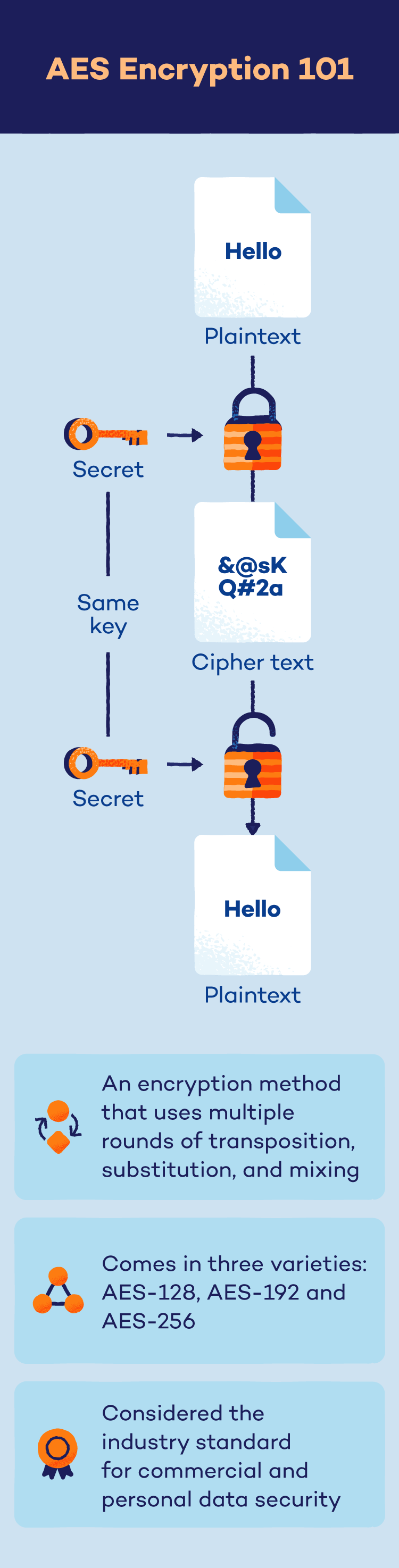
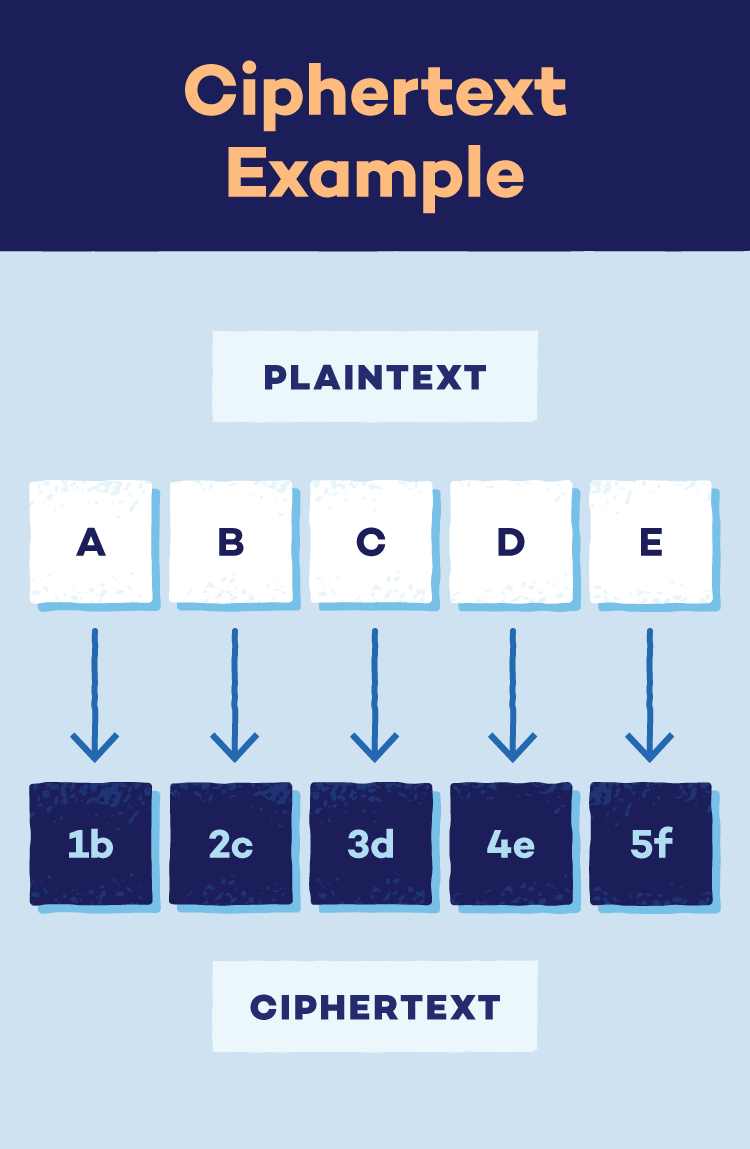
The Advanced Encryption Standard (AES) is an algorithm that uses a strong password (secret key) to scramble your files and messages, making them unreadable to anyone who doesn’t have the key.
