Bots are automated programs that perform tasks online without human intervention. Bots can be helpful, like customer service tools, or harmful, like those that spread spam or steal data.
With so much of our lives happening online, it’s easy to wonder how websites, apps and services seem to work so seamlessly, even without human intervention. Have you ever questioned whether you’re chatting with a real person while receiving instant responses to your queries in a matter of seconds? These experiences are often powered by bots. But what is a bot, exactly?
Website bots are automated programs designed to perform tasks online, sometimes without you even noticing. Learn how bots affect your data privacy and what you can do to protect yourself from the bad ones. We’ll also talk about the different types of bots, how they operate and the roles they play.
What Is a Bot?
A bot is a software application that carries out tasks automatically over the internet. These tasks can range from simple, like answering common customer service questions, to more complex functions, like scanning entire websites to index their content for search engines.
Think of bots as digital assistants that can work much faster and more efficiently than a human could, often without needing any supervision. Bots operate based on a set of programmed instructions, making them ideal for repetitive or time-consuming tasks.
However, not all bots are used for helpful purposes. While some bots, like those used in customer service or website management, streamline online interactions, others are designed with malicious intent. For instance, automated bots are often used in phishing attacks. These bots send fraudulent emails or messages that trick you into sharing sensitive information, like passwords or credit card details.
How Do Bots Work?
Bots are created using programming languages like Python, Java or JavaScript, allowing developers to write code that instructs the bot on what tasks to perform and how to perform them.
- Bots operate through bot automation — they execute tasks automatically based on predefined rules or algorithms.
- Once deployed, bots can perform a wide range of functions, from gathering data to interacting with users in real time.
- They can work autonomously, without the need for human intervention, and are often used in large-scale operations like processing search engine queries or running social media accounts.
Again, not all bots are built for positive purposes. Some are designed as malware, carrying out harmful activities like spreading viruses, launching distributed denial-of-service (DDoS) attacks or stealing personal data.
