Fancy Bear (also known as APT18, Pawn Storm, Sofacy Group, Sednit and STRONTIUM) is a Russian cyber espionage group specialized in cyberattacks that are classified as Advanced Persistent Threats (APTs). As we explained in a previous post, APTs are characterized by their sophistication, for how they tend to target certain select companies or organizations, and for their capacity to outwit traditional defense mechanisms.
And Fancy Bear’s most recent development fits in perfectly with this level of sophistication: it is called LoJax, and it is a piece of malware that is able to survive an operating system being reinstalled. This makes it especially dangerous for companies and institutions that are lacking protection against this kind of attack.
How does LoJax work?
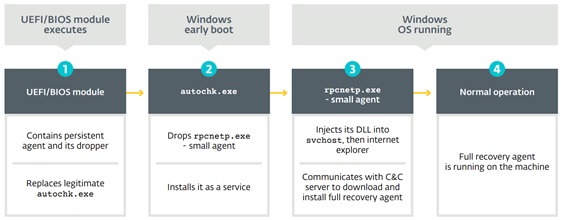
LoJax acts like a rootkit, that is, a program or set of tools that provides access to a computer or network’s administrative levels whilst staying hidden. But what makes LoJax so special is that it is the first rootkit to be detected that directly attacks the Unified Extensible Firmware Interface (UEFI).
And what is the UEFI? UEFI is the successor of BIOS, the key to any computer, since both are firmware stored in a separate memory found on the motherboard, and both contain the instructions that control the operations on the computer’s circuits, all of which means that it does not rely on operating systems.
Accordingly, LoJax takes advantage of a vulnerability in Computrace LoJack, a piece of software that comes preinstalled on many computers’ UEFI. This software sends information about the location of the computer, as well as allowing files to be deleted or blocked in case of theft. As it is an anti-theft mechanism, LoJack was designed to remain on a computer even if the operating system is reinstalled or replaced on the hard drive, since these are both elements that thieves usually alter after stealing a laptop.
The way that LoJax accesses both the UEFI and LoJack is by using binary files that, from the operating system, compile information about its hardware. From there, they patch the UEFI, hide the malicious code, and write on it again, all from Windows. This way, the cyberattacker can take total control of the UEFI.
How to avoid attacks like LoJax
LoJax isn’t dangerous simply because of the infection of the UEFI itself, but also due to the fact that many cybersecurity solutions, including corporate cybersecurity solutions that are present in many companies, completely overlook Computrace LoJack and the UEFI software, as the classify it to be safe. For this reason, LoJax throws into sharp relief the fact that organizations must take cybersecurity measures that go beyond those aimed at protecting operating systems. Below, we’ve detailed some of our recommendations:
1.- Secure Boot Mode: the good news is that Fancy Bear’s rootkit is not properly signed, i.e., securely registered like the rest of the common hardware installed and detected on the UEFI. The first security measure, therefore, is to activate the UEFI’s Secure Boot Mode on the company’s computers. When this mode is activated, all the components of the firmware must be properly signed, and it does not allow those that show any anomalies, as would be the case of LoJax.
2.- Modernization of computers’ chipsets. The vulnerabilities discovered in Computrace LoJack that allow the LoJax attack only work with old UEFI settings. The series 5 Intel chipsets, first introduced in 2008, have platform controller hubs, which have been proven to be immune to LoJax.
3.- 360º security solutions. In any case, to provide general protection from malware, it is advisable to have 360º security solutions that go beyond detecting vulnerabilities in entrypoints, and also take into account security on the endpoint. It is vital to have solutions that automatize the prevention, detection, containment and response to any advanced threat, like APTs. Our advanced cybersecurity suite, Panda Adaptive Defense, is capable of totally monitoring all possible cyberattacks and unwanted accesses. What’s more, it has a complementary module that takes care of an aspect that is often overlooked: the installation of patches and updates. Our 360º solution combines detailed visibility of the activity on the endpoints, control of all running processes and reduction of the attack surface, to keep companies from falling victim to attacks, no matter how sophisticated they are.






1 comment
In order to protect HW, all we need is HW-oriented solution. Say if you wanted to update the UEFI/BIOS you should’ve move a “read-only” switch.. So simple – yet powerful. Sometimes the simple goo-old things are the best in life..