Since two-factor authentication (2FA) came into our lives, many heads of cybersecurity in large companies have managed to breathe a sigh of relief: finally, here was a security measure that was available to every employee in the company, one that could face up to hackers.
However, we shouldn’t see it as a silver bullet: having employees access online services using not only a password but also a message or code received via SMS is a great breakthrough for security, but by no means does it mean that our job here is done and we can now put our feet up.
Here’s how two-factor authentication can be bypassed
The bad news was brought to light not long ago by Kevin Mitnick, Chief Hacking Officer (CHO) at KnowBe4. The security consultant and former hacker found that if an attacker wants to bypass the cybersecurity of an employee who isn’t an expert in these matters, in fact, it isn’t so hard. A little social engineering to show the employee some fake credentials was enough to get their data.
Mitnick showed that, using a link to a real looking domain spelled slightly wrong (faceboook.com, Linkedln – with ‘L’ instead of capital ‘i’– and so on), he could show a fake login page and steal the person in question’s sensitive data. With this data, getting around two-factor authentication is pretty much child’s play.
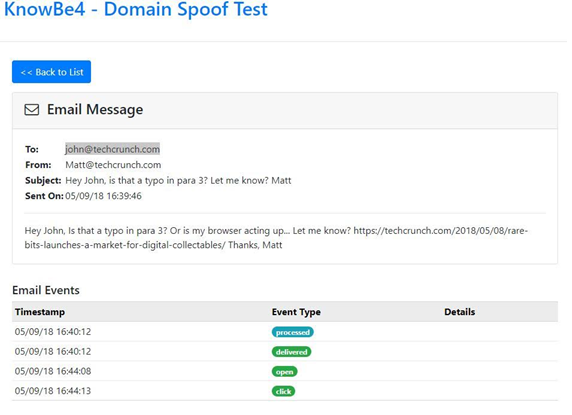
To prove this, Mitnick tested it out on a TechCrunch writer, to whom he sent an email containing a fake link. With this link, he managed to get hold of the writer’s data.
This may seem like a one-off, but it is far from being an isolated case. Tools like Evilginx make this task much, much simpler, which brings us to an obvious conclusion: two-factor authentication is undeniably a step in the right direction for corporate cybersecurity, but it is far from being foolproof.
How to keep this from happening in your company
If you’re worried that part of your company could fall for this type of phishing scam, there are several thing you can do about it, as well as several tips that every member of staff can follow.
1.- Don’t rely on an SMS
Most of the time, two-factor authentication tends to rely on an SMS being sent to a user so that they can sign in. But in this case, thieves could gain access to this SMS. To combat this, you could opt for other two-factor authentication methods, so that the second alert has to appear on the user’s physical device or their operating system. An example of this is verification via Google Authenticator.
2.- Dynamic or one time passwords
Remembering a password can be pretty tedious for your employees, but at the same time, never changing passwords can become a real cybersecurity problem for the whole company. In these cases we can fall back on One-time password algorithm technology, which gives us a password that is valid for just one login. What’s more, it’s not a static password, but a dynamic one. This means that a one-off breach won’t jeopardize login cybersecurity forever.
3.- Be suspicious and ask questions
This advice may seem obvious, but it’s also the most important for your company’s employees: they have to be extremely wary when it comes to entering their login details anywhere. If they have any doubts or suspicions, they should get in touch with someone in charge of cybersecurity straight away. Better safe than sorry.
4.- Communication protocol
The TechCrunch writer had his two-factor authentication broken because he got an email telling him about a typo. It’s always going to be complicated to anticipate threats of this type, but some protocols can help avoid them. For example, if your company makes it a rule that no one in top management can ask an employee for certain confidential information over a simple email, you’ll be able to avoid future upsets like the famous CEO scam.
On the rare occasion that these measures aren’t enough to stop an attacker from breaching the two-factor authentication system, it’s important to have advanced cybersecurity solutions such as Panda Adaptive Defense, which allows continuous and immediate response to cybercriminals.






1 comment
Well, 2-Factor authentication was seemed to be much more secure than every other method out there. Even I was using this on many of my accounts, now I need to think twice before using it.