Imagine opening your inbox and not being bombarded by a tidal wave of unwanted emails. Sounds like a dream, right? Unfortunately, for most of us, spam emails are a daily nuisance, ranging from mildly irritating to downright dangerous. They clutter our inboxes, peddle dubious products and, worse, can harbor malware designed to steal your personal data.
But fear not! You can reclaim your inbox and banish those digital pests. Let’s dive right into the actionable steps on how to stop spam emails and regain control.
1. Report Spam Emails
Simply deleting spam emails doesn’t stop them from flooding your inbox. You need to actively report spam to strengthen your email provider’s spam filters and reduce future unwanted messages. This moves the emails to your spam folder and helps your email client better identify and block similar emails. Here’s how:
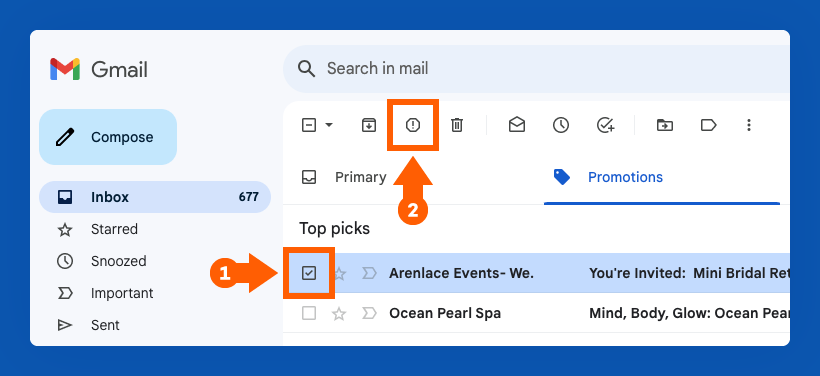
How to Report Spam in Gmail
To report an email as spam in Gmail:
- Select the email(s) you want to report as spam by checking the box next to it or opening a specific email.
- Click the Report spam button. It looks like an exclamation mark within a stop sign shape and is located at the top of the page next to the Archive and Delete buttons.
Once you do this, the selected emails will be sent to your spam folder, and you shouldn’t receive emails from those senders in the future.
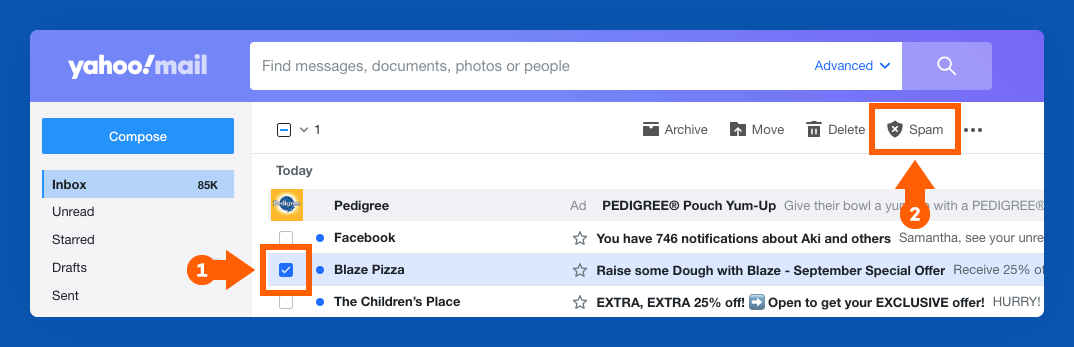
How to Report Spam in Yahoo Mail
To report an email as spam in Yahoo Mail:
1. Select the email(s) you want to report as spam by checking the box next to it or clicking into a specific email.
