Hackers can exploit phishing links, malicious apps, unsecured Wi-Fi hotspots or zero-day software flaws to infiltrate your iPhone and steal your data.
Avoid this by:
- Disconnecting and powering off your device
- Removing external components
- Accessing your Apple ID
- Enabling two-factor authentication
- Checking your iPhone settings
- Contacting your service provider
- Updating your phone regularly
- Using a reliable VPN
You might think your iPhone is a digital fortress, but even the best walls can have cracks. And if you’re wondering, “Can someone hack my iPhone?,” the answer is yes. Hackers use tricks like fake Wi-Fi hotspots and phishing texts to sneak in and steal your data.
Learn how attacks happen and why iPhones aren’t invincible. We’ll also share eight simple fixes for how to secure your iPhone from hackers, so you can keep your data safe.
3 Common Security Myths About iPhones
Many people believe iPhones are immune to malware because of Apple’s strict controls, but that’s not exactly true. Here are the three most common iPhone myths that might be putting your data at risk:
1. iPhone Apps Can’t Have Viruses
If you think any app from Apple’s App Store is virus-free, think again. In 2015, the XcodeGhost incident showed that malicious code can slip past review and infect real apps.
Tip: Before you tap “Get,” check app reviews, download counts, developer info and required permissions.
2. iPhones Can’t Get Viruses
It’s true that iOS’ walled-garden design makes virus attacks rarer. Yet, scareware and malware campaigns still target iOS users — clicking a fake link or installing a dodgy profile can let threats in. This means that even iPhones can get viruses.
Tip: Never click links from unknown senders and only install software from trusted sources.
3. Only Jailbroken iPhones Can Get Hacked
Jailbreaking does lower your defenses, but you don’t need to break free of Apple’s rules to be at risk. Phishing texts, unsecured Wi-Fi hotspots and unpatched zero-day flaws can compromise even stock iPhones. Jailbroken iPhones usually need an antivirus to strengthen their security.
Tip: Keep iOS up-to-date, use a strong passcode and avoid public Wi-Fi without a VPN.
Can iPhones Be Hacked?
iPhones are more secure than Androids, but attackers can still hack iPhones. Android devices have a reputation for customization and manipulation at the software level since their open-source code makes them much less secure and easier to compromise via different types of malware. iPhones, on the other hand, are closed-source, making them far more challenging to compromise.
