CryptoLocker is a family of ransomware whose business model (yes, malware is a business to some!) is based on extorting money from users. This continues the trend started by another infamous piece of malware which also extorts its victims, the so-called ‘Police Virus’, which asks users to pay a ‘fine’ to unlock their computers. However, unlike the Police Virus, CryptoLocker hijacks users’ documents and asks them to pay a ransom (with a time limit to send the payment).
Malware installation
CryptoLocker uses social engineering techniques to trick the user into running it. More specifically, the victim receives an email with a password-protected ZIP file purporting to be from a logistics company.
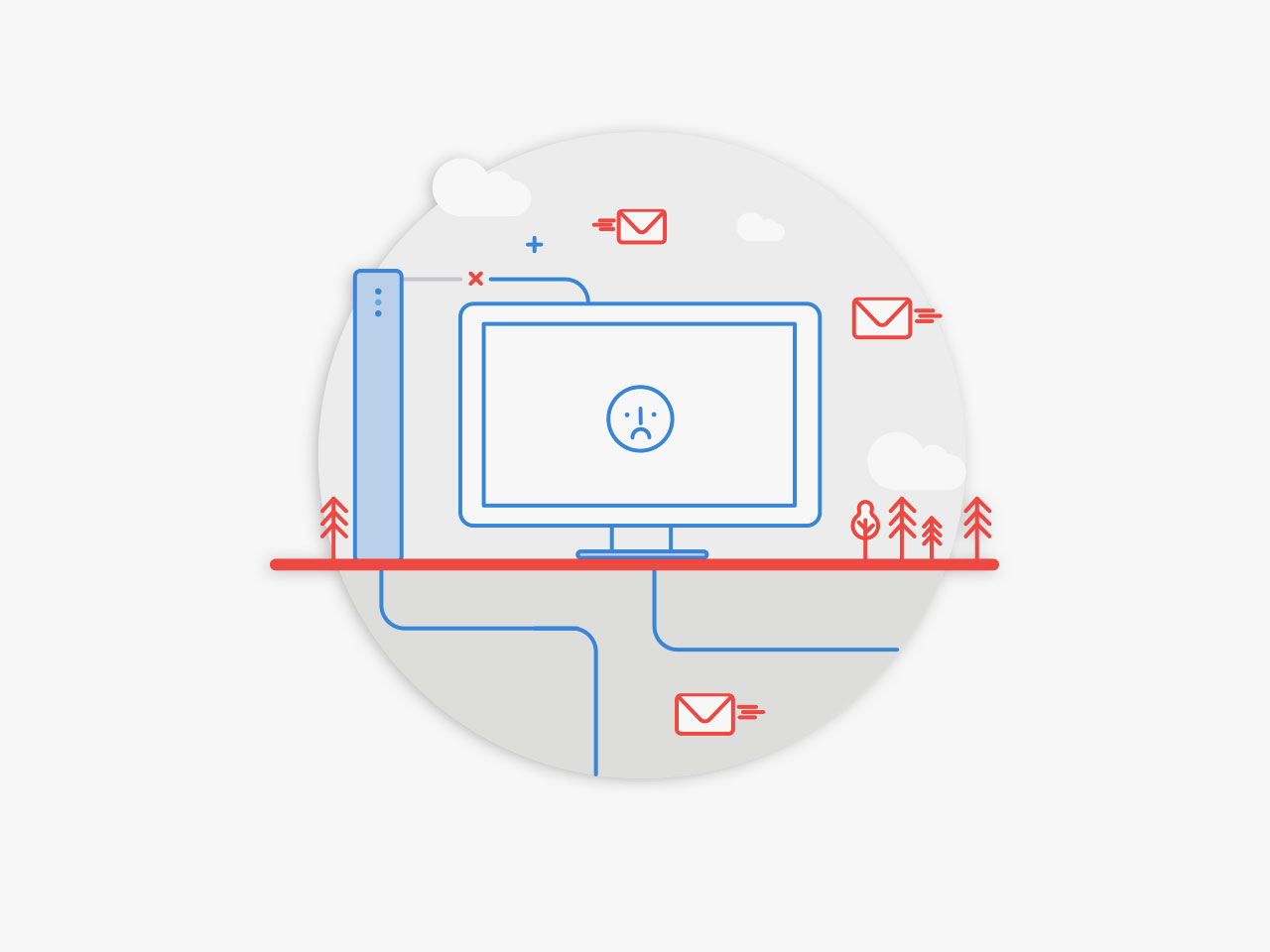
The Trojan gets run when the user opens the attached ZIP file, by entering the password included in the message, and attempts to open the PDF it contains. CryptoLocker takes advantage of Windows’ default behavior of hiding the extension from file names to disguise the real .EXE extension of the malicious file.
