PandaLabs, Panda Security’s anti-malware laboratory, has published its Quarterly Report for Q1, analyzing the IT security events and incidents from January through March 2013. Despite the numerous security incidents that took place during the first quarter of the year, the fight against cyber-crime is on the right track, and though there is still a long way to go, international co-operation among security agencies is beginning to pay off and criminals around the world are being brought to justice.
“The start of the year has seen some serious cyber-attacks, including the hacking of the Twitter accounts of major organizations such as the BBC or Burger King, and one of the biggest attacks ever, targeting some of the world’s leading technology companies: Apple, Facebook, Microsoft and Twitter. But there have been some victories for security forces as well, including the arrest of a group of hackers accused of extortion using the infamous ‘Police Virus’,” said Luis Corrons, technical director of PandaLabs.
Android, Top Target for Mobile Malware
Practically all news regarding malware attacks on mobile platforms involved the Android operating system, which has the largest share of this market. In addition to the usual attacks, this quarter saw new techniques that deserve mention. A strain of Android malware -hidden inside Google Play- not only infected cell phones but could also infect computers via smartphones and tablets.
According to Corrons, the area of cyber-war and espionage is becoming more and more interesting. “Many countries are looking suspiciously at China regarding its suspected involvement in attacks on large organizations and public institutions around the world, and this could lead to real world consequences. There are those who argue for international agreements, a type of Geneva Convention, to attempt to establish limits to these activities”, he said.
The Fight against Cyber-Crime
On January 11, the European Commission inaugurated the in order to support member states in the fight against cyber-attacks. Also in January, the FBI published details of an investigation that began in 2010 and thwarted a gang of cyber-criminals who had infected more than a million computers since 2005. This operation stands out not least because of the coordination between security forces in different countries. The FBI had the support of police in Moldavia, Romania, Holland, Germany, Finland, Switzerland and the UK.
There are also many different aspects to the fight against cyber-crime. And one which is often ignored is the need to alert companies to the importance of dedicating resources to protecting customer data. As a timely reminder of this, the UK division of Sony Computer Entertainment was ordered to pay 250,000 pounds as a result of the theft of customer data in 2011. The sentence is the consequence of the lack of measures that the company had implemented to protect customer information.
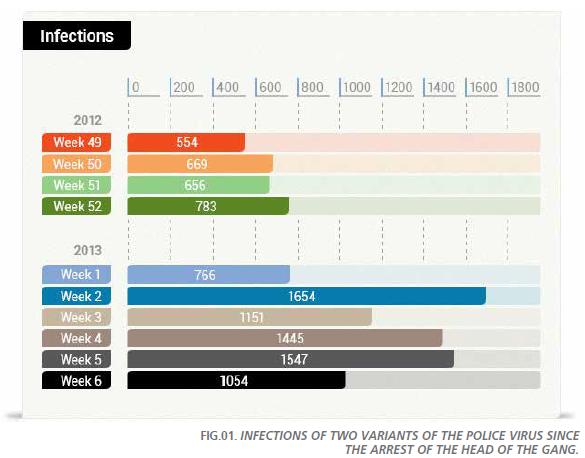
Police Virus Scam
One of the most infamous cases of the last year or so has been the ‘Police Virus’. In February this virus once again hit the headlines, but this time for a very different reason. The Technological Investigation Brigade of Spain’s National Police, together with Europol and Interpol, dismantled the cyber-crime ring responsible for the Police Virus. “We noticed that the news mentioned the arrest of ‘the gang’ of cyber-criminals, yet the information we have at PandaLabs points to the existence of several gangs responsible for these attacks. We reached this conclusion after analyzing numerous variants of the malware over time, and observing significant differences between them. In short, we are afraid the Police Virus is not likely to go away anytime soon. Users shouldn’t lower their guard,” said Corrons.
