A step-by-step guide to disappear from the Internet
Before you delete yourself from the internet, make sure that this is what you want. And if you are not 100% sure, create a backup of the information that you may need in the future.
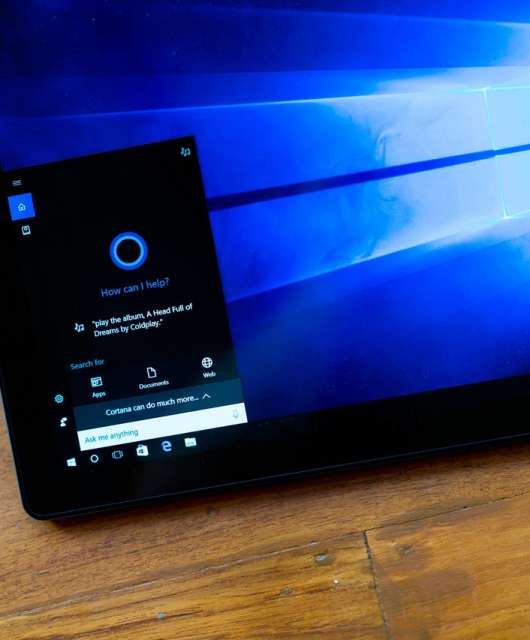
Cortana security flaw means your PC may be compromised
A new security flaw means that Cortana, Microsoft’s virtual assistant, could be abused by hackers and be used to run scripts and other executables from a USB drive.
How to Save Data
Our smartphones are latched to us at all times and we constantly spend time online. From using applications to searching the web, we spend at least a few hours a day connected to the internet. But at what cost?
The hunter becomes the hunted: How cyber counterintelligence works
Counterintelligence takes as a jumping off point one basic premise: if someone is going to attack your company, the best defense is a good offense.
Danger on board: shipping routes are at risk
Updates to the cybersecurity ecosystem seem to have gotten lost at sea for the shipping industry. Measures that have been outdated for years in other…
Employee habits that can put your company at risk
There are many cybersecurity risks that companies can be exposed to. And the fact remains that there are several things that employees may do every day that could well lead to serious security breaches
Who has access to your real-time location data?
Wireless carriers and middlemen-companies are not always fully aware how the data is being used and do not have an effective way to monitor if consents are obtained.