Passwords are the most common way to prove we are who we say we are when it comes to using websites, social media accounts, email, and even the computer itself. Passwords also give us and others access into mobile phones, bank applications, work log-ins, and confidential files. For many online systems, a password is the only thing keeping a hacker from stealing our personal data. Read on to learn how cyber criminals can hack passwords and password protection techniques.
Why It’s Easy for Hackers to Hack
While creating a password may seem like a safe bet, large, reliable companies such as eBay, LinkedIn and most recently Facebook have all been breached, compromising passwords for many of their users. According to the chief executive of specialist insurer Hiscox, in 2016 cybercrime cost the global economy more than $450 billion and over two billion records were stolen. Why is it so easy for hackers to access accounts and obtain secure passwords?
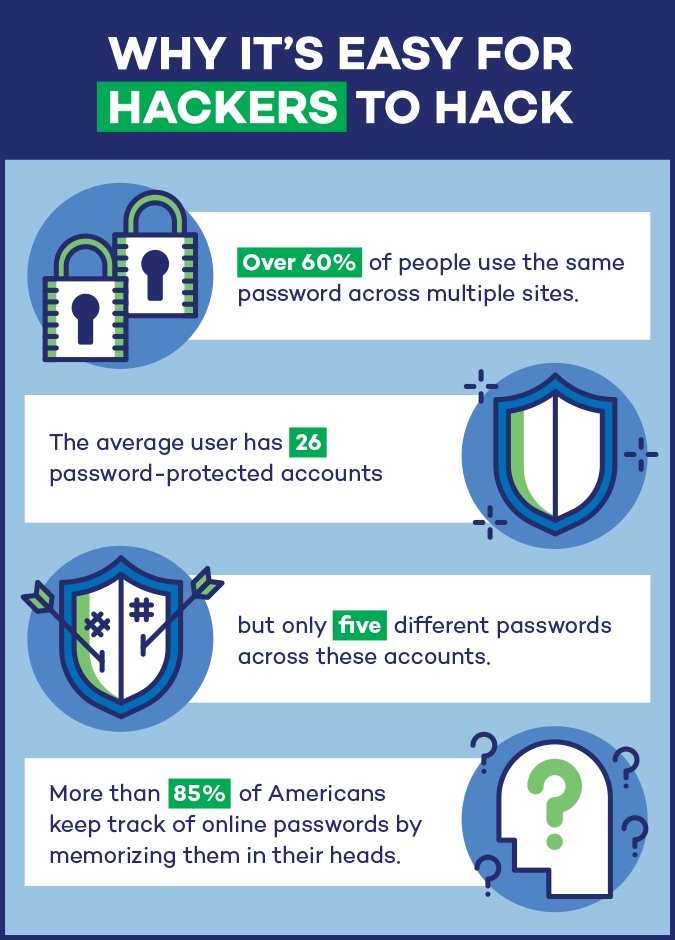
First and foremost, we reuse our passwords. Over 60 percent of the population use the same password across multiple sites. And since 39 percent have a hard time keeping track of passwords, we become incredibly susceptible to hackers when we keep passwords for years or even decades.
People are also incredibly predictable. We tend to use passwords that are personalized in some form to our lives, because they are easier to remember. Because of our visual memory capacity, it is easier to remember images and information that we are already familiar with and have some meaning to us. This is why we often create easy to remember, predictable passwords based on things like family members, pets, or birthdays.
The average user also has about 26 password-protected accounts, but only has five different passwords across these accounts. That makes us more susceptible to hacks, especially brute force attacks. With more than 85 percent of Americans keeping track of online passwords by memorizing them in their heads, it’s nearly impossible to memorize up to 26 passwords. And with a plethora of passwords, it’s important to install a password management program. However, a shocking low 12 percent of Americans actually have one installed.
The standard rule of thumb used to be to change passwords every 90 days. However, in recent years this method has been defined as ineffective by the FTC Chief Technologist and Carnegie Mellon computer science professor, Lorrie Cranor. She found that when people are forced to change their passwords on the regular, they put less mental effort into it. This is another way that hackers can take advantage of people’s lack of effort or desire to change or diversify their passwords.
