Our colleagues at PandaLabs have discovered a new strain of ransomware, a piece of malicious software which allows cyber-criminals to remotely lock the computers they infect.
Ransomware locks computer systems and encrypts files, demanding the user pay a ransom to get control back.
The new variant has been detected as Trj/Crypdef.A.
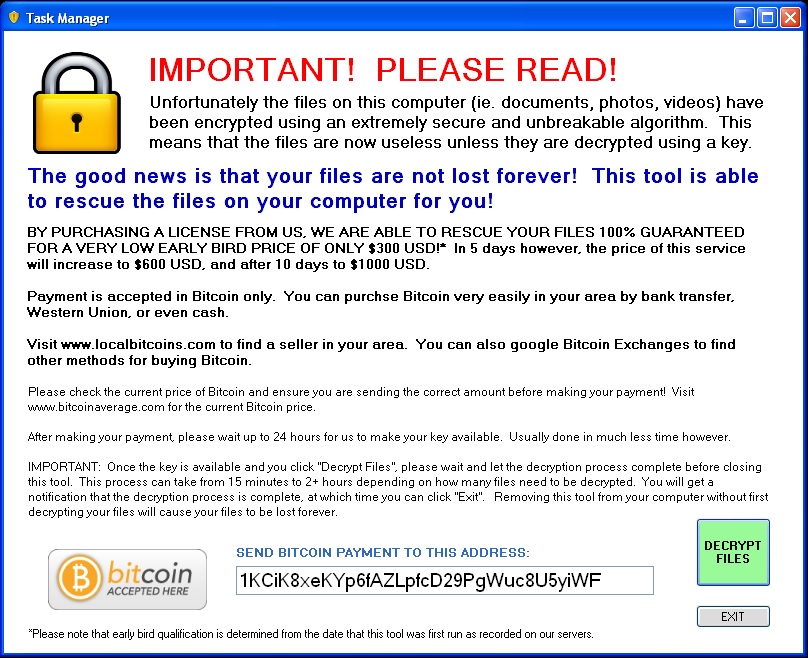
How Trj/Crypdef.A works
- It creates the following registry entry: HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\ESENT\Process\(file name)\DEBUG
- It creates the directory C:\ZeroLocker and copies itself to it as the file ZeroRescue.exe
- It creates the following registry entry so that it runs whenever the computer starts:
HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run “FileRescue”
Data: C:\ZeroLocker\ZeroRescue.exe
- It connects to the following URLs:
- hXXp://5.199.171.47/patriote/sansviolence
- hXXp://5.199.171.47/zConfig/173812
- hXXp://5.199.171.47/zImprimer/446305781-6Anf32MoZG805MwwG2lX-17xQqSvhHu3bEmYdmo1G1hwob1h6UFq3oe
How to avoid the ransomware
- Keep your operating system up to date to avoid security vulnerabilities.
- Install a good antivirus.
- Do not open email messages or files from unknown sources.
- Avoid accessing unsafe Web pages or pages with questionable content.