Whether it be sending and receiving emails, transferring files or simply browsing the web, data transfer exists everywhere in our technological world.
In an age in which cybercriminals are trying to access that data at every turn, businesses and consumers alike need to be protected — and the first step is to learn what AES encryption is.
AES encryption is an encryption method that has become the industry standard due to its security, ease of use and speed. In this article, we will detail what AES encryption is, how it works and how Panda can equip you with this valuable security method via a VPN and password manager.
What Is AES Encryption?
The Advanced Encryption Standard (AES) is a powerful algorithm established by the U.S. government to electronically secure sensitive data. It utilizes a secret key to scramble information into an unreadable format, rendering it useless without authorized access.
Widely adopted by the U.S. government, businesses and individuals, AES safeguards critical information during storage or transmission. This ensures confidentiality even if data is intercepted by unauthorized parties.
This method was first conceptualized in 1997 when the National Institute of Standards and Technology (NIST) became vulnerable to brute force attacks and needed a stronger encryption method. NIST enlisted a pair of developers to tackle the problem — Vincent Rijmen and Joan Daemen — who developed the eventually selected technology, AES, in 1998.
AES has been the encryption standard for the NIST since its full-scale adoption in 2002. Overall, there are three main types of AES encryption:
- AES-128: This method uses a 128-bit key length for encryption and decryption, which results in 10 rounds of encryption with 3.4 x 1038 different potential combinations.
- AES-192: This method uses a 192-bit key length for encryption and decryption, which results in 12 rounds of encryption with 6.2 x 1057 different potential combinations.
- AES-256: This method uses a 256-bit key length for encryption and decryption, which results in 14 rounds of encryption with 1.1 x 1077 different potential combinations.
What Is AES Used For?
Even though AES was first formulated in conjunction with the United States government, this encryption method is now used in both governmental and civilian applications. A few of the most common uses of AES encryption include:
- VPNs: The job of a virtual private network (VPN) is to provide secure and private online browsing. Since this process connects users to different servers, AES encryption is used to protect user data against leaks and cyberattacks.
- Password managers: Password managers are used to safely store login credentials under a single master key. Given a single breach could compromise a user’s entire collection of passwords, AES is often used to secure this software.
- Wi-Fi: Wireless internet typically uses many encryption methods such as WPA2, and AES can often be found in these connections as well.
- Mobile apps: Any app that involves messaging or photo sharing typically utilizes AES to aid in data security.
- Internet browsers: When you visit a website that uses HTTPS, the communication between your browser and the website is encrypted using AES. This protects sensitive information you send or receive, such as credit card details or login credentials, from being intercepted by hackers.
- Databases: Databases often store confidential information, like medical records or financial data. AES can be used to encrypt this data at rest (when stored on a server) or in transit (when transferred between systems). This ensures that even if someone gains access to the database, they cannot decipher the information without the decryption key.