2. Click the icon with an “X” labeled Mark as Spam in the toolbar at the top of your inbox, next to the Delete button.
How to Report Spam in Apple Mail
To report an email as spam in Apple Mail:
1. Select the email you want to report as spam.
2. Click the Junk button at the top of your toolbar. It looks like a container with an “X” inside, and it’s located next to the Trash button.
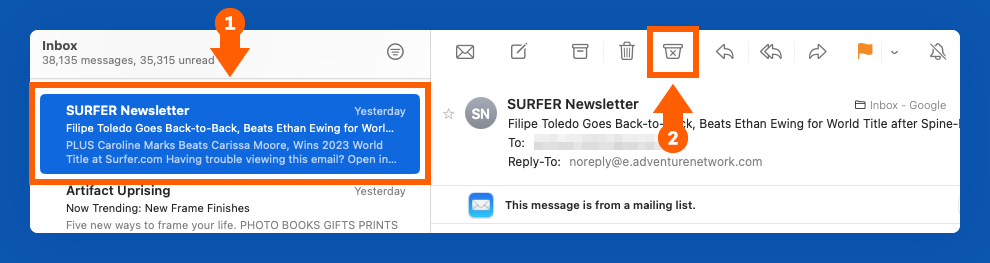
3. You can also drag the message to the Junk folder on the left sidebar.
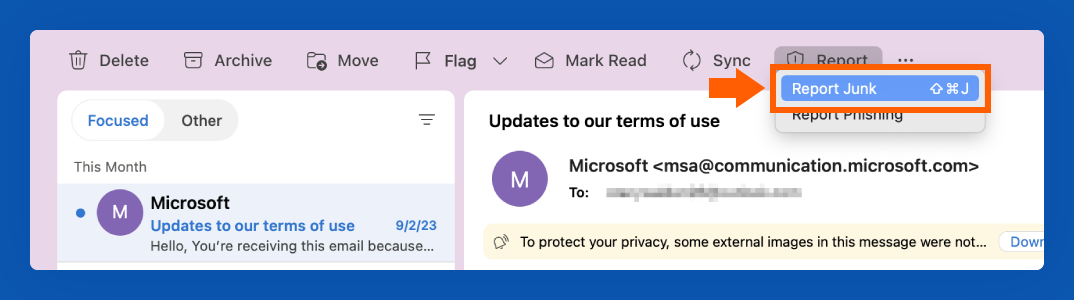
How to Report Spam in Outlook
To report an email as spam in Outlook:
1. Click the email you want to report as spam.
2. In the top ribbon, click “Report.”
3. Choose “Report Junk.”
2. Block Spam Email Addresses
If you’ve followed the steps above to report an email as spam but find you’re still receiving emails from certain senders, you can block them from ever reaching your inbox.
How to Block Spam in Gmail
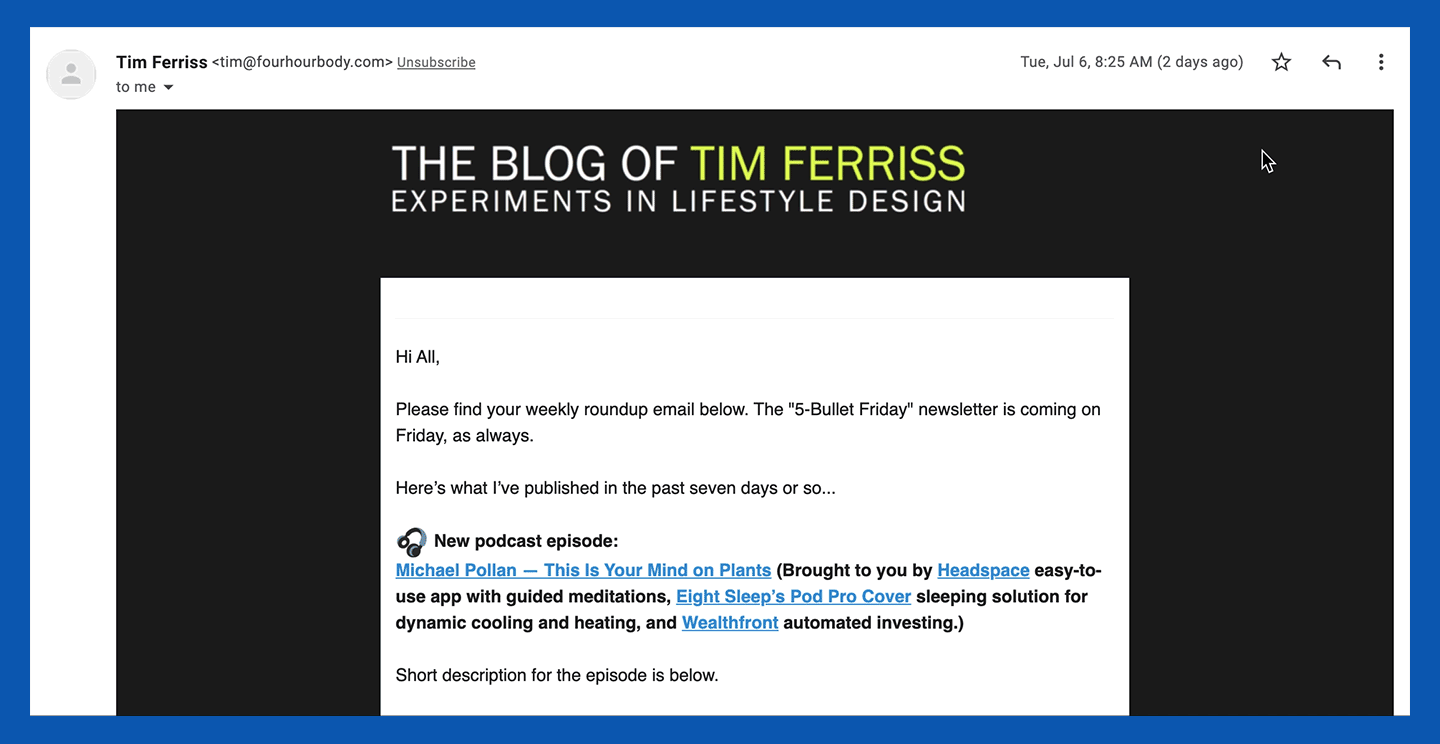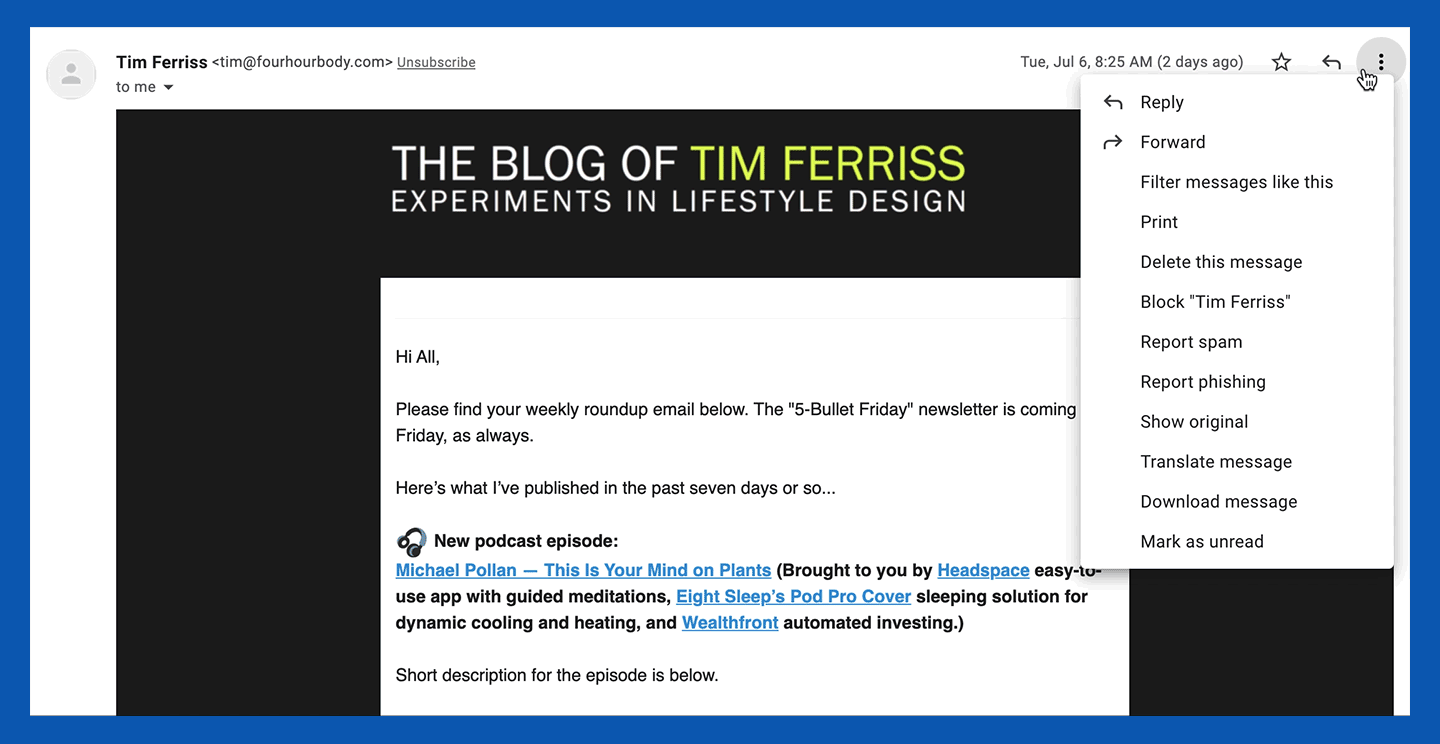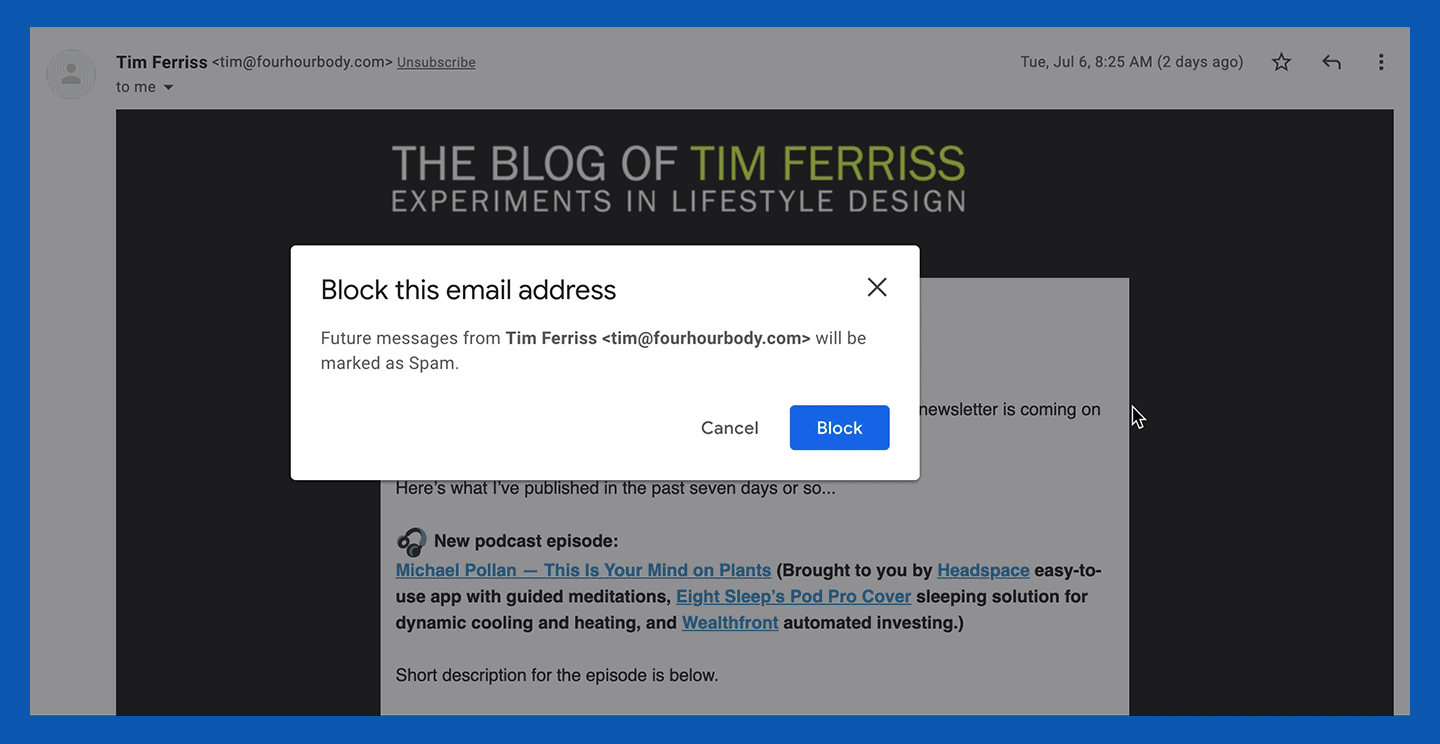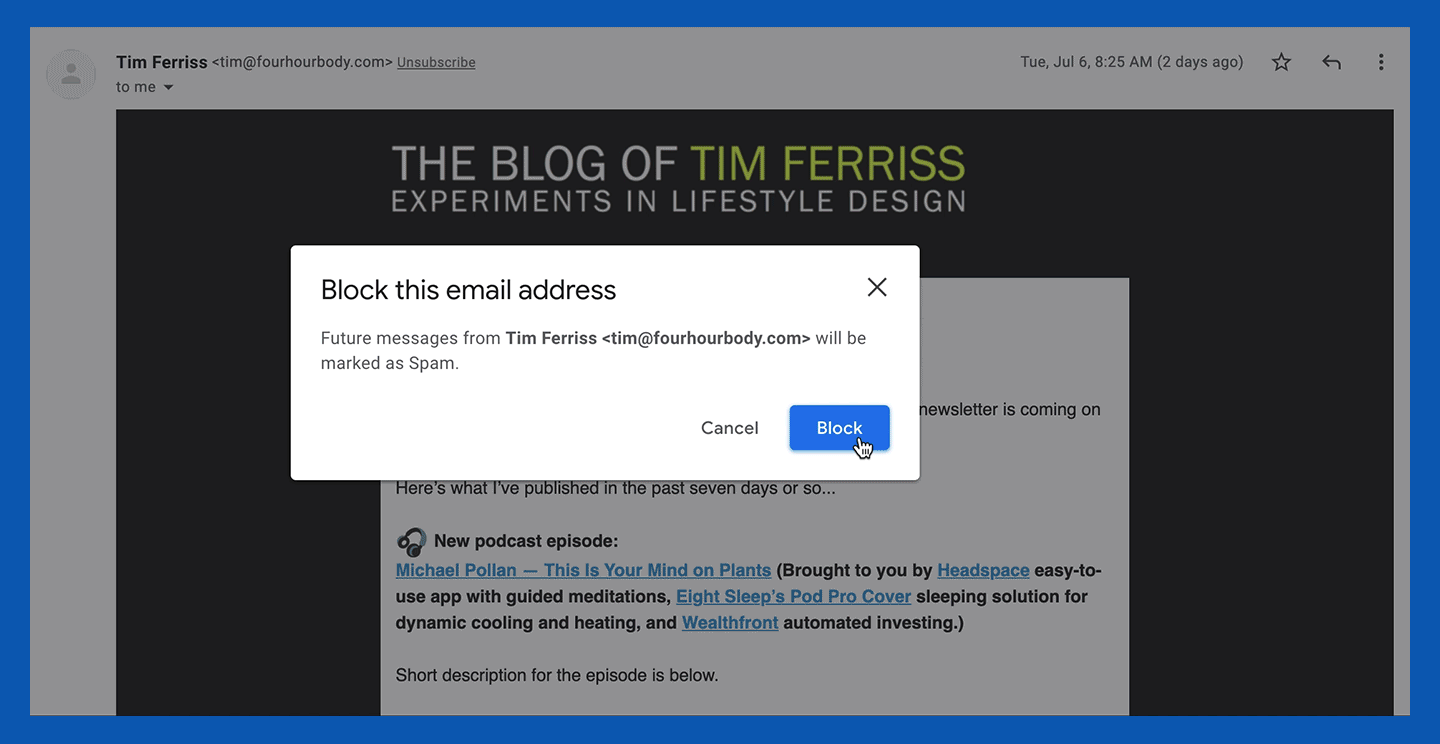
1. Open a message from the specific sender you want to block.
2. In the top right corner, next to the sender details, click the three vertical dots to open the options menu.
3. Click “Block [sender].”
4. If you also want to report the message, click the “Report spam” option below the “Block [sender] option.”
How to Block Spam in Yahoo Mail
To block emails in Yahoo Mail, start on the homepage of your inbox.
