Each and every day we see new black hat SEO attacks, where criminals poison search engine results to spread malware. Today we were researching yet another attack, with some world cup terms targeted:
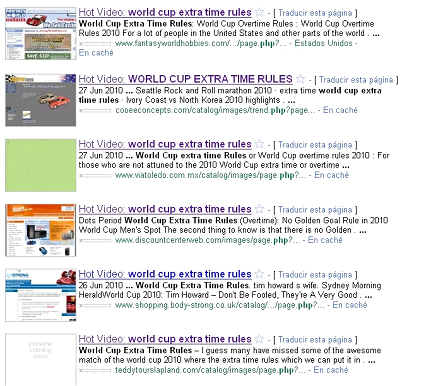
When clicking on one of these malicious results, you go to a Youtube-like web:
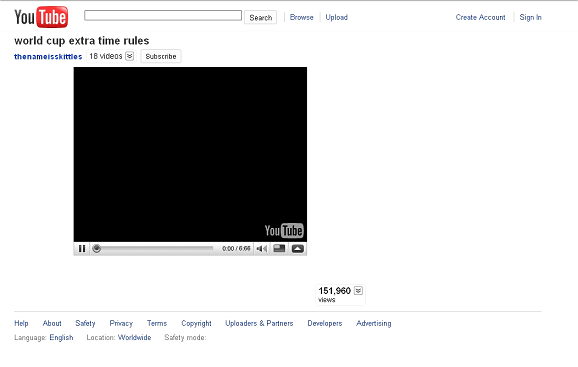
As usual, it will tell you that you need to install some codecs in order to watch the video. Of course that’s not a codec, but a rogueware (infamous Adware/MySecurityEngine).
We have realized that there is an “image” folder and it is not protected… so we have taken a look at it, just a matter of curiosity 😉
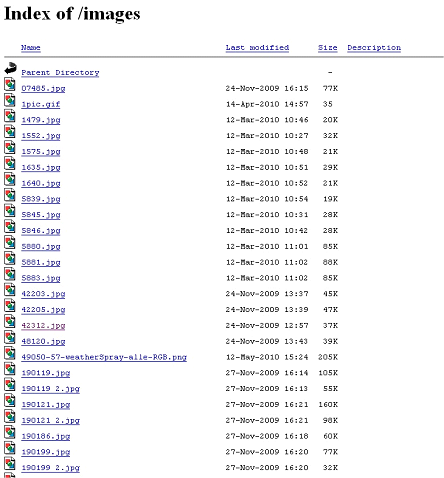 Â
Â
Among all those pictures, there are also a a few interesting files:
key.txt -> 8.000 search terms, searching them in Google leads to malware.
Sites.txt -> 177 malicious urls used in the very same attack.
SiteMap.php -> The terms of the file Key.txt with links to the Sites.txt urls, with the search terms as parameters. For instance:
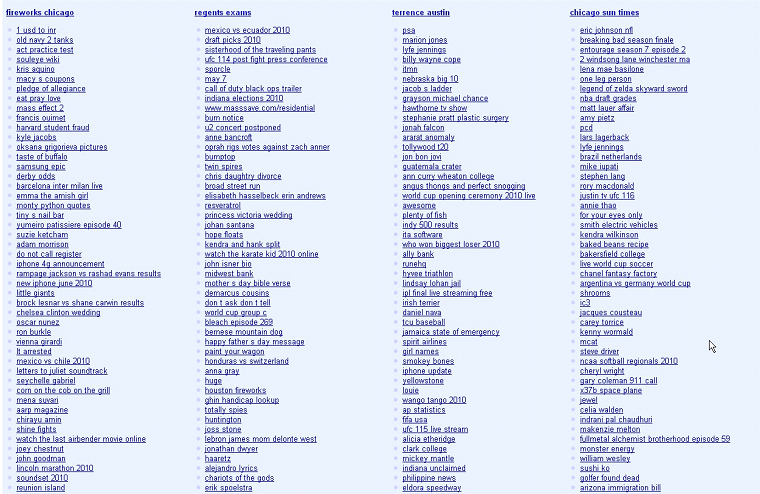
This kind of file (sitemap) is a usual tool used by webmasters to help Google indexing better their sites. However, in this case it is being used by the cybercriminals to have their malicious web sites with a better page rank. Everytime the Google bot is visiting this SiteMap.php, the page changes, but always including all the malicious URLs involved in the attack with different combinations of all the targeted search terms as parameters. Having 177 different sites doing the same, pointing to each other all the time, makes them to have a better page rank, which means that will appear in a higher position in the search results.
Page.dot -> Template of the fake YouTube web:
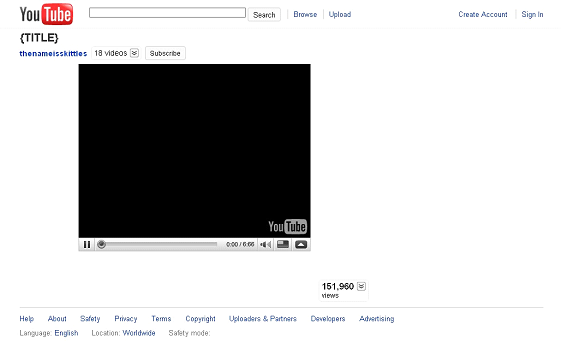
The URL where the fake codec is located it’s not hardcoded in the template, but it is obtained in real time using a script. Every time a user gets to the website, the template is loaded with the search terms as parameters, and a script named we.php is loaded. In some cases the php file is located in the same server, while in others it is located in external servers. This we.php will give back the URL where the malware has to be downloaded from.
This is all they need to launch a black hat SEO attack on an automatic way. If they monitorize Google trends to target the most popular searches, that’s all they need. And they are also doing that.
Thanks to Asier MartÃnez Retenaga for all his research.






6 comments
Hi Luis, Kindly thank Asier MartÃnez Retenaga from my side for his R & D effort. It is these kinds of noble gestures that are still keeping Black hats at bay. I am reminded of a folksy spiritual song, part of which translated would go like this : ‘…the weight of sins is ever increasing; i wonder how this Earth still sustains itself…’
SEO black hat trick has ever survived the propellants who work for the search engines. They don’t survive because they compromise the quality of search results.
Thanks for the wonderful post, helped me so much .
Thank you for reading us!
Kind regards,
Panda Security.