What lurks in our microphones?
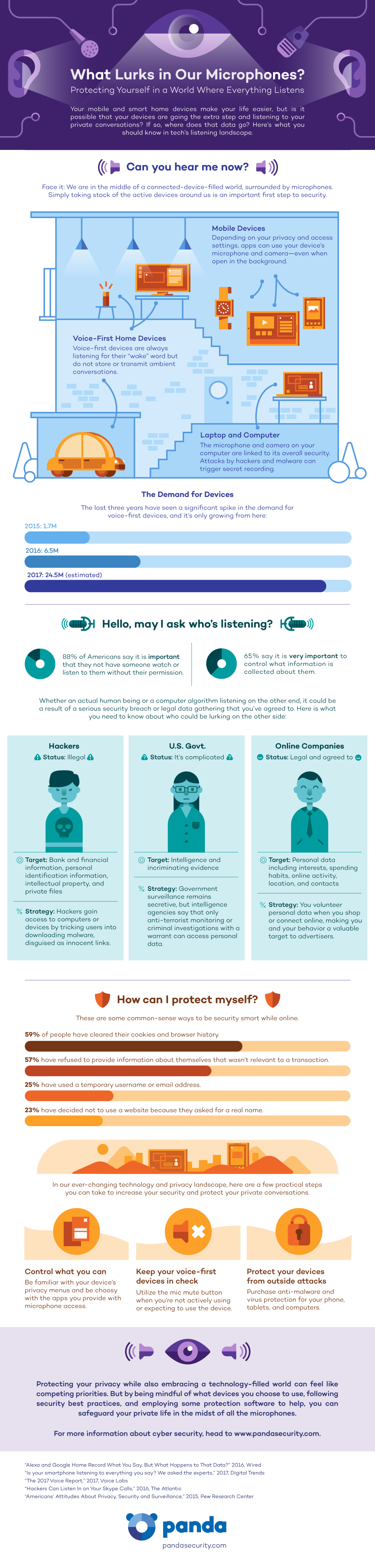
Microphones play an important part in day-to-day life. We can talk with almost anyone in the world using our smartphones, tablets and laptops. We can even give our in-home smart technology instructions simply by speaking to it.
But this power and convenience often means that microphones have to be left switched on – which means that everything is captured, including what we are not saying directly to the microphone.
Smart home speakers
For many services, privacy is traded in exchange for free access to a service. The Amazon Echo and Google Home speakers are constantly listening for the trigger words that tell them to expect an instruction – each device constantly records snippets of conversation in readiness. If the trigger word is not used, the snippet is deleted.
It is worth noting that where the trigger word is detected, captured snippets are retained forever – even if you delete them from your command history.
Smartphone apps
Modern smartphones also contain a voice activated assistant, typically Google Now or Apple’s Siri. When activated, these voice assistants also capture and store your instructions, treating the captured audio in the same way as smart speakers.
The actual apps that you install on your phone may also need access to the microphone. Normally you will be asked to allow access, but if you choose to block the microphone, you may not be able to use the service. If you are worried about how your data is collected and used, you should read the app’s Terms of Service before agreeing.
Your laptops and PCs
Apps like Skype and FaceTime need access to your microphone – otherwise you cannot chat with your contacts. Typically none of these services record or store your data, although Google Hangouts does monitor every conversation to make “smart” suggestions. It is unclear whether this data is retained by Google, but judging by their general terms of service, it would be unusual if they didn’t.
What about hacking?
Every internet-connected device is at risk of hacking. Cybercriminals could use the microphones built into your laptop or smartphone to collect sensitive data about you, like passwords. In theory they could even record personal information that they later use to blackmail you.
Recent leaks suggest that the US government has developed a tool for hacking smart TVs for instance, allowing them to monitor and record nearby conversations. If the government can do it, so can criminals.
Although smartphone and smart device hacking is on the increase, your PCs and laptops remain the easiest targets for hackers. And because we rarely turn computers off any more, they are perfect for eavesdroppers keen to grab our sensitive information.
It’s worth noting that government monitoring of your microphones may not be illegal. They are permitted to access your systems if they are investigating criminal activity or terrorism for instance.
How to protect yourself
Preventing your microphones from being compromised relies on two principles: installing anti-malware tools to block hackers, and applying common sense – paying attention to the apps you install and use.
You must pay special attention to the apps you give permission to access your microphones. If you notice that your microphones are being used without permission, there may be a problem.






4 comments
Es ist absolut perfekt das Panda so auf die Privatsphäre achtet und diese schützt
Danke!