1. Select the message(s) from a certain sender you want to block by checking the box to the left of the message.
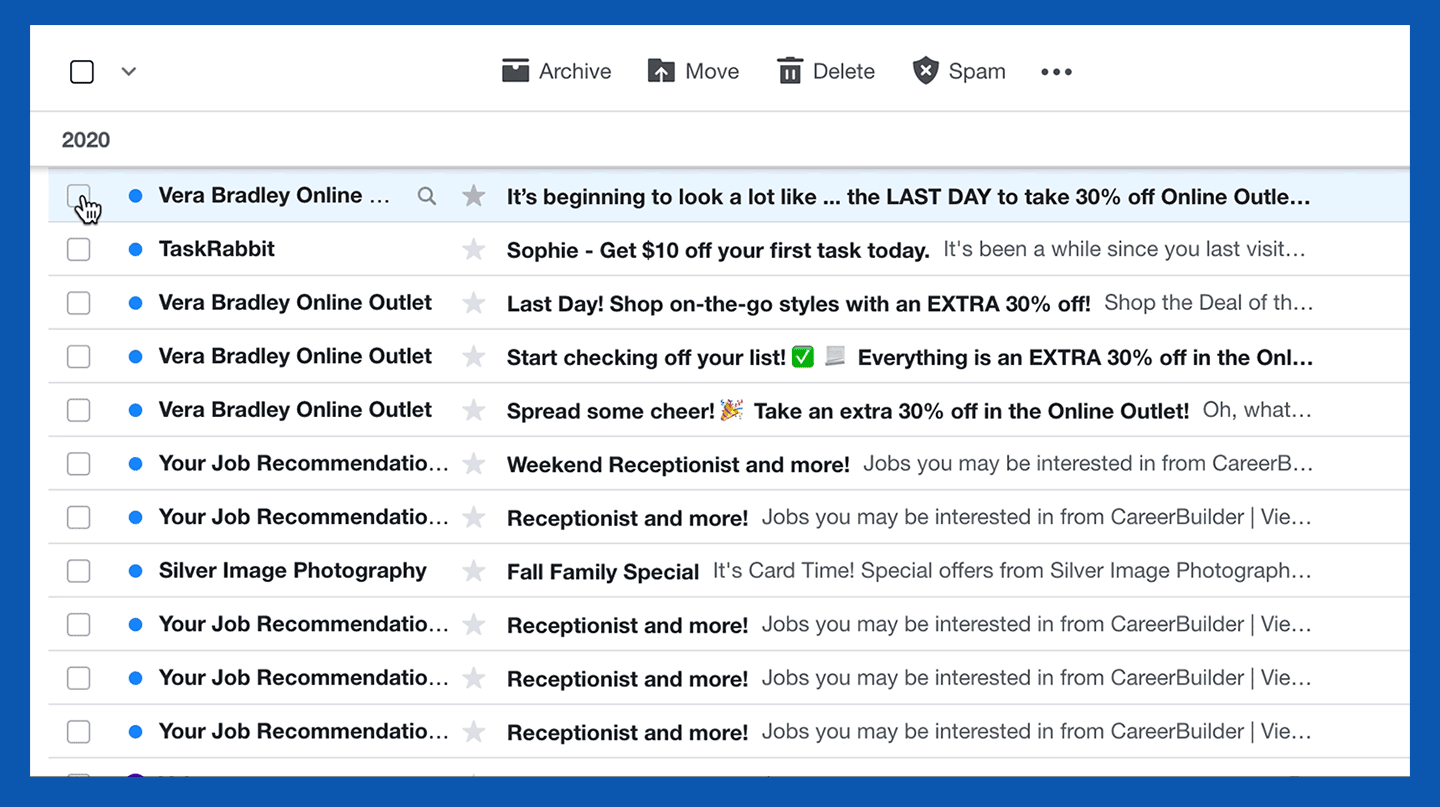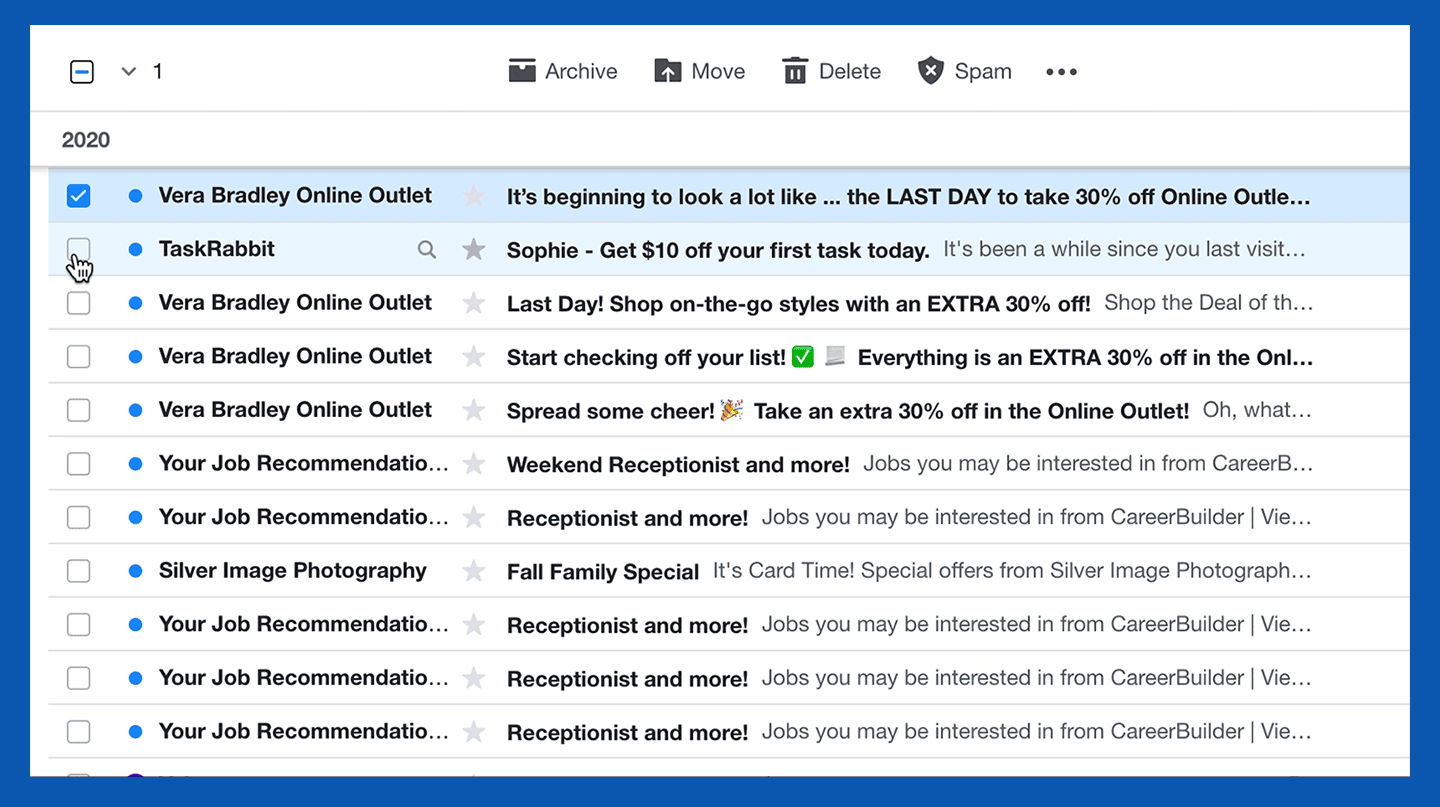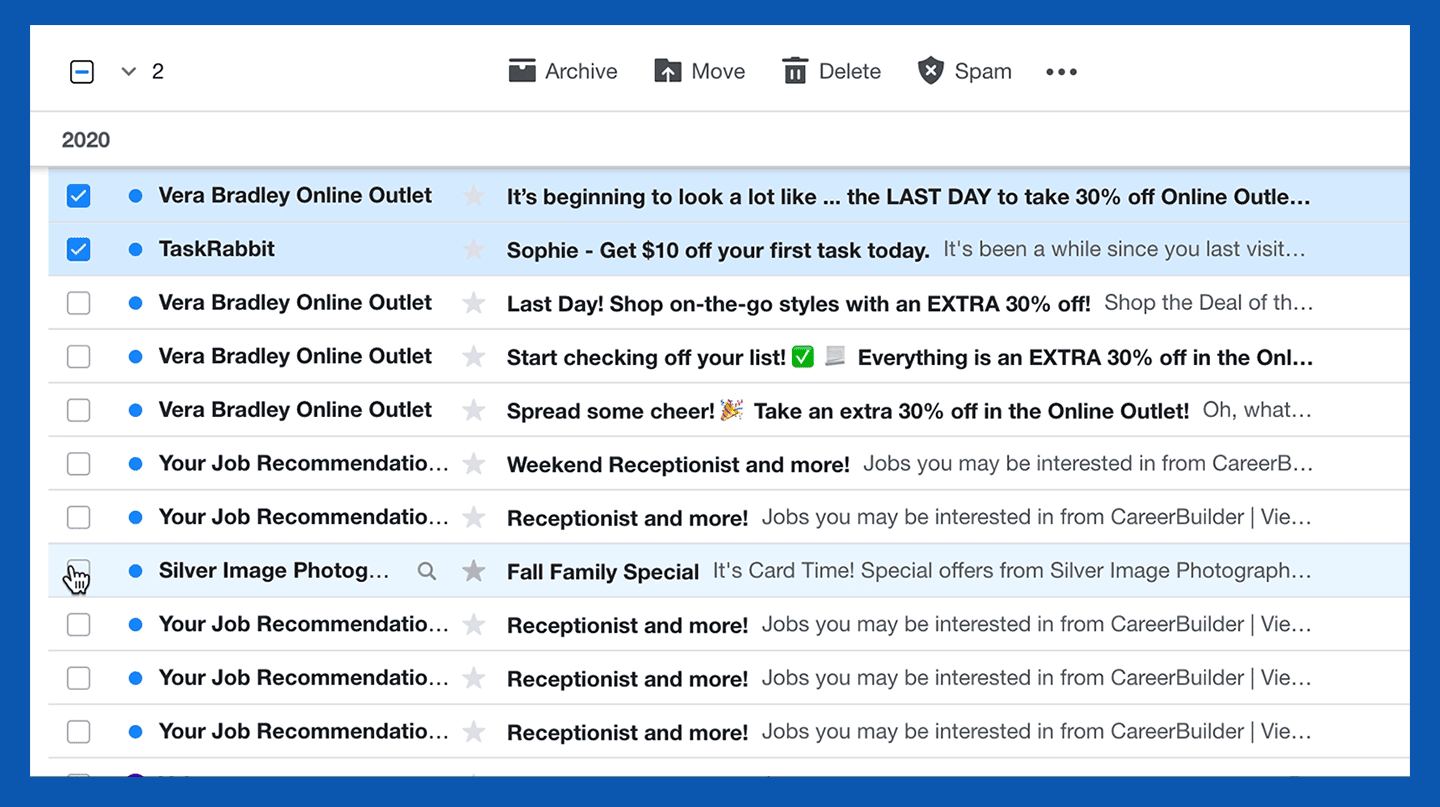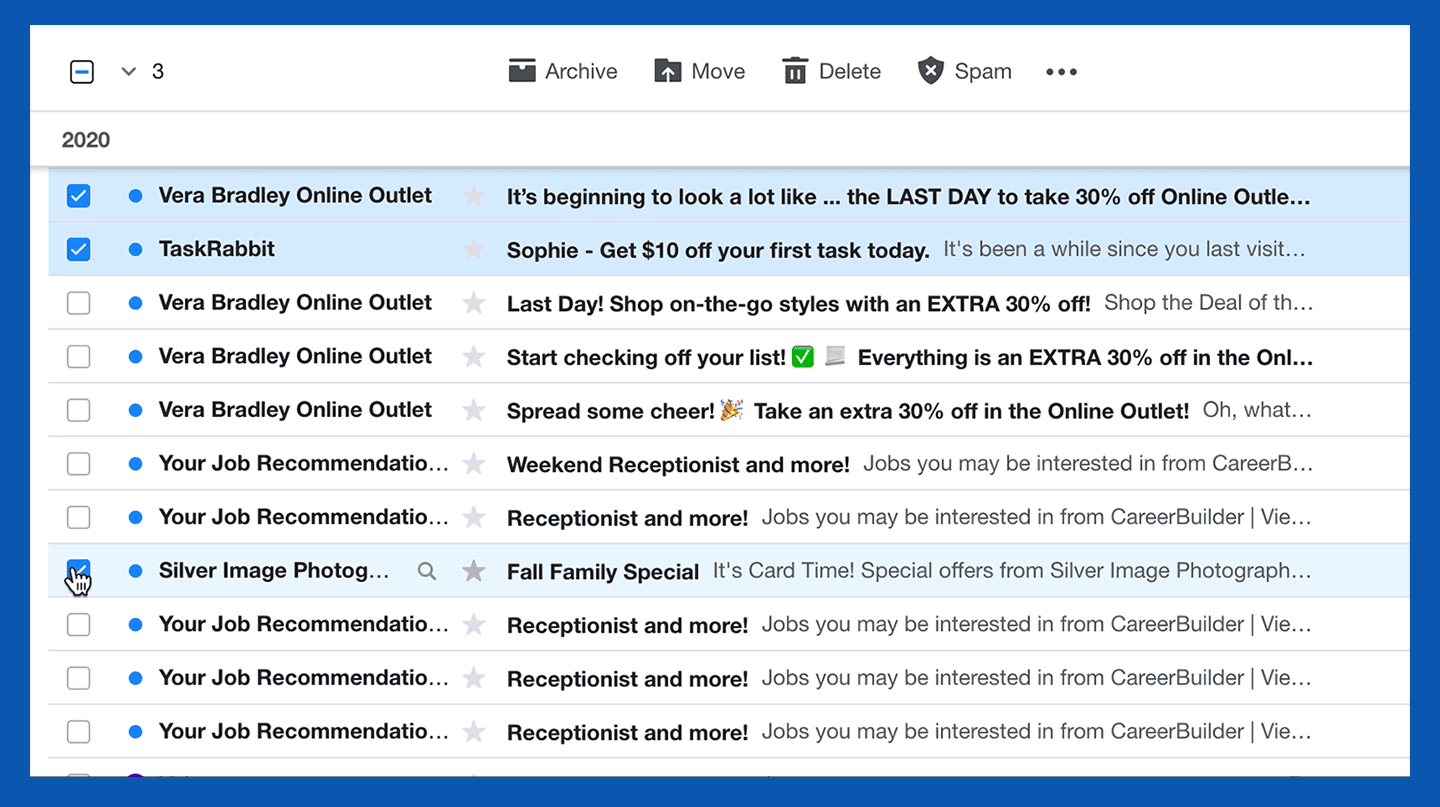
