Pharming is a scam that cybercriminals use to install malicious code on personal computers or servers. As the name suggests, it comes from the words “farming” and “phishing,” and it represents a new, more complicated technique hackers use to access sensitive information.
The malicious code involved in pharming attacks changes the IP address information, which misdirects users to fake websites without their knowledge or consent. Once redirected to these fake websites, users are prompted to enter personal information, which is then used to commit identity theft or financial fraud.
Attackers mainly target customers of banks or other monetary exchange systems when executing pharming attacks. This tactic is successful because it allows hackers to infiltrate multiple devices at once. Additionally, hackers don’t need to convince users to click a doubtful email link or suspicious advertisement. The malicious code is automatically downloaded without any action from the user.

How Does Pharming Work?
Pharming is an exploitative practice done by either infiltrating individual computers or poisoning a server. Both options use code that redirects websites, but each is executed differently.
But how does pharming work on a case-by-case basis? To understand the mechanisms and nuances, you should first understand the different types of pharming.
Hacking Individual Computers
In this type of pharming, the hacker sends an email with a code that modifies the host files of an individual’s computer. Once the host files are infiltrated, they can redirect URLs to a fake version of the website the individual intends to visit by replacing the legitimate IP address with a fake one. Even if the user types in the correct URL, the page will redirect. These websites mimic the appearance of real sites, so users may not be aware they are victims.
Poisoning a DNS or DNS Cache
A much more extreme version of pharming is domain name system poisoning, or DNS poisoning. To understand this type of pharming, you first need to understand what a domain name system (DNS) is and how it works. DNS servers essentially translate domain names into IP addresses — changing them between “human” and “computer” languages.
In this pharming attack, a hacker attacks the DNS server rather than infiltrating files on a personal computer. This server can handle thousands to millions of internet users’ URL requests — meaning each user is unknowingly redirected to fake pages. This large-scale threat is especially dangerous because affected users can become victims despite having a secure and malware-free device.
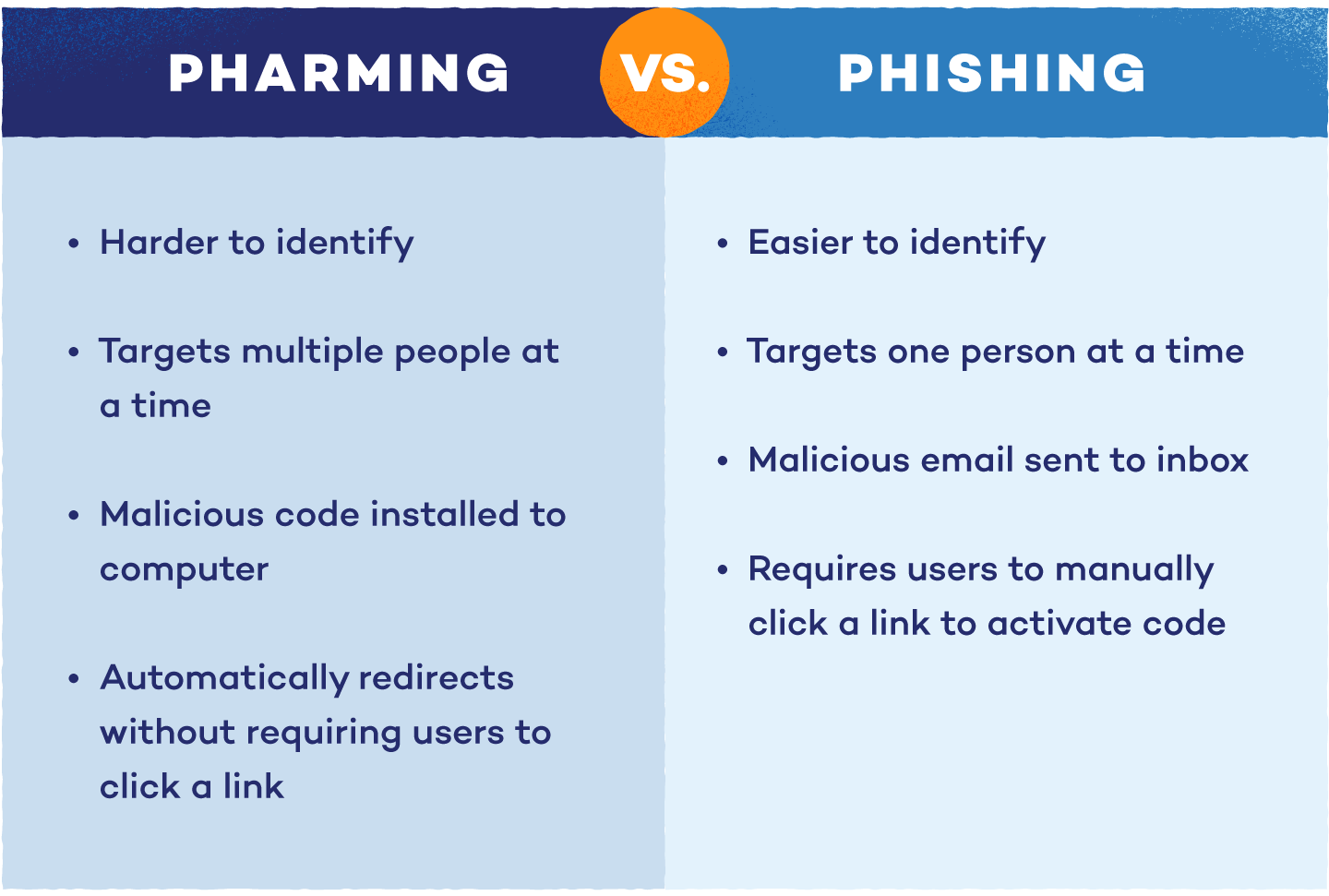
Pharming vs. Phishing
With so many “ph-” words to keep straight, it might be hard to differentiate between pharming, phishing and other cyberattacks.