- Safeguarding sensitive files: You can use AES to encrypt individual files on your computer or other devices. This is particularly useful for protecting personal information such as documents, photos or financial records. Encryption ensures that even if someone steals your device or gains access to your storage, they cannot access the encrypted files without the decryption key.
How Does AES Work?
No matter the type of AES, the encryption process is similar and can be described in a series of steps:
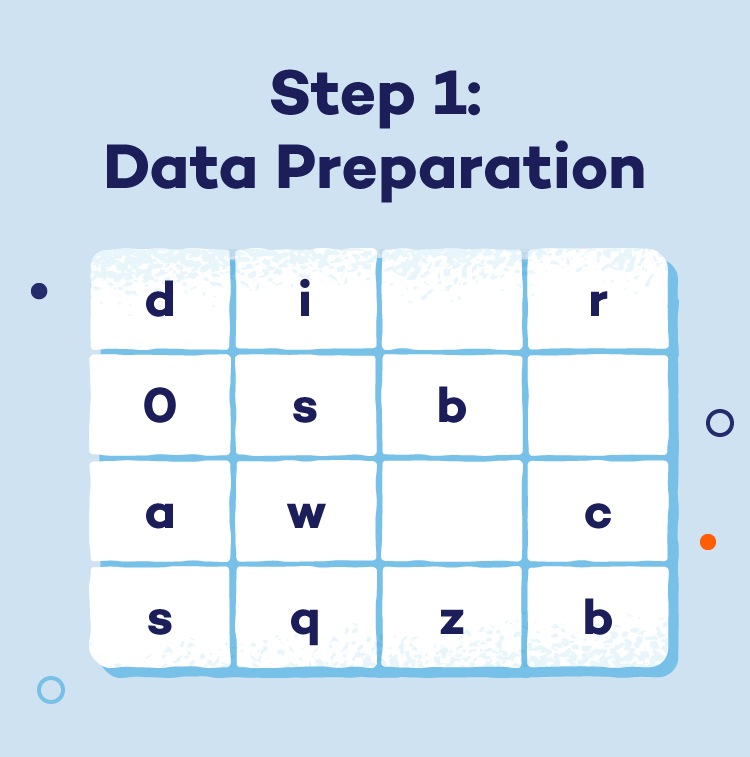
- Step 1: Data preparation: AES divides the initial message (plaintext) into fixed-size blocks (typically 128 bits) for efficient processing.
- Step 2: Key expansion: A secret key, crucial for both encryption and decryption, is used to derive a series of unique round keys. This expansion process enhances the overall security of the encryption.
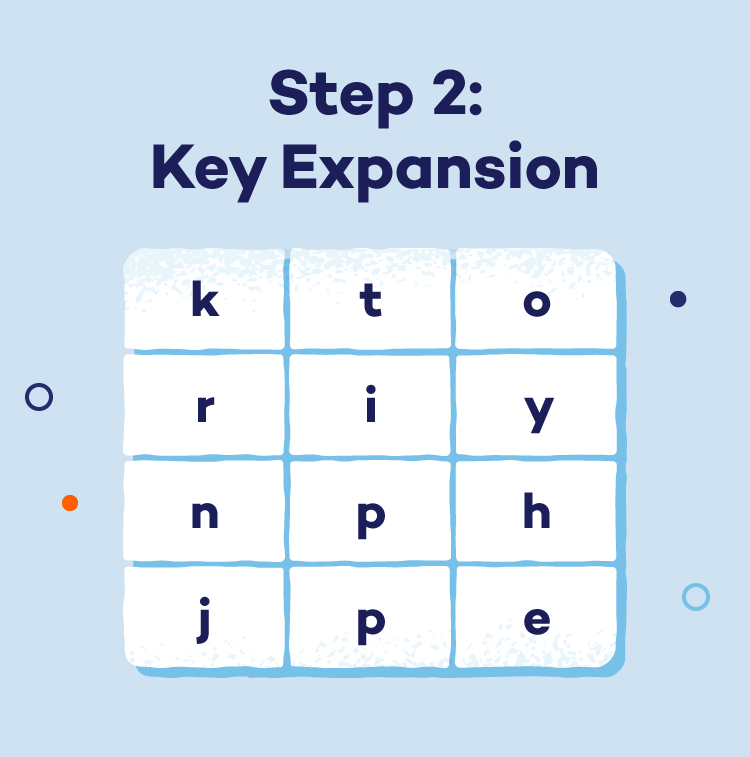
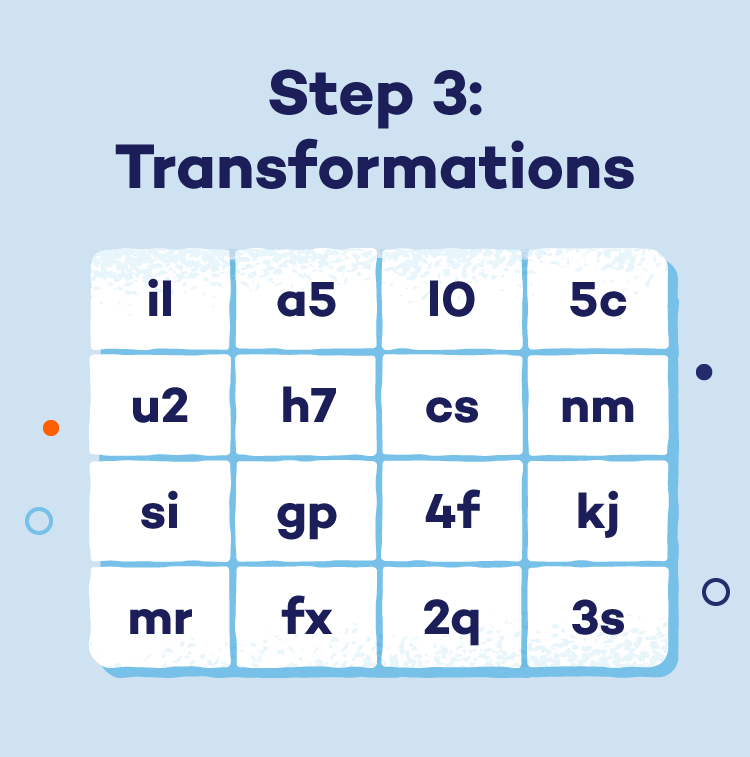
- Step 3: Transformations: Each data block undergoes multiple rounds of intricate transformations. (The number of rounds depends on the key length.) These rounds aim to thoroughly confuse the data via:
- SubBytes: A predefined table substitutes each byte in the block with a completely different byte.
- ShiftRows: The rows of the data block are cyclically shifted to disrupt any patterns.
