The average person spends about seven hours every day connected to the internet, yet complaints and frustrations about web browsing experiences are on the rise. There are a few common themes that occur again and again, including a lack of website compatibility, the threats posed by malicious software and viruses, and concerns about intrusive advertising, disruptive pop-ups, and data privacy.
Fortunately, there are several ways to protect yourself and make your internet experience safer and more satisfying, whether you are browsing on a laptop, tablet or smartphone. Here are some of our top safe web browsing tips.
Why Is Safe Web Browsing Important?
Safe web browsing is the digital equivalent of looking both ways before crossing the street. There’s no denying that the internet can be dangerous and unpredictable. People use it for a variety of harmful things, including scams and elaborate identity theft schemes.
Practicing online safety is one of the few lines of defense you have at your disposal. It may not always prevent cybercrime, but it can reduce the chances of it happening to you. Here are a few online threats that safe web browsing habits can protect you from:
- Personal data theft: These are attempts to access your data, such as credit card information or identity details. Phishing scams are very common and succeed more often than you might think.
- Virus attacks: Unsafe web browsing practices can leave you vulnerable to virus attacks, potentially compromising your files, passwords, accounts and devices.
- Social engineering: This attack tactic attempts to manipulate web users into divulging information or taking actions they otherwise wouldn’t.
- Denial-of-service (DoS) attacks: A DoS attack targets a network or system in an attempt to block out users. This advanced and complex cyberattack is difficult to defend against.
- Ransomware: As the name suggests, this type of threat targets and encrypts your files for ransom.
11 Tips for Safe Web Browsing
Practicing online safety can save you a lot of financial and digital loss, including private information, access to online accounts, and digital assets you own, like premium software accounts, digital products, software, games, or online wallets. Here are some internet safety tips to get you started.

1. Keep Your Browser and Any Plugins Updated
Web browsers are often your first point of contact with the internet, no matter what device you are using. Developers release frequent updates to ensure you can experience the latest the web has to offer — more than ever, websites are taking advantage of all the new features enabled by HTML5 video and audio, advanced styling and improved speeds. Many sites have stopped supporting older browser versions due to compatibility and security concerns.
Hackers often target vulnerabilities in web browsers, which is why the companies that make them release regular updates to patch any vulnerabilities. Installing the latest versions helps keep your device secure — fortunately, most common browsers include options to automatically update either in the browser themselves or as part of the operating system update tools.
2. Use a Browser With Advanced Privacy and Security Features
Most modern browsers allow you to create an account so you can reduce your reliance on search engines and synchronize your bookmarks between your laptop, tablet, and smartphone. Many even enable you to see the pages you have open on other devices and open them on the device you are using at the time.
While many browsers attempt to offer a secure experience, not all succeed. Millions of users know and trust some names due to their advanced security measures. Browsers like Google Chrome, Firefox, Brave and Tor guard against cyberthreats by allowlisting authorized programs and blocking unknown functions.
3. Block Pop-Ups
While desktop pop-ups from your operating system are unavoidable, pop-ups in your web browser can often be switched off. Browser pop-ups typically open new browser windows to push adverts, and while most are just annoying, some can contain malicious links or inappropriate content.
