Cybercrime is a very profitable and attractive business. This is a new phase of cyber theft that involves stealing money directly from banks, rather than from their customers, using phishing attacks to infect the computers of bank employees. The million-dollar question is: where are the largest sums of money? They are, without a doubt, in the financial institutions themselves.
Panda Security launches a Survival Guide for Million- Dollar Cyberattacks , where analyzes the main tendencies of cybercriminal activity in the banking sector, and offers recommendations on how to avoid advanced attacks on users of online banking platforms and on the banks themselves.
Trends in Financial Cybercrime
International organizations are proposing actions to reinforce banks against cyberattacks in the face of increased attacks on the SWIFT network, with a 20% success rate for cyberheists. In addition, the use of malware for Android will rise among cybercriminals, increasing the number of victims of phishing or banking Trojans.
Despite being a sector that uses the very best anti-malware solutions, advanced attacks can still compromise large amounts of sensitive information at financial institutions:
These attacks have been traditionally aimed at customers of financial institutions, as they are the weakest link in the chain and the easiest to compromise. However, in recent years we’ve seen how criminal groups have diversified, and seek out money in other areas:

ATMs: These are also nothing more than computers with a very specific purpose, and cases have been recorded in which hackers have infiltrated them to withdraw money directly.

Banks: These highly-sophisticated attacks require far greater resources and ingenuity to carry out, but the million-dollar payoffs make it worth the while for attackers.

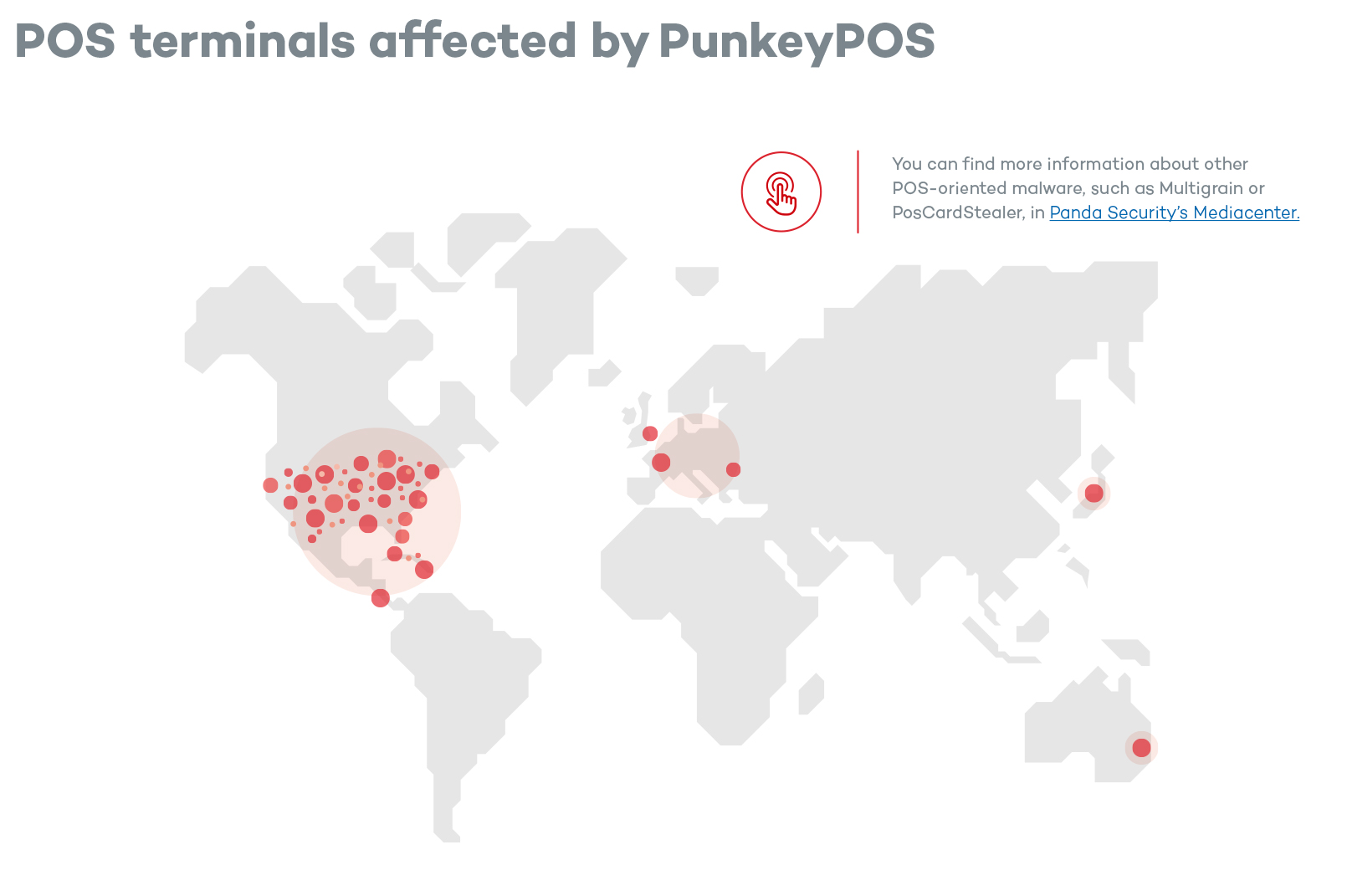
Computer- controlled POS terminals: malware specifically created for these terminals does exist, and is used to steal information from debit and credit cards.
Recommendations for avoiding Cyberheists
One of the most frustrating things for victims is the lack of information shared with them about the attack. For example, after the attack on the Bangladesh Bank, three samples of malware were recovered — and that is all that was left behind. The attackers surely used many other tools that were deleted after use, and of which the victims will never know a thing.
Panda Security’s corporate security solution, Adaptive Defense, protects the data and sensitive information of financial institutions and their clients, detecting data leaks whether they come from malware or from the bank’s own employees. This is considered to be one of the most valued abilities in the sector.








4 comments