2. In the toolbar at the top of your inbox, click the three horizontal dots next to the Spam button.
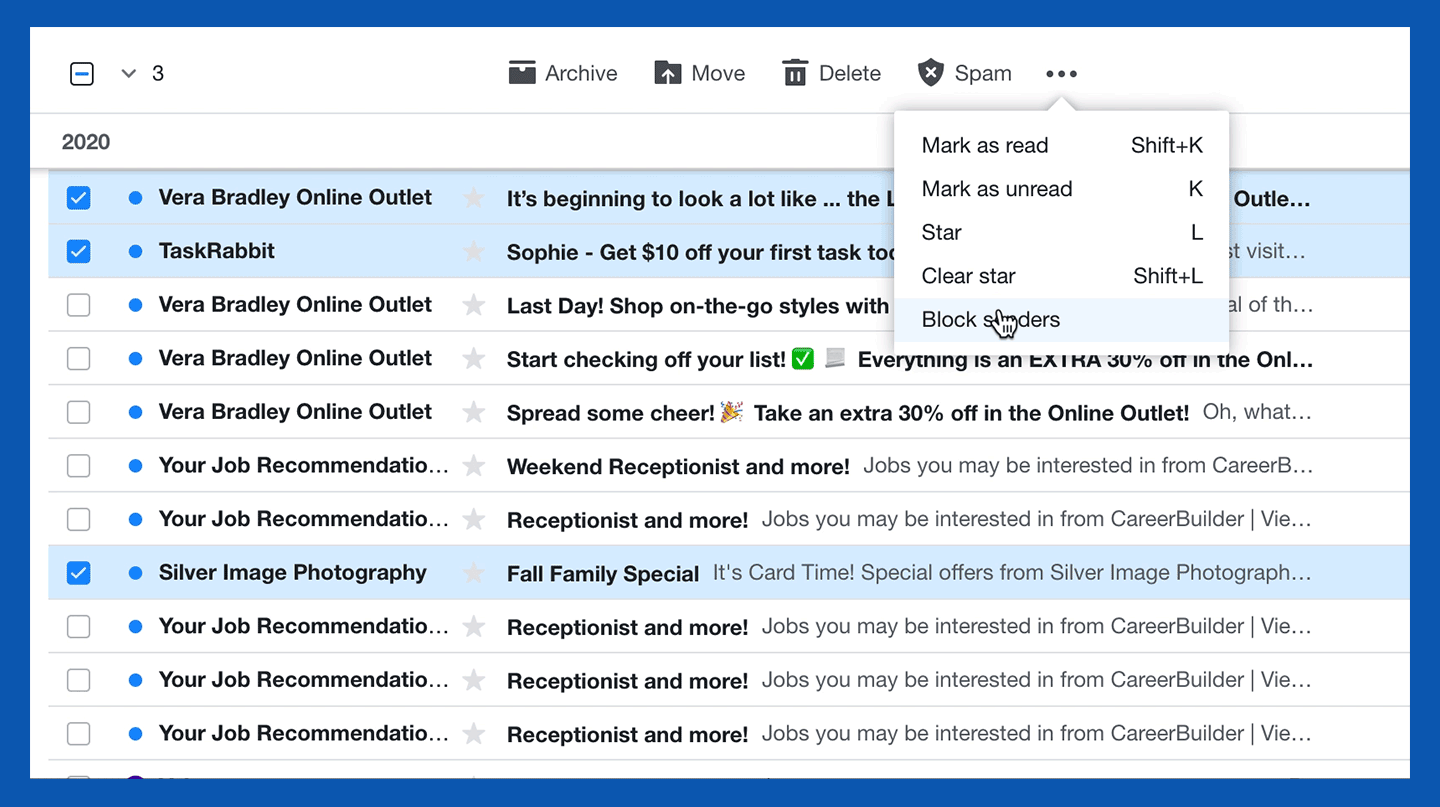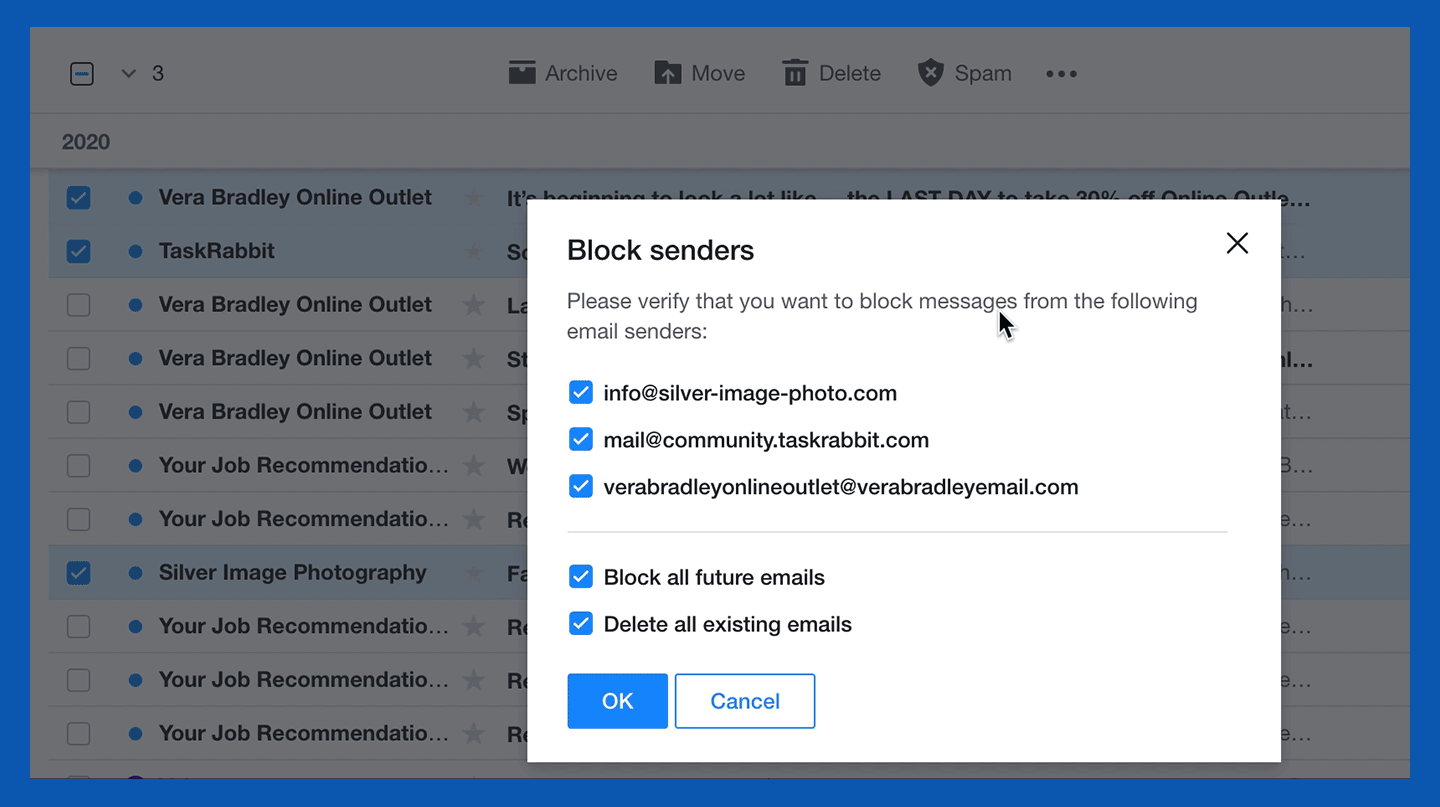