Using public Wi-Fi networks can pose significant security risks, including exposure to evil twin attacks. An evil twin attack is dangerous because hackers can obtain sensitive information like your financial accounts, passwords, credit card transactions and more. A hacker can use this information to steal money, commit identity theft or open a fraudulent account in your name.
Read on to learn how an evil twin attack works, tips for protecting yourself and what you can do if you fall victim to an attack.
What Is an Evil Twin Attack?
An evil twin attack is a spoofing cyberattack that tricks users into connecting to a fake Wi-Fi access point that mimics a legitimate network. Once a user is connected to an evil twin access point, hackers can access everything from their network traffic to private login credentials.
Evil twin attacks get their name from their ability to imitate legitimate Wi-Fi networks to the extent that they are indistinguishable from one another. Hackers create these false networks to trick unsuspecting users into logging in and accessing user data to steal personal information and commit crimes. This is especially dangerous for users who use the same username and password for multiple accounts since the hacker could gain access to all of them by monitoring just one login attempt. What’s worse, these attacks are nearly impossible to identify.
How an Evil Twin Attack Works
The most dangerous evil twin attacks work by tricking victims into thinking that they are connecting to a reliable public Wi-Fi network. To make the attack as believable as possible, hackers typically use the following steps.
Step 1: Choosing a Location With Free Wi-Fi
Hackers choose a busy location with free, popular Wi-Fi, like an airport, library or coffee shop, to execute their attack. These places often have multiple access points with the same name, making it easier for a hacker’s fake network to go unnoticed.
Step 2: Setting Up a Wi-Fi Access Point
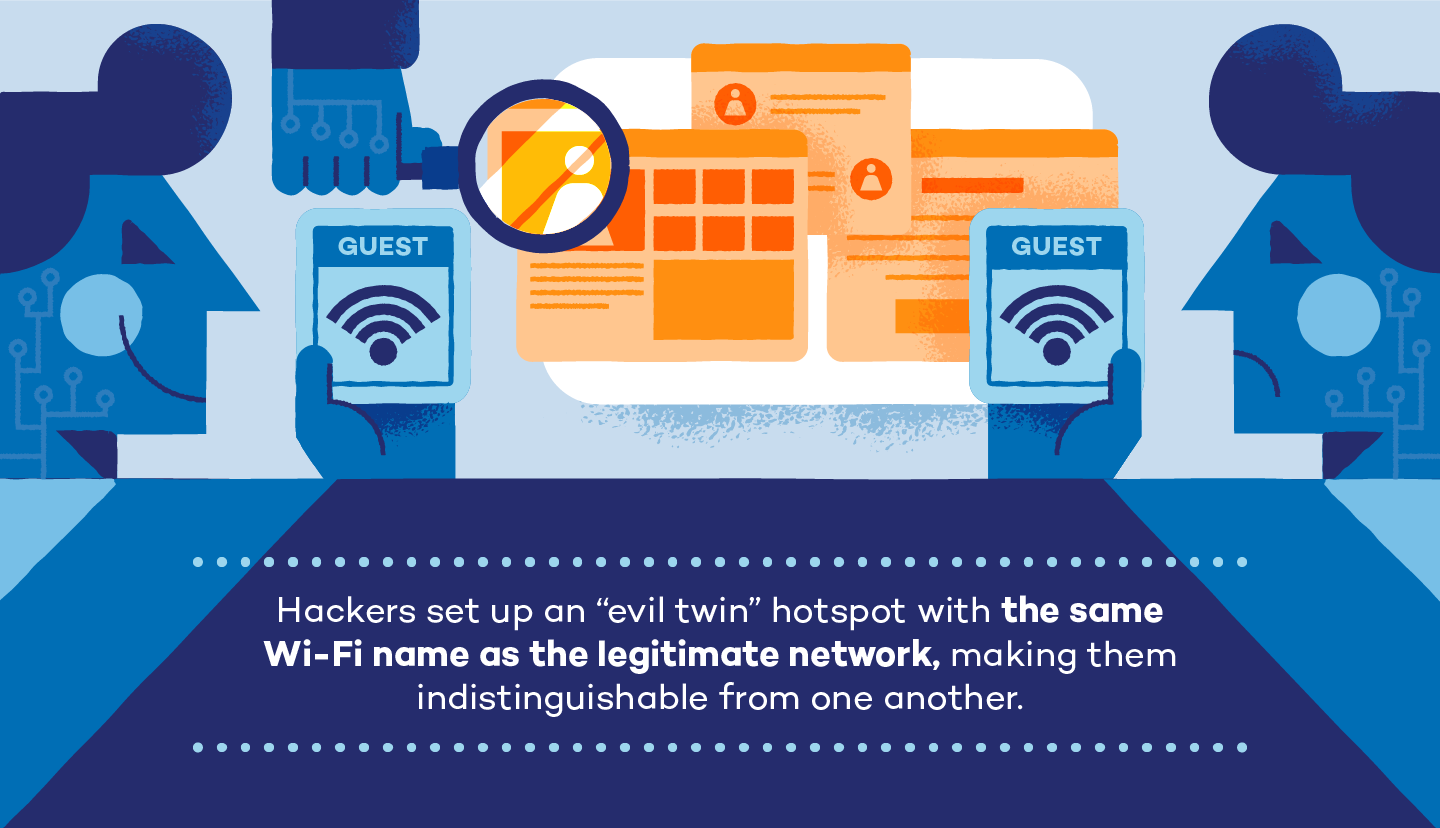
Next, the hacker creates a new hotspot using the same Service Set Identifier (SSID) name as the legitimate network. They can use almost any device to do this, including phones, laptops, portable routers and tablets. Some hackers may even use a Wi-Fi Pineapple to achieve a broader range.
Step 3: Creating a Fake Captive Portal Page
If you’ve ever logged into a public Wi-Fi network, you’ve probably encountered a captive portal page. These typically require you to enter a password or other basic information to access the network.
While many legitimate networks use these, hackers can easily replicate them to trick users into sending over their login information. Unfortunately, it can be nearly impossible to tell the difference between a legitimate and fake captive portal page if the hacker knows what they’re doing.
