We don’t know if you’ve heard of the new Ransomware which is called ‘Locky’…
It works as follows:
- It arrives by mail and the attachment is a Word document with macros.
- Upon opening the document the macros infects the computer.
- It deletes any security copies that Windows has made and starts to encrypt the files.
- Once finished, it opens a file called “_Locky_recover_instructions.txt” in the notepad.
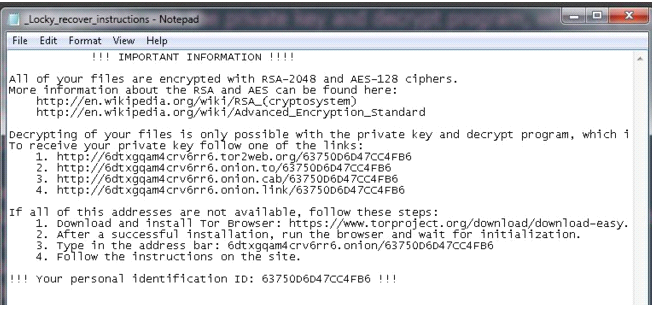
In fact, if we suspect that we have been attacked by Locky we can look for one of these files in our computer – if they’re there, then we know Locky has paid us a visit:
- “_Locky_recover_instructions.txt”
- “_Locky_recover_instructions.bmp”
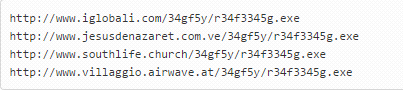
When the Word document that started the infection is opened, it downloads Locky, and what we have seen is that in all cases the malware comes from a legal website which has been compromised. It is there that the malware is stored. These are some of the URLs hosting malware:
The email that it comes attached in is the following:
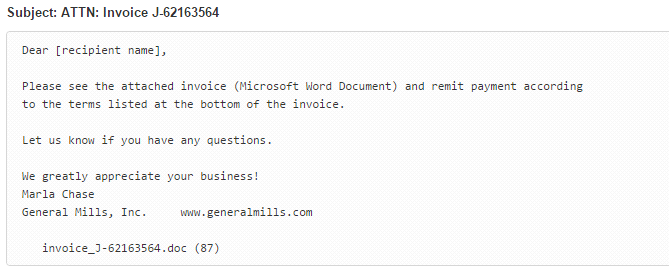
In this case, the attached Word is called invoice_J-67870889.doc
Some of the variants that we have seen used PowerShell to carry out the downloading and running of Locky from the macro, with the rest of it being the same.






4 comments
Hi,
Is it true that the only available solution to preventing from infection is Panda Adaptive Defense? if so please let us know how it works and how will secure us against ransomware.
“Cryptolocker” was an encrypting ransomware in it’s own right, and probably the one which kicked off the current trend. Rather than the term “”cryptoware” which seems to be the generally accepted term , you seem to use Cryptolocker as the generic term for encrypting ransomware. I think this is confusing and on the whole unhelpful.
Hi Gordon,
You’re right! Sorry for the confusion. We have updated the post.
Have a great day.