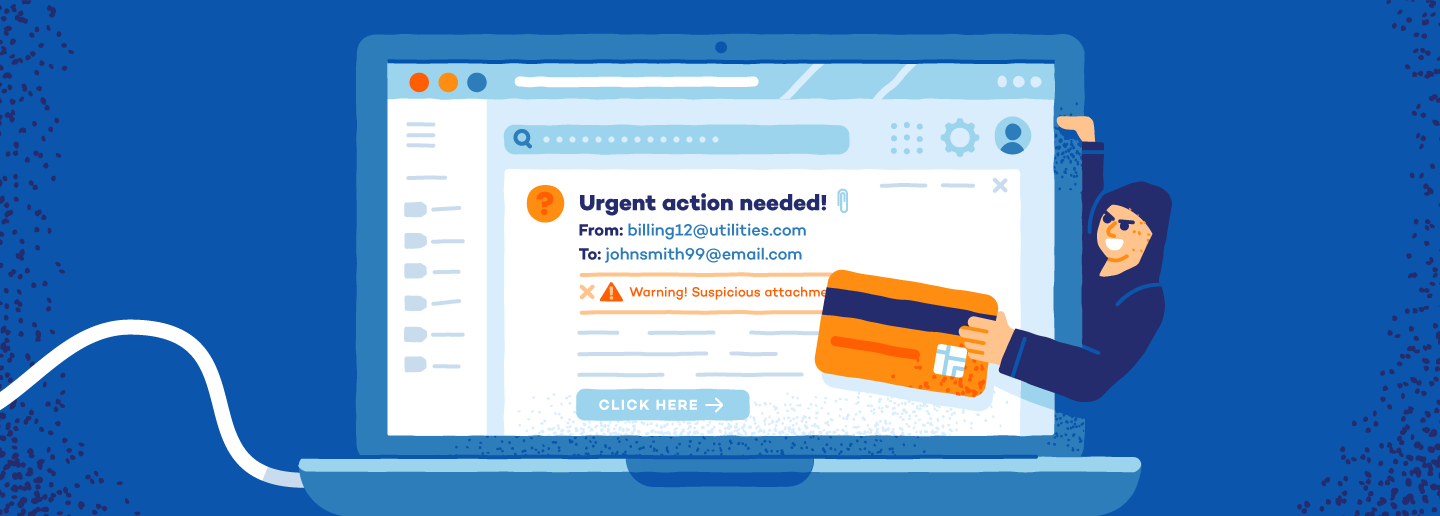
Spoofing operates on a dual strategy: the creation of a deceptive façade, such as a counterfeit email or website (also known as the spoof), coupled with social engineering, which persuades individuals to take certain actions.
For example, imagine receiving an email purportedly from a well-known online retailer, enticing you with a tempting discount offer. The email (the deceptive façade) appears authentic, complete with the company’s logo and branding. Eager to seize the opportunity (the social engineering element that manipulates your emotions and desires), you click on the provided link, only to land on a counterfeit website designed to capture your payment information.
The consequences of spoofing can be severe, leading to various harmful outcomes. Victims may experience unauthorized access to their accounts or sensitive information, resulting in identity theft, financial loss or privacy breaches. Additionally, spoofing attacks can compromise the integrity of communication channels, facilitating the spread of malware, phishing scams or other malicious activities.
Spoofing includes a wide range of attacks, from simple email and website tricks to complex technical manipulations involving IP addresses, ARP and DNS servers.
10 Types of Spoofing
Spoofing comes in many forms, and it’s important to be aware of the different attacks you may encounter. Below are some common types of spoofing and tips to prevent spoofing:

1. Caller ID Spoofing
Caller ID spoofing is a deceptive practice where callers manipulate the information displayed on the recipient’s caller ID to disguise their true identity and make it appear as if the call is originating from a different phone number or entity.
Scammers often use this technique to trick individuals into answering calls by displaying familiar or legitimate phone numbers, such as those belonging to banks, government agencies or trusted contacts — when in reality, the caller’s true identity may be fraudulent.
Most scammers use Voice over Internet Protocol (VoIP) to perform caller ID spoofing. VoIP helps scammers create a realistic phone number and caller ID name. When someone answers the phone, the scammer will try to deceive them into revealing personal information.
How to prevent it:
- Utilize call blocking or caller ID spoofing detection apps or services offered by your phone carrier or available for download to help identify and block suspicious calls.
- Exercise caution when answering calls from unknown numbers, especially if they claim to be from familiar organizations or individuals. Double-check with the organization they’re claiming to be from.
- Refrain from providing personal or financial information over the phone unless you initiated the call and are confident in the other party’s authenticity. Legitimate organizations will typically not request sensitive information over the phone.
- Look out for caller ID that says “911.” Spoofed caller IDs often show up as “911 Emergency” instead of the spoofer’s real phone number.