- MixColumns: A specific mathematical operation mixes the data within each column, further enhancing obfuscation.
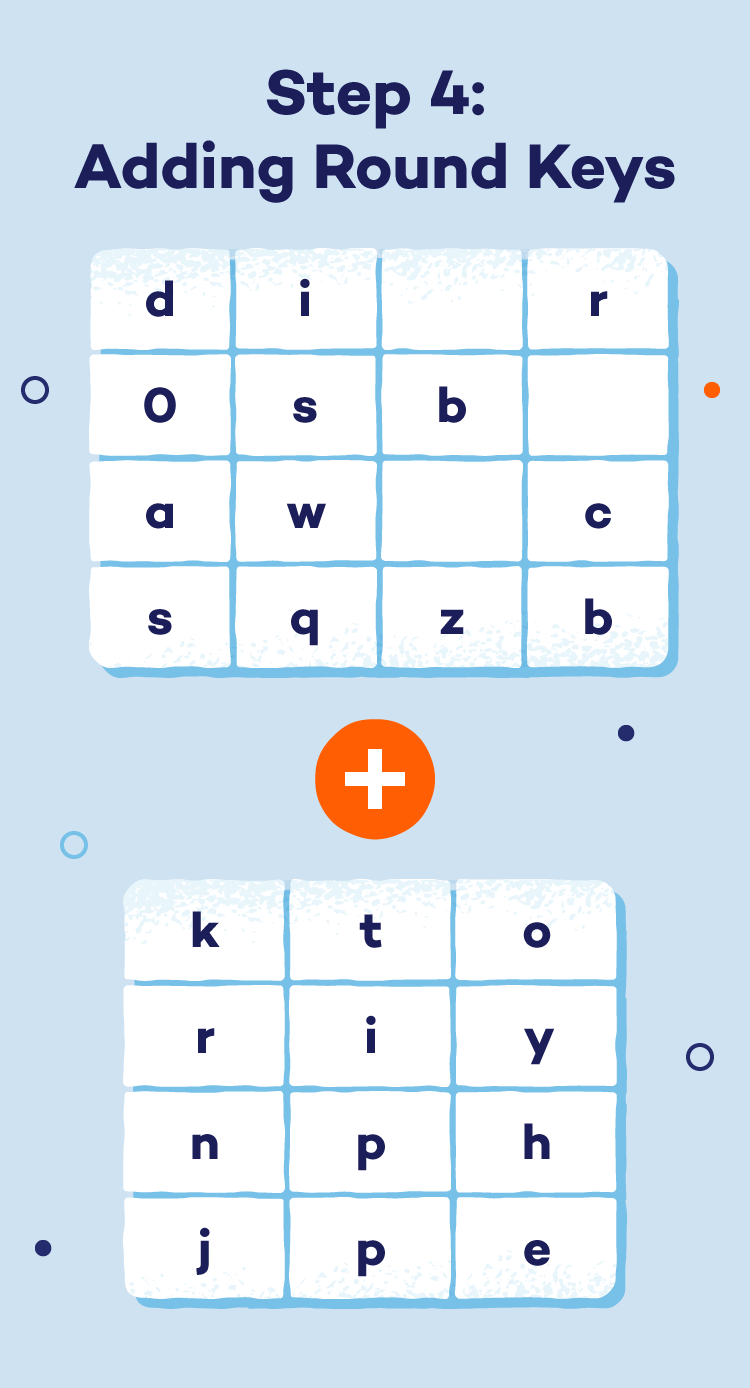
- Step 4: Adding round keys: In each round, a different round key (derived from the original secret key) is applied to the data block. This adds another layer of encryption with unique keys for each round.
- The result: Encrypted data (ciphertext): After all the rounds, the data blocks are transformed into an unreadable form called ciphertext. This ciphertext is what is securely stored or transmitted. Deciphering it requires the corresponding secret key.
Advantages of AES Encryption
AES is the preferred encryption method because it excels in many key performance metrics. A few benefits of AES include:
- Security: Even the lowest level of AES encryption, AES-128, would take an estimated 1 billion billion years (no, that extra billion isn’t a typo) to crack if using a brute force method.
- Cost: AES encryption is available for free, as it was originally developed to be released on a royalty-free basis.
- Ease of use: The AES algorithm is easy to implement across a multitude of applications and is known for its simplicity and ability to conform across hardware and software platforms.
AES Encryption Attacks
AES is a robust encryption algorithm widely trusted for securing sensitive data. However, no security measure is foolproof, and AES encryption is still susceptible to attacks, including:
- Side-channel attacks: These attacks exploit weaknesses in the implementation of AES rather than the algorithm itself. They might target information leaks during encryption, such as processing time fluctuations or power consumption. By analyzing these leaks, attackers could potentially glean clues about the secret key.
- Brute force attacks: This attack involves trying every single possible key combination until the correct one is found.
- Related-key attacks: These attacks are less common and require a specific scenario in which an attacker has access to multiple sets of data encrypted with related keys. By analyzing the relationships between the ciphertexts, they could theoretically gain insights into the key itself. However, this requires a very specific situation and is not a typical threat for most users.
How to Prevent AES Encryption Attacks
While AES encryption is powerful, a layered security approach is crucial. Here’s how you can minimize the risk of attacks:
- Create strong passwords: When using AES encryption (often found in disk encryption software or password managers), choose long and complex passwords for your encryption keys. Imagine your key as a gatekeeper — the stronger and more intricate, the harder it is to break in.
