One of the most interesting things in order to know how the bot behind Mariposa has been spreading is to study the geographical distribution of the infections. Unlike other cases, the Mariposa Working Group stats don’t come from scanning PCs. In order to avoid the DDP Team from controlling Mariposa, we managed to change the DNS of the C&C servers, so all the bots where redirected to a sinkhole. That’s when we realized for the first time how huge was the botnet. We were able to see all the IP addresses of each and every bot that was trying to reach the C&C server to receive instructions. As you know, the number of IPs is not equivalent to the number of computers, as one computer can use multiple IP addresses, and many computers can use just 1 IP address (this usually happens in companies that connect to the Internet through a proxy server).
Before gathering all the info my guess was that most of the bots would be in the US, some countries in Western Europe, and some others in Asia (Japan, China). However, I was totally wrong. Here you can see a map, the darker the color the bigger the number of IPs:
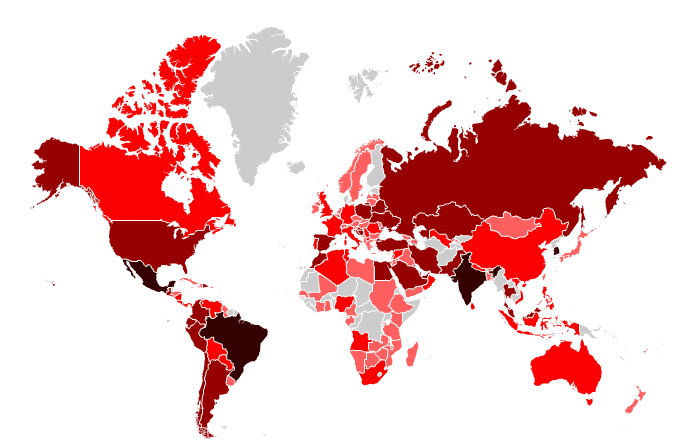
As you can see, there are infections in almost every country around the world. These are the top 20 cities with more Mariposa bots worldwide:
| # | Cities | % | IPs |
| 1 | Seoul | 5,36% | 761,444 |
| 2 | Bombay | 4,45% | 631,927 |
| 3 | New Delhi | 4,27% | 605,518 |
| 4 | Mexico | 3,89% | 551,705 |
| 5 | Bogotá | 2,68% | 380,487 |
| 6 | Lima | 1,98% | 281,103 |
| 7 | Kiev | 1,68% | 238,611 |
| 8 | Bangalore | 1,39% | 197,699 |
| 9 | Islamabad | 1,24% | 176,049 |
| 10 | Tehran | 1,23% | 174,455 |
| 11 | Kuala Lumpur | 1,16% | 164,986 |
| 12 | Madras | 1,11% | 157,070 |
| 13 | Santiago | 1,03% | 145,838 |
| 14 | Cairo | 1,01% | 143,187 |
| 15 | Hyderabad | 0,82% | 116,352 |
| 16 | Santo Domingo | 0,75% | 106,538 |