2. Website Spoofing
Website spoofing is when someone creates a fake website that looks like a real one to trick people into thinking it’s legitimate. The fake website may have a similar design, logo, and web address to the real one, but it’s controlled by scammers who use it to steal personal information or spread malware.
Typically, the copycat site’s URL address will be similar enough to a legitimate site so it looks real at first glance.
How to prevent it:
- Check the URL before clicking. If you’re suspicious about a link, hover your mouse over the link. A URL address will pop up in the bottom left corner of your window so you can see where the link will take you before you click it.
- Check the address bar to verify the website is secure by looking for “https://” before the URL. This indicates encryption and protection against cyberthreats. If you land on a website that starts with “http://” (without the “s” at the end), close the window quickly.
- Use a password manager, as they should not autofill login credentials on spoofed websites. If your previously saved credentials aren’t autofilled, it could indicate a spoofed site.
- Look for the lock symbol or green bar next to the URL, indicating a secure connection.
3. Email Spoofing
Email spoofing is a fraudulent technique where attackers manipulate the sender’s email address to make it appear as if the email is coming from a trusted source, such as a reputable organization or individual. In reality, these emails are from a malicious actor. This deceptive practice is commonly used in phishing attacks to trick recipients into disclosing sensitive information or taking harmful actions.
How to prevent it:
- Check for any discrepancies or similarities with known addresses and confirm with the sender if you’re uncertain.
- Avoid opening attachments from unknown or suspicious senders, as they may contain malware.
- Use two-factor authentication to add another layer of security against spoofing attacks on your devices. It’s important to note that it is not completely foolproof, so be sure to pair it with good cybersecurity habits.
- Find the sender’s contact information online to confirm authenticity and search suspicious email contents on Google for potential scams.
- Report suspicious emails as spam to avoid clicking on any malicious links or attachments by mistake.
4. IP Spoofing
IP spoofing is when an attacker fakes their IP address to trick a system into thinking they’re someone else. They use this to hide their identity, launch attacks or gain unauthorized access to networks.
How to prevent it:
- Enable IP address validation: Using mechanisms like SEND or DAI helps ensure that devices on a network use genuine IP addresses and are not being impersonated by attackers. Configure these security features on your network devices. Specific steps may vary depending on the device and its configuration interface, so seek assistance from a knowledgeable network administrator if you have questions.
- Deploy encryption protocols such as IPsec to secure network communication.
- Utilize strong and unique passwords for network equipment.
- Enable firewall and intrusion detection systems.
- Regularly monitor network traffic for suspicious activity.
5. DNS Server Spoofing
Domain Name System (DNS) spoofing sends traffic to different IP addresses and is often used to bring visitors to malicious websites. Scammers achieve this by replacing the IP addresses stored in the DNS server with the malicious addresses they want you to use. Because it alters your stored data for malicious purposes, DNS spoofing is also known as cache poisoning.
How to prevent it:
- Use DNSSEC (Domain Name System Security Extensions) to authenticate DNS responses.
- Implement DNS filtering solutions to block malicious domains and prevent DNS spoofing attacks.
- Regularly update DNS server software to patch vulnerabilities.
- Utilize VPN (virtual private network) services to encrypt DNS traffic and protect against DNS spoofing.
- Verify website URLs by looking for “https://” and double-checking the domain name before entering sensitive information.
6. ARP Spoofing
Address Resolution Protocol (ARP) spoofing is frequently used to modify or steal data for in-session hijacking. It’s also referred to as ARP poisoning or ARP cache poisoning. Scammers usually do this by linking their media access control to an IP address so they can intercept data originally intended for someone else.
How to prevent it:
- Implement ARP spoofing detection tools or security solutions that can identify and block suspicious ARP packets.
- Configure packet filtering rules on network devices — such as routers or firewalls — to block or filter out ARP packets from unauthorized sources.
7. Text Message Spoofing
Text message spoofing is a deceptive practice where someone manipulates the sender’s phone number using online services or software that allows them to send text messages with a forged sender ID. Using this software allows the sender to disguise their identity and potentially trick the recipient into believing the message is from a trusted source when it may be a text message scam.
How to prevent it:
- Be cautious of unexpected messages from an unknown sender or with suspicious content, and refrain from clicking on any links or providing personal information.
- Double-check the sender’s phone number or alphanumeric sender ID to ensure it matches known contacts or trusted sources before responding or taking action.
- Avoid sharing personal information such as passwords, account numbers or verification codes via text message — especially if the request seems unusual or unexpected.
- Enable spam filters or blocking features provided by your mobile carrier or messaging app to filter out suspicious text messages and prevent potential text message spoofing attempts.
8. GPS Spoofing
GPS spoofing is a deceptive technique where someone manipulates the GPS signals received by a device to falsely report its location. This allows the spoofer to trick the device into believing it is located in a different place than it actually is.
