Most of the news about attacks that use basic Internet protocols focuses on the World Wide Web. This means that HTTP and DNS are usually the key players, and as such, many policies, and a lot of the cybersecurity software in use, are mainly focused on these protocols. However, there are also risks related to other protocols that can also be used by cybercriminals as attack vectors. These protocols are BGP, NTP and FTP. All three can mean real risks for a company’s information, and at times they don’t receive the attention they deserve given the potential threat that they can pose. Below, we’ll look into what each of them implies and how cyberattackers can use them.
BGP
The Border Gateway Protocol is used to exchange routing information between autonomous systems – that is, those groups of IP networks that have their own, independent policies. Essentially, it is a protocol used by large nodes on the Internet to communicate between themselves and convey a large quantity of information between points on the network. For this reason, one of the risks related to this protocol is that, for the vast majority of users, it is very complex, and companies only start to work directly with this protocol when they have their own large scale networks.
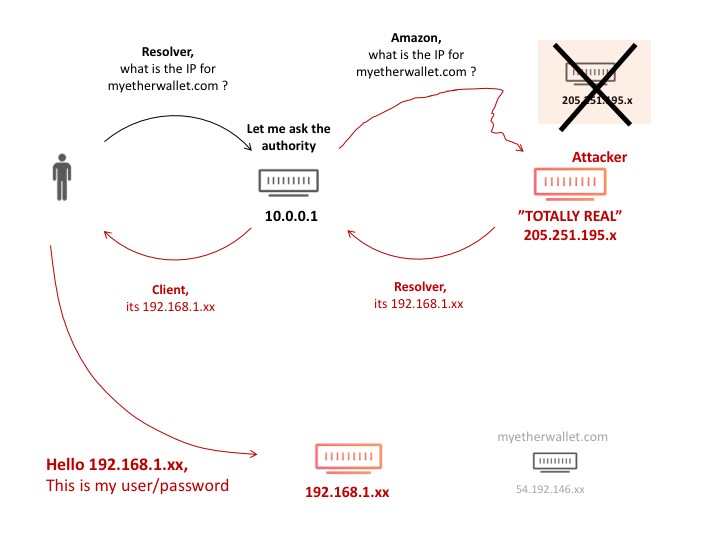
An example of an attack using this protocol was the leaking of information from cryptocurrency wallets, as the provider Cloudflare explained. In general, the cyberattacker manages to “trick” the network into redirecting companies’ or users’ IP prefixes, and when the network responds in order to send information, this information is leaked to the cyberattacker.
NTP
The Network Time Protocol (NTP) is mainly used to synchronize clocks on the computers on a network. However, older versions of the protocol on some networks also have a monitoring service that allows administrators to compile a list of the 600 hosts that have connected to the server, via a command called Monlist. The cyberattackers leverage this feature by carrying out a “reflex attack”: they send a package with a false IP address, through which they obtain the list from the Monlist command. Afterwards, they amplify it by carrying out a denial of service attack (DDoS) that can leave the connection of all addresses of the hosts on the list temporarily out of action.
FTP
Although HTTP is used more and more often to send files, the old file transfer protocol (FTP) is still present on many systems and in many companies. Given that it wasn’t originally designed to be a secure transfer protocol, it has many vulnerabilities that attackers can take advantage of. This is exactly what happened last year. The FBI warned of an attack on FTP servers belonging to hospitals and dental clinics that aimed to access patients’ medical records by exploiting a vulnerability that uses an anonymous mode of FTP: older FTP servers can be accessed with a common user name such as “anonymous” or “ftp”, with no need to introduce a password or user name.
How to avoid attacks via these protocols
As we commented before, these protocols are less common for cyberattackers than HTTP, but that doesn’t mean that they’re going to stop posing a risk to companies. This is why organizations must follow certain general guidelines to prevent attacks that use them.
- Adoption of MANRS: The MANRS (Mutually Agreed Norms for Routing Security) are a joint initiative created by network operators and Internet exchange points (IXPs) with the aim of developing stronger routing security to avoid, among other things, BGP attacks. Any large company that has broad control over its networks and nodes should adopt them.
- Updating networks and their protocols: the most common attacks over NTP protocols happen because outdated versions are being used. The same thing happens with FTP, since it is a primitive protocol that, by default, wasn’t designed with encryption for the exchange of files (for this, there are encrypted modes: FTPS). IT teams in companies should use the most up-to-date versions of these protocols in order to avoid potential cyberattacks.
- Correct configuration of servers An incorrectly configured FTP can allow cyberattackers a way in if they connect in anonymous mode. A configuration of the FTP server that requires a secure password is already a more complex barrier for the attacker. In the same way, the NTP protocol can leave its list of hosts exposed if it doesn’t have its accesses correctly configured.
- Advanced cybersecurity solutions: as well as all the above, it is vital that companies of any size have an advanced cybersecurity solution active on all endpoints – one that is able to prevent, detect, and neutralize attacks at all times.






2 comments
Thanks for telling us about this risk.
Thanks for telling about these protocols risks.