Virus Encyclopedia
Welcome to the Virus Encyclopedia of Panda Security.
Stuxnet.A | |
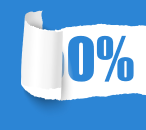
Threat Level Damage Distribution |
Effects |
The aim of Stuxnet.A is to carry out a targeted attack to companies with SCADA (see Note) systems which use WINCC of Siemens, in order to steal information. In order to be installed in the computer, it uses the vulnerability MS10-046 (CVE-2010-2568). It is a Windows vulnerability that affects shortcuts and which allows remote code execution. Stuxnet.A carries out the following actions: - The infection starts with several shortcuts specially designed to exploit the vulnerability and which are located in an infected USB key.
- The malicious shortcuts are the following:
Copy of Copy of Copy of Copy of Shortcut to.lnk
Copy of Copy of Copy of Shortcut to.lnk
Copy of Copy of Shortcut to.lnk
Copy of Shortcut to.lnk - If the computer is vulnerable, the library ~WTR4141.TMP is automatically downloaded and run without clicking on the shortcut, as this vulnerability allows remote code execution.
- This library loads and runs another library, called ~WTR4132.TMP, which drops several rootkits to the computer. These rootkits allow the worm to be hidden, making its detection more difficult.
Microsoft has already released the security patch that solves this vulnerability. If you have a Windows 2008/7/Vista/2003/XP computer, it is recommended to download and apply the security patch for this vulnerability. Access the web page for downloading the patch. Note: SCADA stands for supervisory control and data acquisition. It generally refers to an industrial control system: a computer system monitoring and controlling a process. Infection strategy Stuxnet.A creates the following files: - MRXCLS.SYS and MRXNET.SYS, in the folder drivers of the Windows system directory. These files belong to the malware detected as Rootkit/TmpHider. These files have the digital signatures of certain companies, which have been supposedly stolen from them. The aim is to pass themselves as legitimate files.
- MDMCPQ3.PNF, MDMERIC3.PNF, OEM6C.PNF and OEM7A.PNF, in the folder Inf of the Windows directory. The files with a PNF extension are files with encrypted data.
Stuxnet.A creates the following entries in the Windows Registry: - HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Enum\Root\LEGACY_MRXCLS
- HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Enum\Root\LEGACY_MRXCLS\0000
- HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Enum\Root\LEGACY_MRXCLS\0000\Control
- HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Enum\Root\LEGACY_MRXNET
- HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Enum\Root\LEGACY_MRXNET\0000
- HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Enum\Root\LEGACY_MRXNET\0000\Control
- HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\MRxCls
- HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\MRxCls\Enum
- HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\MRxNet
- HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\MRxNet\Enum
- HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Enum\Root\LEGACY_MRXCLS
- HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Enum\Root\LEGACY_MRXCLS\0000
- HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Enum\Root\LEGACY_MRXCLS\0000\Control
- HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Enum\Root\LEGACY_MRXNET
- HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Enum\Root\LEGACY_MRXNET\0000
- HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Enum\Root\LEGACY_MRXNET\0000\Control
- HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\MRxCls
- HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\MRxCls\Enum
- HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\MRxNet
- HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\MRxNet\Enum
By creating these entries, the rootkits register themselves as a service and can be run whenever the computer is started. Additionally, they are injected into LSASS.EXE, SERVICES.EXE, EXPLORER.EXE y SVCHOST.EXE processes, so that they cannot be viewed.
|
Means of transmission
Stuxnet.A spreads through removable devices, like USB keys, making copies of the malicious shortcuts to the USB keys that are connected to an infected computer. These shortcuts use the vulnerability called MS10-046 (CVE-2010-2568), which affects files with a LNK extension.
Further Details
Stuxnet.A is 8,192 bytes in size.
Stuxnet.A creates several random mutexes, in order to ensure that only a copy of the worm is active at any moment.