How Long it Takes Cyber Criminals to Determine Your Password
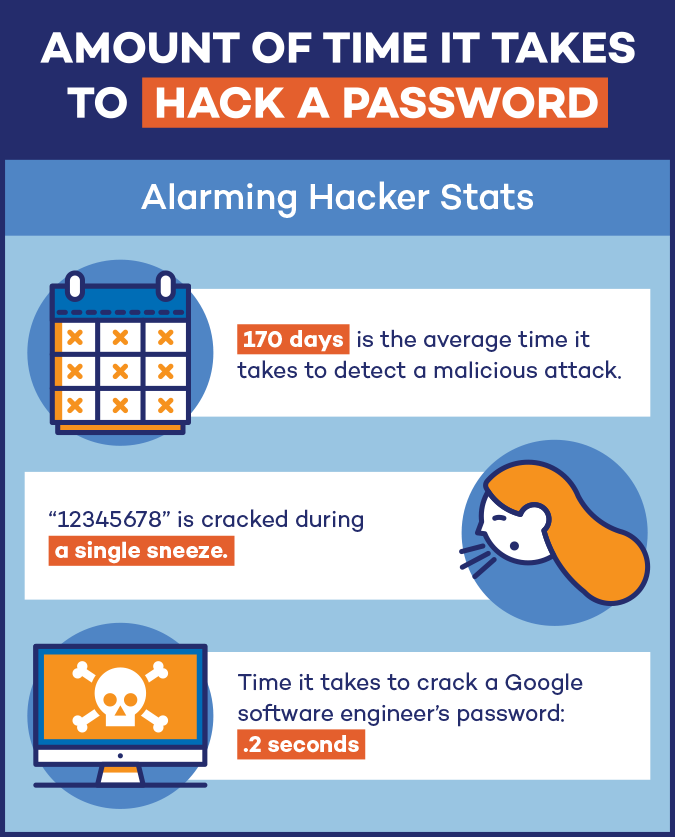
If you have a password as simple as “password” or “abcdefg”, it would only take a hacker 0.29 milliseconds to crack it according to BetterBuys’ password-cracking times. Even more surprising? The password 123456789 is cracked 431 times during the blink of an eye. Even more complicated passwords are being hacked faster. What used to take hackers three years to crack is now taking under two months.
Hackers first go after the easiest and most common worst passwords, then move on to passwords with the least amount of characters. While a password with seven characters may take only 0.29 milliseconds to crack, one with 12 characters can take up to two centuries. The longer that passwords are, the longer it will take for the hackers to get the right combination.
How Cyber Criminals Hack Passwords
So how do hackers actually do their dirty work? First off, it’s important to understand that this is their job. For most modern, successful hackers, this is what they put their time and effort into on a daily basis. The most common ways that hackers can access your accounts through your credentials are:
- keylogger attacks
- brute force attacks
- dictionary attacks
- phishing attacks
Keylogger Attacks
A keylogger is a type of surveillance technology used to record and monitor each keystroke typed on a specific device’s keyboard. Cybercriminals use keyloggers as a spyware tool to seal personal information, login information, and sensitive enterprise data.
How to Protect Yourself:
Use a firewall to prevent a keylogger from transmitting information to a third party. You can also install a password manager, which will autofill your passwords and prevent keyloggers from accessing your credentials. Make sure to also keep your software updated, as keyloggers can take advantage of software vulnerabilities to inject themselves into your system.
Brute Force Attacks
We use passwords that are simple, relevant and can be guessed within a few tries. When using the brute force method, hackers use software that repeatedly tries several password combinations. This is a reliable way to steal your information, as many users use passwords as easy as “abcd”. Some of the most common password stealing softwares include Brutus, Wfuzz, and RainbowCrack.
How to Protect Yourself:
There are a number of ways to prevent brute force attacks. First, you can implement an account lockout policy, so after a few failed login attempts, the account is locked until an administrator unlocks it. You can also implement progressive delays, which lock out user accounts for a set period of time after failed attempts, increasing the lock out time after each failed attempt.
Another solution is using a challenge-response test to prevent an automated submission to the login page. Systems such as reCAPTCHA can require a word or math problem to make sure a person is entering credentials rather than a hacking system.
Dictionary Attacks
In 2012, more than 6 million passwords were hacked on LinkedIn due to a dictionary attack. A dictionary attack works by systematically entering every word in a dictionary as a password. Dictionary attacks seem to succeed because people have a tendency to choose short, common passwords.
How to Protect Yourself:
Choose a password that is at least 8 characters. Avoid any words in the dictionary, or common predictable variations on words. Use SSH keys to connect to a remote server to store your password. You should also only allow SSH connections for certain hosts or IP addresses so you know what computers are connecting to your server.
Phishing Attacks
Phishing attacks involve hackers using fake emails and websites to steal your credentials. They are most commonly emails that disguise as legitimate companies, asking you to download a file or click on a link. Most commonly, phishing attacks can involve a hacker masking as your bank provider, which can be especially detrimental.
How to Protect Yourself
Be cautious of emails that come from unrecognized senders, are not personalized, ask you to confirm personal or financial information, or are urging you to act quickly with threatening information. Do not click on links, download files, or open attachments from unknown senders. Never email personal or financial information to even those you trust, as your email can still be breached.