As soon as the victim runs it, the Trojan goes memory resident on the computer and takes the following actions:
- Saves itself to a folder in the user’s profile (AppData, LocalAppData).
- Adds a key to the registry to make sure it runs every time the computer starts up.
- Spawns two processes of itself: One is the main process, whereas the other aims to protect the main process against termination.
File encryption
The Trojan generates a random symmetric key for each file it encrypts, and encrypts the file’s content with the AES algorithm, using that key. Then, it encrypts the random key using an asymmetric public-private key encryption algorithm (RSA) and keys of over 1024 bits (we’ve seen samples that used 2048-bit keys), and adds it to the encrypted file. This way, the Trojan makes sure that only the owner of the private RSA key can obtain the random key used to encrypt the file. Also, as the computer files are overwritten, it is impossible to retrieve them using forensic methods.

Once run, the first thing the Trojan does is obtain the public key (PK) from its C&C server. To find an active C&C server, The Trojan incorporates a domain generation algorithm (DGA) known as ‘Mersenne twister’ to generate random domain names. This algorithm uses the current date as seed and can generate up to 1,000 different fixed-size domains every day.
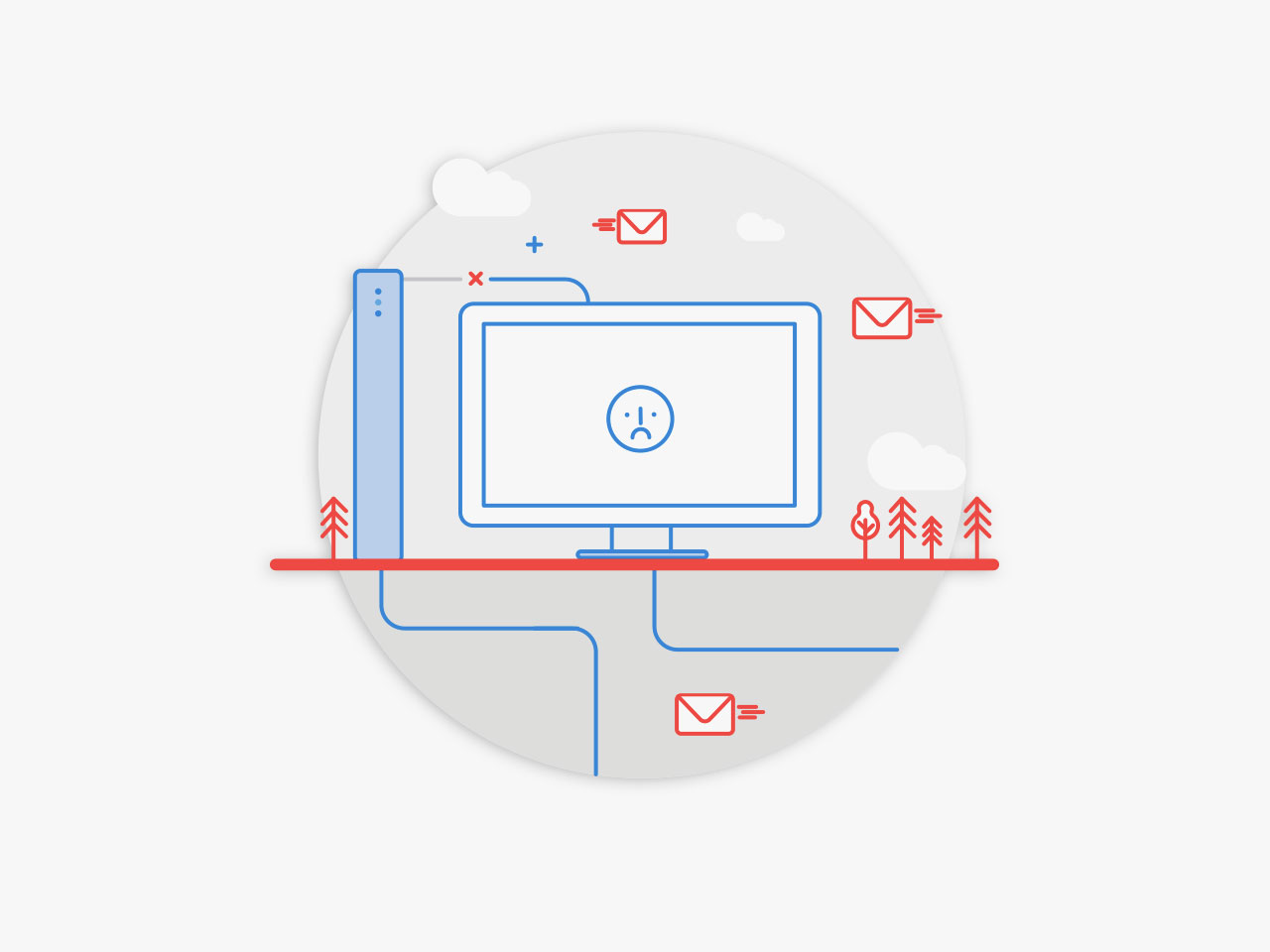
After the Trojan has downloaded the PK, it saves it inside the following Windows registry key: HKCUSoftwareCryptoLockerPublic Key. Then, it starts encrypting files on the computer’s hard disk and every network drive the infected user has access to.
CryptoLocker doesn’t encrypt every file it finds, but only non-executable files with the extensions included in the malware’s code:

Additionally,CryptoLocker logs each file encrypted to the following registry key:
HKEY_CURRENT_USERSoftwareCryptoLockerFiles
When the Trojan finishes encrypting every file that meets the aforementioned conditions, it displays the following message asking the user to make a ransom payment, with a time limit to send the payment before the private key kept by the malware writer is destroyed.
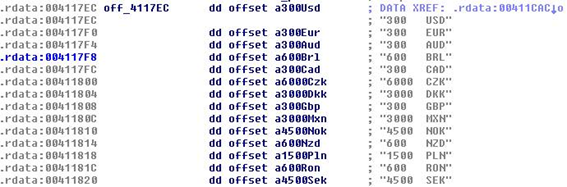