GPS manipulation can be used for various purposes, such as fooling location-based apps or services, evading geofencing restrictions or conducting cyberattacks that rely on accurate location data.
How to prevent it:
- Use encrypted GPS signals, which are more difficult for spoofers to manipulate. Using receivers that support encrypted signals can help prevent GPS spoofing.
- Employ signal authentication, such as receiver autonomous integrity monitoring (RAIM) or space-based augmentation systems (SBAS), which can detect and reject spoofed signals.
9. Man-in-the-middle (MitM) Attack
A man-in-the-middle (MITM) attack refers to when someone hacks a Wi-Fi network to intercept web traffic between two parties. It also includes when a scammer creates a duplicate fraudulent network in that location for the same purpose.
If the attack is successful, scammers will have the ability to reroute sensitive information, such as logins or credit card numbers, to themselves. They can then use this information for malicious purposes.
How to prevent it:
- Utilize protocols like HTTPS for websites and SSL/TLS for email to encrypt data transmitted between your device and servers, making it difficult for attackers to intercept and manipulate.
- Exercise caution when using public Wi-Fi networks, as they are vulnerable to MITM attacks. Avoid accessing sensitive information or logging into accounts that require passwords when connected to unsecured Wi-Fi.
- Always verify SSL certificates when accessing websites or online services. Ensure the certificates are valid and issued by trusted certificate authorities to mitigate the risk of falling victim to MITM attacks through forged certificates. Most web browsers allow you to view the SSL certificate details. You can usually do this by clicking on the padlock icon next to the URL in the address bar. Look for an option like “View Certificate” or “Certificate Information”.
- Use a VPN when connecting to public Wi-Fi or unfamiliar networks to encrypt your internet traffic and protect against MITM attacks by securing data transmission.
10. Extension Spoofing
Extension spoofing allows scammers to disguise malware in extension folders. Files are usually renamed as a text document (e.g., “filename.txt.exe”) and have malware hidden inside. When a user opens the text file, they unknowingly run a malicious program.
How to prevent it:
- Verify extension sources and only install browser extensions from trusted sources such as official browser extension stores or reputable developers. Avoid downloading extensions from unknown or untrusted sources to reduce the risk of extension spoofing.
- Keep all browser extensions up-to-date with the latest versions to ensure they have the latest security patches and protections against extension spoofing vulnerabilities.
- Review permissions before installing an extension. Be cautious of extensions that require excessive permissions or access to sensitive data, as they may be designed for malicious purposes, including extension spoofing.
- Install and regularly update reputable antivirus or anti-malware software on your devices. These security programs can help detect and prevent malicious browser extensions, including those involved in extension spoofing attacks.How to Prevent Spoofing Attacks
How to Prevent Spoofing Attacks

There are many things you can do to protect yourself against spoofing attacks. Stay one step ahead of scammers with these helpful do’s and don’ts:
Do’s
Here are some tips to keep in mind to protect yourself against spoofing attacks:
- Turn on your spam filter: This prevents most spoofed emails from even reaching your email inbox.
- Read messages closely: Spoof attacks usually contain poor grammar or unnatural sentence structure. If you see this, it’s a sign that the request is not safe. Always double-check that the URL address of a website or the sender’s email address is correct before sending sensitive information.
- Confirm the source: If you receive communication that seems suspicious, it’s best to reach out to the sender and confirm that the call or email you received is legitimate.
- Install cybersecurity software: Investing in cybersecurity software is a great way to protect yourself from cybercriminals online. If you suspect that you’re being spoofed, download malware removal or antivirus software to protect your devices from malicious threats or viruses.
Don’ts
Here are some things you should avoid to protect yourself from spoofing attacks:
- Don’t download or click unfamiliar links or attachments: If a link or attachment looks questionable, don’t click on it. If they’re from a scammer, it likely contains malware or other viruses that are dangerous for your computer.
- Don’t answer calls or emails from unknown senders: If you don’t recognize the sender, don’t respond to the call or email. By not communicating with a potential scammer, you avoid revealing your personal information.
- Don’t disclose sensitive information: Avoid sharing personal information, like your address, bank account, or Social Security number. If you need to provide this information, take extra steps to confirm that it’s a trusted source.
- Don’t use the same password: Many people use weak passwords that scammers can easily guess. Create strong passwords and update them often to prevent scammers from getting a hold of one. Also, never use the same password for every login.

If you think you’ve been spoofed, you can file a complaint at the FCC’s Consumer Complaint Center. You can also contact your local police department if you’ve lost money due to spoofing.
The above prevention tips, as well as other tips to protect your personal information online, will help you stay vigilant. Be sure to use antivirus software to secure your digital information and protect yourself against spoofing.