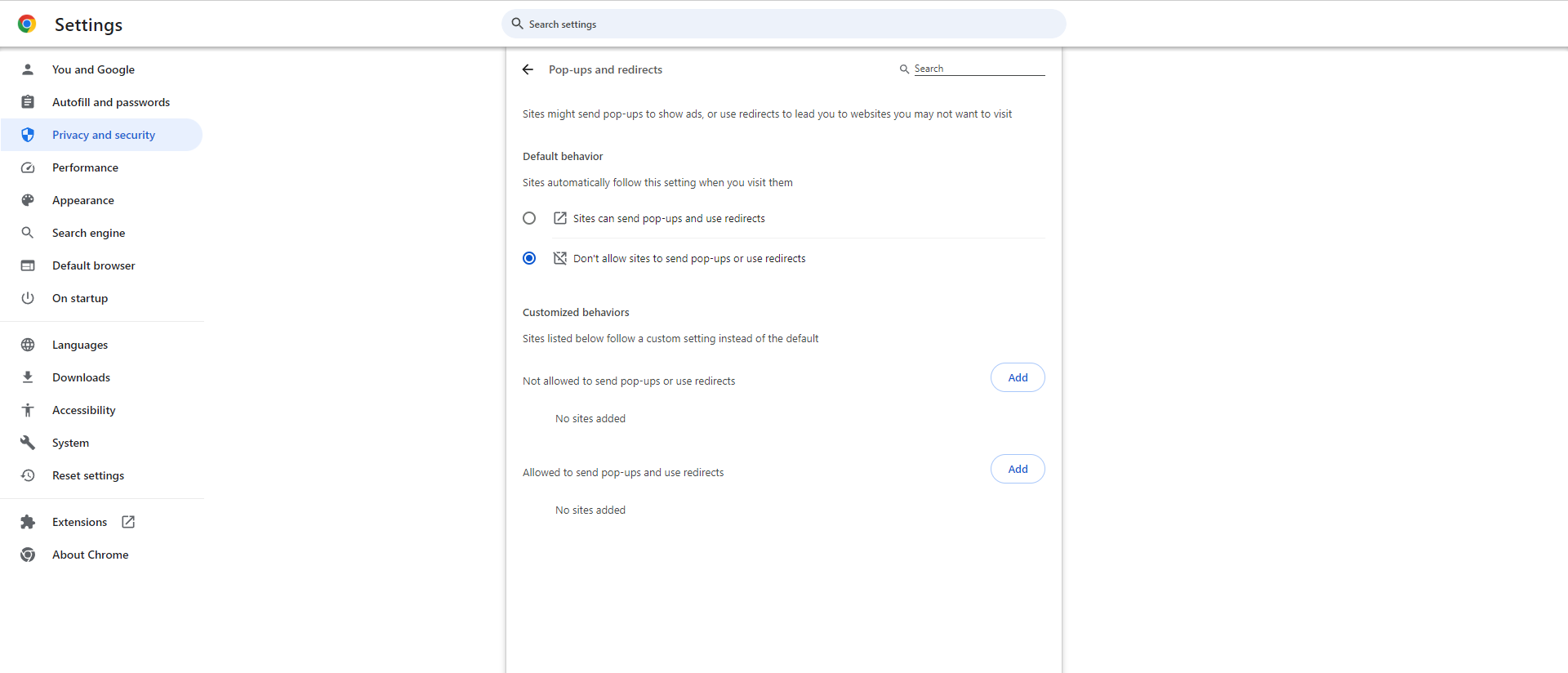
Most browsers come with filters that automatically block pop-ups and enable you to allow them for those trusted sites where they may be advantageous. Here’s how to do this on Google Chrome:
- In Settings, navigate to Privacy and security.
- Click on Site settings.
- Navigate to Pop-ups and redirects.
- Enable the Don’t allow sites to send pop-ups or use redirects option.
4. Pay Attention to URL Security Icons
You can easily tell if a website you’re visiting provides a secure connection. HTTP indicates that the connection isn’t secure and is susceptible to third-party interference. HTTPS is the secure version of the protocol, encrypting any data or information you share on that site.
One of the two tags will precede the web address you’re on. Most browsers also display a URL security icon — a lock sign to indicate that the connection is secure and an exclamation point for when it isn’t.
Depending on the browser and extensions you have, you might see some prompted warnings appear when you follow a link that isn’t secure. Here’s what these warnings might look like.