Twitter, Facebook, Apple and Microsoft Victims of the Same Attack
On February 1, Twitter published an article on its blog (“Keeping our users secure“) detailing how the social network had fallen victim to an attack resulting in unauthorized access to the details of some 250,000 Twitter users. A couple of weeks later, Facebook also released an article on its blog, “Protecting People On Facebook”, acknowledging that their systems had been targeted by a sophisticated attack. According to sources from the social network, user data was not compromised in this attack. Just a few days after the Facebook announcement, spokesmen from Apple told Reuters that the company had also been targeted by the same attack. And finally, of no less importance, Microsoft admitted that it too had been targeted. All these attacks exploited a previously unknown security hole in Java for which no patch was available. This is known as a zero-day vulnerability. In any event, here it is critical to be able to identify an attack when it is occurring, and Twitter, Facebook, Apple and Microsoft were able to do this.
Java
Most infections today occur through ‘exploit kits’, infecting users’ computers through a vulnerability without their knowledge. More than 90 percent of these are through Java vulnerabilities in browsers. The attacks on Microsoft, Apple, Facebook and Twitter used Java. Most ‘Police Virus’ infections managed to reach victims’ computers thanks to outdated versions of Java. What is the best way to prevent these infections? Simple: Just remove Java from the browser. If for any reason you need Java on your browser to use an application, use it on another browser set up specifically for this task.
Cyber-Attacks
The number and variety of attacks in this quarter have been significant to say the least. Evernote was the victim of an intrusion that prompted the firm to release a statement calling on more than 50 million users to change their passwords. According to a statement from the U.S. Federal Reserve, its website was also attacked, although it did not say whether any data was stolen. The incident coincided however with the publication, by Anonymous, of the personal information of 4,000 U.S. bank executives, suggesting that the attack on the Fed may have been carried out by this group. NASA was also the victim of an intrusion. Internal information including email addresses, real names and passwords, was published on the popular website Pastebin.
Social Media
During this quarter various Twitter accounts have been hacked, including those of celebrities and also those of companies. One of the most notable cases was that of Burger King, with attackers seemingly managing to work out the account password and take control of the account. They changed the background image to that of McDonalds and claimed that the company had been taken over by its main rival.
The Twitter account of car company Jeep was also the victim of a similar attack, in this case stating that the company had been bought out by Cadillac. Other attacks on Twitter accounts had a more political slant. A group of cyber-crooks calling themselves the “Syrian Electronic Army” managed to hack accounts belonging to several organizations. Apparently, phishing attacks were first launched to get the passwords and then the accounts were hijacked. Their victims included Human Rights Watch, the French news channel France 24 and the BBC weather service.
Cyber-War
China often gets a mention in this section, but in Q1, the Asian giant has earned all the headlines. On January 30, The New York Times ran a front-page article explaining how they had been victims of an attack that had allowed their computers to be accessed and spied on for months. Coincidentally, the attack came just after the paper released an article describing how Chinese PM, Wen Jiabao, and his family had amassed a billion-dollar fortune.
A day later, The Wall Street Journal declared that it had also been the victim of a similar attack by Chinese hackers. The Chinese government protested against these ‘unjustified attacks’ and Hong Lei –Chinese Foreign Minister– claimed it was “…unprofessional and groundless to accuse the Chinese military of launching cyber attacks without any conclusive evidence”.
Interestingly, in both incidents the attackers were able to access all types of data (customer details, etc.), yet only focused on information about journalists and employees, trying to find any reference to investigative journalism regarding China, and in particular, looking for the papers’ sources.
The day after the Wall Street Journal’s revelations, another US media giant, The Washington Post, announced they had suffered a similar attack in 2011, also originating in China.
Some weeks later, Mandiant published a damning 76-page report (APT1: Exposing One of China’s Cyber Espionage Units, http://intelreport.mandiant.com/) explaining how Unit 61398 of the Chinese army has specialized in cyber-espionage. The report revealed more than 3,000 pieces of evidence showing how this unit has been running since at least 2006, stealing information from no less than 141 organizations worldwide.
“We may not truly appreciate the importance of the Mandiant report and the impact it may have in the mid to long term. Proving who is behind any attack is highly complex, even in normal cyber-crime cases. When it comes to cyber-espionage things are further complicated by the simple fact that whoever is behind the operation is highly qualified and is adept at covering their tracks. For some years now, people have turned their gaze to China whenever this type of incident occurs, yet without any real evidence that the Chinese government is behind such attacks. Now, for the first time, it has been proven that the Chinese army is actively involved in espionage on a global scale, infiltrating companies across many sectors and stealing information”, explained Corrons.