Phishing is a technique that acquires personal information by sending malicious emails designed to look legitimate. Attackers use pitching to convince users to click on a link in a fraudulent email. In addition to email phishing, hackers are moving on to other forms of communication, such as texting (smishing) and voice messaging (vishing).
Pharming, on the other hand, involves creating fake websites to steal personal information. While phishing involves clicking on a link from a fraudulent email, pharming doesn’t always require users to take manual action — they are redirected to these false websites without even knowing.
Signs of a Pharming Attack
Pharming attacks can be difficult to detect, especially if a malicious website is nearly identical to the original. However, there are subtle ways to tell if you’ve fallen victim to an attack. Some common signs of pharming to watch out for include:
Subtle Changes to a Link or Website
Attackers sometimes change letters in the URL or use altered graphics when creating a malicious website. If you notice typos, altered logos or colors you don’t recognize when visiting a familiar site, it could be a pharming website.
Unsafe Connection
Pharming sites often use “http” instead of “https” in the URL, indicating that the connection is not secure. If you receive a message warning that your connection is not secured or you don’t see a gray padlock symbol in the address bar, you could be on a malicious website.
Unusual Account or Banking Activity
Attackers often use pharming to access bank accounts and other sensitive information. If you notice unauthorized activity on your credit card or bank account, you may have fallen victim to a pharming attack.
Unauthorized Password Changes
If an attacker gains access to your login information for an online account, they may change the password to prevent you from logging in. Random password changes are a good indicator that someone has hacked your account.
Unfamiliar Apps or Downloads
An unfamiliar app or program that suddenly appears could be a sign that a hacker has gained access to your device.
Cybersecurity Risks
Pharming attacks can have serious implications for companies and individual users alike. Some of the most common risks include:
Data Loss
Attackers can use pharming to access personal data or other sensitive information. This is especially dangerous for business owners or people who use the same password for multiple accounts. If you suspect that an attacker gained access to your login information through a pharming attack, you should change your passwords immediately and take steps to secure affected accounts.
Malware
Opening a pharming website or clicking an unfamiliar link could expose your device to viruses and other malware. Unless you use a reliable antivirus detection tool, you might not notice this process taking place.
Financial Theft or Fraud
Once an attacker gains access to your accounts, they could use your information to steal money or make fraudulent purchases. This is especially common for fraudulent sites that mimic banks or other financial institutions.