To counter malicious bots, websites often use tools like CAPTCHA to distinguish between human users and bots, preventing automated programs from accessing certain features or exploiting vulnerabilities. These defenses help ensure that harmful bots can’t easily infiltrate systems or gather information without detection.
Types of Bots
Bots can either be helpful tools that make your online experience smoother or harmful programs that cause problems. Some bots help you get things done faster, like keeping websites up-to-date or assisting with customer service, while others are created to spread spam or steal personal information.
For example, news apps use bots to bring you the latest updates, and services like Spotify use them to suggest new music. However, some bots can be harmful, like those used in DNS attacks to disrupt websites.
Let’s explore the different types of bots — the ones that help and the ones you should watch out for.
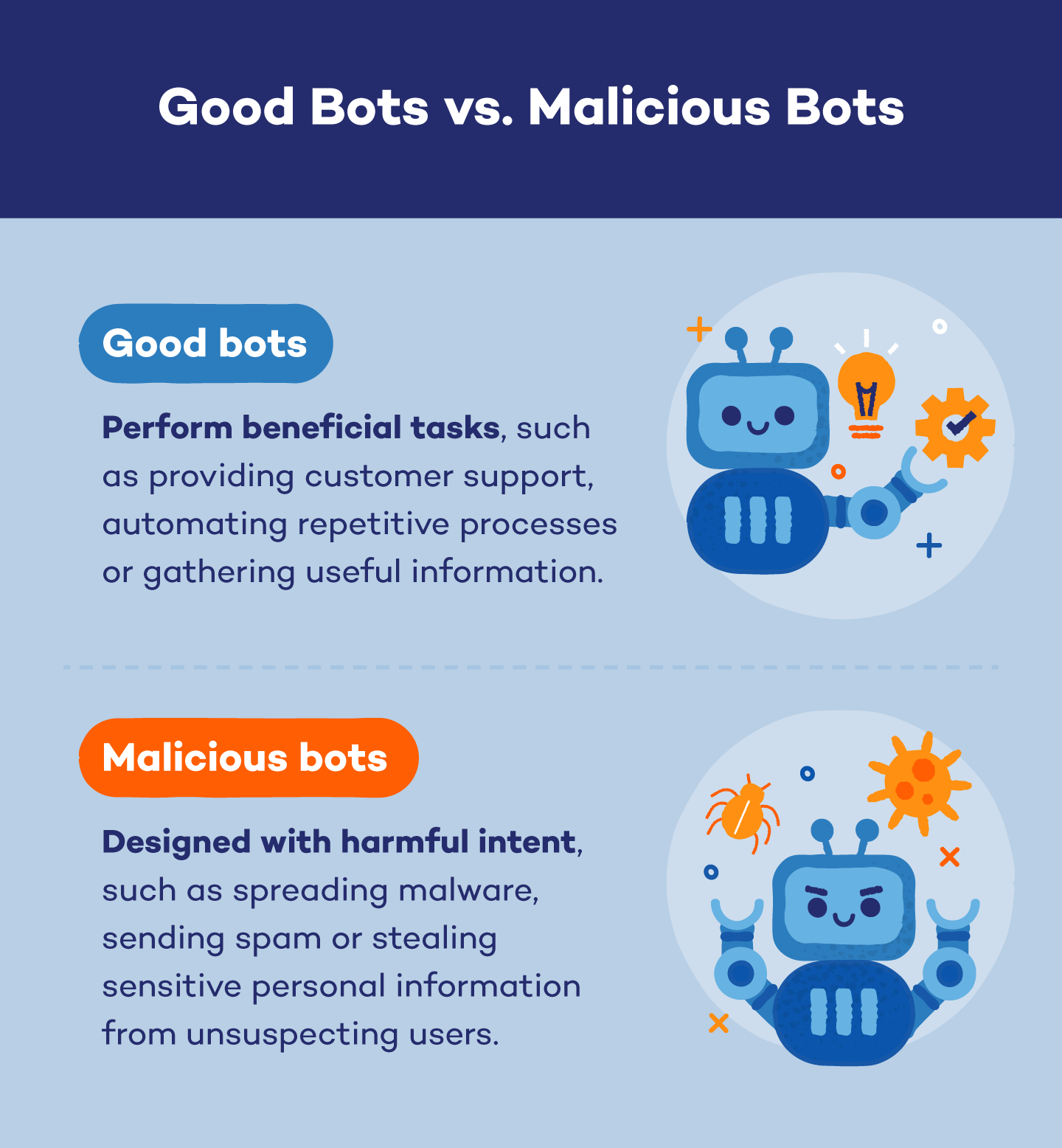
Good Bots
Good bots work behind the scenes to make your online experience better. They include:
- Customer service bots: These bots chat with you online, answering your questions quickly, day or night.
- Search engine bots: These bots scan the internet to help search engines like Google find and rank websites.
- Chatbots: Found on many websites, chatbots help guide you through tasks, like placing an order or finding information.
- Scraper bots: These bots collect information from websites, like prices, so you can compare them.
- Web crawlers: Similar to search engine bots, web crawlers browse the internet to keep websites up-to-date in search results.
- Monitoring bots: These bots check websites to ensure they’re working properly and alert users when something goes wrong.
- Transaction bots: They automate things like processing payments or orders online.
Malicious Bots
Malicious bots are the ones you need to be careful of. They’re built to cause trouble online and can include:
- Spam bots: These bots send unwanted messages or comments, often promoting scams.
- Denial-of-service (DoS) bots: DoS bots flood websites with traffic, causing them to crash and go offline.
- Download bots: They fake downloads to make apps or files seem more popular than they really are.
- Ticketing bots: These bots buy event tickets quickly, reselling them at higher prices. Now you know why it’s so hard to get your hands on those concert tickets!
- Click fraud bots: They click on online ads to drain advertising budgets or generate fake revenue.
- Social media bots: These bots create fake accounts or spread misinformation online.