Creating a Fool-Proof Password
Cybercriminals have become experts in determining passwords. 50 percent of small to midsize organizations suffered at least one cyberattack in 2017. That’s half of all small businesses, not to mention the large corporations such as T-Mobile, JP Morgan, and eBay who have suffered massive cyber attacks affecting hundreds of millions of customers. That’s not even the scariest part.
According to this WordPress’ UnMasked study, even high-level executives like the senior engineer at PayPal or the program manager at Microsoft have faulty, predictable passwords. This could seriously impacted their businesses. When creating a password, there are a few tips that can significantly help you keep your accounts safe and hackers out.
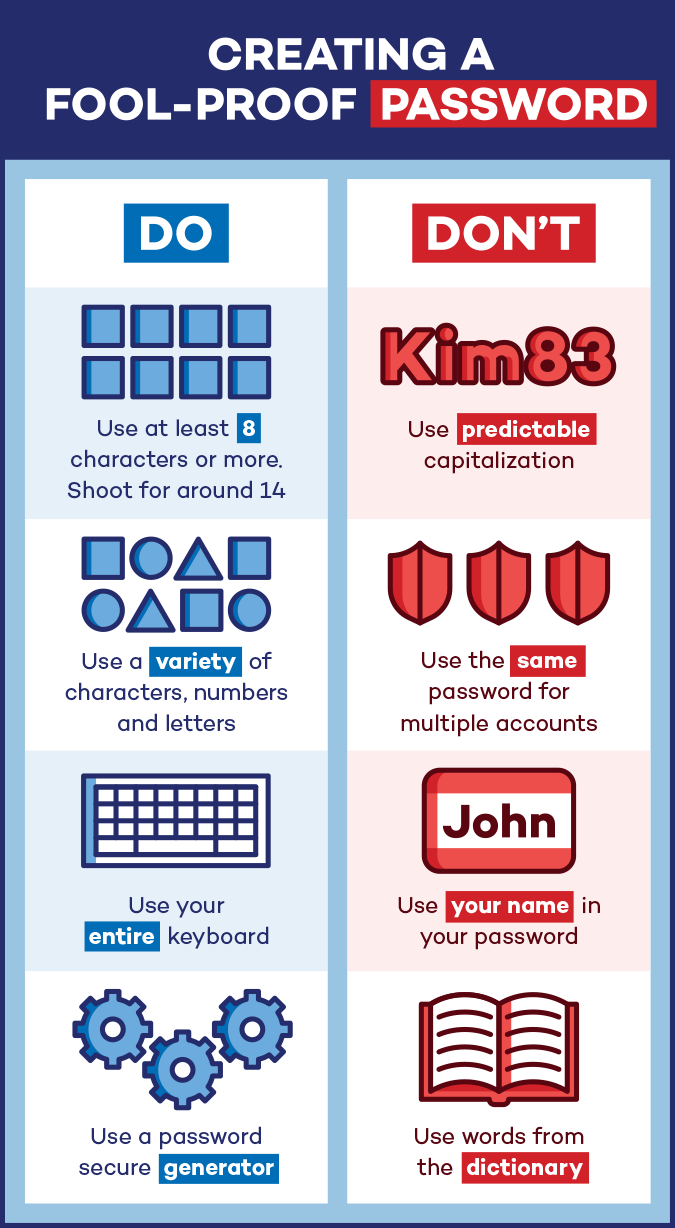
A password that is at least 14 characters is ideal. Eight characters is the shortest that a password should be. Make sure to use a variety of characters, numbers, and letters that have seamlessly no correlation or direct link to you or your hobbies.
Avoid predictable patterns in letter capitalization like at the beginning or end of your password, or for proper nouns. Also, try to use your entire keyboard, and not just characters you use on a daily basis, as hackers know this and will target the common characters.
