Situation
This article provides you with guidelines and recommendations regarding the protection upgrade of Panda Adaptive Defense/Panda EndPoint Protection products in your network environment.
Considerations
Usually, administrators decide to plan the upgrade of their environment, either to be able to test a new product feature, or to install a new version that includes a fix for an existing issue. These specific upgrade requests are usually managed directly through an Account Manager or a Support representative.
As a general consideration, bear in mind that a version upgrade could potentially lead to the following:
- Console version upgrade (transparent, at the Panda server side).
- Agent version upgrade (transparent, does not require reboot, at the endpoint side).
- Protection version upgrade.
As it happens with any other security software, the Panda Security protection module is the most sensitive module of our security products and it runs in the background of the operating system. Sometimes, upgrading it may require to uninstall or install drivers that cause the computer to restart.
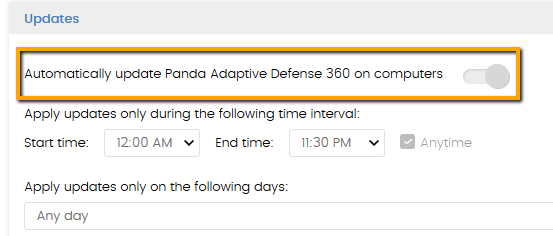
NOTE: To enable/disable and configure upgrade settings, open the administration console, select the Settings tab, click on the left pane Per-computer settings menu, and access the Updates section:
|
Controlled Protection Upgrade Process
A controlled protection upgrade limits the scope of the process to a few endspoints and groups that you, as network administrator, designate. Once you verify everything is working as expected after you apply the limited upgrade to certain groups of computers, we recommend that you plan and execute the process for the rest of your network gradually.
Follow the steps below:
- Disable the Upgrade option in all your profiles.
- Create a profile or group and include a set of computers and devices that are representative of your environment, for example: regular endpoints, endpoints with key business applications, endpoints with settings that are specific to the management team, servers with key custom applications installed, etc.
- Enable the upgrade settings for that group.
- Monitor the upgrade for a reasonable period of time, such as one or two weeks, to ensure the upgrade has been carried out succesfully and all the applications are working as expected. Be aware that, in most cases, upgrading requires a complete reboot. If you experience any issues, raise a case with your Support representative.
- Split the deployment of the protection upgrade of your network into progressive stages. The process can be done in two or three phases, depending on your network configuration (number of endpoints, servers, etc.).
Take into consideration that to ensure the best protection of your environment, all the endpoints of your network, including your servers, plus environments with gold images or virtual systems in place, must be migrated to the latest protection version and get the latest technologies available.