Despite their superior security features, iPhones are still susceptible to:
- Unsecured Wi-Fi network traps
- Suspicious apps and social engineering schemes
- Security vulnerabilities the iOS can’t prevent
- Getting your Apple ID stolen and used
From there, the hacker can access all data on your iPhone, including cloud storage, pictures, messages and sensitive financial and personal information.

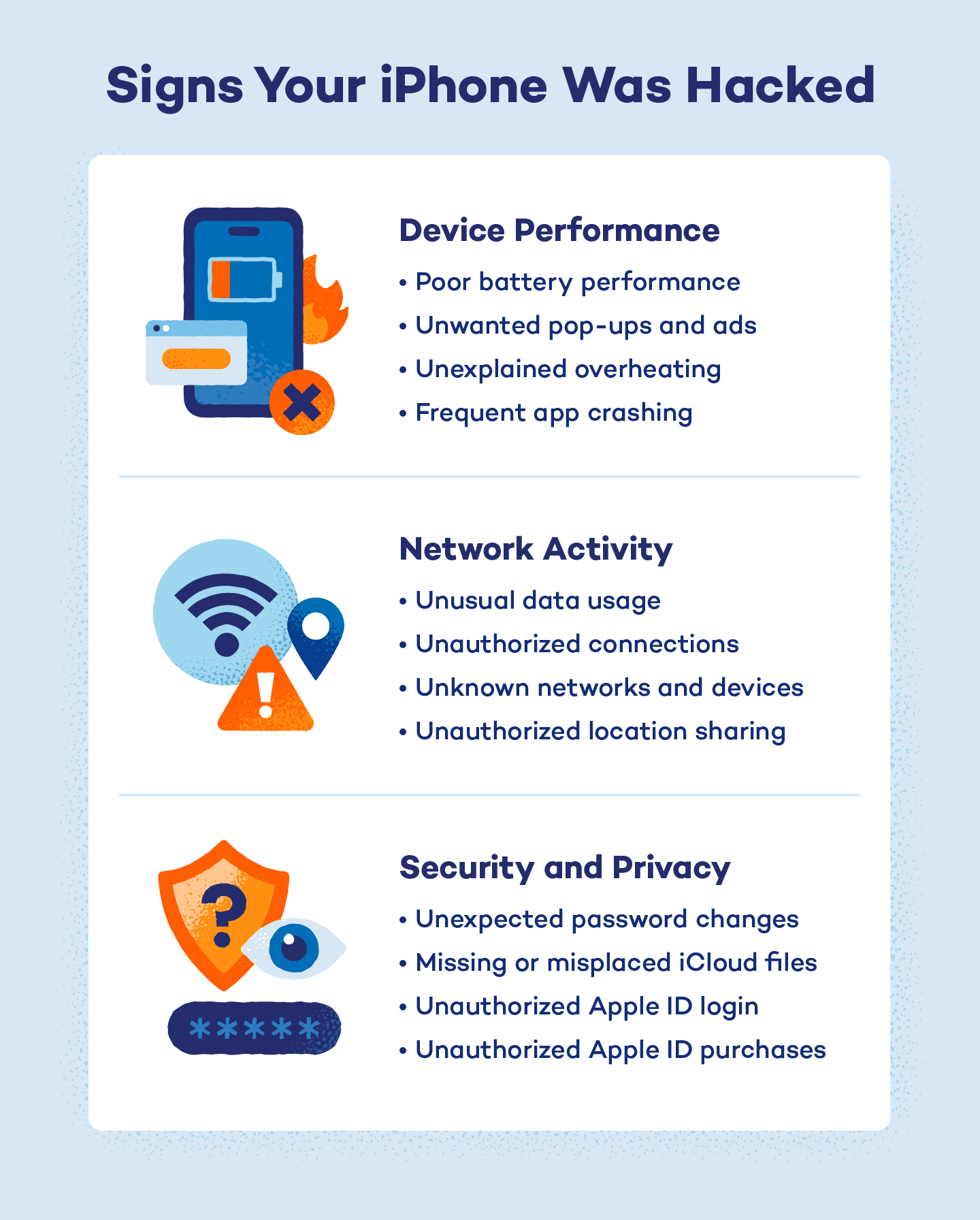
How to Tell If Your iPhone Is Hacked
No one knows your iPhone better than you. If you notice your device behaving in strange and unusual ways, your iPhone may have been hacked. Here’s how to know if your iPhone is hacked.
Device Performance
Malware can slow your iPhone, drain its battery quickly and even make it overheat when you’re barely using it. You might also see unexplained pop-ups or ads in your browser or notice apps crashing more often than normal. Some of these issues can be chalked up to an older device or a worn-out battery. But if your iPhone is in good shape and still underperforms, unwanted software might be at work.
Tip: Check your battery health in Settings > Battery, clear website data in Safari’s settings to banish pop-ups and restart your phone in Safe Mode (hold Power and Volume Up) to see if performance improves. This can help you isolate and remove any malicious apps.
Network Activity
Malware often talks behind your back, sending and receiving data without you knowing. You might see sudden spikes in data usage or notice your iPhone auto-connecting to unfamiliar Wi-Fi or Bluetooth devices. These sneaky connections can mean someone’s siphoning your info or controlling your phone remotely.
Tip: Go to Settings > Mobile Service > Usage to spot unusual data use, disable “Auto-Join” for unknown networks in Wi-Fi settings and use a trusted VPN to encrypt your traffic and block hidden connections. In some iPhone models, the steps might be a bit different. Look for anything related to “mobile data or cellular” under Settings.
Security and Privacy
Malware can sneak into your Apple ID and mess with your security settings, locking you out or changing your passwords without warning. You might also spot strange iCloud activity — files moved, deleted or accounts suddenly locked — that you didn’t initiate. These are clear iPhone hacked signs, indicating that someone’s trying to control your device or hijack your data.