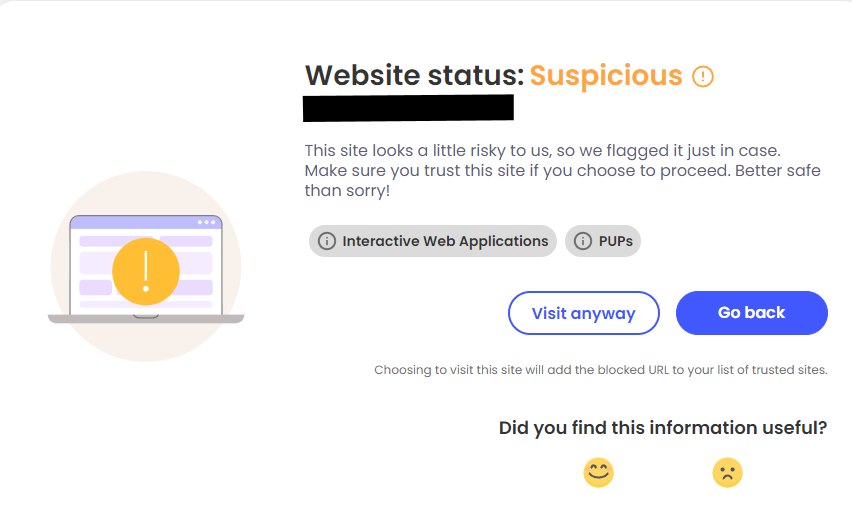
These warnings are the result of frequent malicious or suspicious activity connected to that page. It’s important to always heed them to avoid potential cyberthreats.
![]()
5. Use an Ad Blocker
Pop-up ads, and the feeling of ads following you around the internet, have led to the rise in popularity of the ad blocker. Ad blockers stop webpages from showing you ads, which sounds great until you realize how controversial this subject is and the profound impact it could have on the websites you visit.
A lot of websites use ads in a manner that interrupts and bogs down your browsing experience, making misclicks extremely hard to avoid. Some may even have malware attached to their ads, which can lead to dangerous content.
By all means, protect yourself using an ad blocker, but do consider allowlisting your favorite and most trusted sites, as the ad revenue is what keeps them in business!
6. Enable “Do Not Track” in Your Browser
Many browsers include the ability to send a “do not track” request to websites, which asks them not to collect or track your browsing data. However, what happens depends on how the sites respond to the request — but most websites and web servers don’t change their behavior and would appear to ignore the request. Still, making it clear you don’t wish to be tracked is a good start.
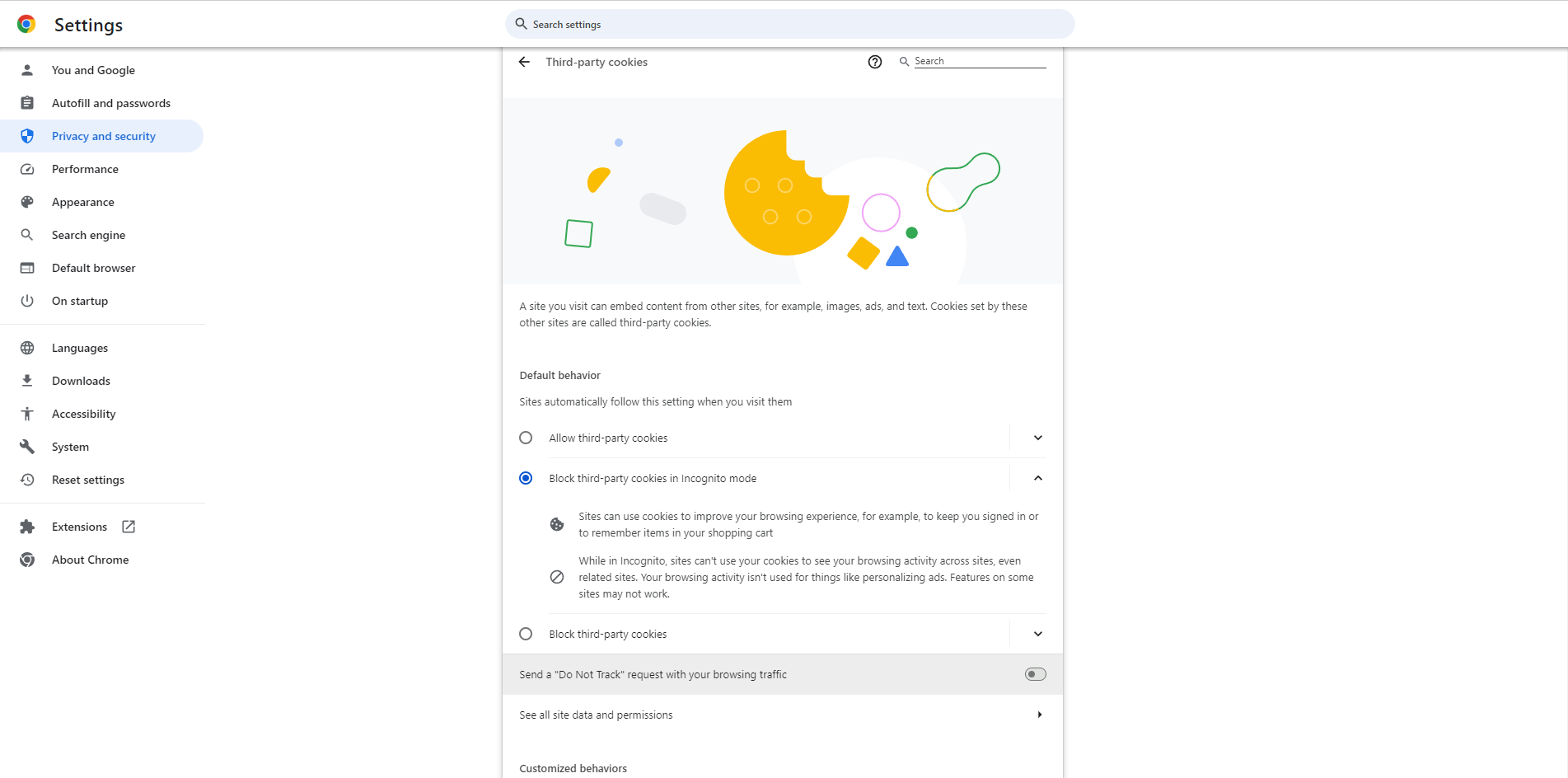
Every browser should have its own setting for this, but here’s how to activate it in Google Chrome:
- In Settings, navigate to Privacy and security.
- Click on Third-party cookies.
- Enable the Send a “Do Not Track” request with your browsing traffic option.
7. Clear Your Web Browser Cache and Cookies
Even if websites do decide to track your browsing data, you can limit the impact by regularly clearing your browser cache and deleting unwanted cookies. This prevents ads from following you around the web and can also ensure you have the latest version of a webpage downloaded.
All major browsers allow you to do this manually, and you can easily clear all your data, but there are also software options that automate the process to make your life easier. Whichever route you choose to go, it may be worth considering allowlisting those sites that you regularly log in to avoid having to re-enter login details constantly.
8. Turn on Private Browsing
Private browsing protects your private information and blocks some websites from tracking your search and browsing data. It won’t hide your activity from your internet service provider, but it does reduce the accumulation of cookies and can be helpful if you are buying presents online for a significant other.