- Credential stuffing bots: These bots use stolen usernames and passwords to break into your accounts.
- Malware bots: These bots infect computers with viruses or other harmful software.
- Botnet: Botnets are large groups of infected computers controlled remotely, often used to spread malware or launch widespread attacks.
How to Detect Malicious Bots
Malicious bots can sneak onto your devices without you even realizing it, but there are signs you can watch out for to stay protected. These bots often cause unusual behaviors that may indicate your system is compromised.
Knowing what to look for can help you detect these threats early and take steps like malware removal to safeguard your data.
- Unexpected messages or emails: If you receive strange emails or messages from unknown senders, it could be a bot trying to trick you into clicking malicious links.
- Abnormal account activity: Keep an eye on your accounts — sudden changes, logins from unfamiliar locations or unauthorized transactions may indicate a bot is at work.
- Unfamiliar apps or software: If new apps appear on your device that you didn’t install, it’s a sign that malicious bots may have slipped unwanted software onto your system.
- Slow device: Bots running in the background can consume system resources, causing your device to run noticeably slower than usual.
- High network usage: If your internet usage spikes unexpectedly, it could be a bot using your connection to send out spam or carry out attacks.
- Redirects: If your browser frequently redirects you to strange or unwanted websites, a malicious bot may be hijacking your browsing activity.
- Pop-ups: Frequent or unexpected pop-ups can be a sign that a bot has infected your device and is trying to push ads or malicious content.
- Unusual error messages: If your device starts showing unfamiliar error messages, especially when using everyday apps, it could be a sign that malware or bots have infiltrated your system.
How to Prevent Malicious Bot Activity

Protecting yourself from malicious bot activity is essential to keep your devices and personal information secure. Luckily, there are effective strategies you can use to prevent these attacks from happening in the first place.
Use Reputable Anti-Malware Software
Installing an effective anti-malware program is one of the best ways to defend against malicious bots. Anti-malware software can detect, block and remove bots before they cause harm to your system. Make sure to keep your software updated to catch the latest threats.
Install a Bot Manager
Bot managers are specialized tools that help identify and control the flow of automated traffic. Installing a bot manager helps block suspicious or malicious bot activity while allowing helpful bots (like those from search engines) to function as intended. This is particularly useful for preventing automated attacks on your system.
Use Strong Passwords
Bots often use credential stuffing to guess weak passwords and break into accounts. By using strong, unique passwords that combine letters, numbers and symbols, you can significantly reduce the risk of bots gaining unauthorized access to your accounts. Consider using a password manager to create and store complex passwords securely.
Enable a Firewall
A firewall is like a security guard for your internet connection. It filters incoming and outgoing traffic, blocking potentially harmful bots from accessing your devices. Ensure your firewall is turned on and properly configured to provide an extra layer of protection against malicious bots trying to exploit vulnerabilities.
Be Cautious With Downloads
Malicious bots can enter your system through unsafe downloads. Avoid downloading software, apps or files from unverified websites or unfamiliar sources. Always check reviews, certifications and publisher details to ensure the download is legitimate and free from malware or bot programs.
Be Wary of Phishing Attempts
Phishing scams are a common way for malicious bots to access your device. To prevent phishing attacks, be careful when dealing with unexpected emails, text messages or pop-ups. Never click on suspicious links or download attachments from unknown sources. Always verify the legitimacy of the sender before sharing any personal information.
Educate Yourself About Online Security
Staying informed about the latest security threats is key to staying protected. Regularly learning about new methods hackers and bots use can help you avoid traps. Following basic online safety practices, such as recognizing phishing emails and avoiding risky downloads, can go a long way in preventing bot-related attacks.
Start Browsing With Confidence
Now that you know what a bot is and how to identify and prevent malicious bots, you can browse the internet with greater peace of mind. Implementing the strategies above can help protect your personal information and enhance your online security. For added safety, consider using Panda Dome antivirus software to keep your devices secure from potential threats.