If you are one of the many people that uses a simple password for your accounts, your information is at risk.
A brute force attack is a hacking strategy in which a cybercriminal attempts to log into an account by trying multiple password options until successful. With the help of computer scripts, hackers can make thousands of attempts per second — hacking simple passwords in the blink of an eye.
While this is a common threat to online safety, there are plenty of ways to protect yourself from these attacks. In this article, we will detail the basics of brute force and go through ways to stay safe with password management and similar strategies. Read on to ensure your information remains secure.
What Is a Brute Force Attack?
A brute force attack is a hacking strategy that uses guesswork to obtain passwords and other confidential login information.
This method is primarily fuelled by trial and error, as the hacker — either by hand or with the help of a computer script — tries multiple usernames and passwords to gain access to the target’s account. If successful, this process can take anywhere from a few seconds to a few weeks.
Brute force attacks are an older method of hacking but people are still at risk today, as many people have poor password security on their accounts.
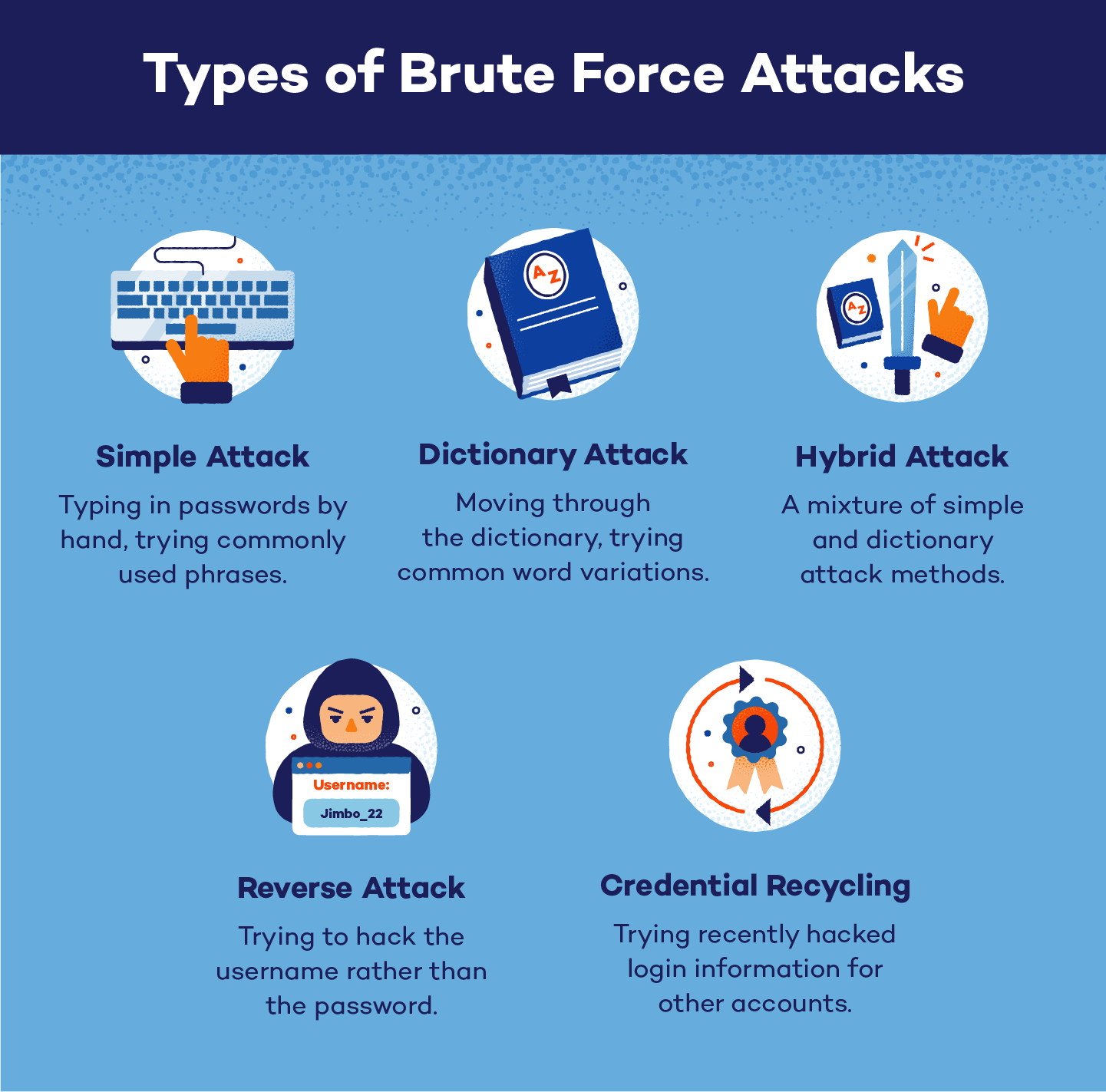
Types of Brute Force Attacks
Brute force attacks can happen in various ways. Here are five of the most common types of brute force attacks:
Simple Attack
Simple brute force attacks are just that — simple.
