Post Updated on 6/24/09 at 7:52 PM
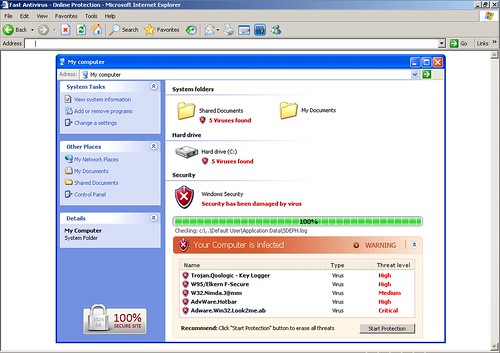
For the past few weeks, cyber criminals have been targeting Twitter users by creating thousands of messages (tweets) embedded with words involving trending topics and malicious URLs. If the URLs were accessed, the victims would arrive at a rogueware website designed to trick them into thinking that their computer is infected, therefore justifying the need to purchase the fake software offered.
Since the initial discovery, we have been keeping a close eye on this attack, but the malicious tweets continue. From June 2nd – 3rd we noticed over 3,000 of these malicious tweets (actually, the number is a lot higher than 3k because we only tracked the main abuse site and excluded the shortened URL’s from the initial search). On June 6th, the main site was taken offline and the attack shifted from Adware/PrivacyCenter to the Adware/FastScan. On June 23rd, the fake screen saver website appeared.
Update
In the last 48 hours we have observed over 54,000 malicious tweets on
Twitter.
We have been working tirelessly with various URL shortening services, in
conjunction with Blogspirit, Bloglines, and Twitter to get these malware sites and
accounts taken down as soon as possible. The attack has reduced by now,
but it's not going to go away. Understand that we are witnessing the
evolution of Blackhat SEO right in front of our eyes. In the past, the
cyber criminals had to wait for search engines to index their malicious
content. This meant that they could not take advantage of 100% real-time
trends. With an open communication tool and a readily available API,
cyber criminals are now able to prime their SEO campaigns in real-time via Twitter.
At the same time, they also generate the same old BHSEO campaigns on the search
engines. Evidence of this was first shown in our earlier posts of a
tandem attack on Google search results and Twitter (http://bit.ly/XSwBS, http://bit.ly/lFde3) Luckily,
Twitter's problem is easier to fix than the problem with search engines, which
must rely on search algorithms. Since Twitter has not publicly
acknowledged the situation, we'll just have to wait and see what they do.
Current targeted phrases:
Outlook 2010, Spain, HTC-Touch, Korea, Argentina, Transformers 2, Perez Hilton, Ed McMahon, #iranelection, free, invites, fake, girls, follow, blackout, control, tehran, Fathers Day, Fake Twitter Invites, WordPress 2, Fallon, Top Chef, Tila Tequila Live, AT&T, Limp Bizkit, Sytycd, iPhone, Adam Lambert, Wipeout, Holocaust Museum, Miss California, Claim your Facebook, Squarespace, Lakers, NBA Finals, Zack Morris, addict, video, trailer.
Malicious Tweet:

Malware distribution sites: (Updated 6/24/09 6:57 PM)
Bloglines page
Blogspirit Page
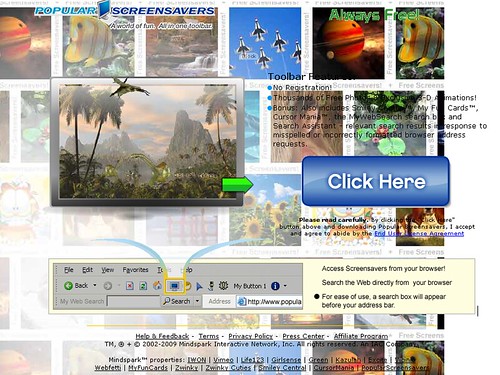
Fake screen saver website
Fake codec website
Fake scan site
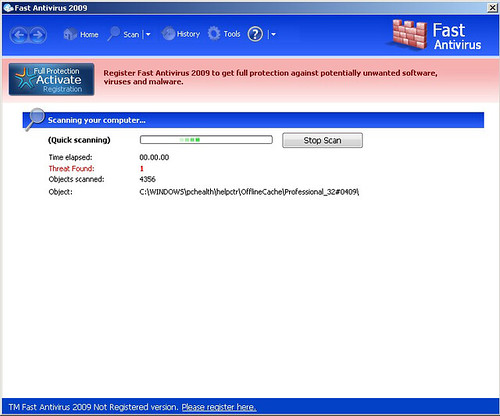
File: Adobe-Flash-Player-Upgrade-Pack_125.exe
File: Setup_build6_27.exe (MD5: efe9ddbea8bd71fdfee44d44811e4695 )
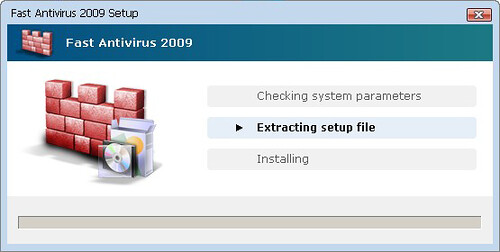
Installer:
Adware/FastAntivirus
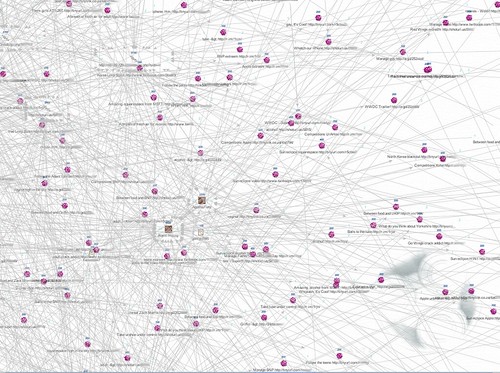
Visualization: (Updated: 6/24/09)
Blue = Twitter Account
Yellow = Tweet
2 hour capture of malicious tweets (Updated 6/24/09 6:57 PM)
Zoom in:
The ease of carrying out this type of attack leaves us to believe that this will not go away anytime soon. We’re all going to have to work together in taking these threats down and the good news, in this case, is that I have already received a response from the abuse team at TinyURL and they have responded by killing the redirections on their end. Now all we need is for everyone else to start working together and we’ll be able to help take these dangerous accounts down sooner!