Step 4: Setting Up Closer to Potential Victims
Once a hacker has finished setting up the evil twin access point and fake captive portal page, they may move their device or router closer to potential victims to create a stronger signal. This convinces people to choose their network over the weaker ones and forces some devices to connect automatically.
Step 5: Monitoring and Stealing User Data

Once a victim has connected their device to an evil twin network, the hacker can monitor everything they do online, from scrolling through social media accounts to checking bank statements. If a user logs into any of their accounts while connected to the network, the hacker can collect their login credentials. This is especially dangerous if the user uses the same credentials for multiple sensitive accounts.
Rogue Access Point vs. Evil Twin: Key Differences
A rogue access point can be considered an evil twin; however, the terms are not interchangeable. A rogue access point is an unapproved wireless connection point added to a network without the network administrator’s awareness or consent. An evil twin is essentially a copy of a real Wi-Fi network connection. Examples of rogue access points include unauthorized Wi-Fi routers, incorrectly set up devices or even forgotten devices with wireless connectivity.
To understand the difference between rogue access points and evil twin attacks, imagine this scenario:
Let’s say a worker installs a personal wireless router in their workspace without authorization from management. This device would be considered a rogue access point because it operates without the proper authorization to be there. But if the worker were to clone the company’s Wi-Fi and use that fake copy to steal sensitive information from the people who connect to it, that would be considered an evil twin attack.
You can install software like Wi-Fi protection and network monitoring tools to help detect rogue access points.
Evil Twin Attack Example
Let’s say that a user decides to connect to a public Wi-Fi network at a local coffee shop. They’ve connected to the access point there before, so they assume it’s safe and reliable. This time, however, a hacker has set up an evil twin network with an identical SSID name and a stronger signal than the legitimate access point. The user connects to it despite it being listed as “Unsecure.”
While connected to the network, the user logs into their bank account to check their balance and later accesses their company’s portal to catch up on work. Because the user has not set up a virtual private network (VPN) to encrypt their data, the evil twin network allows the hacker to access their banking information and company website.