This is the most basic of methods in which a hacker attempts to guess login credentials by hand, without the aid of a computer. This tactic works when the target has extremely basic passwords, such as “password,” their birthday or other easily identifiable information.
Dictionary Attack
Similar to simple attacks, dictionary attacks involve using common words or phrases to guess the password of an account. This can be done when cybercriminals move through an actual dictionary by trying and augmenting frequently-used password terms in an effort to gain access to the target’s system.
While not technically a brute force attack, hackers use this method to aid their password-cracking abilities.
Hybrid Attack
A hybrid attack is a mixture of a simple attack and a dictionary attack.
Once the hacker has the username of the account they want to access, they will try a mixture of simple phrases, common words and any personally identifiable information. Password guesses using birth dates, birth places or pet names — such as “Minneapolis1982” or “Spot123!” — could be good jumping-off points for a hacker using this method.
Credential Recycling
Credential recycling involves using recently cracked login information for other websites or accounts. For example, if a hacker just got access to a target’s email account, they may try to use the same login credentials to infiltrate their social media or bank accounts as well.
Reverse Attack
Reverse attacks happen when hackers know the password for an account, but not the username.
Oftentimes, cybercriminals will gain access to passwords via data breaches, leading them on a hunt to find the correct username. Usernames are easier to crack than passwords, but this process still involves sifting through millions of different options.
How Common Are Brute Force Attacks?
Brute force attacks are a more basic form of hacking and remain a consistent threat to individuals and corporations with poor security or password etiquette. In March of 2020, when the country largely shifted to remote work, there were roughly one million attempted brute force attacks per day.
Why Do These Attacks Happen?
There are different types of hackers: Some help organizations improve their security systems, and some —like brute force attacks — illegally access information for personal gain.
By using these methods, cybercriminals can steal personal information, spread malware and hurt the reputation of a person or business. A few common brute force attack motives are as follows:
Exploiting Online Ads for Profit
By gaining access to websites and online advertising accounts, hackers can manipulate the messages for profit. One way of doing this is to reroute the advertising links.
After breaching the intended account, the hacker can change the hyperlinks on the website advertisements or alter the ad message entirely. This routes unsuspecting users to a website of the hacker’s choosing and leads to illegal sales commissions or ad revenue.
Stealing Personal Information
Stealing personal information can be a goldmine for hackers.
Once cybercriminals have access to someone’s account, it’s possible to use this information to access other personal accounts, bank information, Social Security numbers and a host of other sensitive data. From there, they can exploit this information however they choose or sell it to the highest bidder.
Spreading Malware
After a hacker breaches someone’s account, they may use viruses such as malware to disable systems for the fun of it or gain access to other accounts via texts or emails. This can lead to deeper infiltration into an organization, where cybercriminals can obtain more personal information from internal directories or website visitors.
Hijacking a System or Network
With valid login credentials, hackers can take control of a company’s IT infrastructure to gain more information or coordinate cyberattacks. Different methods like distributed denial-of-service (DDoS) attacks can cripple a network, gather valuable data or cause panic in an organization.
Hurting a Business’s Reputation
Having access to a system or website means that a hacker can control the content that customers see. Shutting down the website entirely or displaying offensive content are common methods to ruin a business’s reputation and hurt their sales.