| 17 | Rio De Janeiro | 0,75% | 106,066 |
| 18 | Riyadh | 0,72% | 101,797 |
| 19 | MedellÃn | 0,65% | 92,433 |
| 20 | Dubai | 0,63% | 89,494 |
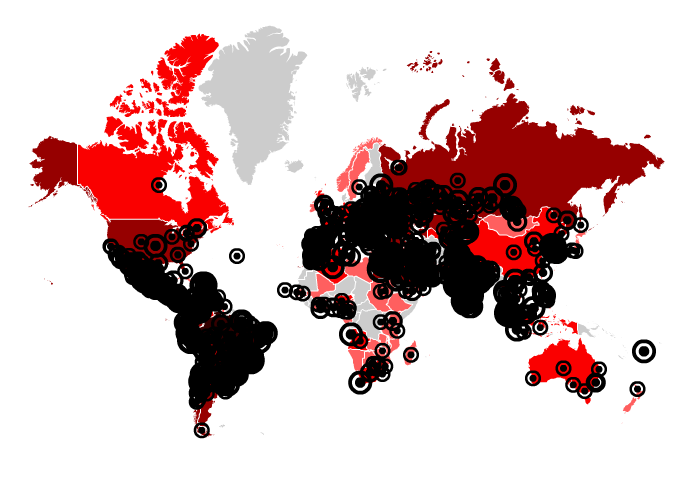
I have tried to represent all the cities in the world map, but drawing 31,901 different cities and towns is somehow complicated 😉
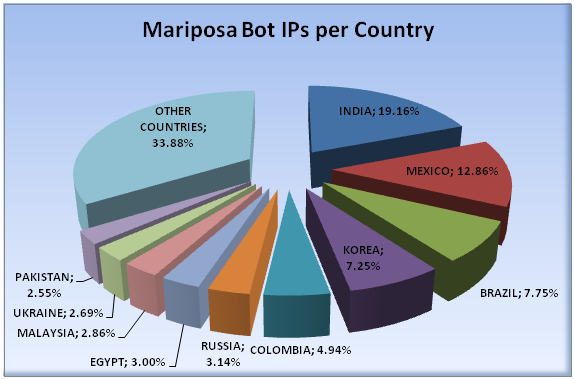
These are the top 10 countries:
And the detail of the top 20 countries:
| # | Countries | % | IPs |
| 1 | INDIA | 19,16% | 2,717,812 |
| 2 | MEXICO | 12,86% | 1,824,495 |
| 3 | BRAZIL | 7,75% | 1,099,058 |
| 4 | KOREA | 7,25% | 1,027,958 |
| 5 | COLOMBIA | 4,94% | 700,680 |
| 6 | RUSSIA | 3,14% | 445,293 |
| 7 | EGYPT | 3,00% | 424,984 |
| 8 | MALAYSIA | 2,86% | 406,129 |
| 9 | UKRAINE | 2,69% | 381,975 |
| 10 | PAKISTAN | 2,55% | 362,152 |
| 11 | PERU | 2,42% | 342,876 |
| 12 | IRAN | 2,07% | 293,673 |
| 13 | SAUDI ARABIA | 1,85% | 262,465 |
| 14 | CHILE | 1,74% | 246,941 |
| 15 | KAZAKHSTAN | 0,00% | 196,383 |
| 16 | UNITED ARAB EMIRATES | 0,00% | 163,440 |
| 17 | MOROCCO | 0,00% | 160,059 |
| 18 | ARGENTINA | 0,00% | 156,870 |
| 19 | UNITED STATES | 0,00% | 148,818 |
| 20 | BELARUS | 0,00% | 139,056 |
| 1 | Seoul | 5,36% | 761,444 |
| 2 | Bombay | 4,45% | 631,927 |
| 3 | New Delhi | 4,27% | 605,518 |
| 4 | Mexico | 3,89% | 551,705 |
| 5 | Bogotá | 2,68% | 380,487 |
| 6 | Lima | 1,98% | 281,103 |
| 7 | Kiev | 1,68% | 238,611 |
| 8 | Bangalore | 1,39% | 197,699 |
| 9 | Islamabad | 1,24% | 176,049 |
| 10 | Tehran | 1,23% | 174,455 |
| 11 | Kuala Lumpur | 1,16% | 164,986 |
| 12 | Madras | 1,11% | 157,070 |
| 13 | Santiago | 1,03% | 145,838 |
| 14 | Cairo | 1,01% | 143,187 |
| 15 | Delhi | 0,87% | 124,057 |
| 16 | Hyderabad | 0,82% | 116,352 |
| 17 | Santo Domingo | 0,75% | 106,538 |
| 18 | Rio De Janeiro | 0,75% | 106,066 |
| 19 | Riyadh | 0,72% | 101,797 |
| 20 | MedellÃn | 0,65% | 92,433 |






7 comments