- Software updates matter: Keep your software up-to-date, especially security applications and disk encryption tools. Updates often include patches for vulnerabilities that could be exploited in AES implementations.
- Secrecy is key: Never share your encryption keys with anyone, and be mindful of where you store them. Avoid keeping them on the same device you’re encrypting. Consider using a password manager with strong security features.
- Use multi-factor authentication: Implement multi-factor authentication (MFA) whenever possible. MFA adds an extra step to the login process, requiring a second verification factor beyond your password. This makes it significantly harder for attackers to access your encrypted data, even if they obtain your password.
How Does AES Compare to Other Encryption?
While AES is an impressive encryption method, how does it compare to other options available? Here is how AES stacks up against similar systems.
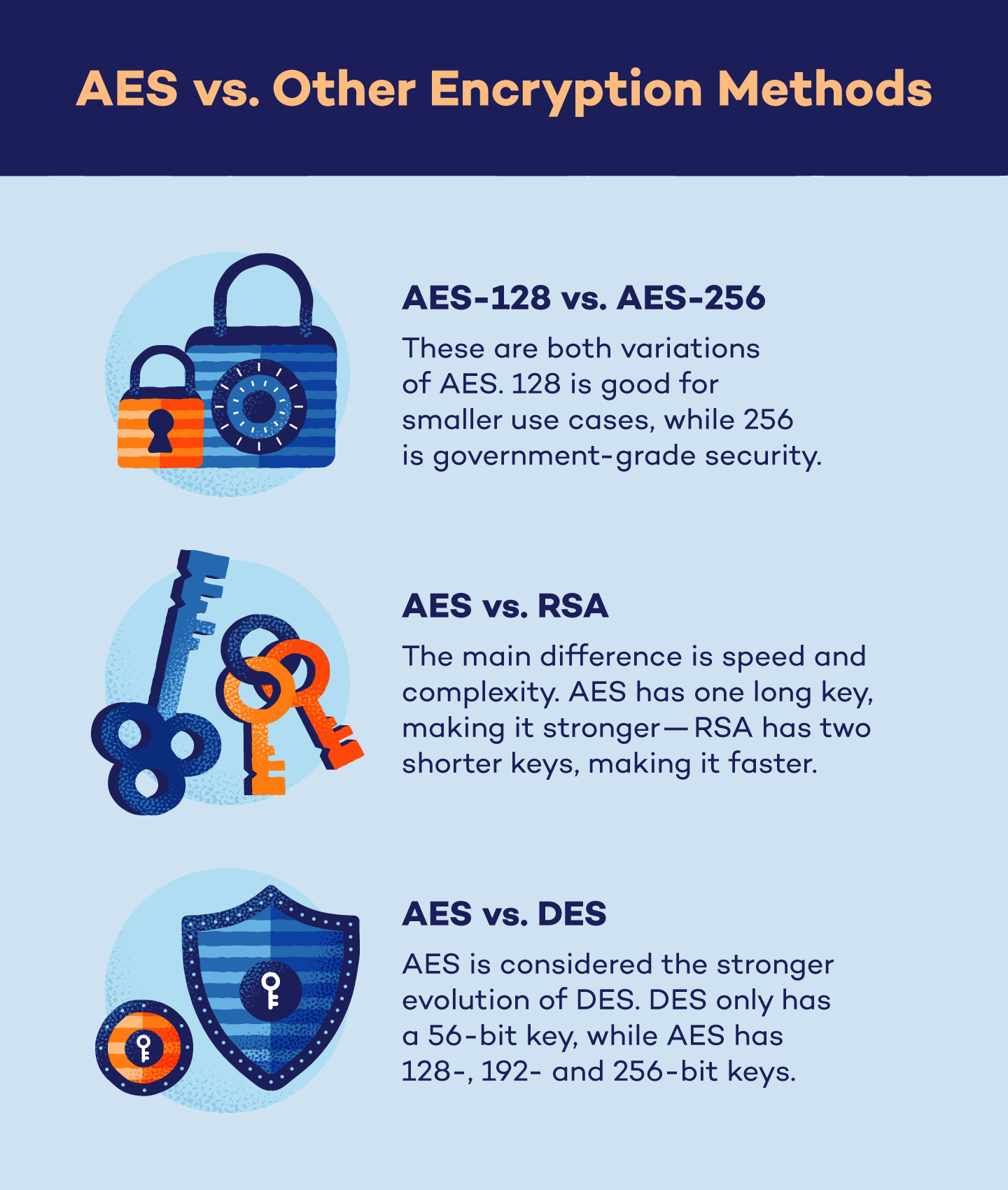
AES-128 vs. AES-256
AES-128 and AES-256 may seem like two different systems, but they are simply two variations of the same encryption method.