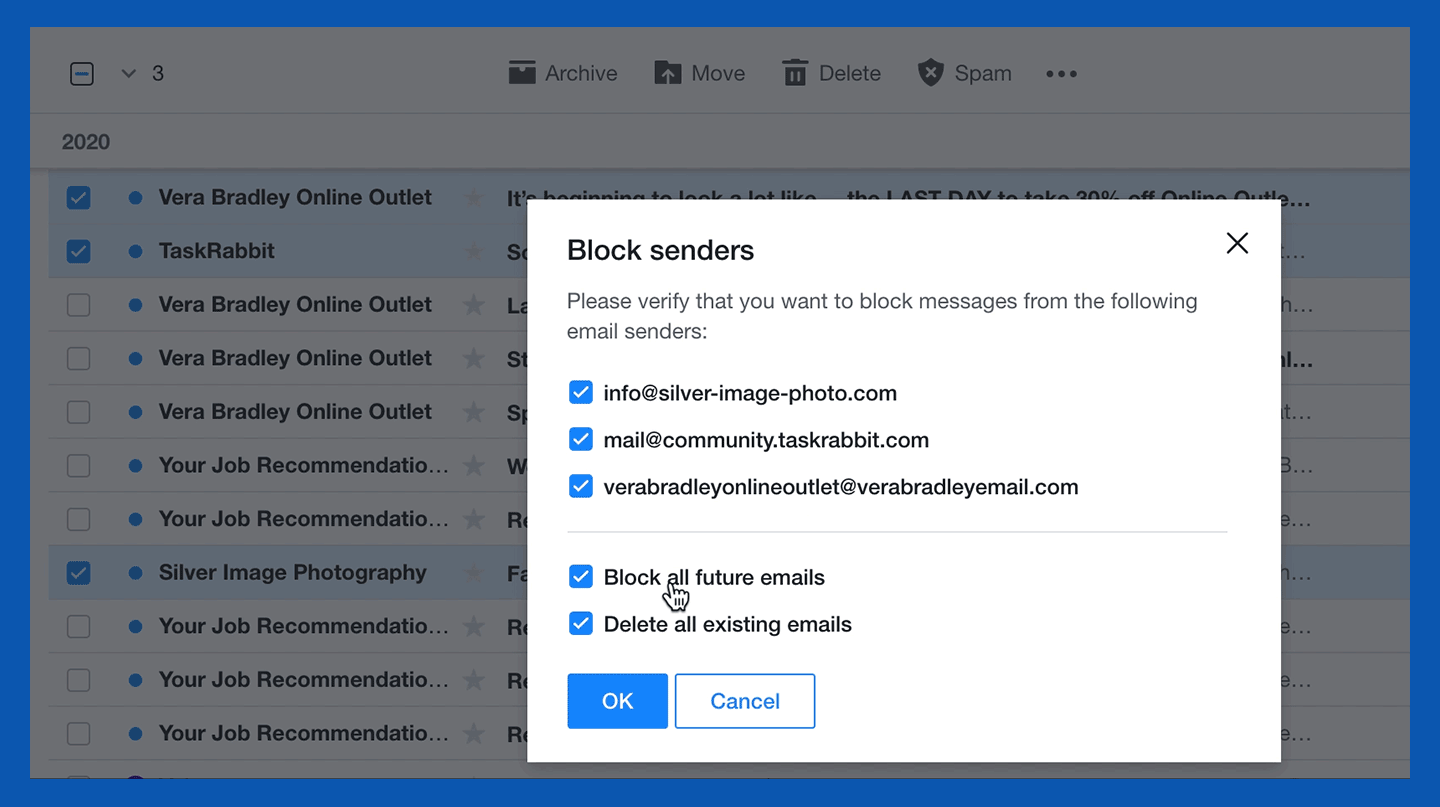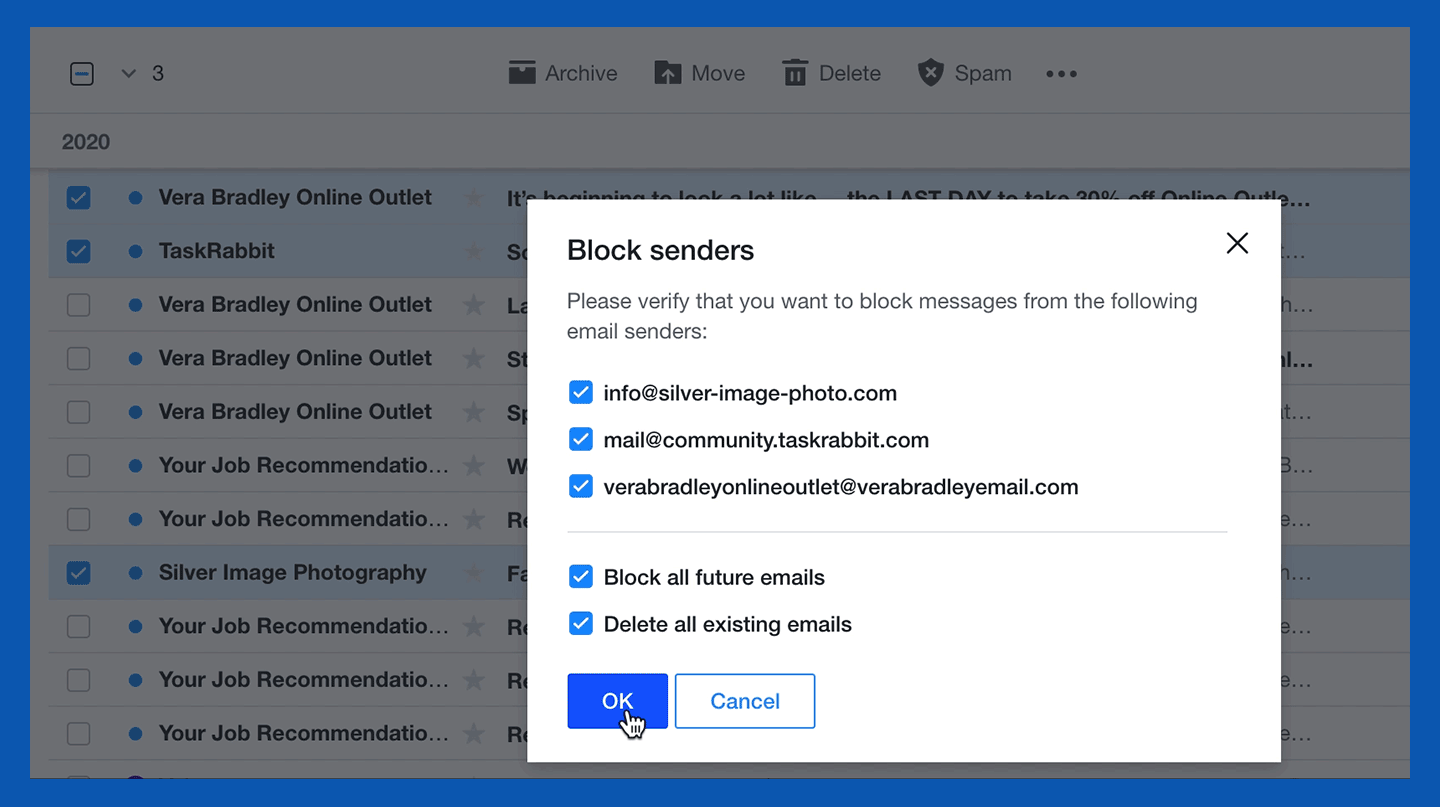
3. Select the “Block senders” option.
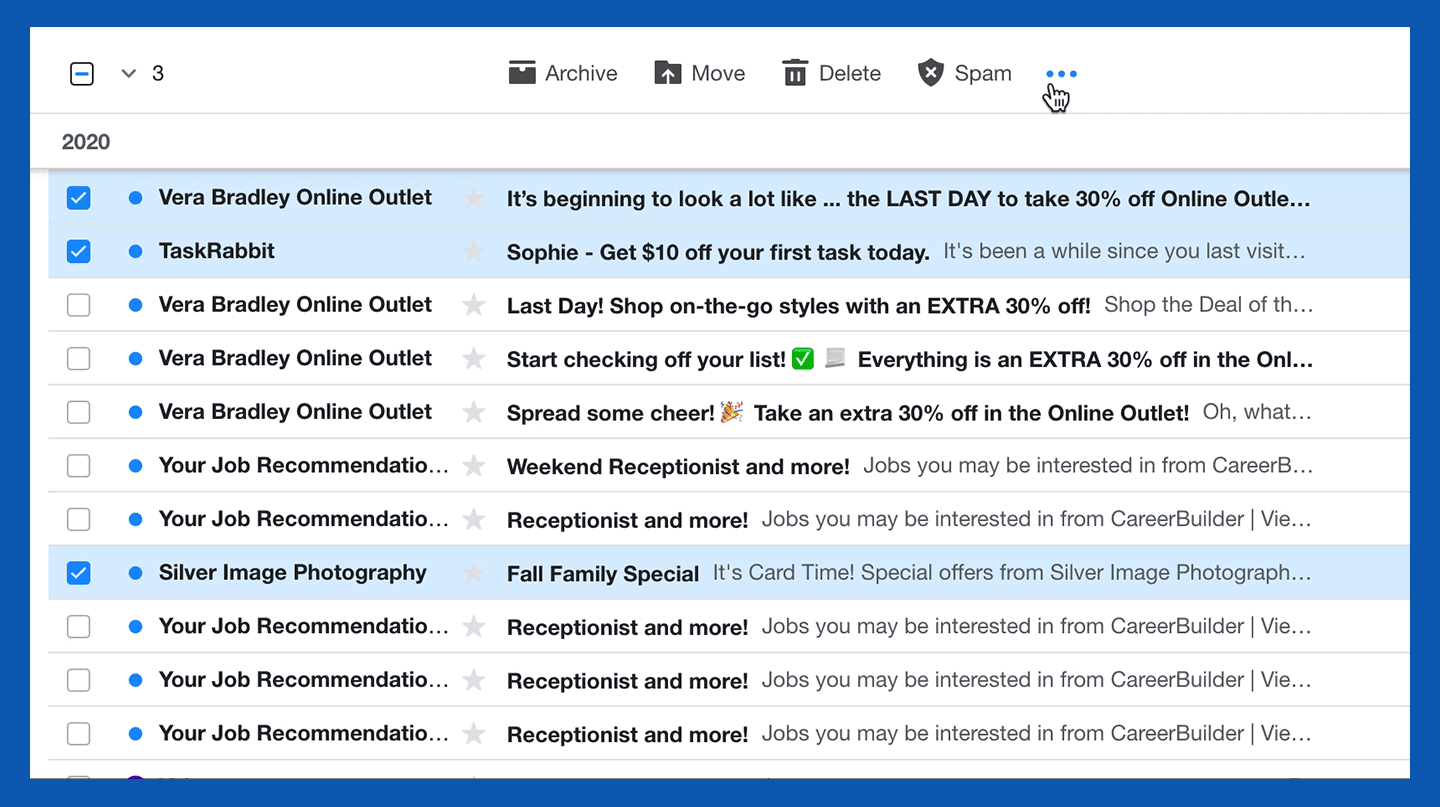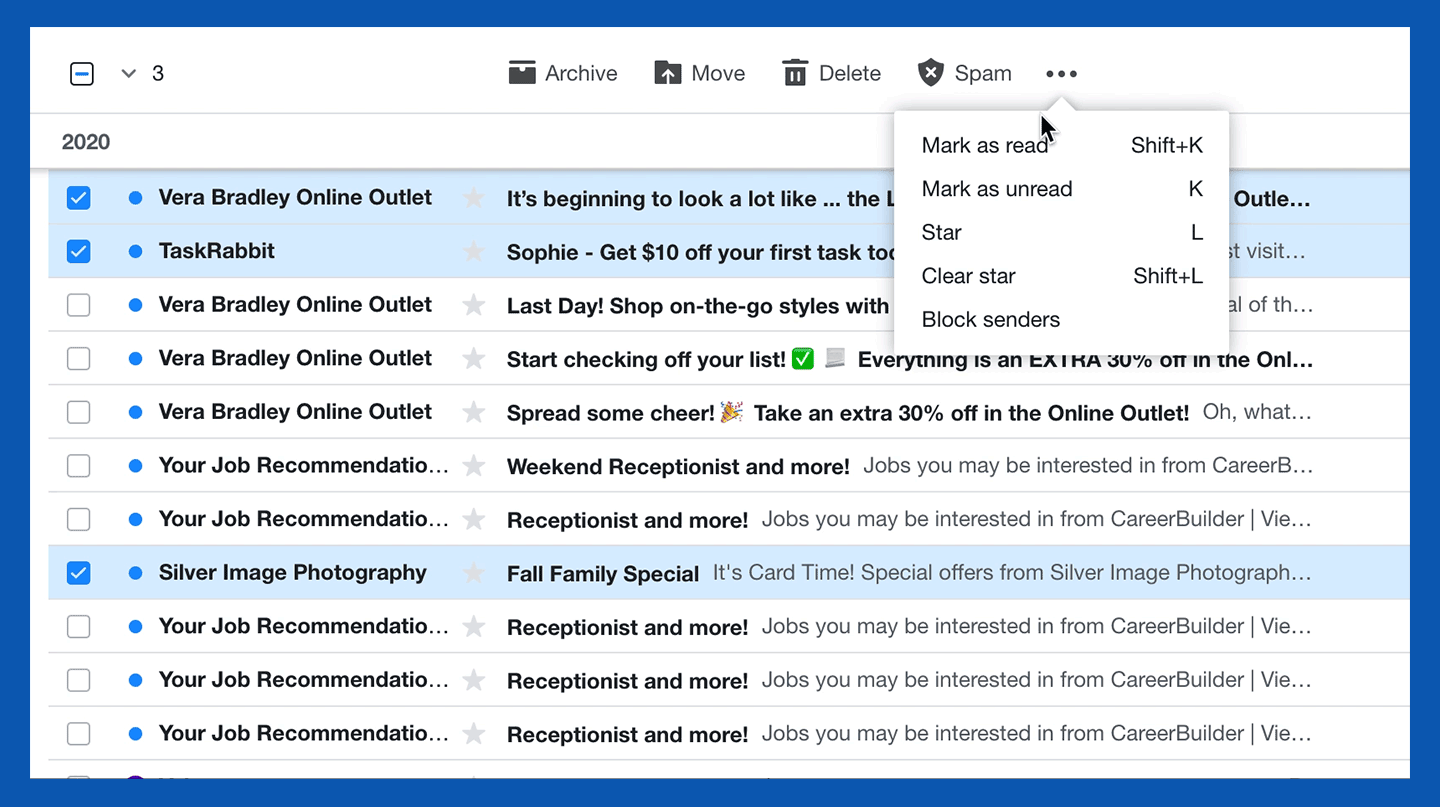