Tip: Turn on two-factor authentication (2FA) in Settings > [your name] > Sign-In & Security, review your account’s device list regularly and sign out of any unfamiliar sessions in appleid.apple.com to keep unwanted guests at bay.
Unknown Apps
If you spot apps on your home screen that you didn’t install, it could be spyware silently stealing your data. Hackers often disguise malicious software under ordinary names so it blends in with legitimate apps.
Tip: Regularly review your installed apps in Settings > General > iPhone Storage and delete any you don’t recognize.
Strange Messages From Your Number
If friends ask why they got weird texts or emails from you, hackers may have taken over your messaging app to send scams or phishing links. Malware can hijack your number and blast out harmful links to everyone in your contacts list.
Tip: Block and report any suspicious messages, then change your Apple ID password immediately to stop further misuse.
Locked Out of Apple ID
If you suddenly can’t sign in and see alerts that your Apple ID is locked or disabled, someone may have gained control of your account. Hackers often change your password or security questions, so you lose access and they can roam freely.
Tip: Go to iforgot.apple.com to reset your password and contact Apple Support if you still can’t regain access.
8 Tips if Your iPhone Was Hacked
If you think your iPhone or Apple ID has been compromised, remember that you have a short amount of time to secure your account before you’re locked out or your data is stolen. Here’s what to do if your iPhone is hacked:
- Disconnect and power off your device: Turn off your Wi-Fi, Bluetooth and cellular data. Then, disconnect the iPhone from any accessories or wired connections and power it down.
- Remove external components: Take out your SIM card and any external storage or charging devices.
- Access your Apple ID: Use another device to access your Apple ID account. Then, reset your Apple ID password and check for any unknown connections. Immediately change passwords for all accounts linked to the device. Use strong passwords.
- Enable two-factor authentication: Add an extra layer of security with 2FA to your accounts where possible.
- Check your iPhone settings: Check the settings for services or apps you’re signed in to with your Apple ID. To do this, open the Settings app on your iPhone. Tap your name and verify the email address associated with your Apple ID.
- Contact your service provider: Inform your cellular service provider about the hacking incident and verify if there were any purchases or suspicious charges on your service provider’s app.
- Update your phone: Install the newest iOS update in Settings > General > Software Update to patch any security flaws attackers might exploit. Running outdated software is one of the fastest ways to get into your phone.
- Use a reliable VPN: Secure your online activity on all devices by using a reliable virtual private network service and browse the internet safely while protecting your personal information.
How VPNs Can Protect Your iPhone
Even with Apple’s built-in defenses, public Wi-Fi and phishing sites can still expose your data. A reliable VPN service can help you avoid getting your phone hacked and make it hard for hackers to track it.
Panda Dome VPN encrypts every bit of traffic and masks your IP so snoopers and hackers can’t track or intercept your online activity. With one-tap connections, a strict no-logs policy and lightning-fast servers, it turns any network into a private tunnel. Download Panda Dome for free from the App Store or upgrade to a premium version today and browse safely.
iPhone Hacking FAQ
Learn how iPhones can be compromised to keep your personal information from being stolen and used.
What Are the Signs My iPhone Has Been Hacked?
Look for sudden battery drain, sluggish performance, unexpected data spikes or apps you never installed. These often mean malware is running in the background. You might also see constant pop-ups or ads, frequent crashes or overheating when the phone is barely in use.
Are iPhones Safer Than Androids?
Yes — iOS’ closed ecosystem and strict App Store review process make iPhones less prone to malware than Android devices, which allow side-loading and have a larger attack surface. That said, both platforms rely on you to keep software updated, download only from official stores and use strong passwords.
How Can You Tell if Someone Is Remotely Accessing Your iPhone?
Watch for sudden password or setting changes you didn’t make, like two-factor prompts for no reason. Also, check Settings > Privacy & Security > Location Services > Share My Location for unknown devices sharing your location. Unfamiliar outbound texts or spikes in data usage can be further clues that someone’s tapping into your phone.