Curiously enough, the malware doesn’t ask users for the same amount of money, but incorporates its own currency conversion table.
How to avoid CryptoLocker
This malware spreads via email by using social engineering techniques. Therefore, our recommendation are:
- Being particularly wary of emails from senders you don’t know, especially those with attached files.
- Disabling hidden file extensions in Windows will also help recognize this type of attack.
- We’d like to remind you of the importance of having a backup system in place for your critical files. This will help mitigate the damage caused not only by malware infections, but hardware problems or any other incidents as well.
- If you become infected and don’t have a backup copy of your files, our recommendation is not to pay the ransom. That’s NEVER a good solution, as it turns the malware into a highly profitable business model and will contribute to the flourishing of this type of attack.




68 comments
Now that you know all about this threat, what are you doing to protect your customers? Will GP14 detect this Trojan?
Yes, it detects all the variants we have found so far.
Is the Cryptolocker virus more dangerous then the Zeus Virus?
It is different, both Trojans are really dangerous. The main problem with this one is that you can lose all your data. Zeus won’t destroy your information, but it will probably send it to cybercriminals.
We’ve seen what the cryptolocker virus can do – nasty thing. Bitcoins, which is the currency the criminals want payment in, have gone up in value by a ridiculous amount since this virus came onto the scene.
We managed to restore our clients’ data from our datacentre
Quote:
Netstar says:
December 10, 2013 at 11:38 am
We’ve seen what the cryptolocker virus can do – nasty thing. Bitcoins, which is the currency the criminals want payment in, have gone up in value by a ridiculous amount since this virus came onto the scene.
We managed to restore our clients’ data from our datacentre
Bitcoins and the upswing in market value has nothing to do with Cryptolocker, or the hackers who are using Cryptolocker to force payment. Bitcoins just happen to be completely anonymous, with no tracability back to the user. It would be rather easy to trace someone requesting EUR/USD, now wouldn’t it?