Password Protection: Keeping Your Passwords Safe
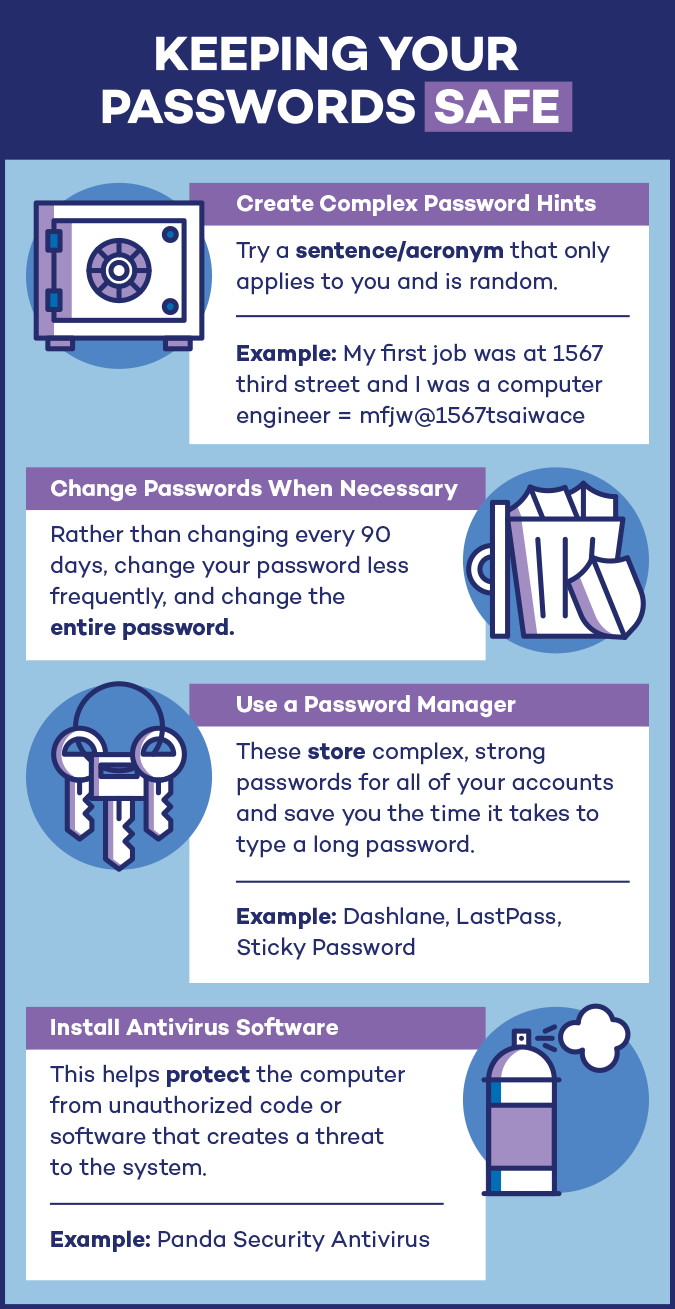
In order to keep your passwords locked and secure, it’s important to create quality passwords and use security measures when creating new accounts. While many studies used to say to change your password every 90 days, the newest guidelines actually suggest changing your passwords when necessary, as changing too often can actually hurt you rather than help you.
Also, make new password hints as these are easy ways for hackers to receive a “recovery email” with your account information. Try to use uncommon answers such as obscure teacher names, or even create random answers and write these down to remember. Another technique is to create a sentence or acronym that only applies to you but is random enough to fool hackers.
Use a password manager such as Dashlane, LastPass, or Sticky Password. These tools generate and store complex passwords for you. The password managers live in your browser and can fill in your login information whenever on a site.
Lastly, install antivirus software for password protection across the internet. Install your antivirus on all devices, in order to keep tabs on suspicious activity and keep unknown downloads from installing on your computer.





12 comments
This is a great article, excellent in fact. I use 16 letters,numbers,and symbols and I have been on the internet since inception and when I was able to use as many characters. As I wanted I have used 16 and never have been hacked not even by my ex’s and children lol
Hello Michel,
We are glad to know you liked our article! Also happy to see you are a carefull Internet user. There should be more like you! ?
Kind regards,
Panda Security.
Yes, the password is important but one needs to check the type he/she installing, As the mobile is the only big thing, most security happens in mobile device now. Many apps, mostly pirated ones create a backdoor entry on the mobile device. When comparing with Android, iOS seems to be more secure due to the high moderation on App store.
Since a few weeks I have downloaded Dashlane and it works alright. But now it will cost about 40 € p.a. I would have preferred to find a passwork manager within the Panda product world.
Hello,
Panda Dome Complete and Panda Dome Premium both offer Password Manager. You can find more information on this link: https://www.pandasecurity.com/homeusers/
Thanks for getting in touch!
Best regards,
Panda Security.
thanks for the information
A decent VPN supplier, similar to Le VPN, will have servers in various areas around the globe empowering clients to pick voluntarily where their IP address is found. Le VPN has servers in over 120+ nations settling on it a top decision for web based gushing free TV.
Hi
I’m not really sure with set up a good password but in this article sharing huge information about how to protect our password now I know exactly How to Protect ourselves…
Thanks
Michel.J
As a technology enthusiast, I appreciate the depth of your insights.
I’m really glad that there’s technology like dashlane and lastpass. I have such a bad memory that I tried to use same pass pattern is many of my accounts.
I thoroughly enjoyed your post! The depth of insights presented in such an engaging manner made it a pleasure to read.
As a technology lovers, I appreciate the depth of your insights on this post.