What Is a Heuristic Virus?
A heuristic virus is a type of computer virus that uses heuristic techniques to infect systems. Instead of following a specific set of instructions or patterns that are known to antivirus programs, it behaves more flexibly and adaptively.
You eagerly power up your computer, ready to dive into a day of productivity or leisure, only to be greeted by a digital nightmare: All your computer data is missing. Your system is infected with a mysterious and elusive intruder. This isn’t just any ordinary virus; it’s a cunning and adaptive foe known as a heuristic virus.
Heuristic viruses pose a risk of data loss by infiltrating systems and potentially corrupting or deleting files. This can disrupt personal or business operations and lead to irreplaceable data loss. These viruses can also compromise the stability of your device, causing frequent crashes, slow performance and overall diminished functionality.
In this post, we’ll explore how heuristic viruses work, how to get rid of them and, most importantly, how to protect yourself from their tricky attacks.
Heuristic Virus vs. Heuristic Analysis
While the term “heuristic virus” can refer to the method by which malicious code is detected, it’s better suited to describe a specific virus, Heur.Invader — a malware designed to change system settings.
What Is a Heuristic Virus?
Heuristic virus — a term used to describe the virus Heur.Invader — is a type of computer virus that compromises your system’s settings, opening the door to other malware. It operates by adapting and attempting to evade detection by security measures through unpredictable tactics.
A Trojan is a common type of heuristic virus that appears to be safe software but causes damage.
These viruses mess with your device’s settings or code, which lets malware sneak in. Sometimes, cybercriminals use heuristic viruses to put spyware and other harmful software on your device to steal your private information.
What Is Heuristic Analysis?
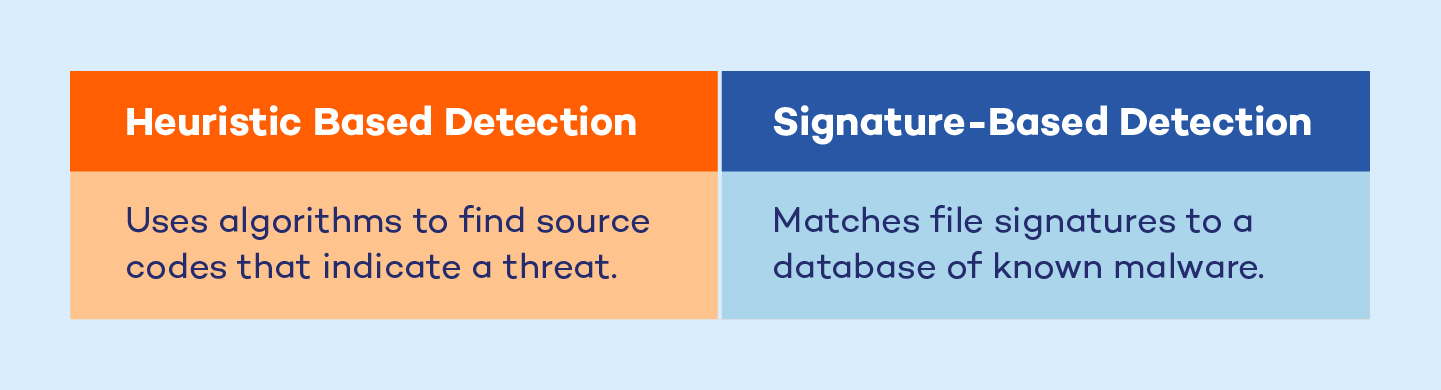
Heuristic analysis is a technique employed by antivirus software to identify potential threats that were previously unknown. Instead of relying on a list of known threats, it looks for suspicious behavior. It’s a smart way for antivirus software to catch new, unknown viruses before they cause harm.
Heuristic-based analysis uses several techniques to analyze behaviors and threat levels, including:
- Dynamic scanning: Analyzes the behavior of a file in a simulated environment
- File analysis: Analyzes the intent, destination and purpose of a file
- Multicriteria analysis (MCA): Analyzes the weight of the potential threat
What Is Heuristic Scanning?