How to Protect Against an Attack
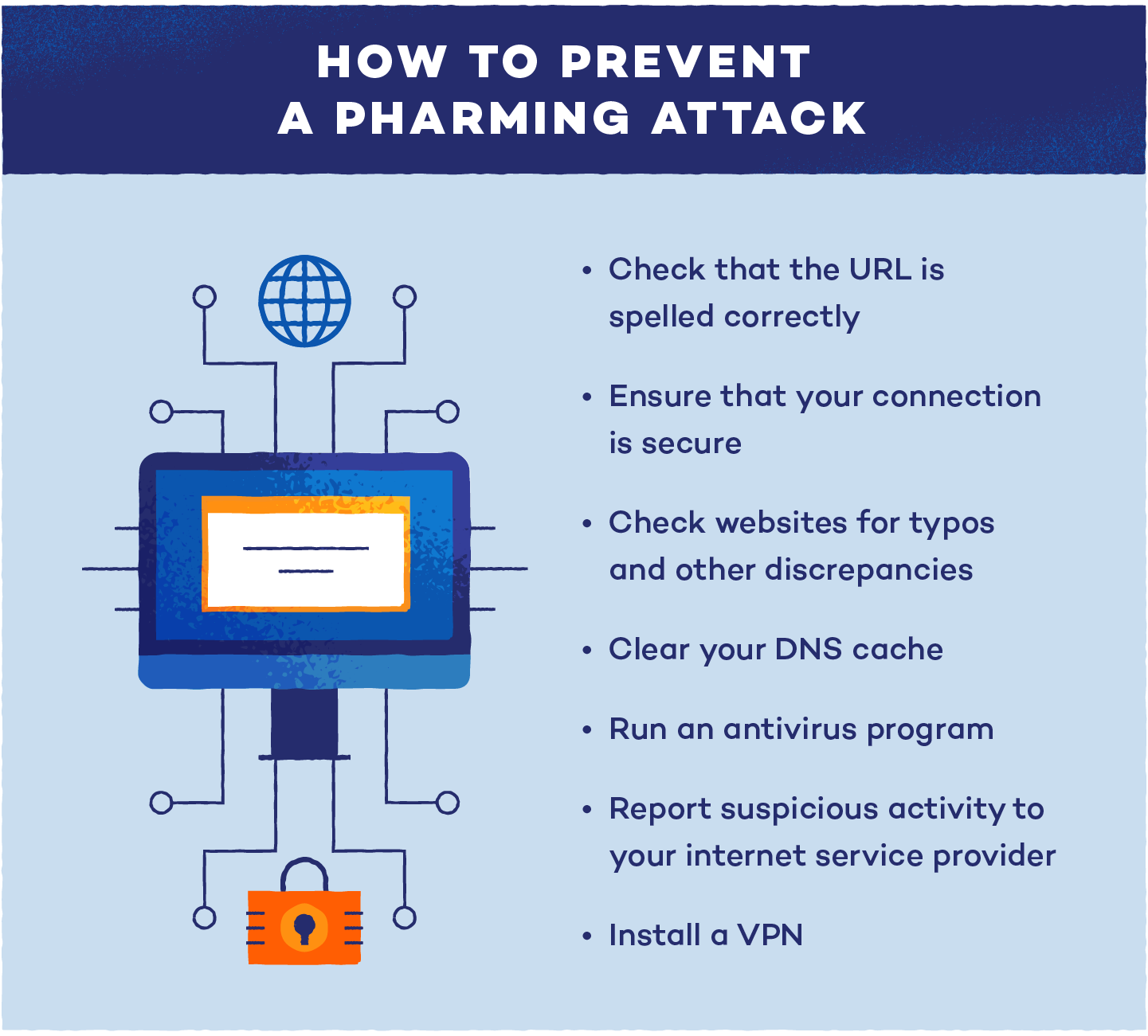
Although many pharming attacks can’t be prevented, there are a few steps that can ward off cybercriminals.
- If you think you are a victim of an attack, clear your DNS cache.
- Run an antivirus program to make sure your device is secure.
- If you believe your server is compromised, contact your internet service provider.
- Install a VPN for secure online browsing.
With the prevalence of predatory tactics like pharming and phishing, it’s more important than ever to protect yourself from all sorts of malware attacks. If you take precautions and are diligent with your internet use, you can minimize the chances of your data being stolen with malicious code. Check out our antivirus software to secure your digital life today.



