Even though Apple always seems to have made an effort to ensure the security of data on its devices, security researcher Jonathan Zdziarski claims that the company has done so to make sure it can legally access data on users’ smartphones.
Zdziarski is a forensic scientist and hacker who, with claims like these, is sowing the seeds of distrust among the Apple faithful. His specialty is forensic analysis, a set of techniques aimed at recovering data from any device –above all Apple in his case- even though the data may appear to be hidden.
During a talk he gave at Hackers On Planet Earth (HOPE/X), the security expert revealed the results of his latest tests on over 600 million devices with iOS: he discovered ‘backdoors’ or security holes that allowed users’ data to be leaked.

According to Zdziarski, these devices run hidden services similar to those he himself uses to retrieve data in forensic analysis.
Apple has been quick to respond to these allegations, claiming that there is no security flaws in its technology. They admit there are backdoors, though insist it’s not a serious issue. According to the company, they are for diagnostic purposes and are used to repair and configure the system, and always with the user’s consent.
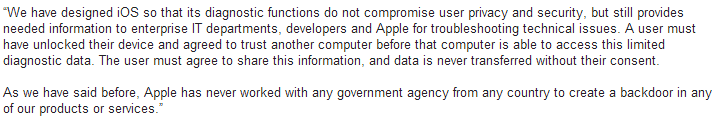
Yet these statements are not borne out by some of Zdziarski’s findings. Apparently, the suspicious tools had no function, and although some are mentioned in the user guides, their purpose is not specified.
If these components don’t have a clear purpose, why does Apple continue to maintain and update them?
Silent spies
The software supposedly accesses users’ information without notifying them, contrary to what would happen if it were really a diagnostic tool or application, and then stores the information on the smartphone or tablet in a an unusual format.
While it’s true that the data is encrypted, this is only when the device is rebooted. According to Zdziarski, if the device is in use, or just blocked, this data is unprotected and accessible.
The forensic scientist explains that to get the information stored by the hidden software, it’s only necessary to connect the device via USB to a PC or Mac. It could also be possible via WiFi, provided the device is not switched off. One way of increasing security is to install an antivirus like the one Panda has designed to detect malware on Mac computers, iPhones and iPads.
To obtain the iPhone or iPad, according to Zdziarski, all the authorities would need to do is stop users in a routine traffic control or arrest them and confiscate the device before it can be switched off, thereby preventing the information from being encrypted.
Permissive legislation
The IT expert claims that the entire strategy is well thought out, as U.S. laws state that a simple search warrant is sufficient to access the contents of apps like iCloud, iTunes or the device itself. Even though a recent change in legislation means that the users must be informed of the process, there is still a way to avoid this: a non-disclosure order.
Moreover, as it’s also accessible via WiFi when the device is switched on, Zdziarski believes that Apple could get a search warrant and extract information from files on devices running iOS, without informing users.

While the researcher says he is not accusing the company of working for the NSA, he still suspects that some of these services may have been used by U.S. Intelligence to obtain information from Apple customers.
One solution put forward by Zdziarski is to use Apple Configurator apps, available from the Mac App Store which can add security restrictions to the device and prevent it from being accessed by WiFi.