9. Use a VPN
Virtual proxy networks, or VPNs, help you maintain your privacy by encrypting your data and internet requests before they ever hit the internet. The technology works the same no matter how you have connected to the internet — the encrypted data is sent to the VPN server, which decrypts the requests before sending them to the online destination. The information is then sent back through the same process, meaning that sites, advertisers and internet service providers can’t track what you are doing. VPNs such as the one included in Panda Dome use the most secure encryption protocols on the market to ensure the only person who can see your data is you.
10. Use a Password Manager
The number of password leaks that occur when websites are hacked makes it very dangerous to reuse the same password for a range of different sites. To prevent password leaks from being too damaging, you need to use unique passwords on every website. These should also be strong passwords — long, unpredictable passwords that contain numbers and symbols.
However, remembering all those different passwords is almost impossible — that’s where a password manager like Panda Dome Passwords comes in. They encrypt and securely store your login information for all the websites you use and help you log in automatically — leaving you to remember just one master password.
11. Ensure You Have Up-to-Date Antivirus and Firewall Protection
You need antivirus and firewall protection software on your computer, even if you’re cautious when navigating links and files.
Threats can be hidden in even the most reputable websites or files, and ensuring you are protected with a smart antivirus platform is well worth a small investment in time. The most reputable antivirus software solutions currently available use big data and AI to monitor every running application and detect attacks before they happen.
Closing Thoughts on Safe Web Browsing
The internet can be an unpredictable place. Safe web browsing practices should be every web surfer’s priority, especially since the majority of our important information is stored in the digital world.
Using the right browser, the right features, and the right VPN can be the difference between disaster and safe web browsing. For more help and advice about how to be safe online, take a look at the tips and tricks on the Panda Security blog.