AES-128 involves a 128-bit key length in which data goes through 10 rounds of encryption. While this method is extremely secure against brute force attacks, it has the lowest security specs of all AES variations.
AES-256 involves a 256-bit key length in which data goes through 14 rounds of encryption, and has the highest security specs of all AES variations. 256 is slowly being adopted into everyday use due to continuous advancements in technology.
AES vs. RSA
RSA, or Rivest, Shamir and Adleman, is a type of encryption that uses an asymmetric algorithm to encrypt and decrypt data. This method can be paired with other encryption methods such as PGP encryption to generate a pair of related keys — otherwise known as public and private keys.
While both algorithms are secure, the main difference between AES and RSA comes down to speed and complexity.
Since AES uses the same key to encrypt and decrypt data, it is more user-friendly, cheaper and more secure against brute force attacks due to the length of the password. RSA, on the other hand, is faster in processing data because the length of the keys are shorter.
Despite their differences, both AES and RSA are reliable methods to encrypt and secure data.
AES vs. DES
DES, or data encryption standard, is the now-outdated encryption method used by government agencies starting in the 1970s.
DES and AES are similar in functionality, but the difference is simply that AES is more efficient and secure. While DES uses a 56-bit key, AES uses 128-, 192-, and 256-bit keys which results in increased security. AES is also faster than DES, resulting in quicker encryption.
Overall, AES has replaced DES in nearly every capacity.
AES Encryption FAQ
Finally, we will wrap up with a few frequently asked questions about AES encryption.
Is AES Symmetric or Asymmetric?
AES is classified as a symmetric encryption algorithm. This means that the same secret key is used for both encrypting and decrypting data. This symmetric approach offers advantages in terms of speed and efficiency, especially when dealing with large data volumes. However, it also necessitates careful key management. Anyone who possesses the secret key can decrypt the data, making it crucial to keep the key secure.
What Is AES 128 vs. 192 vs. 256?
AES 128, 192 and 256 are all variations of the same algorithm, but the difference lies in the key length and rounds of encryption.
AES-128 uses a 128-bit key length for encryption and decryption, which results in 10 rounds of encryption; AES-192 uses a 192-bit key length for encryption and decryption, which results in 12 rounds of encryption; and AES-256 uses a 256-bit key length for encryption and decryption, which results in 14 rounds of encryption.
Is 128-Bit AES Secure?
Yes, 128-bit AES is secure. In fact, if using brute force methods, it would take 1 billion billion years to crack.
Is AES Free to Use?
Yes, AES is free to use. It was originally developed to be released on a royalty-free basis.
Is AES the Best Encryption Method?
The best encryption method for you depends on what’s important for your situation. That said, AES is one of the leading encryption methods on the market, trusted by the National Institute of Standards and Technology since 2002.
Panda Security Can Help With Encryption
AES encryption is an extremely secure and user-friendly algorithm that can protect your most sensitive data. Found in a number of everyday applications, this method is the go-to for defending sensitive data against brute force attacks.
If you want the power of AES encryption in your everyday cyber activity, enlist the help of Panda’s VPN and password manager services to expertly secure your data against cyberthreats.