Regards,
Alex
@Alex Bos.
“Bitcoins and the upswing in market value has nothing to do with Cryptolocker,”
“Bitcoins just happen to be completely anonymous, with no tracability back to the user.”
So what you’re saying is, bitcoins has EVERYTHING to do with cryptolocker. Otherwise, it would be completely unsuccessful.
Good write up on what is cryptolocker – keeps things basic, but goes to explain it so that someone who is not very tech savvy to understand how it actually works and what it does. I really liked the definition you put up for it as well; “hijacks users’ documents and asks them to pay a ransom (with a time limit to send the payment).” Strange I didn’t find it earlier.
In the last part, on how to avoid Cryptolocker, I like how to included having a backup system in place. This could not be more important, along with user education of course. I would add however on software that can remove or reverse cryptolocker if indeed it strikes. What worked for me was using Rollback Rx, something like windows system restore only more powerful, as it works outside windows on its own OS.
Great article.
Why not just use one summetric key for all files and decrypt it? I understand if they generate a unique IV or nonce for each block cipher, but I don’t see the benefit in using a unique symmetric key for each file. Could someone please explain this?
🙂 – not so anonymous – bitcoin transactions – in the near future many hackers will have problems because of it. Remember the blockchain is open and all of those idiots are cashingout the BTC they won by hacking only 2-3 days later is so easy for the police to catch them 🙂
Great article explaining the cryptolocker malware, thanks for sharing
cryptolocker
Thank you so much for sharing this with us. This type of virus intrusion is big business now for the hackers now. So we need a global wide effort to get it under control
We agree with you, thanks for your comment!
Best regards,
Panda Security.
I believe that you need a three pronged approach to approaching Crypto and other variants of Ransomware : Prevention (via next generation endpoint security + DNS level protection), Education (The users are the weakest link in an organization’s IT security framework. They need to be educated on security basics) and Recovery (Rollback of the attack + recovery of data from offsite backups.
Cybercriminals keep getting more and more sophisticated and are launching very targeted attacks. It’s imperative that businesses take necessary steps to protect themselves.
For those of you who want to learn more, we have published a nifty Infographic on Ransomware during ‘World Backup Day 2017’.
It’s actually very complicated in this active life
to listen news on TV, therefore I just use world wide web for that reason, and take the most up-to-date information.
It is very important to keep updated about cyber threats so we make sure we can fight them. And also, have your devices protected at all times.
Thanks for your message!
Best regards,
Panda Security.
A fascinating discussion is definitely worth comment. I think that you need to
publish more on this subject, it might not
be a taboo matter but generally folks don’t speak about these topics.
To the next! Best wishes!!
Hello!
We will definitely keep talking about this matter, susbcribe to our blog so you can keep yourself posted!
Thanks for reading us!
Best regards,
Panda Security.
Hi,
This article is great for us, presently I have found cryptolocker beaconing as a risk warning one of our pc .This type of virus intrusion is big business now for the hackers now. So we need a global awareness to get it under control.
Thanks for reading us!
We agree awareness and protecting your devices is essential for preventing being victims of these attacks.
Best regards,
Panda Security.
If some one needs expert view about blogging then i advise him/her to pay a
visit this blog, Keep up the pleasant job.
Thanks a lot! We appreciate your opinion!
Best regards,
Panda Security.
Great article, thanks for sharing.
Think it’s worth adding that Cryptolocker can infect backups. End users should ensure they disconnect their external hard drives after each backup completes, to minimise chance of infection.
A really good summary of cryptolocker and how dangerous it can be. Totally agree with the importance you stress on back up. From our experience helping clients hit by cryptolocker and other ransomware, the better the back up strategy the less damage it will cause the business.
Great article, still just as relevant now.
Thanks for your input and for reading us!
Best regards,
Panda Security.
Is Cryptolocker decreasing in popularity in terms of active threats?
We have only seen 1 issue of an infection and most people are backing up to the cloud which means these sorts of threats surely are becoming less financially viable but still irritating?