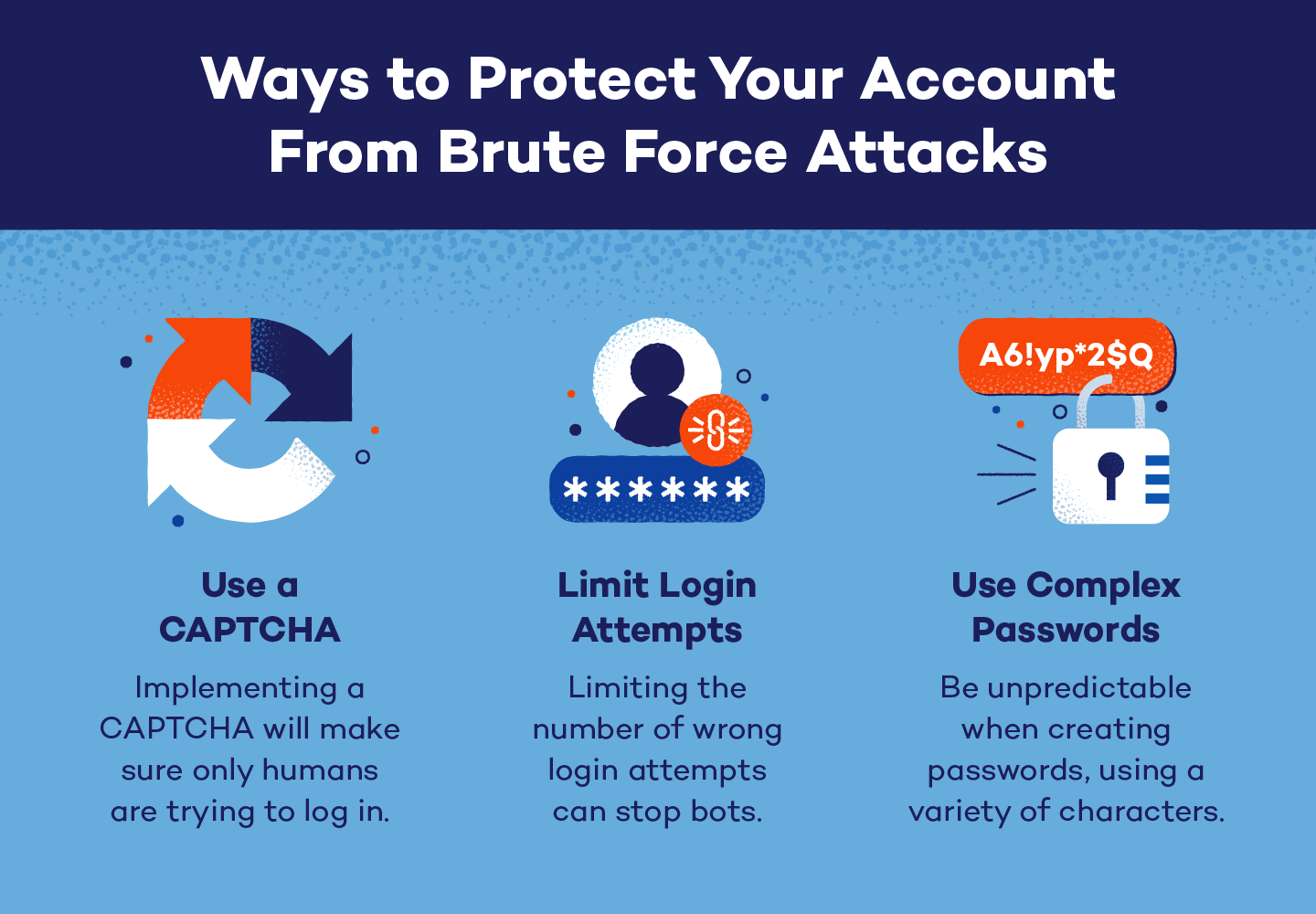
How to Protect Your Information
Brute force attacks are a common cybersecurity issue, and it’s important to protect your information as best as you can. While it isn’t necessary to enact an entire vulnerability assessment, a few simple changes in your day-to-day operations can make a world of difference.
Use Longer, More Complex Passwords
Cybercriminals can hack basic passwords in the blink of an eye, and the time to crack a password is directly proportional to how long and complex it is. Therefore, when you’re creating or changing passwords, factors such as complexity and unpredictability are incredibly important. A few best practices when creating passwords include:
- Using a password manager: With password managers, users can have strong passwords for every account without needing to memorize them. This software generates complex login information and securely stores data to ensure your accounts stay safe.
- Using eight characters or more: You should be using at least eight characters in your passwords, with a goal of 14.
- Using a variety of characters: Don’t only use lowercase letters or numbers because it’s easy for you to remember. Switch up your passwords with symbols and capitalization to increase complexity and safety.
- Being unpredictable: The more predictable a password is, the easier a brute force attack will be. Use random capitalizations, numbers and symbols throughout to make passwords harder to guess.
- Not using personal information: Never use personal information in your passwords. This can include your name, home town, job or anything else that could easily be found with a bit of cybersleuthing.
Use CAPTCHA
Have you ever tried to log in to a website and the system made you click pictures of a bus before you could continue? That is called a CAPTCHA (Completely Automated Public Turing test to tell Computers and Humans Apart), and it’s a powerful tool to guard against brute force attacks.
A CAPTCHA will fend off bots by requiring some form of human interaction. Whether it be clicking a box, typing characters into a text area or clicking all of the pictures of a certain item, they’ll make sure there is a real person on the other side of the screen.
Since brute force attacks are usually run with bots or computer scripts, a CAPTCHA can be a powerful ally against these cyber attacks.
Limit login attempts
Everyone has been locked out of an account for typing in the wrong password too many times. Businesses don’t do this for the sole purpose of annoying their customers — they do it to protect you against brute force attacks.
Since these attacks require up to thousands of tries to successfully crack a password, an organization limiting the number of login attempts can stop brute force attacks before they are successful.
Other Brute Force Attack FAQs
Finally, here are a few frequently asked questions and answers about brute force attacks.
How Does Brute Force Work?
Brute force attacks are when hackers try to gain access to an account by using guesswork. This can include techniques such as hybrid attacks and credential recycling with the goal of gathering passwords and other confidential information.
Do Hackers Still Use Brute Force?
Yes, hackers still use brute force attacks. While this is an older method of obtaining information, brute force hacking is still alive and well in the cyber world — and can result in big problems for your data, business or home network if not thoroughly secured.
How Long Will it Take to Crack My Password?
It can take as short as a few milliseconds and as long as thousands of years to crack a password. It is entirely dependent on how unique and complex it is.
Panda Security can help protect your data
Brute force attacks are a common problem that everyone should be aware of. Using easy-to-guess passwords leaves accounts vulnerable to infiltration, resulting in identity theft, financial hardships and business attacks.
Whether it be password security or consistent system monitoring, Panda Security can help you or your business stay safe from brute force attacks and other cyber threats. Start protecting your confidential data today.