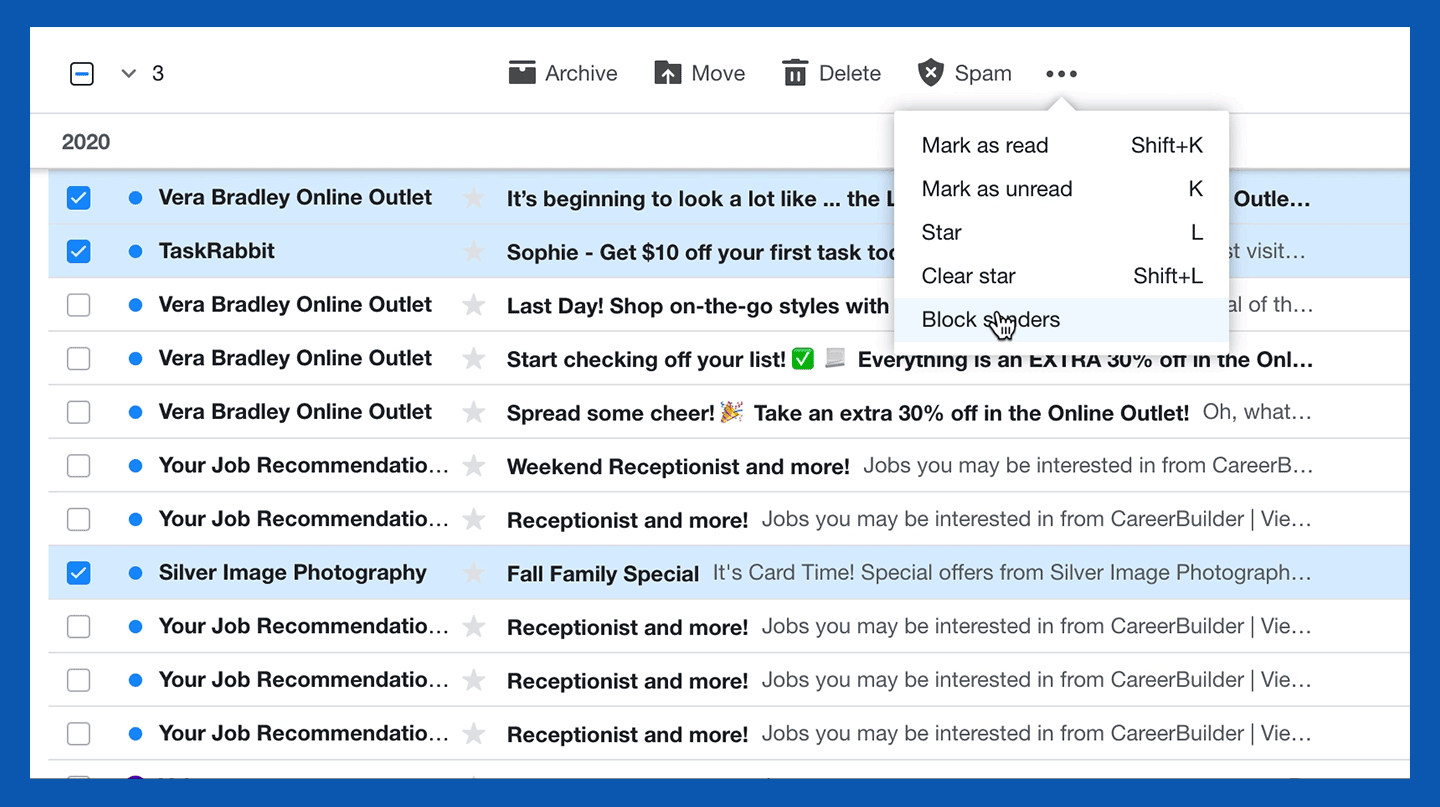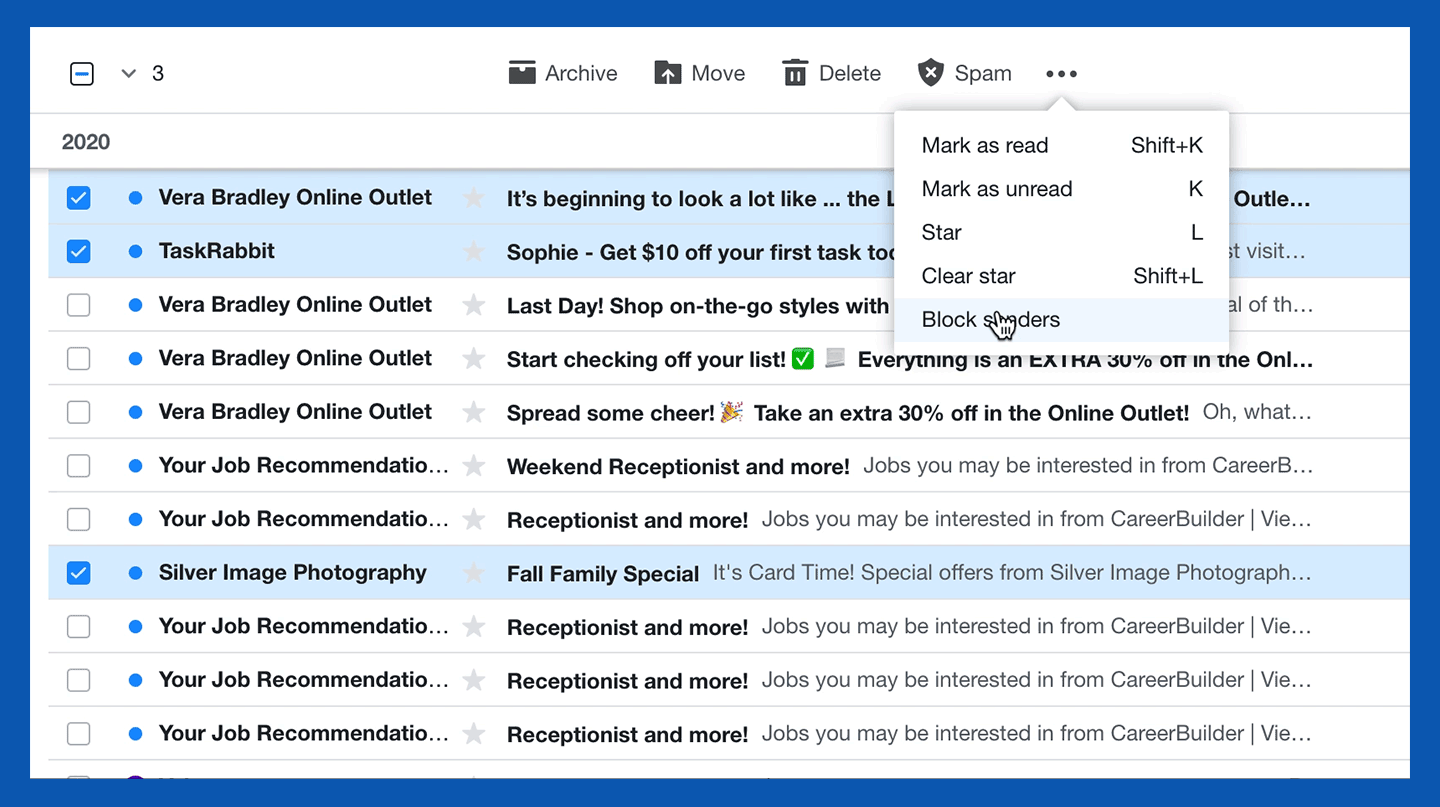
4. Review the senders you wish to block and choose your preferred settings for future and existing emails, then click OK.
