Situation
This article provides you with guidelines and recommendations regarding the protection upgrade of Panda Adaptive Defense/Panda EndPoint Protection products in your network environment.Panda Security products are widely tested in our QA department and pre-release phases yet, there may be custom applications and particular environments that may not be fully covered. Therefore, the main objective of this guide is to reduce the risk of any potential issues and ensure a smooth upgrade of your network environment.
Considerations
If you are reading these lines, it is because you are planning to upgrade your environment, usually, because you want to test a new product feature or you want to install a new version that includes a fix for an existing issue. These specific upgrade requests are usually managed directly with a Panda Account Manager or Support representative.
As a general consideration, keep in mind that a version upgrade could, in some cases, lead to the following:
- Console version upgrade (transparent, at the Panda server side).
- Agent version upgrade (transparent, does not require reboot, at the endpoint side).
- Protection version upgrade.
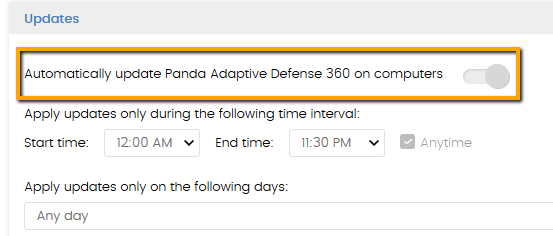
This article refers to the protection version upgrade, which is the most sensitive module of our security products. Remember that the protection upgrade is configured from the administration console:
|
Implementation of a controlled protection upgrade process
For the purpose mentioned above, we will carry out a controlled protection upgrade process. In this way, we will limit the updating process to a few endspoints and profiles, which you, as network administrator, will designate according to your criteria. Once you verify the correct functioning after the protection upgrade, we recommend that you plan and execute the process gradually for the rest of your network. Follow the steps below:
- Disable the Upgrade option in ALL your profiles.
- Create a profile and group and include a set of boxes that you, as network administrator, consider representative of your environment:
- Endpoints: standard endpoint, endpoint with key business applications, endpoints with the settings specific to the management team, etc.
- Servers with key custom applications, etc.
- Enable the upgrade for that profile.
- Monitor the upgrade for a reasonable period of time, for example 1-2 weeks, to ensure the upgrade has been carried out in those boxes and all the applications are working as expected. Keep in mind that in most of the cases, the upgrade will require a complete reboot. If you find any problem, click here to raise a case with your Support representative.
- Split the deployment of the protection upgrade of your network progressively. The process can be done in 2-3 phases, depending on your network configuration (number of endpoints, servers, etc.).
Take into consideration that in order to ensure the best protection of your environment, ALL the endpoints of your network, including your servers, must be migrated to the latest protection, in order to get the latest available technology. Therefore, it would be wise to include the Panda protection upgrade in your next planned maintenance window you schedule.
From this point on, any further installation in your network must be done using the latest installer, available at the Panda administration console. Although old installers might work, they will lead to unnecessary bandwidth consumption and upgrades.
What's more, if you are using gold images or any other imaging system, for example, virtual boxes shots, it is advisable to plan as soon as possible the upgrade of the Adaptive Defense/Endpoint Protection agent to the new version.