How to Protect Yourself From an Evil Twin Attack
Evil twin attacks can be difficult to identify, but there are multiple steps you can take to protect yourself when connecting to public Wi-Fi networks.
Use Your Own Hotspot
The easiest way to protect yourself from an evil twin attack is to use a personal hotspot instead of public Wi-Fi whenever possible. This ensures that you always connect to a reliable network in public spaces and prevents hackers from accessing your data. Just remember to set a password to keep your access point private.
Avoid Unsecured Wi-Fi Networks
If you need to connect to a public network, try to avoid any access points marked “Unsecure.” Unsecured networks lack legitimate security features, and evil twin networks almost always have this designation. Hackers often rely on people brushing this off and connecting to their network without knowing the risks.
Disable Auto Connect
If you have auto connect enabled on your device, it will automatically connect to any networks that you have used before once you’re in range. This can be dangerous in public places, especially if you have unknowingly connected to an evil twin network in the past. To ensure that you always connect to the network you want, disable auto connect any time you leave your home or office.
Never Log Into Private Accounts on Public Wi-Fi
You should avoid logging into private accounts whenever possible when using public Wi-Fi. Hackers can only access your login information if you use it while connected to their evil twin network, so remaining signed out can help protect your private information.
Use a VPN to Encrypt Traffic

A VPN can help protect you from an evil twin attack by encrypting your data before a hacker sees it. When you download a reliable VPN app to your device, it encrypts or scrambles your online activity before sending it to the network, making it impossible for a hacker to read and understand.
Stick to HTTPS Websites
When using a public network, be sure to only visit HTTPS websites. These sites offer end-to-end encryption, preventing hackers from monitoring your activity while you use them.
Use Two-Factor Authentication
Adding two-factor authentication to your private accounts is a great way to prevent hackers from accessing them. Even if a hacker gains access to your login credentials, the two-factor authentication will prevent them from successfully accessing your account.
Use Private Search Engines and Browsers
Private search engines like DuckDuckGo and privacy-focused browsers like Firefox can prevent tracking and data collection while browsing the internet. If you accidentally connect to an evil twin network, these browsers have built-in features like pop-ups that warn against malicious sites and malware. They can also look up a site’s IP address to ensure it’s secure.
Although private browsers reduce the chance of revealing personal information to hackers, they are not specifically designed to detect or prevent connections to evil twin networks.
Enable WPA3 Encryption
WPA3 is the latest Wi-Fi security protocol. It defends against brute force and evil twin attacks by encrypting your data. WPA3-Enterprise is a mode of WPA3 that improves security for public Wi-Fi networks and stops hackers from monitoring your online interactions.
While WPA3 significantly improves Wi-Fi security and guards against evil twin attacks, not all Wi-Fi networks support WPA3, and some older devices may not be compatible. Confirm yours is compatible before trying to enable it, as you may have to settle for WPA or WPA2 (which are still far better than nothing).
Update Software Regularly
Update your operating system, browsers and security extensions regularly to prevent security breaches from outdated software. Software updates often include patches for known vulnerabilities hackers could exploit. Updating your security software monthly or as updates become available ensures continuous protection.
Monitor Your Network
Use network monitoring tools to scan for nearby Wi-Fi networks regularly. Look for any unexpected or suspicious networks, especially those with names similar to known public networks. Avoid connecting to any strange networks and notify the network administrator in person or by emailing a detailed message about the suspected threat, time and location of any strange network behavior you noticed. Time is of the essence in these situations, so notify them as soon as possible.
What to Do If You Fall Victim to an Attack
If you discover that a hacker has breached your data through an evil twin attack, you can file a complaint with the FCC Consumer Complaint Center. You should also contact your local police department and your bank or credit card company if the hacker stole money or gained access to your banking information during the attack.
Protect Your Network With Panda Security
Evil twin attacks are just one method hackers use to gain access to sensitive information online. To further protect yourself from cyberattacks, consider reading up on the most common types of hackers and downloading reputable antivirus software. Contact our specialists online to discuss ways to keep your data secure.