How to Block Spam in Apple Mail
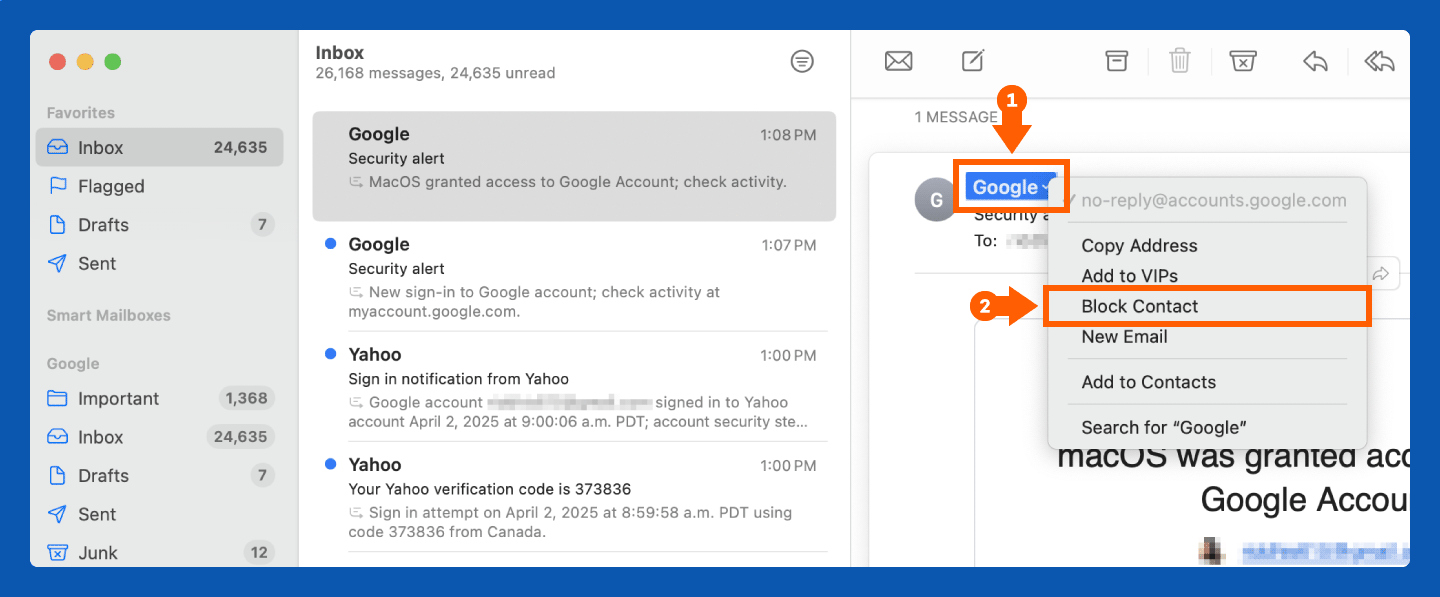
1. Select the email you want to report as spam.
2. Click the small arrow next to the sender’s name.
3. Click “Block Contact.”
How to Block Spam in Outlook
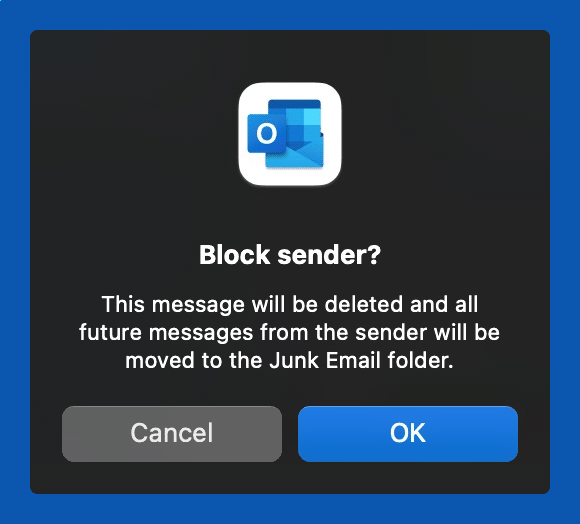
1. Right-click on the message(s) you want to block.
2. Click on Block.
3. Click OK on the Block Sender pop-up.
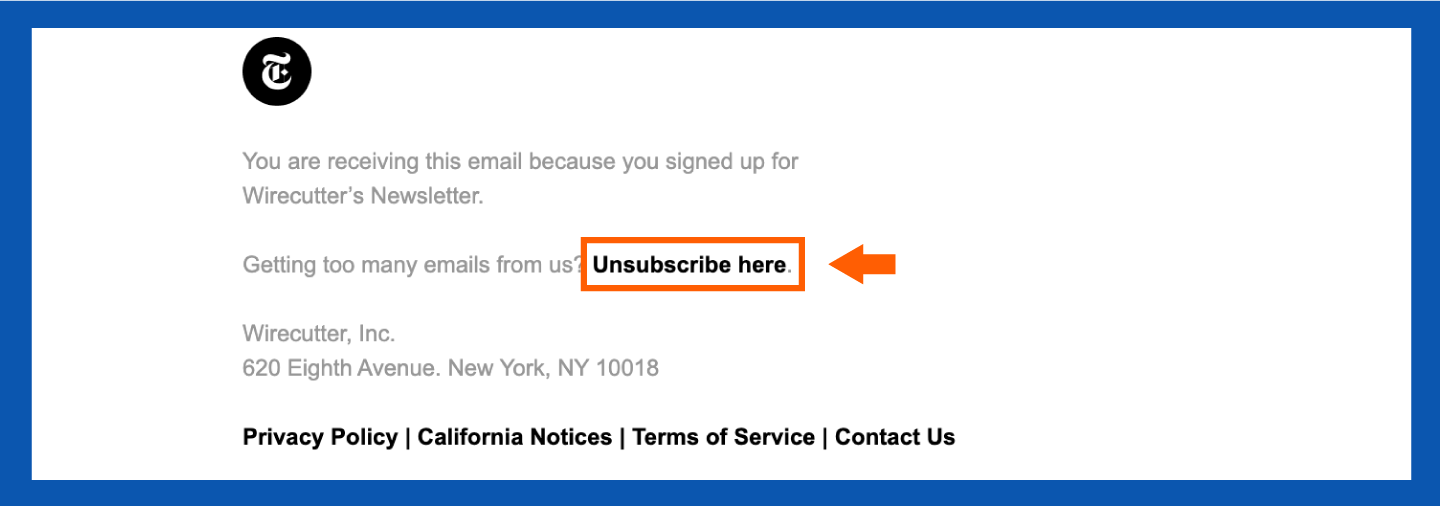
3. Unsubscribe From Mailing Lists
Many unwanted emails are promotional, not malicious. To stop receiving these:
- Open the email: Find an email from the sender you wish to unsubscribe from.
- Scroll to the bottom: Locate the unsubscribe link.
- Click the link: You may be redirected to a confirmation page.
- Follow the prompts: Complete the unsubscription process.
4. Create an Email Alias
You know how it goes — you buy something online or download a file, and suddenly, your inbox is swamped with ads you never asked for. It turns out that a lot of companies sneak you onto their mailing lists when you give them your email. If you sign up for websites with your main email, your spam can pile up.
So, here’s a little trick: Make a ‘junk mail’ email. Use that one for shopping and signing up for stuff. It won’t stop the spam, but at least it’ll keep all that clutter out of your main inbox.
| Pro tip: Want a fast way to clean up your inbox? Use your email’s search function! Type ‘unsubscribe’ to find promotional emails, select the ones you don’t want and hit delete. This instantly clears out a ton of spam. |
5. Update Your Privacy Settings
While blocking spam and junk emails helps clear your inbox temporarily, reducing your overall exposure to spam by keeping your email as private as possible will be even more impactful. Here’s how to update your privacy settings and stop spammers from accessing your email in the first place.
How to Change Your Privacy Settings in Gmail
1. Click the account icon in the top right corner of your screen.
2. Click “Manage your Google Account.”
3. You will be redirected to a new tab. On the left side, click “Security.”
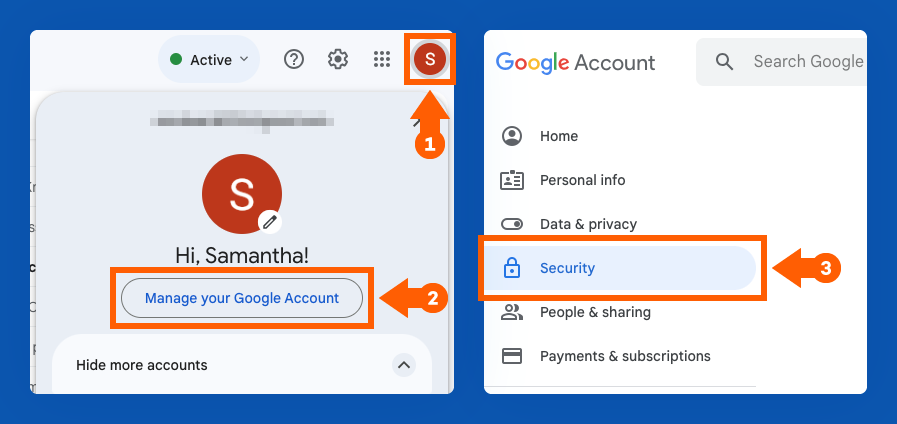
4. Review and update your security settings. This might mean enabling two-step verification, removing third-party access to your account or updating your password.
How to Change Your Privacy Settings in Yahoo Mail
1. Click the gear icon in the top right corner of your screen.
2. Click “More Settings.”
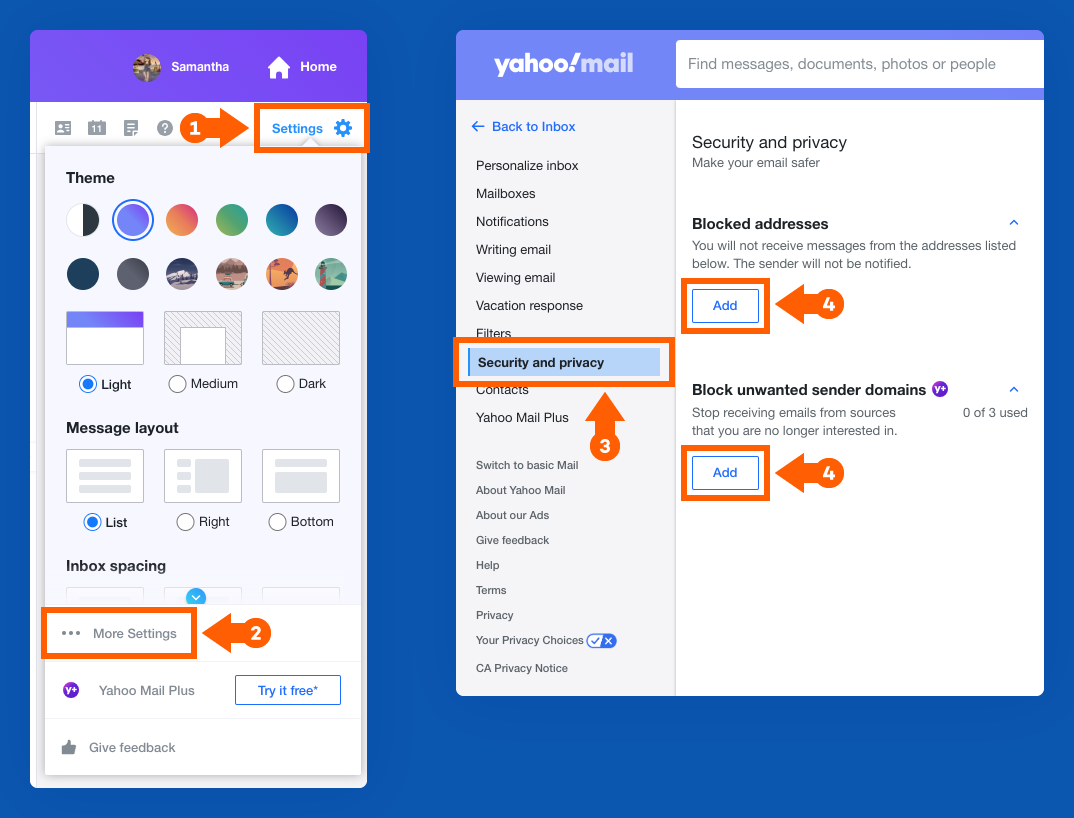
3. On the left sidebar, click “Security and privacy.”
4. Add email addresses or even domain names you want to block.
How to Change Your Privacy Settings in Apple Mail
1. With the Mail app open, click “Mail” in the top left corner of your Mac. Select “Settings.”
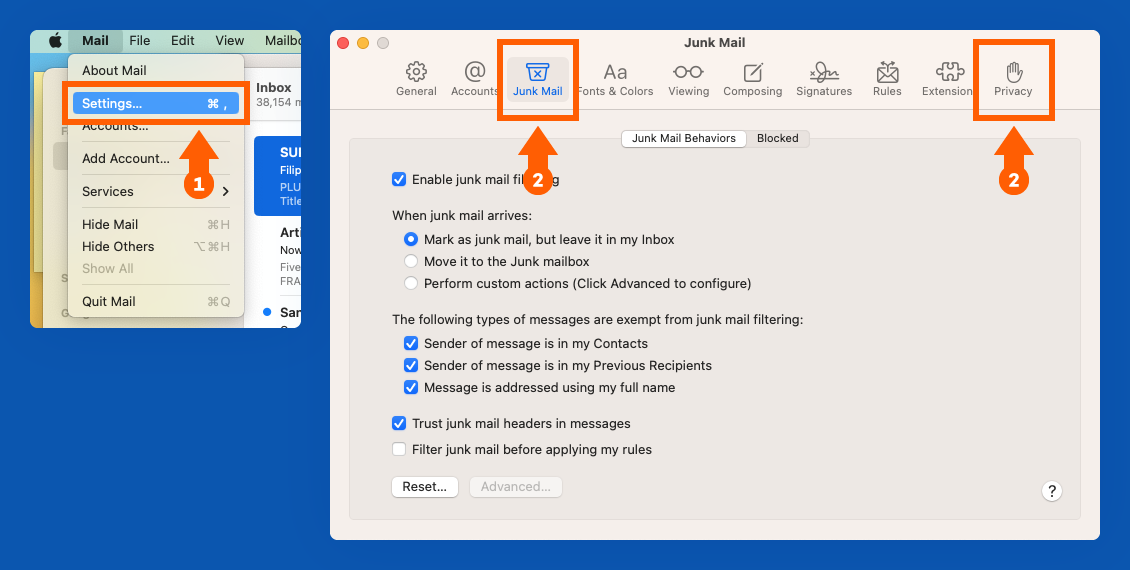
2. Adjust your settings in the “Junk Mail” and “Privacy” tabs.
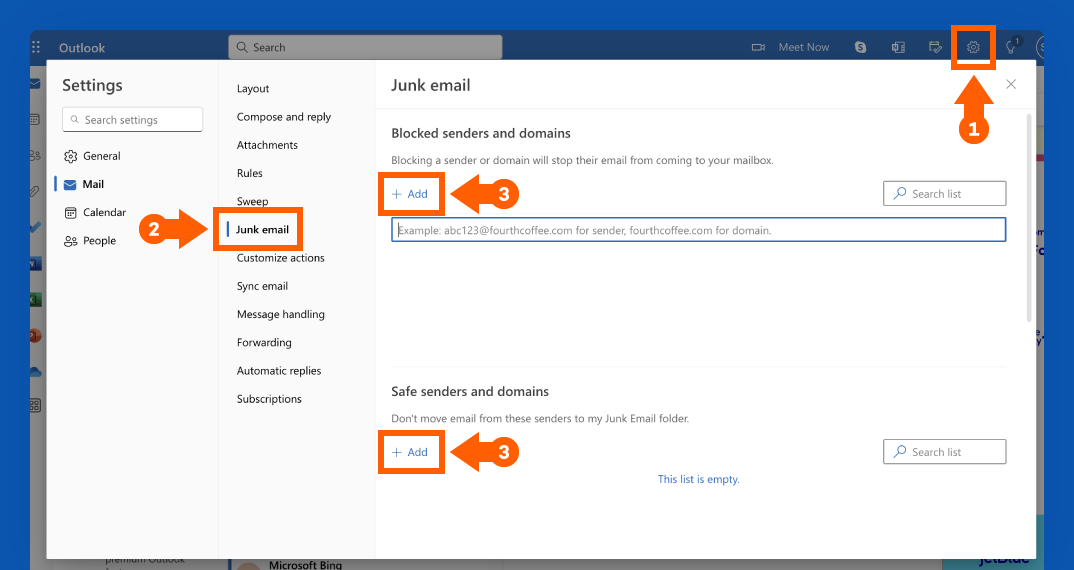
How to Change Your Privacy Settings in Outlook
1. After signing in to Outlook on the web, click the Settings gear button at the top right of your screen.
2. The Mail Settings window should open. Click “Junk email.”
3. Click the + Add button to input addresses for Safe senders and domains or Blocked senders and domains.
6. Use a Third-Party Spam Filter
While most email hosting platforms come equipped with an automatic spam filter, pairing it with a third-party spam blocker can provide an added layer of security and help catch spam that your email host might have missed.