Hello Paul,
We are not too sure that attacks are decreasing… Our most recent PandaLabs report records a 40% increase in attacked devices this quarter. See full report in here: https://www.pandasecurity.com/en/mediacenter/pandalabs/pandalabs-report-q2-2017/
Thanks fore reading us!
Best regards,
Panda Security.
Thank you so much for sharing this with us. Cryptolocker malware needs to be managed to keep everyone safe.
Thanks N-Vico!
It’s remarkable to visit this web site and reading
the vieews of all friends concerning this article, while I am
allso keen of getting familiarity.
Thanks for this very good overview. We’ve seen that the ransom has traditionally been set at a rate intentionally within reach to encourage payment. Having said that I believe that the domains used to direct to the payment gateways are now being quickly removed to try and force people not to capitulate. Has that been your recent experience too?
Thank you for sharing a simple article explaining about Cryptolocker. It is a real problem and this is the reason I always try to keep my antivirus definitions up to date.
We are glad to know you find our content useful!
Kind regards,
Panda Security.
Thanks for the detailed article about the Crypto locker I really learned a different thing this morning. Thanks hoping for more related articles.
Many thanks for reading us! We are glad to know you enjoy our content.
Kind regards,
Panda Security.
This would really help people like me who have zero knowledge of Crypto and its empire.
May I ask one question ?
Do we have any body who is working specifically to track these people ?
I mean this is a crime and they should be punished.
Thank you so much. I was looking for an article like this.
Happy to know you enjoy our content!
Thanks for reading us!
Kind regards,
Panda Security.
This is very great information thanks for sharing this article with us. I bookmarked this website for read this article in future.
Thanks.
Thanks for such nice feedback!
Kind regards,
Panda Security.
very nice information thanks for sharing this article.
Thanks for reading us!
Kind regards,
Panda Security.
You explain each and every point very deeply. I read this article and i feel this article is really amazing thanks for sharing this article with us.
We are happy to know you find our content useful.
Thanks for reading us!
Kind regards,
Panda Security.
Valuable information, I have already been searching for several times but this one is the correct one! You have just received one shared!
The virus publishers/administrators can be traced and identified as there must be two way communications ie demand / payment / delivery of key between them and the prey – so the challenge is for a-v companies to become offensive in processes to protect subscribers , maybe under ” rule 303 “
Thanks for the detailed article about the Crypto locker I really get to know a lot of new things! If you write more articles kindly let me know! You have my email now!
Thanks a lot for sharing your feedback!
We are glad to know you enjoy our content!
Kind regards,
Panda Security.
Oh I already have it but I didn’t get the email and nothing really happening.
Do you know whats happening? ?:/
People can avoid Cryptolocker and various other ransomware threats by simply paying for a more robust antivirus solution. Many people tend to opt for the Free antivirus products which don’t do as greater job as the paid for versions. eSet is our favorite and hasn’t let us down yet.
However, that said, the number one cause for obtaining a virus in the first place is poor user training or awareness. Before you click, be sure what you’re clicking is legitimate.
We wrote an article titled “How to protect your business from a cyber attack”
Your readers may find the tips useful.
https://www.sysfix.co.uk/Blog/How-to-protect-your-business-from-cyber-attack.html
That’s a great article on avoiding the malware.
Thanks for sharing.
Thanks for reading our post!
Kind regards,
Panda Security.
Thanks for sharing knowledge about CryptoLocker. Really got so many new things to learn. Again say that. thanks a lot.
Great Article, Also I need to share that to prevent from becoming a ransomware victim, organizations need to protect their network now and prioritize resources. These attacks will only continue to grow, and no organization wants to be displayed by the media as being forced to pay a ransom. If you are forced to pay, customers can lose trust in your organization’s ability to secure their personal data and the company can see decreases in revenue and profit.
Thanks for sharing Great article….
Fantastic article. I have sent this link other to some of my clients to help them understand it better 🙂
Shocking how much malware is on the rise, in London especially. It’s costing businesses in the billions at this point, and an ounce of prevention really is worth a pound of cure.
Thanks for the informative piece.
Thank you for sharing such a great article. It’s really very helpful compared to the different article about malware on the web. Certainly will be able to communicate to our clients more in dept about viruses.
Thanks for sharing this article regarding Parking spaces on campus, it was quite insightful.
Hoping to see more articles.