Heuristic scanning is a technique used within heuristic analysis to find source codes to detect unknown viruses by looking for suspicious behavior or patterns in files or programs.
Adjusting the sensitivity level in heuristic scans determines how cautious the antivirus is about suspicious files. Higher sensitivity provides better protection but may flag more false positives.
How to Get Rid of Heuristic Virus
Reliable antivirus software is the key to detecting and getting rid of any type of virus, including heuristic viruses.

When removing the Heur.Invader virus, always boot the computer in safe mode. Doing so starts the computer only with the necessary drivers and services and won’t load the virus — which can disable antivirus software.
- Boot the computer in safe mode.
- Run your full antivirus software scan as normal.
- Once the scan denotes malicious code, inspect the element manually for false positives.
- Remove the malicious code.
How to Enable Safe Mode on Windows
To enable safe mode on your PC before beginning an antivirus scan, follow these steps:
- Access startup options: When the sign-in screen appears, hold the Shift key and select Power, then click Restart.
- Choose troubleshoot: Your PC should now know that you’re about to run an antivirus scan. You’ll see a prompt on the screen to “Choose an option.” Click Troubleshoot → Advanced Options → Startup Settings.
- Restart again: Wait for the next window to load and click Restart.
- Select safe mode: After a moment, you’ll see the startup options menu. Select number 4 or press F4 to enable safe mode.
How to Enable Safe Mode on Mac
To enable safe mode on your Mac before beginning an antivirus scan, follow these steps:
- Shut down your Mac: Click on the Apple menu and select Shut Down.
- Start your Mac in safe mode: Press the power button to turn on your Mac, then immediately press and hold the Shift key.
- Release the Shift key: Release the Shift key when you see the Apple logo and progress bar.
- Log in: Log in to your account once your Mac finishes booting up.
- Your Mac is now in safe mode: Perform troubleshooting tasks or run antivirus scans with limited functionality and only essential processes running.
How to Prevent Heuristic Viruses
Heuristic viruses, known for their adaptability and evasive tactics, can wreak havoc on your digital life. Here are some tips to safeguard your devices from heuristic viruses:
Install Reliable Antivirus Software
Installing reputable antivirus software is your first line of defense against heuristic viruses. Choose a comprehensive security suite that offers real-time scanning, heuristic analysis and frequent updates. Regularly scan your system and keep your antivirus software up-to-date to ensure maximum protection against emerging threats.
Protect your device from threats or cyberattacks with Panda Security’s Free Antivirus Software
Keep Software Updated
Regularly updating your operating system and software applications is crucial for staying ahead of heuristic viruses. Software updates often include security patches that fix vulnerabilities. Enable automatic updates whenever possible to ensure your system is always fortified against potential threats.
Be Cautious With Email
Heuristic viruses often spread through malicious email attachments or links. Exercise caution when opening emails from unknown senders or unexpected sources, and avoid clicking on suspicious links or downloading attachments from unfamiliar emails. Be wary of phishing attempts and verify the email’s authenticity before taking action.
Enable Firewall Protection
Enable the built-in firewall protection on your devices to create an additional barrier against heuristic viruses. Firewalls monitor incoming and outgoing network traffic, blocking unauthorized access and potentially harmful connections. Configure your firewall settings to restrict access to your system and enhance your overall cybersecurity posture.
Practice Safe Browsing
Heuristic viruses can exploit vulnerabilities in web browsers to infiltrate your system. Practice safe browsing habits by avoiding suspicious websites and not clicking on pop-up ads or unknown links. Be cautious when downloading files from the internet, and only visit reputable websites with secure HTTPS connections.
Create Strong Passwords
Strong passwords are essential for protecting your accounts from heuristic viruses and cyber threats. Use complex passwords that include a combination of uppercase and lowercase letters, numbers and special characters. Avoid using easily guessable passwords and never share your passwords with anyone.
Protecting your devices from heuristic viruses requires a proactive approach. By implementing reliable antivirus software, keeping software updated and practicing safe browsing habits, you can significantly reduce the risk of falling victim to these stealthy threats. Remember, staying vigilant and informed is key to maintaining a secure digital environment.




