From version 6.81*, Endpoint Protection and Endpoint Protection Plus allow administrators to report issues automatically to our Technical Support department directly from the administration console.
Thus, if a problem occurs on one of the computers on the network, the administrator can report it directly to the Technical Support department, sending the data required to diagnose it with the click of a button.
How to report a problem
- Go to the Endpoint Protection administration console.
- On the Computers tab, go to the details screen of the computer affected by the problem you want to report.
- Click the Report problem with this computer button.
- Enter a short description of the problem and click Send. The product will start collecting the computer data required to analyze the incident.
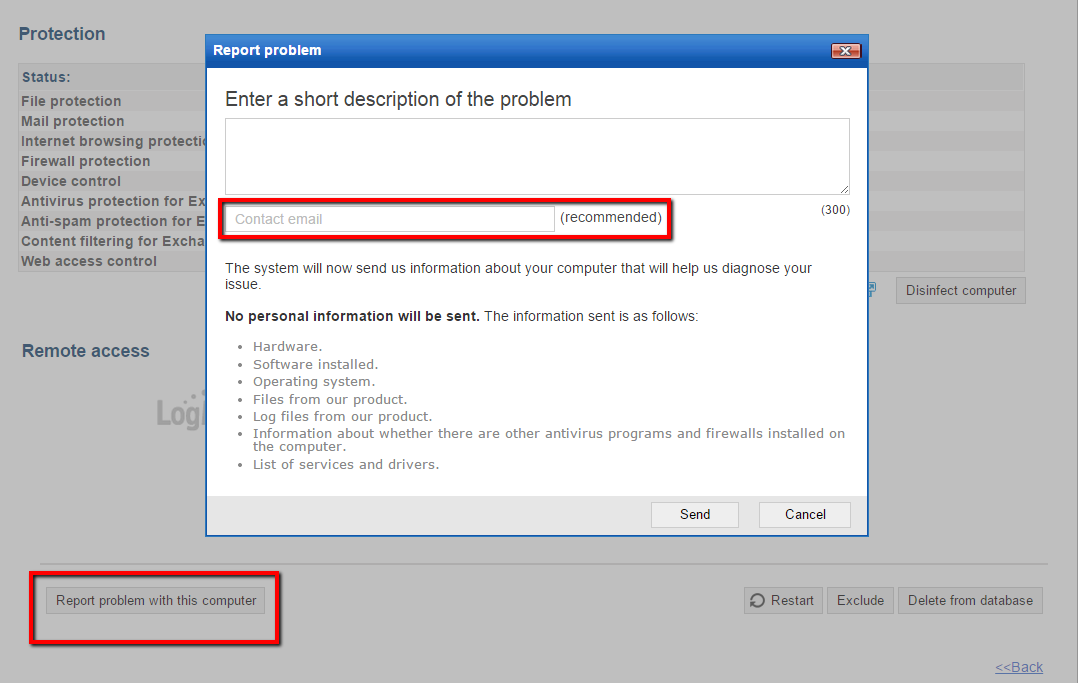
It is very important that you describe the problem briefly but accurately for us to be able to diagnose it as efficiently as possible. We also recommend to provide a valid email address to contact you, if needed.
No personal data is sent to Panda Security. - When the data collection process finishes, a message will be displayed informing you that the problem has been reported correctly to the Technical Support department in your country.
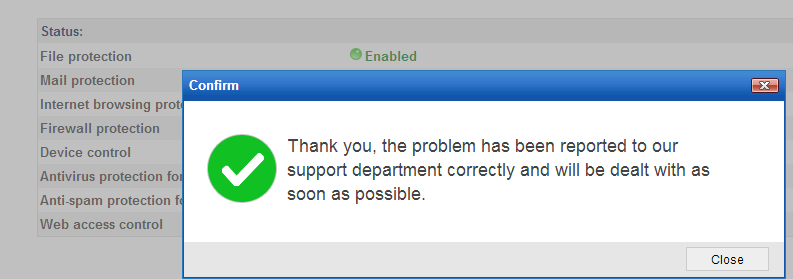
As soon as Panda Security's Technical Support team deals with your problem, it will contact you to provide you with the appropriate solution or, if necessary, request additional information.
* If you have a version prior to 6.81, contact your local office and request an automatic upgrade to the latest version of your product for free.