For an easy-to-use free option, MailWasher is a great choice. Once you sign up, this service will start applying a series of filters to catch unwanted messages. It even lets you review the captured emails online before they actually hit your inbox.
Another effective option is SpamSieve, which is $30 for a paid membership with a free trial available. Similar to Mailwasher, it relies on an intelligent filtering system to sort out spam from your inbox.
As you work with these third-party filters over time and mark which messages are spam and which are safe, both SpamSieve and Mailwasher adapt to your inbox and become smarter in their ability to recognize what’s spam and what’s not.
7. Keep Your Email Address Hidden
You should think of your email address as a valuable piece of personal information — because it is. You don’t want to hand it out to just anyone, and it’s best to keep your primary email address as private as you can.
This is important for public pages like social media profiles or a personal website, which are easy targets for scammers or bots to find your email address. Check the account settings on platforms like Facebook, Twitter and LinkedIn and make sure your email address is only visible to yourself and your friends.
If you have a job that requires your contact information to be visible online, a workaround to maintain your security is to write your address in longhand. For example, instead of “johndoe@google.com,” the longhand could be “John Doe at Google’s Email Service.” This format is still readable to humans but prevents automated bots from recognizing it as an email address.
8. Don’t Interact with Spam Emails
If you’ve ever thought about responding to a spam email, don’t — even if it’s a request to permanently remove yourself from their mailing list. This signals to whoever is on the other end of the email that your account is active and could lead to receiving even more spam as a result.

9. Read the Terms and Conditions
Any time you download, purchase or subscribe to something, you’re asked to agree to certain permissions before you can gain access. Some of these terms include an agreement to receive regular emails from the company or permission to share your information with third parties.
While it’s common to skip through the fine print, reading the Terms & Conditions is an easy way to keep unnecessary spam out of your inbox. This goes for apps, accessing gated content online, online games and software and purchases for products or services.

10. Disable “Auto-Load” for Images
Spammers frequently embed tracking pixels within images, which notify them when you open an email and confirm your active email address. This confirmation makes you a more valuable target for future spam campaigns.
Disabling auto-load prevents these tracking pixels from reporting back, effectively masking your activity and reducing the likelihood of receiving further unwanted emails.
11. Check if Your Email Is on the Dark Web
Regularly checking if your email address has been compromised and surfaced on the dark web is a proactive step in combating spam. When data breaches occur, email addresses are often among the stolen information that ends up being sold or traded in illicit online marketplaces.
If your email is on the dark web, it’s likely already in the hands of spammers, increasing the risk of targeted spam campaigns, phishing attempts and even identity theft. You can use tools like Haveibeenpwned to check if your email is in a data breach.
12. Create a New Email Address
If you’ve tried the strategies above and still can’t keep spam at bay, it’s possible your email was exposed to a data breach, or you unknowingly responded to spam in the past. Whatever the cause, a persistent overload of spam might mean it’s time to switch over to a new email account entirely.
You can do this by registering for a new email account with your preferred email host. Once you do, you should notify your contacts from your new account to let them know you’ve changed email addresses. Be sure to keep both addresses active for a few months to keep track of any incoming emails that need to be redirected to your new account.
While your old email account may continue to get spam, this method ensures it stays out of your primary inbox and reduces the chances you’ll accidentally activate a malicious email. Once you can get rid of the old address, you should have significantly less spam.
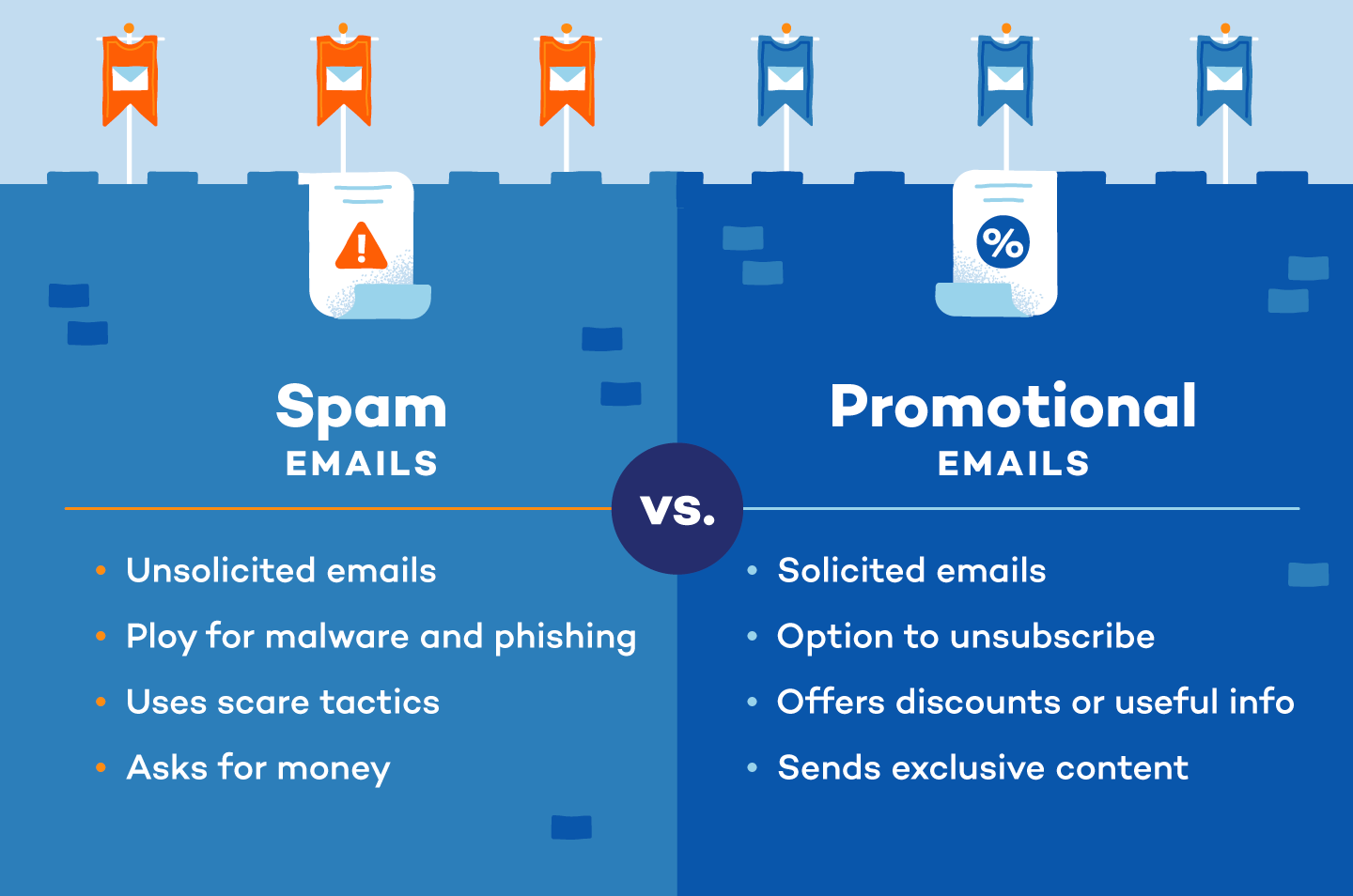
What Are Spam Emails?
Spam emails are unsolicited, mass-distributed messages that clutter inboxes, ranging from annoying advertisements to dangerous phishing attempts and malware. While some are simply unwanted promotions, others aim to steal personal information or infect devices, posing serious risks like identity theft and financial fraud.
Unlike general spam, phishing emails specifically target users to extract sensitive data. Recognizing and reporting these unwanted emails is crucial for maintaining inbox security and protecting against potential harm.
How to Spot a Spam Email
How can you determine whether an email is a legitimate marketing email from a reputable brand or a dangerous spam email? First, you should look for the telltale signs of spam or phishing emails: an unclear subject line, excessive grammar mistakes or anything that conveys a sense of urgency with a payment request are all obvious signs of a spam email. On the other hand, legitimate promotional emails will always use the official email address of a company.
For example, you should be wary of an address that reads SpotifySupport@gmail.com since reputable companies wouldn’t use Gmail as their email host. Instead, it would read support@spotify.com.
As automated technology evolves, safeguarding your online identity from spam becomes essential. By consistently reporting spam, you train your email provider’s filters for better inbox protection. Enhance security further with strong, non-sequential passwords and robust antivirus software to deter hackers.
FAQ
Have more questions about email encryption and security? Here are answers to some frequently asked questions to help you understand how you can protect your emails and ensure your sensitive information stays secure.
Why Am I Suddenly Getting So Many Spam Emails?
A sudden increase in spam can result from several factors: recent data breaches exposing your email, signing up for newsletters or services that sell your data or spammers discovering your address through online activity. Sometimes, a surge in spam indicates your email is on a new spam list or being actively targeted.
Why Does Blocking Spam Emails Not Work?
Blocking individual spam emails often proves ineffective because spammers frequently change sender addresses and tactics.
While blocking can temporarily reduce specific senders, it doesn’t address the root issue of your email being on spam lists or the evolving techniques used by spammers.
How Do You Remove Your Email From Spam Lists?
It is nearly impossible to remove your email address entirely from all spam lists. However, you can significantly reduce spam by unsubscribing from legitimate mailing lists, reporting spam to your email provider, changing privacy settings on online accounts and being cautious about where you share your email address.
Is It Better to Block Spam Emails or Just Delete Them?
Reporting spam is generally more effective than simply deleting it. Reporting helps train your email provider’s filters to recognize and block similar spam in the future, improving overall inbox security. Deleting does nothing to prevent future spam. In the case of phishing attempts, reporting is crucial.





2 comments
We need to stop phishing emails for our organization, and we need demos and pricing to implement them.
google are doing nothing to stop spam emails in my spam file, i block them and report them as phishing but they still keep coming 50-100 per day, the same messages from a slightly different email address, its so annoying, why cant they block the ip address instead, the filter doesnt work.